Reviewed by Matt Edmondson
Recently I saw an email from ForensicFocus.com seeking a volunteer to write a review for Oxygen Forensics’ DETECTIVE Mobile Device Forensics Suite. I have quite a bit of mobile device forensics experience, but mostly using other tools, and very little experience with Oxygen Forensics products. I thought this would be a great opportunity to test out a new tool. My overall impression of DETECTIVE’s features:
– Intuitive functionality and easy to personalize reporting mechanism
– Robust Social Graphing and Social Charting capabilities
– Ability to analyze data acquired from multiple devices and create integrated timelines and maps
– Smart phone savvy, even with models not supported on their website; “feature” (non-smart phones) not supported as robustlyInstallation of DETECTIVE was fairly straightforward. I downloaded the newest version of the software from the Oxygen site, as well as a “driver pack” of device drivers to be installed on the computer. Once the software was installed, it asked me to obtain an “activation key.” The process was quick, and the license was good for installation on two systems.
The first phone I examined with DETECTIVE was a jail-broken Apple iPhone 5s. The device was recognized quickly and I was presented with multiple options for acquiring data from the device. Instead of just giving me names of the options, DETECTIVE provided a small paragraph for each explaining what the differences were. That was the first of many nice, user friendly touches I noticed while using this product.
Once the data from the iPhone 5s was acquired, it was time to examine the data in the DETECTIVE user interface. I found the interface to be clean and intuitive. I never once had to reference the documentation to figure out how to accomplish a task that I wanted to perform.
The iPhone 5s I tried first hadn’t been used much (it’s a test phone), but DETECTIVE did a great job of pulling off what information was present. After I poked around some of the data – including quite a few plain text passwords – I marked a few items as “Key Evidence” and generated a report. The reporting module was very well done and offers a variety of export options including PDF, HTML, CSV, RTF, XML and XLS. There were also numerous checkbox options that allow you to select what categories you would like to add or remove from the report. This was a much appreciated feature, as smart phone reports can get quite large.
I generated a PDF report and was pleased with the layout. The items I had marked as “Key Evidence” were presented early in the report, right after the device information and aggregated contacts. The timeline portion was also helpful, and I’ll discuss this feature more in depth a little later in this report.
After I finished examining the iPhone 5s results, I hooked up a Samsung Galaxy to be acquired. The specific model of Android I was examining wasn’t among the list of supported devices, but I selected another Samsung Android with a similar model number, and the process continued without a hitch.
Once again I was presented with multiple acquisition options, along with a brief explanation of what the different options consisted of. I selected an aggressive option which included trying to root the device in order to acquire a physical acquisition. DETECTIVE gave me a list of steps to be performed on the device and then it attempted to root the Android phone. The rooting process was unsuccessful, but DETECTIVE automatically acquired the phone data by backing the device up.
The Android contained quite a bit more information than the iPhone 5s, so there was more content to look at. I decided to take a look at DETECTIVE’s “Social Graph” function.
Social Graph is one of the methods that DETECTIVE provides to let examiners visualize a user’s activities. It does a FANTASTIC job! Social Graph creates a link chart with all forms of communications that it can find (calls, SMS, chat apps, etc.) and lets an examiner instantly see with whom the user of the device has frequent communications. In the past, I had used tools that provided this functionality, but it often felt bolted on and not fully functional. Here are some of the things I was able to do with the Social Graph tool on an iPhone 6 dump.
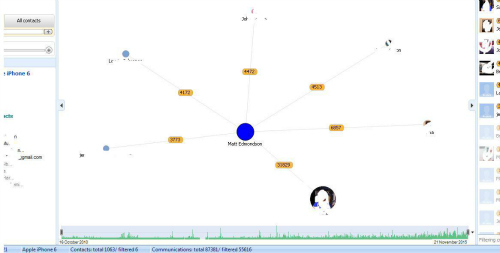
– I had so much activity on the phone that the initial chart was incredibly busy. A slider on the upper right allowed me adjust and limit the chart to only show individuals with whom I’d had a large number of communications.
– I wanted to limit the chart to a specific time period. The software allowed me to drag and drop a start and end date on the slider at the bottom of the screen.
– I wanted to remove Twitter chats from the chart and was able to deselect “Twitter Messages” from the “Type” options in the upper right.
– I noticed that one person accounted for a sizeable chunk of my activity. I clicked on that individual and was presented with an “Index Card” containing their contact info. It also had a tab with statistics which broke down what percentage of our communications used certain methods (SMS, Calls, etc.), and a communications tab listing every communication I’ve had with that person dating back over five years, and including two previous iPhones, all sorted in chronological order.
For these reasons and others, I fell in love with the “Social Chart” module.
After I examined the Android device, I acquired a fully updated iPhone 6. This device had quite a bit of usage and really let me explore the features of DETECTIVE.
The first thing I wanted to check was the applications. Just about every forensics tool does a good job parsing data from major apps such as Skype and WhatsApp, but what I was interested in was how DETECTIVE handled data from applications that weren’t supported. With the constantly changing app landscape, it’s critical to be able to examine applications that aren’t automatically parsed for you by the tool.
In the applications section of the DETECTIVE user interface, several apps were listed with a short summary of activity count in the app. For example: navigation apps had a search history; fitness apps had my workout history (and GPS logs), and so on. There was also a generic looking folder named “applications” which indicated that it had 112 entries underneath it. I clicked on the folder and was taken to a list of all applications on the device, including those which were parsed, those which were part of standard iOS installs, and third party apps.
I navigated to a third party app that wasn’t supported by any forensics tool that I’m aware of but which I use quite frequently. DETECTIVE brought up a sub menu of 24 files associated with that app including telling me what extension the files were and how big they were. I double clicked on a .plist file and, much to my delight, the contents of the file were instantly opened in a new window by “Oxygen Forensic Plist Viewer.” The Plist Viewer is relativity simple and very well laid out. I was able to easily navigate through the records and also view the raw data at the bottom of the screen and what the value was in about 20 different types of encodings on the right hand side of the screen, including multiple time stamp formats. The tool is very well done.
Next up I clicked on a .sql file associated with the application and one again the file was instantly opened in a new window. This time the window was the “Oxygen Forensic SQLite Viewer,” which is very similar to the Plist viewer. Once again the user interface was straightforward, including having the raw data displayed at the bottom and common encodings on the right. This made it incredibly easy to identify timestamps in fields.
I noticed a “Recover Deleted Records” button at the top of SQLite Viewer, so of course I had to press it. It only took around a second to run and found four deleted records in one of the tables.
As I stated earlier, most forensics tools parse the popular apps, but many of them require the use of other tools to parse third party apps that aren’t supported. DETECTIVE has very well designed tools included to analyze such apps. Using these built in tools, I navigated to an unsupported app and was able to easily examine the sqlite and plist files to find the entire history of search terms typed into the app, all of the items browsed in the app, relevant time stamps, etc. Once again, the functionality felt very well thought out instead of having been an afterthought.
Oxygen has several different forensic product tiers, and DETECTIVE is at the top of their tier list. One of the features DETECTIVE offers that their other products do not is “Cloud Data Extraction.” Cloud data has been a topic of discussion on several forensics mailing lists that I’m a member of. How useful it is depends largely on what type of work you do and how often you have the opportunity to legally acquire data from cloud services. I wanted to give it a try so I clicked the “Clouds” button in the upper right.
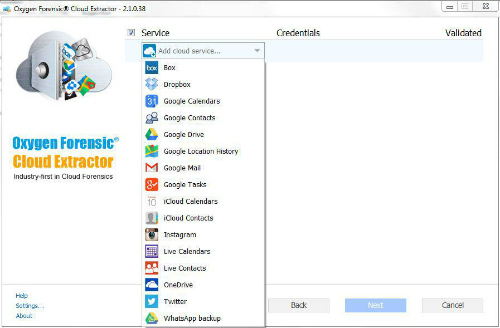
The two methods for obtaining cloud data are to enter the credentials for the various services or to acquire cloud credentials from an Android device. I entered credentials for a cloud service. DETECTIVE had data parsed within a few minutes and added the data obtained to my “test1” case with the three devices that I had previously examined. The cloud data had a similar user interface as the phone data, including a timeline, social graph, aggregated contacts, etc.
DETECTIVE offers several other tools, including maps and the ability to import call data records from cell phone service providers. While I wasn’t able to fully test the call data records tool, I made a quick dummy CSV file. The import process appears to be a fairly manual one designed to parse .xls or .csv files after the examiner identifies the fields.
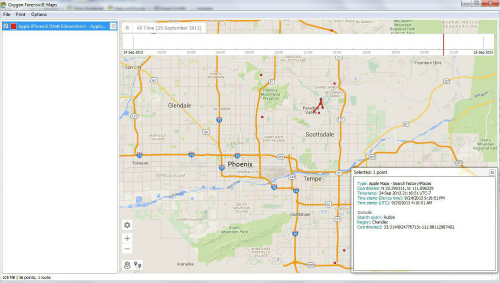
I was able to test the mapping feature and generated individual maps from things like fitness apps or where I googled for my favorite BBQ place in Phoenix. These maps can be viewed on Google Maps or exported to a KML file.
While most examinations nowadays are of smart phones, examiners are still sometimes asked to examine cheaper, less functional “feature phones.” With the amount of new devices being released every month, no mobile device forensics tool can acquire data from every phone, and Oxygen Forensics DETECTIVE is no different. While their website claims it supports over 11,170 devices, I tried to examine three cheap “feature” phones and was unable to connect to or acquire data from any of the three devices. This didn’t raise any huge red flags for me, as many tools struggle with the variety of feature phones on today’s market, but I wanted to mention it. Feature phones usually contain far less data than smart phones, but it’s always nice when your tools parse that data and report it for you instead of having to go through a device by hand.
In addition to the traditional methods of acquiring data, DETECTIVE provides quite a few import methods for examining data acquired from device backups, other tools or from JTAG/chip-off acquisitions.
This last feature of DETECTIVE may be my favorite. When I started to examine my devices (and my cloud), I created a “test” case folder in the tool and assigned each of my acquisitions to that folder. In addition to being able to examine devices individually, DETECTIVE has an “Analytical Tasks” button at the top, which opens several tools that examine all devices in a case.
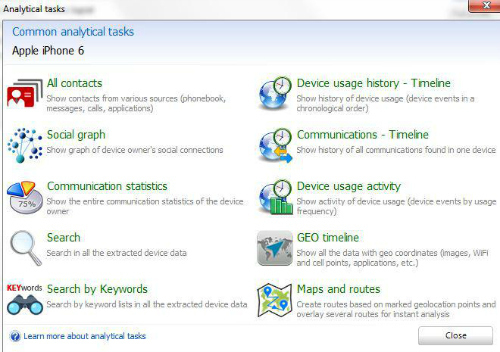
This toolset allows for incredibly powerful analysis, such as timelines, to see what communications or other activities were occurring at specific dates and times across multiple devices. Contacts and Social Graphs can also be analyzed for all devices within a case.
When examining an individual device, I thought DETECTIVE’s mapping capabilities were good, but not great. However, once I opened up the Analytical Tasks window, I found exactly what I was looking for. Analysts can create a “Geo Timeline,” which looks at things like app data, image metadata, etc., to create a timeline of what devices were where during any timeframe. Users can also create maps that contain all map-able data from devices within a case.
In summary, I didn’t have much experience with Oxygen Forensics products but ended my trial a big fan. The intuitive nature of the software and its robust features, specifically the social link charting and multi-device analysis, make it an easy choice for professional examiners. If a majority of your examinations are of smart phones, and these features sound like they would benefit you, I would definitely look into the Oxygen Forensics line of forensics products.
To find out more about Oxygen Forensics' DETECTIVE and order a copy, visit their website.
Matt Edmondson performs technical duties for the U.S. government and is a Principal at Argelius Labs, where he performs security assessments and consulting work. Matt’s extensive experience with digital forensics includes conducting numerous examinations and testifying as an expert witness on multiple occasions.
A recognized expert in his field with a knack for communicating complicated technical issues to non-technical personnel, Matt routinely provides cyber security instruction to individuals from the Department of Defense, Department of Justice, Department of Homeland Security, Department of Interior, as well as other agencies, and has spoken frequently at information security conferences and meetings. Matt is a member of the SANS Advisory Board and holds 11 GIAC certifications. Among them: GREM, GCFA, GPEN, GCIH, GWAPT, GMOB and GCIA.