Reviewed by Jonathan Krause of Forensic Control.
Helix 3 Enterprise (H3E) is e-fense’s flagship investigation suite pitched at a similar level as EnCase Enterprise or Access Data Enterprise. It’s aimed at organisations which need to be able to carry out incident response, forensics and e-discovery functions over networks. H3E facilitates centralised incident response, imaging of drives and volatile data and also enables scans and searches of a user’s internet history and documents on any computer which has had the H3E Agent pre-installed on it. The integrity of data in transit and within the H3E database is ensured through 256-bit AES encryption.H3E’s main differentiator from its competitors is on price and ease of use. Whether this product is financially viable for your organisation is for your personal assessment, as in my experience the prices of such enterprise class products are seldom fixed, being based more upon the individual circumstances in which they are going to be used. So rather than examine value for money, this review focuses on the usability of the product and how well it achieves its stated goals. I was given a time-limited trial version of Release 1 of the 2009 Version of H3E which I tested on a Windows platform.
Install
The main thing I liked about H3E was its relative simplicity in use, and this was certainly true of the installation process. H3E consists of three separate elements (the Agent, the CAT and the Server) each taking less than a minute to install. The Agents sit on the target computers and need to be installed pre-incident if your desire is to maximise the amount of data available for analysis and to minimise any contamination issues which may arise. The other two elements which make up H3E are the Server and the Console Administration Tool (or CAT for short). The H3E manual describes the Server as “the system’s headquarters” and the CAT as “the command centre” which seem to me to be very similar functions. I wonder if e-fense could simplify things for the end user by combining the Server and the CAT into a single install process; additionally I see no benefit with invented names to describe old functions; just Agent and Server would seem to be perfectly simple and self-explanatory. The instruction manual reminds you that to ensure you are running the latest version of H3E you should visit h3e.e-fense.com to find up to date downloads but unfortunately at the time of writing this review this resulted in a ‘404 Page Not Found’ error.
The Agents can be installed in a number of ways including through the use of applications such as HP OpenView or PSExec. I installed the Agents manually, which obviously requires physical access to the target machine and an account with administrator-level privileges. Double clicking on the Agent installer package quickly completes the install; I feel options here to rename the default service name (h3e-sma) and to define ports to those of your choosing would be welcome. The CAT installer politely asks where you want the shortcuts to be placed but the Server installer once double-clicked requires no input and finishes rather abruptly with no indication that it has finished or installed correctly.
I was impressed that the H3E Server and CAT can install on Windows, Mac and Linux boxes which gives administrators a good choice of what they can run it from but was less impressed that the Agent can only be run on Windows (post Windows 2000) boxes. Organisations running desktop Macs or Unix derivatives will need additional solutions.
There is a very informative chart in the manual laying out the minimum and recommended specs for running the Agent, the CAT and the Server but as the pdf manual is password encrypted and does not allow extraction of contents unfortunately I’m unable to reproduce it here. However I can say that the minimum requirements for Agents are a Windows 2000 operating system or later, a 400 MHz Celeron processor or equivalent, 256MB RAM and 10MB free disk space. The Server and CAT components would obviously benefit from being on more powerful boxes with the fast network interface.
Use
On starting the CAT, the first thing which struck me was the quality of design of the interface, how easy it was on the eye, its responsiveness and how well it was laid out. A real pleasure to use.
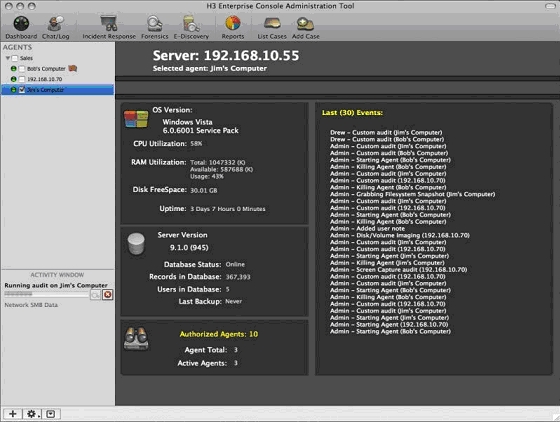
The pleasing interface to the H3E CAT
Once the Agents are installed (keep in mind that you must configure any firewall and the like on your target machines to let the Agents communicate with the CAT and the Server) they should automatically appear under the ‘Agents’ portion of the CAT GUI, on the left in the illustration above; I only knew this (and that I didn’t need to do anything to ‘make’ them appear) after a call to technical support. For me this part is a fundamental part of the application which should really be covered in the manual.
Once the agents were showing that they were available I was able to properly test the capability of H3E. Generating reports including such information as contents of the setipapi.log, screen captures, installed applications, clipboard contents and so on was very straightforward. The key logging capability could also be very useful although I could not find any information as to how much could be stored and what happens when the key logging capacity is reached. Testing the key logger produced the results exactly as I expected but one drawback is it cannot record Unicode characters – for example a simple sentence in Japanese characters typed in on the target machine was recorded on the CAT as ASCII characters.
Accessing the file system of a target machine was very straightforward. The file system hierarchy is viewed via the right window pane within the CAT console (see illustration below) which is spilt into two, the left first section is the hierarchy itself (in a narrow window which you can’t expand, meaning a lot of left and right scrolling) and the other pane shows the contents of each folder. Right clicking on any file allows you to ‘download’ it to your machine where you can examine it using the built in hex viewer, or go to the file itself and analyse it using your tools of choice. H3E allows you to examine the file’s properties, however the MAC times given are those of the file once it arrived on your machine– the MAC times on the client machine are viewable but rather frustratingly it’s not clear how or indeed if these MAC times can be copied over to your report.
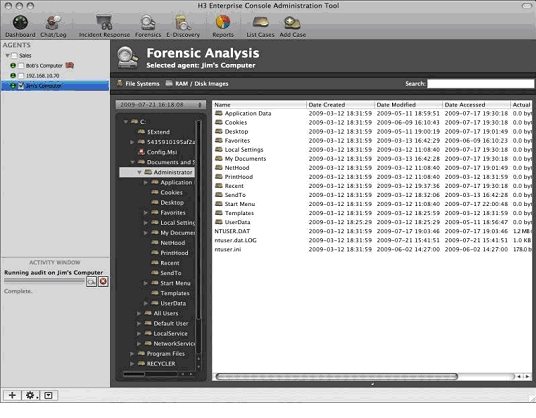
Viewing a remote file system
H3E allows for the imaging of RAM, volumes and physical disks, although the imaging of physical disks is not recommended over a network. Instead, H3E’s many tools can help the investigator pinpoint which machines on the network could be candidates for ‘traditional’ imaging techniques. I tried imaging a remote machine’s RAM contents over the network which worked well; the data stream is encrypted by default which I would imagine adds some overhead to the process. When imaging the investigator can select which port to image over, the image file segment size and the maximum speed you require. What isn’t immediately clear is whether the image file format is to be in EnCase E01 or dd format. During my testing I imaged 2048MB of RAM over a gigabit network where I found the average transfer speed to be approximately 355KB/second; you can see why imaging a whole physical disk using this technique is not recommended.
Another impressive feature of H3E is its search function; it allows for searches by keyword, MD5 hash or by regular expression, all of which can be filtered by date range and also de-duplicated. In my testing in this area the results were returned impressively quickly with corresponding target machine MAC times. The results can then be exported in pdf format, which is very clearly laid out.
Customer Support
My call to e-fense technical support, as touched on above, was prompted by the fact that I followed the available instructions and waited a long time for the available agents to appear in the CAT, and nothing appeared, despite ensuring the Windows Firewall was off and that there were no other security applications in use. Re-boots of the machines with the Agent and CAT on yielded no success either. The process of populating the Agents list came across as rather haphazard and wasn’t helped by the lack of documentation; indeed the ‘Help’ button within the program itself was not that useful as it only contains a link to the pdf manual. The manual itself contains the following ‘if you are unable to find the solution you need, please contact Customer Support at http://fogbugz.e-fense.com/ with a detailed explanation of the issue or request’. However this is another link which leads to a 404 ‘Page Not Found’ response.
The e-fense web site states that additional support is available for Helix3 Enterprise customers Monday – Friday 9:00 AM – 5:00 PM MST, which means that support won’t be available in London until 3pm and not until 4pm in mainland Europe. However I do know that there is support based in England, which at the time of writing is one person. On trying to get a solution to my problem this person happened to be on holiday in America, and although he did do his best for me despite the time differences, accessing help was a bit more of a struggle than I expected with an Enterprise-class product.
Conclusion
Helix 3 Enterprise is a very well designed product which gives the examiner easy access to a wealth of important data from remote machines pre-installed with the Agent. However I felt let down by the content of the manual and the availability of the support, which should be first class considering that it is mandatory to buy the support package. The lack of checking the erroneous content of the manual carried over to a lack of proof-reading in the application itself, such as under the Agent Configuration screen you are told ‘This shows the list of machines that are going to configured’. I felt that this application came across as having something of a ‘beta’ feel about it as it’s evident that it has not been thoroughly and independently tested. H3E is almost there but it does require further refinement. I’ve been informed that support will improve with e-fense setting up an 0800 (toll-free) number for the UK, and equivalent numbers for other countries where they have H3E customers that will route the call to the most appropriate location for that time of day. Also e-fense apparently now have two additional support people in the UK who will receive calls during the day, ensuring that customers will be able to reach a person quickly, until early afternoon when e-fense’s American head office takes over until late evening UK time.
Pricing
Pricing is on application, but it is understood that H3E is priced very favourably in comparison to EnCase Enterprise or AccessData Enterprise.
If you are interested in purchasing H3E or have any questions about it please contact Bright Forensics:
Web: www.brightforensics.com
Tel: +44 (0)845 224 5538
This review can be discussed here.
Review written by Jonathan Krause of Forensic Control.
Based in central London but working throughout the United Kingdom and beyond, Forensic Control provides computer forensics services to the legal and accountancy professions, corporate clients and private individuals.
Web: www.forensiccontrol.com
Email: info@forensiccontrol.com
Telephone: +44 (0)207 19 333 24