
From voice note analysis to digital DNA and laser scanning, this year’s Forensics Europe Expo highlighted the tools and techniques shaping tomorrow’s investigations.
As the pace of technological change accelerates and threats evolve, the world of forensic science is undergoing a seismic transformation.
From AI-driven investigations to real-time data recovery and smarter emergency response coordination, Forensics Europe Expo (FEE) 2025 is set to bring the global forensics community together at Olympia London on 18-19 June.
Now in its 12th year, FEE 2025 promises to be a landmark event, co-located for the first time with The Blue Light Show, the UK’s only exhibition dedicated to emergency services interoperability.
This co-location creates a powerful platform for law enforcement, government agencies, academia and the private sector to collaborate, innovate, and shape the future of public safety and forensic investigation.
Thousands of delegates are preparing to attend this unmissable event, free to attend for those who register in advance.
Cybercrime, digital evidence and emerging technologies are now central to forensic investigation. Reflecting this shift, FEE 2025 will feature a strong emphasis on digital forensics, with a series of sessions designed to help professionals stay ahead of rapidly evolving threats.
Attendees can expect deep dives into topics such as:
These sessions provide real-world insight into the tools, techniques and technologies that will define the next generation of forensic investigation.
The FEE 2025 conference programme brings together a line-up of experts across academia, law enforcement and industry. Among this year’s high-profile speakers:
From traditional techniques to emerging science, these sessions offer a vital opportunity to learn, question and connect with the field’s most respected thinkers.
For the first time, Forensics Europe Expo will be co-located with The Blue Light Show, creating an expanded ecosystem of knowledge sharing and collaboration across emergency services.
This co-location reflects the growing emphasis on interoperability between frontline responders and forensic teams. FEE 2025 attendees will have full access to six theatres and five content streams at The Blue Light Show, including:
From police to fire, ambulance to rescue services, the show brings together the entire emergency response chain. It’s a chance to better understand how evidence and insights from forensics are being used in live, high-pressure scenarios and how closer collaboration can lead to faster decisions, smarter strategies and ultimately – saved lives.
Beyond the conference sessions, FEE and The Blue Light Show will feature over 100 exhibiting companies showcasing the latest innovations in:
Attendees will have the chance to evaluate new products, meet directly with suppliers and discover tools that can improve accuracy, efficiency and courtroom outcomes.
Join us 18-19 June 2025 at Olympia London for Forensics Europe Expo 2025.
by Si Biles, co-host of the Forensic Focus podcast
What do JFK, the most powerful battleship of the Victorian era, unexploded World War Two ordinance and cremated pig bones have in common? Can’t guess? No great surprise unless you attended the Leica Geosystems conference this year – I went, and even I’m still not entirely sure how we covered such a range!
This year’s “Public Safety & Forensics Conference” was hosted at the National Museum of the Royal Navy in Portsmouth. Marcus Rowe, Leica Geosystems Director of Public Safety and the conference organiser, appears to be the embodiment of continual improvement – having taken previous feedback from earlier years (hosted at Red Bull F1 last year…) and secured an excellent lecture theatre with comfortable seats (to handle a previous year’s “numb bum” feedback) and superb catering (OK, I’m a sucker for a mid-morning bacon sandwich). He also scheduled an excellent range of topics and speakers over the two days (earlier than usual this year at the end of February).
It’s a full-on two days – with eleven speakers filling the schedule and registration opening at 0830hrs each day. The most astonishing thing to me though is that this is a free event. Yes, it’s the Leica Geosystems (LG from here on for my sanity) conference – but there’s no hard sell. The only talk given by an LG employee (Dan Prewitt) actually had little to do with the products that they sell – focusing on Evidential Storytelling and leaning in to true geekdom by using Lord of the Rings as an opening example! LG had some of their equipment in the small exhibition area outside – and it is immensely impressive technical kit – but the ethos here is about knowledge transfer.
The community that comes together is highly varied, but there is one common theme, which is that these are people who deal with hugely complicated real-world scenes. They range from the criminal investigators working crime scenes, to fire and crash investigators dealing with charred and crushed remains, geospatial-intelligence consumers, academics and trainers.
Slides from the presentations are not made available – this is a conscious decision, and I wholeheartedly support it. These aren’t academic papers – like they are at DFRWS, for example – and therefore the presentations are much better appreciated live. LG are about creating community, so just downloading another slide deck would miss the point.
It was a welcoming and open atmosphere; I think that this was particularly evidenced by the fact that there were two speakers who gave their very first public talk here. I wouldn’t have been able to tell if they hadn’t said, and the audience were universally supportive. I note that, so buoyed up by her success here, Fran Peacock – after her excellent and admirably geeky talk, complete with Terry Pratchett references – spoke again barely two weeks later at the National CCTV Conference (at which she also acquitted herself admirably!).
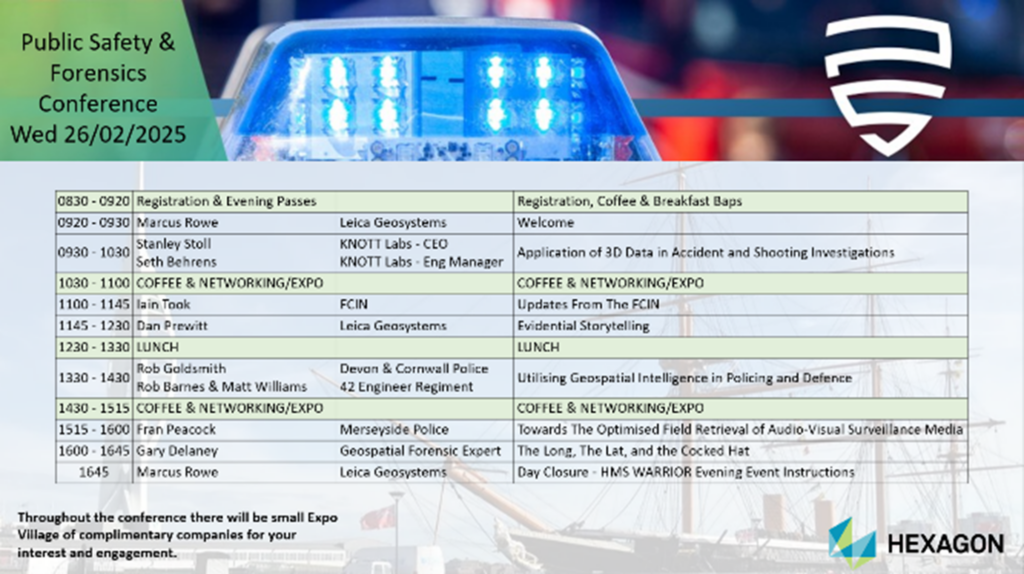
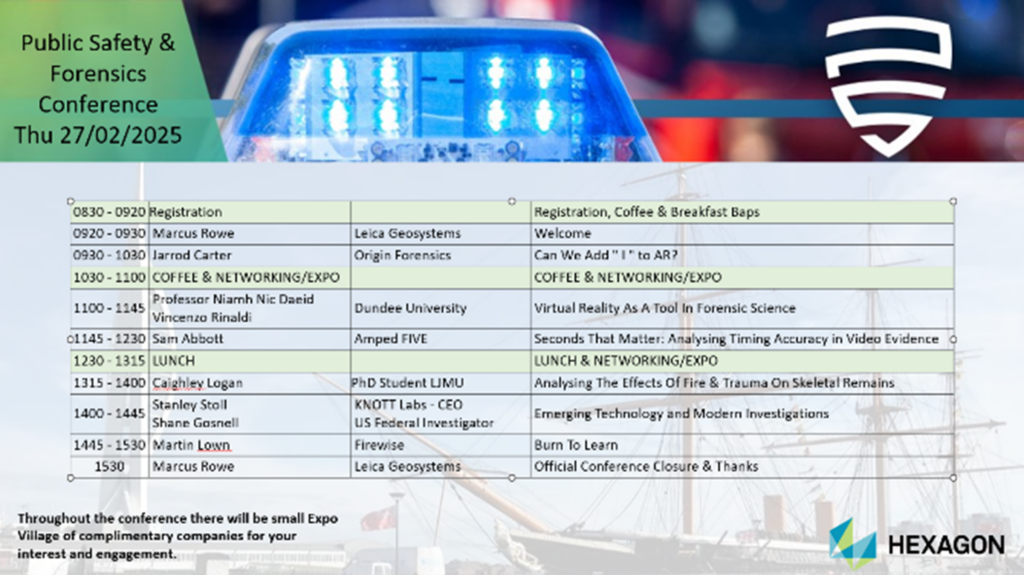
It’s tempting on the one hand to call out each and every speaker, as there genuinely wasn’t a single one that didn’t educate and entertain me – and to that end, I’ve included the schedule above – but I am going to shout three more on top of Fran and Dan and our good friends at Amped, represented ably by Sam Abbott talking on timing accuracy in video, as examples of the breadth of topic that was on display:
Firstly – Gary Delaney’s talk on “The Long, the Lat and the Cocked Hat” was a fascinating dive into both naval history (starting with us being piped with a bosun’s pipe!) and the GPS systems and evidence used in a large drug running case.
Secondly – Jarrod Carter’s talk on “Can we add ‘I’ to ‘AR’ ?”, which looked at the implications of machine learning on accident reconstruction (AR). This was the best talk on the way that AI/ML works and the pitfalls of it that I’ve ever seen – and I’ve given some – so I walked away with tips and tricks there!
Finally, but by no means least – Caighley Logan discussed “Analysing the Effects of Fire & Trauma On Skeletal Remains”. I had skipped lunch on the second day, as I opted to go for a walk around some of the museum in lieu of food. I was secretly quite glad that I did, and I don’t think that I’ll ever look at barbequing a piece of pork in quite the same way again.
Marcus secured HMS Warrior for the evening – no mean feat being an 1860s frigate – and the most fantastic entertainer. With his sharp wit, encyclopaedic knowledge of the ship, and skills with a mandolin, our compare – Martin Jakeman – was absolutely brilliant.

There is a wonderful truth about mass singing that – on average – people can follow a tune. Those singing sharp are cancelled sufficiently by those singing flat, those ahead are cancelled by those who are behind, and – in sea shanties – no one actually cares anyway.
Martin in his nom de guerre as Commander Tryon (who in reality, in June 1861, was selected to become the second in command on HMS WARRIOR) led, and Marcus encouraged, us in increasingly loud if not increasingly competent shanties – my personal favourite, and probably the globally best known, “What shall we do with the drunken sailor?” is a memory that I will never forget.
Having opened with JFK as click bait, it would be remiss of me to leave the reader unsatisfied as to the connection. The very final talk, of the final day, was on additional research carried out on the JFK assassination. Using the same tools we’d been discussing over the previous two days and bringing the weight of modern science to bear on the matter, we had a small preview of future work given the additional material now coming to light. This is the second year that this topic has come up – with enhancements each year on the additional research – so I’m in for next year to see if it really was an alien conspiracy.
I’m going to close simply with: I don’t know how Marcus is going to outdo himself next year – but I can’t wait to find out, and I hope to see you there!
The Techno Security and Digital Forensics Conference returns to Wilmington, North Carolina June 3-5, with top-tier speakers and educational sessions covering the latest technology and developments in Cybersecurity, Digital forensics, eDiscovery and Investigations.
Jennifer Salvadori, Event Director, adds: “In addition to the educational program of over 100 sessions, we are excited to host T-Warz, a live cyber incident response CTF. For the second year, Cyber5W and The Leahy Center for Digital Forensics and Cybersecurity at Champlain College are sponsoring and partnering with Techno to put together this exciting challenge for attendees to participate in.”
Take a glimpse into what Wilmington has in store for you within the Techno East conference program this year. The full conference program can be viewed here.
Kicking off the conference at 8:00am, Tuesday, June 3th, Erin West, Founder of Operation Shamrock will present Disrupting Transnational Crime and Protecting Victims. During this engaging talk, Erin will uncover the dark world of ‘pig butchering’ scams—sophisticated schemes run by global criminal networks that exploit victims through manipulation and financial deception.
LEAPP Forward: Unlocking the Power of Open-Source Forensic Analysis: Alexis Brignoni, Special Agent with the Department of Justice, and Heather Charpentier, Computer Forensic Analyst with the New York State Police, will provide an overview of each tool in the LEAPP suite, highlight their specialized capabilities, and share practical examples of artifact extraction and analysis.
Sysdiagnose Logs 101: Kim Bradley, Digital Forensics Content Lead, Hexordia covers the plethora of details examiners may be missing in Sysadiagnose Logs and explores how to generate these logs and examine the data within them.
Encryption Nuts and Bolts: This hands-on lab with Bob Osgood, Director of Digital Forensics and Cyber Analysis Programs, George Mason University, will discuss how to use encryption with AES and RSA algorithms ubiquitous, and how these algorithms actually work and why they are important.
Living Off the Land and Emerging Threats, with speaker Robert Main, Cybersecurity State Coordinator (NC) DHS – CISA | IOD | Region 4 | Cybersecurity Branch, provides a concise yet comprehensive overview of the methodologies employed by nation-state threat actors to infiltrate, persist, and operate within targeted environments undetected.
The Future of Network Security: Trends and Predictions: Jennifer Minella, Security Architect – Viszen Security, will explore the current and emerging technologies shaping network security, from AI-powered threat detection to the convergence of wired, Wi-Fi, and cloud-native security.
Staying Ahead of Cybercriminals: Generative AI and the New Era of Financial Fraud presented by Michele Boland, Global Technologist, Check Point Software, will help attendees understand the threat landscape and gain insights into how cybercriminals are leveraging Generative AI, including deepfakes, to execute sophisticated financial fraud such as CEO/CFO impersonation and electronic fund transfer schemes.
The Critical Role of Metadata in Solving a Complex Child Exploitation Case: Chad Gish, Forensic Consultant, Magnet Forensics, shares a case study that exemplifies the crucial importance of metadata in forensic investigations and demonstrates how a single, deleted digital artifact can be the breakthrough needed to bring justice and prevent future harm to children.
Calling All Digital Forensics Examiners: Outsmarting Anti-Forensics: Caroline Cappy, Digital Forensics Examiner, Portland Police Bureau will share practical insights and creative techniques used in real law enforcement cases to tackle anti-forensic methods, uncover hidden evidence, and piece together a complete picture of the investigation.
Are You on the Blockchain Train? with Eugene Cunningham, Technical Engineer, MSAB, looks at the fundamentals of blockchain technology and its integration into mobile application development. This presentation will explore how blockchain extends beyond cryptocurrency, powering non-crypto applications, and examine the unique security challenges it introduces for forensic analysis in mobile apps.
The Intersection of AI, Forensic Readiness, and eDiscovery: Preparing for the Future of Litigation, led by Monica Harris, Principal Consultant, Consult Harris Collective (CHC) and Jerry Bui, CEO, Right Forensics. This session will explore how organizations can integrate AI tools into their forensic and eDiscovery workflows to streamline processes, enhance efficiency, and uncover deeper insights—all while maintaining compliance and defensibility in legal proceedings.
What Happens Next? Using eDiscovery Tools and AI to Tell the Rest of the Story: This panel of eDiscovery experts will explore the AI and eDiscovery tools and processes that are used to analyze forensic data and reporting. Attendees will learn about eDiscovery methodologies in collecting data, the pros and cons of using AI tools, and how it impacts the “ROI.” Speakers include: Bree Murphy, Sr. Solutions Consultant, Exterro/ eDiscovery Chicks and Laura Anne Day, Area Sales Director, Epiq.
The Challenge of Hyperlinked Documents in E-Discovery: Hyperlinked files, sometimes referred to as “modern attachments,” are turning up in legal and technical environments, and they are causing headaches for e-discovery, information governance, and forensics professionals. This panel discussion will explore the challenges and potential solutions related to hyperlinked documents. Panelists include: Michael Quartararo, President, Association of Certified E-Discovery Specialists (ACEDS), Robert Fried, SVP Forensics & Investigations, Sandline Global and Ignatius Grande, Director, Berkeley Research Group
A Beacon in the Darkness: Navigating Cryptocurrency Investigations with Ryan Griffith, Director, Financial Investigations & Advisory , Outrider Analytics, will provide best practices and a look into how to investigate cryptocurrency using publicly available information as opposed to paid blockchain analytics services.
Uncovering the Hidden Truth Case Study: Dark Web Marketplaces & Child Exploitation with speaker Melissa A Maranville, Founder/CEO DeVille and Associates LLC, will review the use of cyber technology, focusing on cryptocurrency, clear and dark web data, and OSINT (open-source intelligence), with a special emphasis on child exploitation on the dark web.
Deep Space – Private Space in Android 15 with Dan Dollarhide, Director of Global Solutions, Oxygen Forensics, Inc. will discuss the nature of this new feature and how it can affect mobile device investigations.
The full conference line up of 120+ sessions and product demos, including the above and tracks from the four Titanium sponsors (Cellebrite, Magnet Forensics, MSAB and Oxygen Forensics) can be viewed here: https://www.technosecurity.us/east/conference-program/2025-program.
Forensic Focus members who attend will receive a 10% discount on their registration. To access the discount (not valid on already reduced government rates), enter Promo Code FOR25 during the registration process.
The Techno Security and Digital Forensics Conference returns to the Pasadena Convention Center in Pasadena, CA September 16-18, 2024.
The conference includes over 70 educational sessions and sponsor demos covering the latest technology and insight in digital forensics, cybersecurity, investigations, and e-Discovery.
Event Director Jennifer Salvadori let us know that “The speaker lineup this year features experts from Adobe, Amazon, Microsoft, FBI, US Secret Service, Cellebrite, Magnet Forensics and more.”
Artificial Intelligence features prominently in the program, headlined by a Keynote dedicated to the topic. The program also includes discussions on other key subjects such as cryptocurrency, mobile app and Mac forensics, the dark web, and OSINT.
Attendees will have the opportunity to engage with over 25+ leading vendors on the expo floor. The companies will showcase a diverse array of technology and innovations that attendees can utilize to streamline productivity in their daily work flow.
Here’s a look at some of the topics covered in the program at Techno West:
On Tuesday, September 17, Roman Yampolskiy, Ph.D , Futurist, Author, Professor, University of Louisville, will deliver the keynote, Navigating The Artificial Intelligence Era: Challenges and Strategies for Future of Cybersecurity. During this powerful keynote, we will look at the future of cybersecurity in a world dominated by AI and will discuss the paradox that AI will bring for cybersecurity. He will share how cybersecurity experts can prepare to address the impact from AI in the context of AI safety and security.
Melissa Kimbrell, Amped Software USA, will present: AI Image Synthesis Detection: Unveiling the Limits of Realism with Shadows and Reflection Analysis, where she will share image generation works and how to analyze shadows and reflections to aid in identifying these kinds of deepfakes.
Panel discussion with top leaders in AI will lead Generative AI Growing Pains and discuss the challenges with AI and share the recent Ponemon Institute’s Cost of a Data Breach study.
Unveiling the Hidden: Navigating the Maze of AI Artifacts in Windows Forensics with speaker Anna Truss, Founder / CEO, DefSec LLC, will focus on the challenges of finding AI traces in Windows systems from a digital forensics point of view.
Unmasking the Deepfake: Detecting AI-Generated Video with Chester Hosmer , CEO, Python Forensics and Julie Lewis, CEO, Digital Mountain, Inc. includes a walkthrough of an actual deepfake video and demonstrates how to detect a manipulated video through forensic analysis techniques and emerging AI-driven detection algorithms.
“3 Under Par” Daniel Bowling Case Study, with speakers Roo Powell, CEO and Founder of SOSA (Safe from Online Sex Abuse), and Jennifer Wing, Detective/Task Force Officer, Orlando Police Department/FBI Violent Crimes Against Children and Human Trafficking Task Force, Tampa Division, share how one ICAC case turned into an episode of the docuseries Undercover Underage.
Cryptocurrency Investigations, Pig Butchering presented by Kyle Krueger, Network Intrusion Forensic Analyst, Los Angeles Field Office, United States Secret Service, will give insight into investigations involving the illicit use of digital assets and cryptocurrency, to include pig-butchering and romance scams.
Nicholas Phirippidis , Special Agent, FBI Sacramento, FBI, will discusses “Operation Bayonet”, which was the international effort to dismantle AlphaBay. AlphaBay Market was a Tor-based darkweb market which was the largest in history—featuring hundreds of thousands of listings, including fentanyl, weapons, poisons, and other illegal materials.
Digital Forensic Stories from the Frontline, with Felipe Chee, District Attorney Investigator, San Diego County District Attorney’s Office – attendees will hear actual cases of how digital forensics played a role in homicide investigations. From recovering deleted video to cached data, phone being powered down, smartwatches and how cookies show evidence of app usage.
Unraveling Hidden Clues and Protecting the innocent in Crimes Against Children Investigations led by Page McBeth, Customer Success Manager, USA West – Cellebrite will discuss investigative techniques and best-practices in Crimes Against Children Investigations.
Melissa Maranville, Founder/CEO, DeVille and Associates, LLC will review use of cyber technology, looking at cryptocurrency, surface and dark web data, and OSINT (open-source intelligence) will be discussed in the session, Linkage Investigations: Cryptocurrency, Dark Web & OSINT.
The Dark Web Has Changed Investigations presented by Todd G. Shipley, President, Dark Intel will discuss how investigators need to rethink approaches to these investigations.
Pondering the Perplexities of 3D-Printer Evidence presented by Chris Vance, Senior Technical Forensics Specialist, Magnet Forensics will show examiners how to trace the path of finding 3D-print model files, the software used to prepare and print those files, and artifacts to show the printer’s history for the major operating systems in both computer and mobile including iOS, Android, Windows, and macOS.
Factory Reset’ed Phone, Game Over – Or Is It? From Martin Westman, Exploit Research Manager, MSAB explores scenarios where preventing the factory reset process is possible and examines methods for recovering certain artifacts even after a factory reset has been executed.
Don’t get WASTED: A look into the Wasted App with speaker Peter Phurchpean, Digital Forensic Examiner, Federal Bureau of Investigation, shares insights and research on the Wasted Application, from how it works to what data can be recovered once the application is activated.
Chris Groshong, President, CoinStructive Inc. will share a detailed and step-by-step account of how a team of investigators was able to locate a criminal suspect by using blockchain forensic tools, metadata from NFTs, and traditional OSINT methods, in the session: Locating Criminal Suspects by Tracking NFTs.
An Overview of Business Email Compromise Attacks with Robert E. Gaines , Director, Cybersecurity and Privacy Advisory, PKF O’Connor Davies will look at current tools and methodologies and how to leverage “off-the-shelf” products to perform investigations.
Jeff Stanton, Sr Incident Response Commander, Adobe, will discuss Rapid Response: Triage Collection and Incident Analysis for macOS and share critical techniques and tools necessary for rapid response triage and analysis on macOS devices.
Taming the Tide: Building a Scalable Vulnerability Management Program with Amazon speakers, Krishna Chirumamilla, Security Engineering Manager and Kashif Memon, will dive into conquering the challenge of vulnerability management by exploring methods for implementing a scalable program.
Join Angie Nolet and Bree Murphy, In-House Counsel and Sr. Solutions Consultant, respectively, by day and Co-Hosts of eDiscovery Chicks: the Podcast About All Things eDiscovery & Legal Tech by night, for an informative discussion about the interplay between eDiscovery and forensics in internal investigations.
Brett Burney, eLaw Evangelist, Nextpoint, presents Modern Attachments or Old-Fashioned Links? Navigating the Collection Challenges of Hosted Email, Cloud Storage, and Collaboration Platforms. This session will analyze the current approaches to “modern attachments” and discuss the current best practices for collection, review, and production.
The full conference program and speaker details can be found here: https://www.technosecurity.us/west/conference-program/2024-program
The conference kicks off on Monday, September 16 at 12:00 PM PT.
Forensic Focus members who attend will receive a 10% discount on their registration. To access the discount (not valid on already reduced government rates), enter Promo Code FOR24 during the registration process.
by Si Biles, co-host of the Forensic Focus podcast
Forensics Europe Expo again graced the halls of the ExCeL centre in the heart of London Docklands. Sharing exhibition space alongside the Counter Terrorism Expo on the 19th and 20th June, this was an opportunity for many familiar names – and a few new ones – to lay out their wares in front of an international audience.
Forensic Focus was there again this year, sharing the stand with Sophie Powell, one of the founders of CyberWomen Groups CIC. It was great to catch up with a number of podcast listeners and Forensic Focus users – thank you to all of you who came over to say “Hello !” – and it was nice to be able to point a few new starters to some resources on the forums to help them on their way!
It was interesting to hear about a number of people currently in “meatspace” forensic roles who are looking to transition into the digital realm, and this expo was a pretty good place to do so, with a vast majority of the forensics side of things being taken up with digital.
This year again we saw the excellent hosting skills of Professor Sarah Morris, who ran the event with her usual charm and flair – opening, closing and introducing the talks (which ran from 1000hrs to 1630hrs).
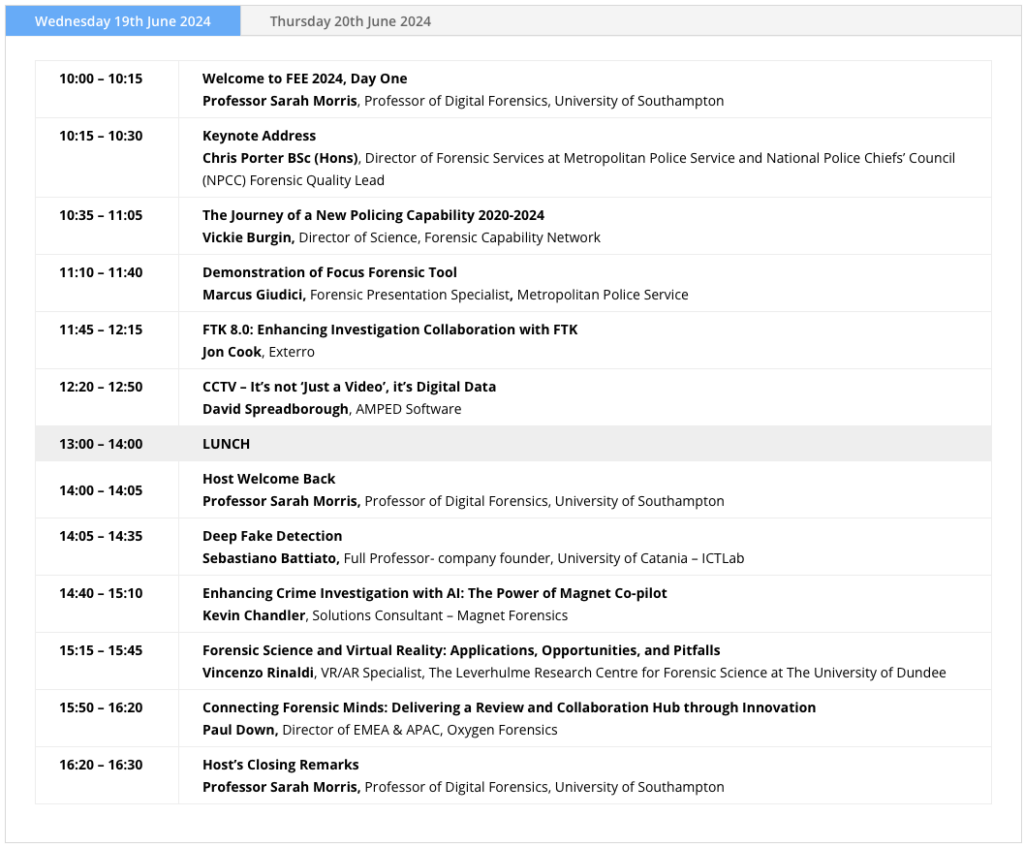
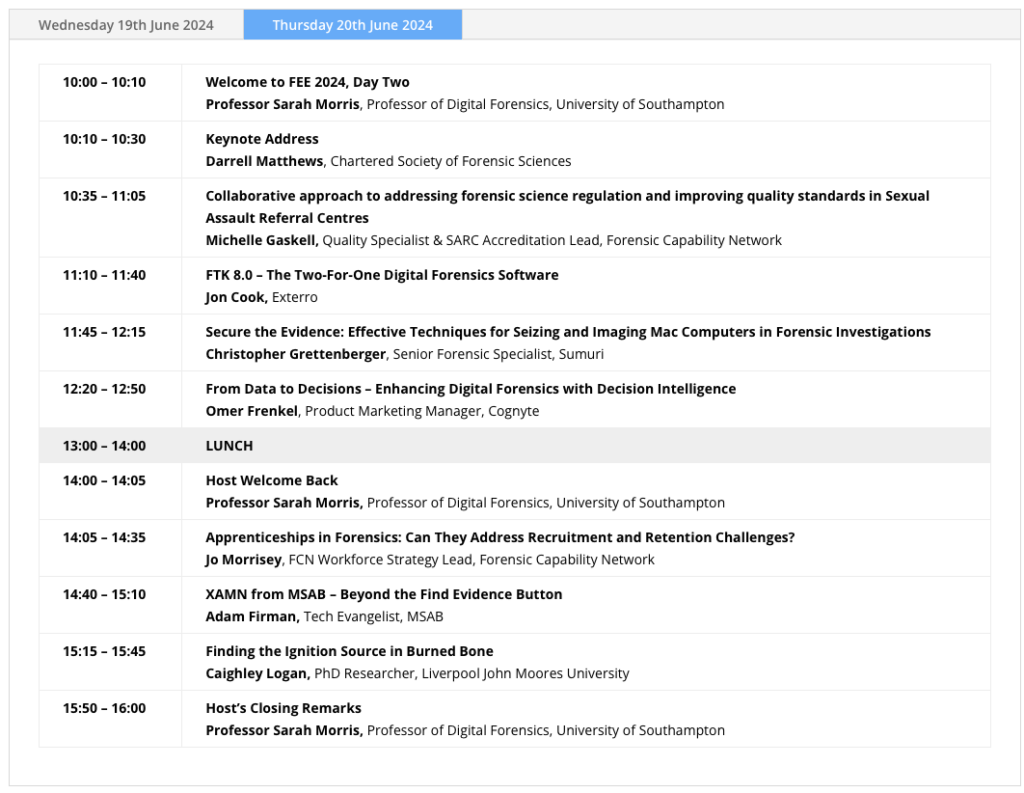
Owing to the footfall at the stand this year, I didn’t get to hear all that much of the talks – but it was great to hear David Spreadborough from Amped bringing “It’s not ‘just a video’, it’s digital data” to the audience, reiterating all the important points about the handling of CCTV evidence in his usual energetic way – which, having found out that he ascends parts of the Himalayas for fun, should come as no surprise!

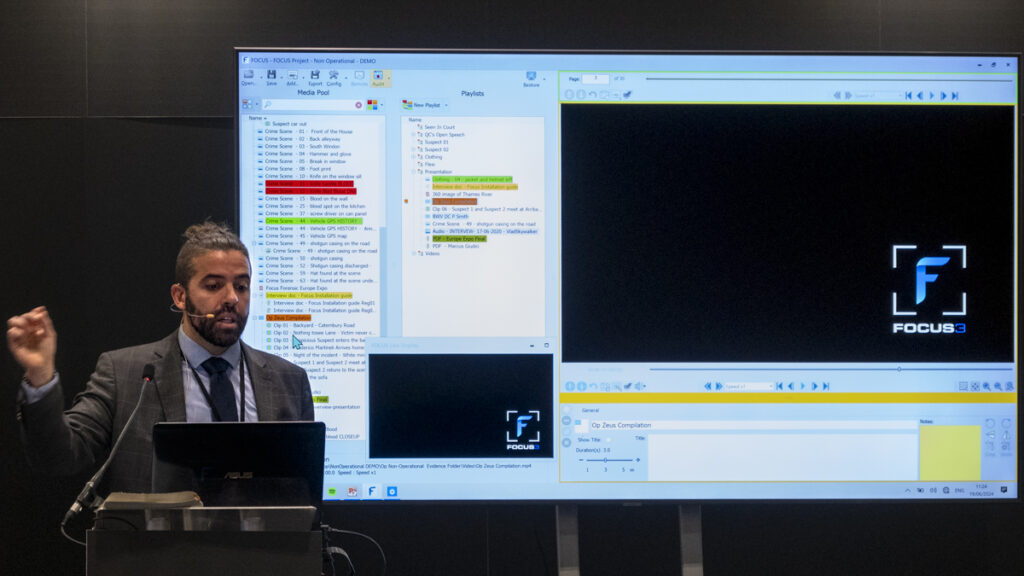
Another great talk was from Macrus Giudici from the Met on the Focus Forensic Tool. I’d been lucky enough to have a preview of this from him on the LEVA level 2 training a few weeks beforehand – and I hope that we’ll be able to bring him and an online demonstration to the podcast in the near future. Freely available to law enforcement in the UK, this video presentation tool is well conceived and well executed – making the delivery of image and video evidence in the courtroom a smooth and flexible process.
Walking the floor brought the usual incremental improvements that we know and love and that are the necessary lifeblood of the forensic software industry.
Leica Geosystems always brings toys that I covet, and this year was no exception – their new “MarvelScan” (lives up to it’s rather brilliant name creating 3d point models with an industry leading 0.02mm accuracy). I was told that the guys on the stand had only had it for two weeks and were still learning the ropes of everything that it could do – as I can’t seem to find it still on the website – I suspect that “bleeding edge” is probably a pretty fair assessment (although I wouldn’t want to suggest that it’s not production ready, it very clearly was). The level of detail that it was able to resolve was astronomical, but be prepared for getting some extra RAM if you’re not already full as the models are – understandably – huge.

There was also another company present whom I’d not heard of before – which is ironic given that they’re not actually terribly far from me at home – Oxford Wave Research. Taking from their website (https://oxfordwaveresearch.com), they are “specialising in audio and speech processing, voice biometrics and deep learning-related product development”, and they have a range of products as you might expect – a lot with rather interesting naming conventions “MADCAT”, “WHISKERS” and “TEAPOT” definitely stood out! The one that I found most interesting was “MADCAT” – which is a “content search, deduplication and time synchronisation system for audio and video files”. It has the nice feature of being “based on the principle that if two or more different recordings contain the same acoustic events, it is possible to search for and identify the parts of the audio that are overlapping and to provide a precise time of match” – basically, lining up clips on the basis of matching audio event. It’s a neat idea and seemed to work well in the brief demonstration that I saw.
The event overall had a good “vibe” to it – people were almost universally friendly and willing to engage, with some language (or possibly cultural!) barriers for overseas visitors probably explaining the cases where it was less so. It’s definitely livelier on the first days than on the second days I’ve attended over the last couple of years – as a visitor, there’s not enough there really to fill more than a couple of hours if you aren’t going to listen into the talks. I’d probably only dedicate a half day to visiting and make sure that you take a look at the talk program in advance to time that with things that you’d like to hear.
As an exhibitor, I’d definitely be prepared for the higher footfall to be on the first day, if you’re staff limited over the two days – more on the first, lighter on the second. It does die down before closing time, but there is a reasonable queue to get in waiting for the doors to open in the morning, so make sure that you’ve had your coffee and are raring to go.
Parking is easy and easy to pre-book, and the Elizabeth Line drops you at the front door – so getting to the ExCeL is easy – although I did hear a rumour that it might be hosted elsewhere next year – I have no confirmation of this so I’d wait for the official announcement if I were you! All other onsite facilities align with what you’d expect from a leading exhibition centre in London – a choice of food, plenty of washrooms, free WiFi and so on – although the pizza wasn’t as good as I remember it!
Keep your eyes out on the events pages for details of next year’s event, and I hope that I can meet many of you there.
Techno Security & Digital Forensics Conference wrapped up its 25th edition of the flagship East event last month after three days of education, networking, and exhibits. Returning to Wilmington for the second year, Techno East celebrated its anniversary edition with special events, including its first Capture the Flag competition, Scavenger Hunt in the exhibit hall, and full day hands-on workshops.
The event continued the celebration with a backyard “Family BBQ” themed party on the back lawn of the convention center, featuring live music from one of Wilmington’s own and lawn games for all attendees and sponsors to enjoy.
“We consider our attendees and sponsors part of our Techno Family” says Jennifer Salvadori, Event Director, Techno Security & Digital Forensics. “Some of our sponsors and attendees have been with us for all 25 years so it felt like the perfect way to celebrate.”
Tuesday morning kicked off the conference with a standing room only keynote, ‘Navigating the Artificial Intelligence Era: Challenges and Strategies for Future of Cybersecurity’, delivered by Roman Yampolskiy, Futurist, Author, Professor at the University of Louisville.
Over three days, the conference included 128 sessions led by 144 industry experts under the primary tracks of Cybersecurity, Forensics, Investigations, and e-Discovery. The conference also included three tracks from Titanium sponsors: Cellebrite, Magnet Forensics and Oxygen Forensics. Sponsor product demos were also featured. The educational program’s stand out topic was Artificial Intelligence, with sessions covering AI’s role in effecting children, litigation and deepfakes. Other key topics discussed were Dark Web & Cryptocurrency Investigations, Open-Source Intelligence (OSINT), Mobile Forensics and Mac Forensics.
This year’s program also included an increased amount of case studies led by law enforcement officials from a variety of jurisdictions. Hands on workshops also attracted a large crowd with topics of Mobile Analysis Methodology and 3rd Party App Analysis and Python – A Crash Course for DFE’s.
The event welcomed 895 verified attendees with over 53% being new to the event. Participants came from 42 states, the District of Columbia, and 29 different countries.
Jesper Eirup Sielemann, Sales Manager, DataExpert ApS, said: “Great event with all the relevant vendors and speakers. My first time, but not the last! An event that is a MUST for all.”
The event also featured an exhibit hall with 72 exhibiting companies which were: Ace Forensics ADF Solutions, AFOSI, Amped Software, ArcPoint Forensics, Atola Technology, AVAIL Forensics, Babel Street, BERLA, Binalyze, BlockChain Security, Casepoint, Cellebrite, Cyacomb Forensics, DATAPILOT, DeSales University, Detego Digital Forensics, Digital Intelligence, EVIDENT, Evolver, Exterro, Faraday Defense,
FileOnQ, Forensafe, Forensic Computers, Inc., G3 Technologies, The George Washington University, College of Professional Studies, GetData Forensics – Forensic Explorer, GMDSOFT, Hexordia / Cyber 5W EDAS FOX, IACIS, iPadRehab, LeadsOnline, LH Computer Services, Logicube, Magnet Forensics, Medex Forensics, Vespereye, MediaClone, Inc., mh Service, Mind Intelligence Lab, Monolith Forensics MOS Equipment, MSAB, Nuix, OpenText, Oxygen Forensics, Pagefreezer, PCi TEC, OSForensics by PassMark Software, PenLink, Raven, Scientific Working Group on Digital Evidence, SEARCH, The National Consortium for Justice Information and Statistics, SecurCube, DekkoSecure Skopenow, Sleuth Kit Labs, SMI Aware, Spyder Forensics Training, SUMURI, SysTools Teel Technologies, Cyber Social Hub, US Secret Service Charlotte Cyber Fraud Task Force, US Department of Health and Human Services – OIG, V2 Forensics, Virginia Tech – Master of Information Technology Programs, Vound Software, WGP – Wholesale Gadget Parts, and WiebeTech.
The 26th edition of the flagship Techno Security & Digital Forensics Conference East will be held June 3-5, 2025, at the Wilmington Convention Center in Wilmington, NC. For more information, please visit www.TechnoSecurity.us.
Techno Security & Digital Forensics Conference hosts two editions annually. After 20+ years in Myrtle Beach South Carolina, the flagship East Coast conference moved to Wilmington, NC in 2023. The West Coast location will hold its sixth edition September 16-18, 2024 at the Pasadena Convention Center. Both editions feature some of the top speakers in the industry, and will raise international awareness of developments, teaching, training, responsibilities and ethics in the field of cybersecurity, digital forensics and eDiscovery. Conference sessions cover a wide range of topics relevant to industry professionals and offer opportunities for discussion.
The Comexposium Group is a world leader in organizing events and animating communities around their businesses and passions. Comexposium organizes more than 150 events for professionals and the general public in more than ten business sectors (agriculture and food, retail and digital, fashion and accessories, leisure, and so on). The group puts 48,000 exhibitors in contact with 3.5 million visitors, 365 days per year. Headquartered in France, Comexposium’s employees and sales network operate in 22 countries. At Comexposium, our business is to create connections. Globally, face to face and digitally, we bring people together to meet and do business. Comexposium aims to be seen as the place to be, building bridges between people and business.
Allison Dowd, +1-201-247-4462, Allison.Dowd@TechnoSecurity.com
Jennifer Salvadori, +1-404-994-2919, Jennifer.Salvadori@TechnoSecurity.com
The Techno Security and Digital Forensics Conference returns to Wilmington, North Carolina June 4-6 to host its 25th Anniversary edition of the flagship East coast event. The conference maintains its tradition of delivering a top-tier lineup of topics and speakers in four primary content areas: Cybersecurity, Digital forensics, eDiscovery and Investigations.
Event Director, Jennifer Salvadori highlighted some changes to the event that have come about from both attendee and exhibitor feedback over the years:
“We have shifted to a full three-day event format, included more hands-on labs to the educational line up, and have added back in attendee lunches to be served in the expo hall.”
Salvadori reports that these changes, combined with hosting the first Techno CTF competition and a 25th Anniversary party, are just some of the additions event participants can expect to see this year.
Take a glimpse into what Wilmington has in store for you within the Techno East conference program this year:
Kicking off the conference at 8:00am on Tuesday, June 4th, Dr. Roman V. Yampolskiy, Futurist, Author, Professor will present Navigating the Artificial Intelligence Era: Challenges and Strategies for Future of Cybersecurity. During this keynote he will discuss the paradox that AI will bring for cybersecurity and share how cybersecurity experts can prepare to address the impact from AI in the context of AI safety and security.
Python – A Crash Course for DFE’s led by Robert Osgood, Director, Digital Forensics, George Mason University. This is a crash course in Python programming that looks at Python from a digital forensics perspective.
Mobile Analysis Methodology and 3rd Party App Analysis with speakers, Jessica Hyde– Founder, Hexordia and Cesar Quezada, Senior Digital Forensics Specialist, Hexordia. This hands-on lab teaches a methodology for mobile forensic analysis of unsupported applications and artifacts. It teaches a 5-part methodology; Discover, Test, Parse, Find, and Script, which are necessary skills to parse 3rd party applications.
AI and the impact it will have on Children, Digital forensics, Regulation and Legislation, Joseph Pizzuro, CEO, Raven and Debbie Garner, Founding Board Member, Raven. This presentation will address what is coming from an AI legislative and policy perspective and discuss how policy and legislation impact digital forensics and cyber investigators.
How to Identify and Mitigate Hacker Obfuscation Techniques, Tony Lauro – Director of Security Technology & Strategy, Akamai. During this session, attendees will discover three of the key obfuscation techniques attackers use to break down defences and exploit systems through undetectable means, including impersonation, trusted site, and human ingenuity techniques.
Navigating the Cloud: Trends in Innovation, Multi-cloud, and Kubernetes, Paul Lawrence, Principal Solutions Architect, Expel. Session attendees will come away with an understanding of the trends and challenges decision makers are facing now, what the landscape could look like in the future if these emerging trends continue, and actionable takeaways to drive security-enabled success for their own businesses.
Leveraging GenAI to Enhance DFIR Capabilities, Matthew Seyer – Director, KPMG LLP, and leveraging this technology for DFIR and how we can address the likely organizational barriers to adoption.
Same Data, Different Story: Law Enforcement vs Independent Experts, Jared Barnhart, Customer Experience Lead, Cellebrite and Patrick Siewert, Director, Digital Forensics & eDiscovery, ArcherHall, will seek to explore the issues from both perspectives in a practical manner and discuss approaches that government/LE examiners can undertake for optimal success when dealing with opposing experts.
Navigating the Shadows: Linux Tails Examinations for the Digital Forensic Examiner, Rob Attoe, CEO, Spyder Forensics, will guide attendees through the intricacies of Linux Tails examinations, equipping them with the knowledge and skills necessary to navigate this complex terrain effectively.
eDiscovery & Investigations in Focus: A Panel on Privacy, Challenges, and Future Trends in a Modern World, Rene Novoa, III – Director of Forensics, HaystackID, John Wilson – President of Forensics/CIO, HaystackID and Clifford Nichols, Assistant United States Attorney, District of Connecticut. This session will delve into pressing issues surrounding privacy concerns, as well as the collection and review hurdles confronting eDiscovery professionals across various industries. The conversation will explore real-world applications, policy implications, the role of artificial intelligence (AI), and the evolving landscape of eDiscovery litigation and investigations.
The Future of Law: Integrating AI, Digital Forensics, and eDiscovery into Tomorrow’s Legal Practice, Carlos A. Baradat – Attorney / ESI Specialist, The Baradat Group. The legal sector is on the cusp of a technological revolution, propelled by AI, digital forensics, and eDiscovery. This talk explores their integration in legal practice, focusing on AI’s impact on research, digital forensics’ role in litigation, and eDiscovery’s relevance in data management.
An E-Discovery Conundrum: The Disappearance of Ephemeral Data, Michael Quartararo – President, Association of Certified E-Discovery Specialists (ACEDS). This panel will help attendees learn more about common sources of ephemeral messaging data and its impact on litigation, investigations and regulatory inquiries.
Domestic Hackers, SIM Swapping, and Cryptocurrency: A Case Study Cassandra Carpentier – Financial Forensic Analyst, United States Secret Service, Matthew Hannon – Special Agent, United States Secret Service, Tom Gillie – Network Intrusion Forensic Analyst, United States Secret Service, Jonathan Vanhouten – Network Intrusion Forensic Analyst, United States Secret Service and Elliot Daniels – Assistant United States Attorney, U.S. Department of Justice
This case study walks through an investigation beginning with a substantial cash out of Bitcoin and the investigation leading into the dark web of hackers and the uncovering of a prolific SIM swapper.
Become a Google Jedi: Building a Better Boolean String, Lauren Wagner – Program Manager, Cybercrime & Digital Forensics, SEARCH and John Trenary – Director of Digital Forensics, SEARCH
By mastering the art of Google Boolean operators and advanced search features, you will learn how to filter search results and uncover relevant information, saving you valuable time and effort. This session will show detailed examples of queries and methods that will enhance your productivity and make you stand out in today’s digital world.
Case Study: Todd Engles- Construction Superintendent During the Day and Producer of Child Sexual Abuse Material (CSAM) at Night. Jennifer Wing – Detective/Task Force Officer, Orlando Police Department/FBI Violent Crimes Against Children and Human Trafficking Task Force, Tampa Division and Roo Powell – Child Advocate, Founder and Subject of the Docuseries Undercover Underage, SOSA
This session will share a case study about a construction superintendent Todd Engles, who produced CSAM with multiple 9-12 year old girls on multiple social media platforms to include Discord, Tiktok and Instagram. The case study will begin with the NCMEC Cybertip and continue through the investigation and details of the communication with the victims and will end with sentencing information.
The full conference line up of 120+ sessions and product demos, including the above and tracks from the three Titanium sponsors (Cellebrite, Magnet Forensics and Oxygen Forensics) is expected to be available on the event web site www.TechnoSecurity.us/east by the second week of March.
Forensic Focus members who attend will receive a 10% discount on their registration. To access the discount (not valid on already reduced government rates), enter Promo Code FOR24 during the registration process.
Magnet Virtual Summit 2024 is almost here!
Save your spot for the virtual DFIR event of the year, taking place February 27 – March 7, which will give you another great chance to catch up on the latest trends and challenges in DFIR from a huge selection of the leading voices in the DFIR field.
MVS 2024 will feature 50+ presentations about topics like mobile forensics, artificial intelligence, eDiscovery, malware, ransomware, digital evidence review, video forensics, and much more! Plus, there’ll be great activities to help you accelerate your skills and special live Q&A sessions to answer your burning questions.
Register for Magnet Virtual Summit 2024 here.
Magnet Virtual Summit 2024 is a great chance to learn about the latest research and findings in mobile forensics, cloud, AI, and everything else DFIR. We’ll have over 50 presentations from experts in the public safety and enterprise spaces, as well as a series of Magnet-related talks from Magnet Forensics experts.
Here are just a few highlights:
Christopher Vance, Magnet Forensics
Most modern electronic devices keep logs running that store information about who, what, when, where, and why processes are performed. Modern smartphones are certainly no different. In fact, certain artifacts can only be recovered by an in-depth review of these logging files. This talk will explore the different types of log files that can be found and how to extract them on iOS, Android, and Chromebook systems.
Jason Jordaan, DFIRLABS
A lot of digital forensic practitioners testify in court, and sometimes their evidence can get in without significant challenges and from unknowledgeable legal practitioners. In some of these cases, the practitioners have gotten the evidence wrong, which led to wrongful convictions or other incorrect liability being allocated. While opposition digital forensic practitioners are often frowned upon, especially from law enforcement, they do play a valuable role in balancing the interests of justice. This can often play a role in ensuring that digital forensics maintain good quality.
Through a discussion of three cases—one criminal, and two civil—this presentation will show how digital forensic evidence presented by either an unqualified or biased digital forensic practitioner almost destroyed the lives of the parties in court. You’ll also see how a proper scientific approach to digital forensics assisted in the courts in achieving justice.
Johann Hoffmann and Mattias Shamlo, Griffeye
In a time where forensic backlogs keep on growing, along with the exponential growth of the volumes of digital media that are constantly being seized, collaboration between investigators and agencies is critical. In this talk, we’ll explore how the Griffeye Analyze platform is designed to address this challenge by minimizing redundancy in investigative work across units and regions. Discover how the platform facilitates seamless sharing of high-quality data, giving investigators worldwide access to vital information and enabling them to build on each other’s casework.
Brandon Epstein, Scientific Working Group on Digital Evidence, Barbara Guttman, National Institute of Standards and Technology (NIST), and Christopher Kelly, Massachusetts Attorney General’s Office
It is no secret that digital evidence touches almost every modern investigation, yet the processing and analysis of this evidence varies from agency to agency and provider to provider. This panel will leverage recently published research to discuss what the digital forensics community can do to improve digital forensic analysis through effective digital evidence quality management. Available resources to build effective workflows, policies, and training programs will be discussed as well as how examiners can get involved to help shape the future of digital evidence quality management and standards.
Joseph Pochron and Jeremy Horowitz, Ernst & Young
Insider threats continue to pose a major risk to organizations. Organizations spent an average of $15.38 million in 2021 to deal with insider threats—up 34% from the $11.45 million in 2020. The number of insider incidents has increased by a staggering 44.3% in a single year, from 2020 to 2021. Data theft is the leading insider threat activity. 42% of insider threat events involved intellectual property (IP) or data theft.
Digital forensic examiners inevitably are needed for insider threat investigations and analysis. This presentation will provide a case study overview of a malicious insider investigation where both Magnet AXIOM Cyber and Magnet VERAKEY proved to be invaluable tools in the investigation. The goal of the presentation is knowledge sharing on how DFIR personnel can leverage these tools for that particular use case. Register for free to see the full agenda and save your spots!
[img-2]
We’re excited to have David Chow, Chief Technology Strategy Officer at Trend Micro, kicking off the second week of Magnet Virtual Summit 2024 as a keynote presenter. David will deliver a keynote address on March 5 at 10:00AM EST | SGT about best practices on public/private sector collaboration and how to ensure these partnerships are symbiotic and impactful. We can’t wait to hear his insights!
We’re bringing another amazing Magnet Virtual Summit Capture The Flag (CTF) for Magnet Virtual Summit 2024! This CTF, powered by Hexordia, will be a three-hour timed event and will test your skills while competing with others. We don’t want to give away too much, but we promise that Jessica Hyde and interns from Champlain College’s Digital Forensic Association have created a CTF that will be fun, challenging, and full of learning opportunities.
This CTF will take place on March 6 from 11:00 – 2:00 PM ET and it will test your skills while competing with others.
Important: Please note registration for this event closes end of day Wednesday, February 28, 2024 and images and download links will be sent out on Friday, March 1.
Need a few tips on taking part in the competition? When you register, you can also take part in a Capture The Flag workshop with CTF creator, Jessica Hyde, and multiple Magnet CTF-winner, Kevin Pagano. Learn more about the MVS CTF in this blog from Jessica.
Drop into these live interactive sessions and chat directly with Magnet Forensics product experts. You’ll have the opportunity to engage in conversation with Product Management, Forensic Consulting, and Market Research team members from Magnet Forensics.
And be sure to join us right before each Live Q&A for a special presentation that will cover the latest Magnet Forensics solutions.
Magnet Forensics for Public Safety: Integrating Tools and Teams for Smarter Digital Investigations
February 28 | 9:30AM EST | CET | SGT
Live Q&A With Magnet Forensics Experts
February 28 | 10:30AM EST
Transforming Digital Investigations With Magnet Forensics
February 29 | 9:30AM EST | CET | SGT
Live Q&A With Magnet Forensics Experts
February 29 | 10:30AM EST
Get access to all of these activities by registering for Magnet Virtual Summit 2024 for free! Head over to magnetvirtualsummit.com for more information and to register and start building out your personalized agenda today. Plus, we’ll have opportunities to take part in special MVS games to gain points and win prizes!
by Si Biles, co-host of the Forensic Focus podcast
The venue was the Novotel Hotel and conference centre in Hammersmith, and for me at least, this was gratefully welcomed, with underground parking that was convenient to access and which you could enter the hotel from without getting drenched – those (including a friend that I was attending with) who had to walk from the tube station (only five minutes away) probably dried out around three in the afternoon.
This is the first BSides that I’ve attended, but I’ve been aware of them for a while, and they’re a global phenomenon, with events worldwide, each run by their own local community, but for the good of everyone and anyone who can attend. I’m going to lean on them and use their own descriptions to explain what they are:
“Security BSides is the first grass roots, DIY, open security conference in the world!”[1]
“… a community-driven event built for and by information security community members. The goal is to expand the spectrum of conversation beyond the traditional confines of space and time. It creates opportunities for individuals to both present and participate in an intimate atmosphere that encourages collaboration. It is where conversations for the next-big-thing are happening …”[2]
The annual event has been running in London since 2011 – with the notable exception of 2020, but we’ve all heard about COVID, so I think we can forgive this slip in their record. This year it was a new venue for them – and a good thing too, as I understand that the old venue had a maximum capacity of 1,200 people, and they managed a headcount of over a hundred and fifty more than that this year. This venue (with a maximum capacity of 2500) should allow them to expand again next year – which I think is well within their reach. The day is spread out over three levels, with a large open hall on the ground floor, smaller workshop rooms on the first, and large auditoria on the third. The schedule for the day is packed with content – and it’s only possible to sample a small subset of what’s on offer.
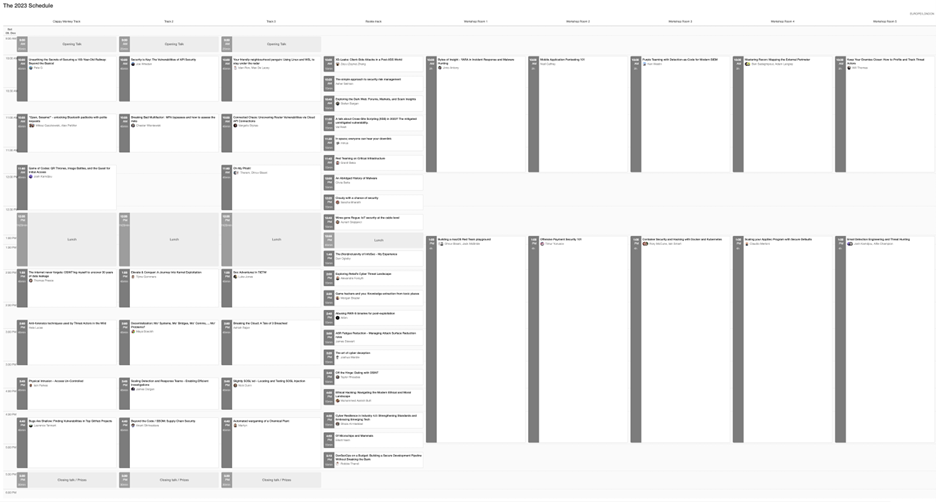
Doors opened at 0830hrs UTC, and the scheduled talks started at 0930hrs with the Opening Welcome Talk – apologies to the reader, I didn’t attend this as I was far too busy enjoying the hall downstairs which is one of the highlights of the conference as a whole. Some of this is because it was a great opportunity to catch up with Desi in his corporeal form as opposed to the disembodied ethereal presence that given our relative geographical locations is more normal. Desi was working, as Security Blue Team were the platinum sponsor for the event and had the prime spot inside the hall, right by the entrance to advertise their wares.
It should be noted, that this was not a vendor conference – rather that those who had sponsored the event had stalls. Yes, they are creating awareness of themselves and what they do, but more than that they were giving away the obligatory conference ‘merch’ (for the record, I like the trend of socks as a giveaway – I obtained one pair from one vendor, I returned to get some later in the afternoon and the other three sock sources that I had identified in the morning had run out, so clearly I’m not the only one!), but there were also competitions and raffles to win some rather nice, geeky, prizes – Lego made a number of appearances, as did AirPods and an Atari 2600+. I was satisfied with a new (high quality!) travel mug courtesy of my “Spin the Wheel” attempt at Security Blue Team, and I’m pretty sure that no-one went home empty handed.

As well as the vendor stands, there were also the “villages” – lockpicking, automotive security and trains[4] all had a presence. As a poor, but reasonably well equipped, lockpicker – I was most taken by the automotive area, which had a rather lovely simulator setup that had been shipped over from Cardiff University where it normally lives. There were also several In Car Entertainment (ICE) head units of dubious parentage and interesting CAN bus interfacing. There are some very knowledgeable people in the villages, and it’s easy to spend a lot of time talking to people who are not only very passionate about their area of interest but incredibly well informed.

I have some small gripes about the main hall. Firstly, the coffee provision isn’t enough for 1350 people who subsist on caffeine as one of their main food groups. And secondly, this main large space is a bit … I don’t know, utilitarian? It’s more like a storage area than a venue, and the lighting is poor at best. This is, of course, a criticism firmly levelled at the venue – who provided both catering and facilities, not at the organisers of the conference, who would have no real control over such things. Nonetheless, if I were to suggest areas for improvement, these would be they. The floors above got swankier the further you rose, and the auditoria were rival of any that I’ve been in before.
Speaking of swanky, the AV setup in the auditoria was very good – when it worked. The feature of being able to link all three of the main spaces so that the screens and audio in each displayed from one meant that no-one was left out of the opening or closing ceremonies, even though not everyone could be accommodated in a single room.
My choice of talks will show my particular areas of interest, and I’m sorry if this doesn’t align with yours. What I would say for future reference is that what I saw – whilst obviously varied in content and presentation style, as you would expect from different people, of different backgrounds, talking about different concepts – was of a universally high standard.
My personal favourites were the talks on Bluetooth Padlocks (which was an absolute masterclass in how not to create any sort of secure service), the one on Physical Intrusion testing (with a distinct flavour of smoke being given by a former fire systems engineer) and the one on the history of malware (very well and humorously presented indeed and a very rapid run through of decades of malicious software). The other talks during the day were enlightening, and I learned more about Linux on Windows (although why you’d bother with the Windows layer still escapes me), anti-forensic techniques in incident response and issues about machine learning systems messing with chemical plants. This last one was an interesting area of research that I think needs a bit more doing on it before it can address the full potential of both offensive and defensive sides.

As I’ve said, there is so very much to choose from in the day, and I only sampled one of the “Rookie Track” presentations and none of the workshops, but I don’t doubt for an instant that there is something that would be of interest to anyone in the industry in the available choice. (My friend who attended is in a decidedly different field to me and – in a way that concerns me regarding his mental health – writes decompilers for fun, and yet he also found things of interest, despite not winning any Lego or the Atari 2600+ …)
The atmosphere at this event was almost carnival like – evidenced by the presence of both stuffed sharks and some interesting headwear. From my side, I’m excited for the future of this particular spot in the annual calendar, and I hope that I’ll be able to return in future.
[1] http://www.securitybsides.com/w/page/12194138/BSides
[2] https://www.securitybsides.org.uk/
[3] https://www.securitybsides.org.uk/schedule.html
[4] Model trains is the source of the word “hacking” from the MIT Model Railway Club – Google it if you don’t believe me.
By Dee Biles, Cokethorpe School
On the 25th of October, CyberWomen@Warwick hosted the second, now annual, CyberWomen Conference. Completely student led and organised, with collaboration between the ever-expanding branches of the CyberWomen Groups C.I.C., the conference explored the changing face of cyber with talks and workshops that promoted inclusivity and diversity by having a wide range of speakers and topics. The conference highlighted the ways in which bringing together teams of people from all backgrounds can foster a safe environment for creativity and innovation, from sharing ideas to giving attendees the opportunity to network and meet professionals who could speak to their own experiences.
The opening talk, given by keynote speaker Chani Simms, gave an overview of how emotional intelligence should, and can, go in hand in hand with cyber careers, using her own impressive background as an example of how it can be done. She touched on parts of her own work that people could relate to. The desire to be a ‘wonder woman’ who does it all was a comment that got many nods from across the room from both the other speakers and the diverse audience who came to the conference. When in a minority, whether in wider society or within a particular industry such as cyber security, there is a consistent pattern of those who are ambitious to feel it is on them alone to make all the changes to their environment, to be a ‘wonder woman’ who excels at their job and makes everything better for everyone all the time. Simms emphasised how this was not possible to do alone, referencing and showcasing her own companies who pride themselves on being teams.

The next lecture was given by Donna Chivers, a product manager at Kaze Consulting, who gave an impressive technical talk about ‘Unravelling Vulnerability Management’ covering the intricacies of cyber resilience while also casually promoting the new Kaze software to help with mitigating risks. Going into this talk with a more or less non-existent understanding of this part of the cyberworld, Chivers made the topic surprisingly accessible through her clarity. With or without an interest in the new software involving a risk detecting ‘AI’, this lecture was highly informative. This was then paired with a workshop just after, delivered by Rohini Paligadu who gave demonstrations of the aforementioned Kaze software with an insight into different approaches to vulnerability management.
With lunch around the corner, the Threat Hunters Rosie and Archa from WithSecure educated the audience about ETW patching and driver abuse, accompanied and aided by some beautiful presentation slides. Clearly both passionate experts, their talk gave the less often glamourised side of hacking – the security on the other side – a much needed glow-up.
After a successful morning, with ample break time supplemented with croissants and refreshments, lunch came with a never-ending amount of sandwiches which were still being offered by leaving time some four hours later. Though the food was a large attraction, the Opportunity Hub where this was all held was the true gem as attendees were able to talk to the speakers and to people in industry. The CyberWomen Groups C.I.C. teams were always around, friendly, and ready to introduce everyone.

The afternoon kicked off with Sophie Powell and her ‘Introduction to CyberWomen Groups C.I.C.’, explaining the origins, present and future of the inspiring students who started it all. Though short, it was a lovely and informative way to commence the next round of talks which had more of a focus on being in and part of the cyber space.
Yasmine Rasselkaf then detailed the wide range of options there are in the cyber space for job opportunities that can suit a diverse range of approaches and interests. From Palo Alto Networks, the Cybersecurity Systems Engineer conveyed the absolute joy she found in her job and offered advice within her talk and during the Q and A portion to those looking to navigate the cybersecurity landscape.
With the two workshops running about the Kaze software and deepfakes, conference-goers were given the chance to attend whichever they had not yet seen (both were offered in the morning after the Kaze talk). ‘Elvis may not have left the building’ was an interesting exploration of how ‘AI’ and impersonation fraud have combined and evolved in recent years. From celebrities golfing to Henry VIII being catfished and the odd middle ground in between, this talk touched on several aspects of issues around the impact of ‘AI’ on trust relations. Janette Bonar Law from the Coventry Building Society opened this talk with a quick history of deepfakes that was then followed by Matthew Treadwell of The Cybarian LTD who talked about one my personal favourite studies, ‘Birds aren’t real’ by Peter McIndoe, using it as an example of how easily manipulated trust relations are. The talk ended with an Elvis impression worthy of a chapel in Vegas.
Next up was a panel with Illyana Mullins, founder of WiTCH, Venessa Eyles who is in charge of the Cyber Resilience Centre for the West Midlands and Vickie Hickinbottom from CGI. They discussed the current hot topic – AI. Looking at different areas that AI could and will affect, they traversed issues around employment and the lack of diversity in the data bases that form the groundwork of the chatbots that are now highly prevalent. This panel was engaging with the three speakers sharing a clear respect for one another that enabled an in-depth discussion around the subject.

The final talk of the day, apparently a last-minute fill in despite how polished it seemed, was about neurodiversity within the cyber space community given by Illyana Mullins. She shared her personal experience of diagnosis of ADHD and autism and how it impacted her life and career. Enlightening, the talk resonated with the audience and debunked myths surrounding being neurodivergent. She also explored how gender can play into the perception of neurodivergence, how embedded inequalities can impact someone on an individual level.
The conference then ended on thank yous from the CyberWomen Groups C.I.C., with cards for each speaker. The conference was intimate and informative, and I fully recommend attending the next one. Having grown up as a girl interested in STEM, I participated in competitions with predominantly male competitors and judges, as well as talks and workshops that were almost exclusively run by older males. I was quite emotional to see a female heavy conference, run and organised by young women in industry with a balanced audience. It was truly inspiring and I am so glad there are organisations like this that exist who are organising events like this.
The Techno Security and Digital Forensics Conference changes venues for the West edition from the Hilton La Jolla at Torrey Pines in San Diego, to its new location in Pasadena, California at the convention center. Running Monday, September 11th through Wednesday, September 13th, the conference continues to offer the high qualify line up of topics and speakers the industry has come to expect from Techno. Primary session tracks are: Cybersecurity, eDiscovery, Forensics and Investigations.
Event Director, Jennifer Salvadori said that the West edition of Techno is in a significant growth phase, and is expected to expand the program and exhibit hall to mirror the flagship East event in the next few years. The goal is to deliver more content, and feature additional technology solutions as requested via feedback received on attendee surveys over the years.
Show Management is working with three hotels in Pasadena, all of which are offering the federal government per diem rate to Techno LEO and government participants. Hotel discount block deadlines are coming quickly, with August 11, August 18 and August 21 being the cut off for each of the three, respectively. Reservations will need to be made through the Techno West Hotels & Travel page of the event website to secure the discounted conference rate.
Below is a look at some of what to expect this year in Pasadena within the Techno West conference program. For session details on the 75+ sessions scheduled, and to register, visit www.TechnoSecurity.us/west .
Brett Shavers, Author, Forensic Analyst, Consultant, will present this year’s keynote, The DFIR Investigative Mindset: Hack your Mind to Crack the Crime, Tuesday morning at 8:30 AM. In his keynote, Brett distills decades of casework into a keynote to show how to do that while avoiding common pitfalls and biases that may sabotage your investigation and your reputation.
OSINT Tools will be presented by Cynthia Navarro, OSMOSIS, on Monday. During this talk, Cynthia will provide valuable guidance, introduce useful tools, and enhance your understanding of OSINT.
On Wednesday, the Dutch Police department will present, Hansken – Big Data Forensics, a platform that is specifically developed for digital forensic investigations that contain of hundreds of Terabytes of data including investigations conducted by law enforcement and intelligence agencies.
Ben LeMere, Berla Corporation, will present Geolocating Vehicles Using Open Source Data on Tuesday. This session will share how to use open-source data to discover historical location information for vehicles that do not store GPS data or vehicles that you may not have physical access to.
Todd Shipley, Dark Intel, LLC, will present The Dark Web and Why It’s Important to Your Investigation, on Wednesday morning. It will discuss what investigators need to get on the Dark web and what possible value it is for OSINT collection.
Colleen Stanich, Detective, National City Police Department, will present a powerful talk, The Kidnapping of Alani C. – Dangers of Online Gaming, on Tuesday. Attendees will get to see the collaboration of both Federal and local police. The rescue of Alani and the capture of the suspect along with follow up interviews of both. Attendees will also get to see the technology used in the case and what went well and what didn’t. The case study will end with the prosecution issues and aftercare for Alani.
Pressing Snapchat to Extract Juicy Data, presented by Matthieu Regnery, Magnet Forensics on Wednesday. This session will dissect Snapchat data obtained from mobile phones extractions. The presenter will dive into obscure serialized format (protobufs) to uncover information needed to recover juicy content (ie media).
Romy Haas and Danielle N. Ponce de Leon, Los Angeles County Sheriff’s Department will present Google Geofences: Understanding the Fundamentals & Dealing with Rejection, on Wednesday. Attendees will be introduced to the search warrant and analysis process, and the anonymized data provided to law enforcement. A brief homicide case study will be presented.
Pig Butchering: An Interactive Case Study, with speakers Andrew Frey and Derek Wang of the United States Secret Service, Los Angeles Field Office, Cyber Fraud Task Force, will share a case study of a cryptocurrency investigation and walk through the steps taken start the investigation to the point of recovering assets using both open source and commercial tools. Ben
On Monday, iOS Forensics – The Good, The Bad, and The Ugly, is presented by Belkasoft. This session will discuss the lifecycle of iOS versions and devices, to include major changes in iOS updates, and what implications they bring to examiners.
Everything You Need to Know About Mac Timestamps: Understanding POSIX and Apple Extended Attribute Timestamps will also be presented on Monday, with Andrew Pomerleau, SUMURI. Participants will learn how to use forensic tools to analyze and interpret timestamps accurately, including how to identify and account for any discrepancies that may arise.
The full conference line up is 75+ sessions and product demos. Forensic Focus members who attend will receive a 10% discount on their registration. To access the discount (not valid on already reduced government rates), enter Promo Code FOR23 during the registration process.
In what used to be the unusably polluted London docklands lies the ExCeL (Exhibition Centre London). FEE shares a hall with CTX (Counter Terror Expo) in the ExCeL, and accordingly the stands vary between the preventative and the investigative – with bomb disposal robots rubbing shoulders with fingerprinting tools. This particular juxtaposition is noticeable several times during the two days as the London Transport Police stage live demonstrations of an “armed suspect takedown” – with significant levels of shouting – at the same time as other talks are ongoing. Poor David Spreadborough of Amped had to pause mid-talk about Amped software to reassure the audience that the fact that someone was currently being “tazered” was, in fact, a planned occurrence and that we shouldn’t worry.
This is a full range forensics event, and, as such, we see a wider variety of “meatspace” services that don’t normally cross into our nice, tidy, blood spatter free digital realm. Eye opening in terms of technological advancement, especially in the terms of optics, with both Sony and Leica (geosystems, rather than cameras) having stands. The Leica stand remains my favourite from last year – not only is their representative Nicolette Beggache wonderfully engaging, articulate, knowledgeable and passionate about their stuff – their equipment for crime scene analysis and reproduction is incredible, and the applications to CCTV and witness testimony analysis by the reconstruction of locations and sight lines is bordering on voodoo![1]
Moving away from the physical back to the digital realm, we see the usual suspects – Amped, Belkasoft, Cellebrite, Exterro, Oxygen, Magnet, Sumuri and so on. I’ll be honest, with co-manning the Forensic Focus stand, attempting to listen to a few of the talks given (more on that shortly) and catching up with friends and acquaintances, I didn’t get a whole lot of time to visit each of them for the latest and greatest offerings that they were promoting. I did have an opportunity to speak with Steve Whalen from Sumuri – a personal visit as I wanted a look at Recon Lab for my own use. Steve also gave a good talk on “Mastering macOS Forensics: Unravelling Security Barriers and Decoding Proprietary Artifacts for Impeccable Data Capture and Analysis” (which, let’s face it, is descriptive even though perhaps a little verbose!). One of my friends was thrilled when he opened a terminal during it! I have to say that I think it’s quite a power move to turn up to a show – where the objective of most is clearly to sell their products – and to do a purely technical talk.[2]

I didn’t catch many of the other talks – Prof. Sarah Morris of the University of Southampon was compère for the two days and did a great job of doing so. There’s been an “elephant in the room” in UK forensics that has somewhat overshadowed the event with the upcoming enforcement of ISO17025 lab requirements, and this showed in the talks and the panel discussion on the first day. There were a couple of representatives from the UK Accreditation Service (UKAS), and I heard Paul Hunter (Senior Assessment Manager, UKAS) speak on the second day on “Accreditation in Forensic Science”. In my humble opinion, this did little to alleviate concerns about the process or how it will be feasible for small businesses. It certainly wasn’t helped by a poor choice of font size and putting white text on a light blue background …
The only other talk that I heard was from David from Amped on “CCTV Investigation and Forensic Video Analysis – Safeguarding cases and protecting staff with science.” This was mostly a whistle stop tour of the Amped history and product suite – a nice run through, no complaints from me, even if I have heard it all before – with a later focus on the new validation tools, which does seem to be a nice touch and is available for free to all existing Amped customers.[3]
Back in the arena, another stand that I visited was that of Semantics 21, where I chatted with Tom Oldroyd about their CSAM handling product. They’re relatively unknown, despite being a pretty significant player in the space, evidenced by their own admission of the number of people asking if they’re new vs. their actual four-year history. We’ll be covering the product in more detail in future with a review and speaking with them on the podcast, so I won’t put too many spoilers in here – what I will tease though is that the product has some very nice, user-friendly features, some interesting machine learning application and is pretty darn quick. Definitely one to watch out for here.
Overall, I would say that the conference seemed more subdued this year. Even the British Transport Police demo mentioned above was only run once on the second day, whereas last year it was run at least twice and drew big crowds on both occasions. The hall was emptying out of visitors and exhibitors well before the closing time on day two. Zoe (my co-rep at UK conferences and keeper of the banners) said it was a lot more lively on the first day, but it still seemed smaller – it was held in a different hall to last year (N12 instead of N2) so it was hard to gauge exactly, but I think overall it was probably only between a half and two-thirds of the floor space occupied in ‘22. Merch seemed more restrained as well – I was hoping to pick up another quality water bottle from Oxygen, but I don’t believe that they had them (although, by the time I got around to going to try and check at the end of the day, they’d left), and apart from the general stress toys (thanks to Avian Cloud for my cloud shaped one – a remarkably firm and satisfying one I must admit), there was little of note.[4] Hopefully the economy will pick up by next year and things will liven up a little!
[1] We hope to get them onto the podcast in the future to discuss their technology and the cross over into the more traditional digital realm.
[2] Steve has also agreed to come and talk on the podcast and talk about Apple forensics platform agnostic – look out for that one in future.
[3] We’ll have Martino on the podcast again soon too …
[4] Forensic Focus has excellent lens cloths, they’re ideal for glasses and camera lenses, are a fetching blue theme and have our URL immediately to hand !
by Alex Desmond, co-host of the Forensic Focus podcast
This year was the 18th International Conference on Cyber Warfare and Security (ICCWS). The word ‘international’ doesn’t necessarily mean it is definitively all nations, as there is a sister conference called the European Conference on Cyber Warfare and Security (ECCWS) and one that used to run out of Perth, Western Australia.
“ICCWS uniquely addresses cybersecurity, cyberwarfare, and information warfare. Over the years, the conference has been attended by a variety of security and military organisations, including the Cyber Security Policy Research Institute, more than 10 national defense colleges, NATO, SHAPE, etc.” – ACI website
This year’s conference ran two in-person streams and two online streams that had different talks. There were 71 talks, including the two keynotes at the beginning of each day. The majority of talks were done by researchers in their respective fields, and topics ranged from military ethics and information warfare with a focus on the Jan 6 US Capitol attack to technical talks on digital forensics in different fields and remote hacking the CAN bus of cars.
For all the papers go here.

The keynote speakers both had thought provoking talks. Mr Justin Fanelli spoke to Zero Trust and how it was used and developed in the US Navy. Dr George R. Lucas gave some insights to recent discussions and development around military ethics and the use of AI algorithms in drone technology in the current conflicts around the world.
You can check out their bios from the conference, as well as information about the other chairs and organisers, here.
Like other workshop conferences, the ICCWS partners with the Journal of Information Warfare, which helps support publishing speakers, whether they are seasoned professionals or students.
Some of the talks that stuck with me and that I have mentioned on the podcast with Si are worth mentioning in here, mostly because I think they’re universal and not a singular cyber domains issue to be conscious of.
Martti Lehto gave a talk on budding research into Cyber security training in Finnish basic and general upper secondary education. My immediate question on this was how the structure of schooling compares to others around the world when using the terminology ‘secondary education’. The motivation behind the research was fantastic, and I think it’s a question we should be asking ourselves in each country – “What should we be teaching children about cyber security?”. The early implementation within this paper focused on asking teachers qualitative questions in their abilities both with regard to cyber security in general, and the confidence they would have teaching this on top of the other curriculum subjects.
It is important to keep in mind that every area involving cyber security has a skills shortage, and in three decades’ time the school children will be choosing where they want their careers to go.
Clara Maathuis delivered a presentation on Social Media Manipulation Deep Learning based Disinformation Detection, along with two other talks as part of a series for her research. It focused in on the information manipulation surrounding the covid-19 pandemic and how social media, particularly twitter, could sway the public view and opinion on the matter.
This issue was highlighted by the UN as disinformation and an “existential risk to humanity”. Clara and her teams’ research were based on how to build deep learning models using an existing dataset. I won’t go into the model of choices here in this article (BERT and CNN were used), since the paper does a good job explaining and I would probably butcher it.
What I personally conclude after reading the paper is that humans are still so vital in training these models and ensuring that false positives or true negatives are identified where possible. However, with the sheer amount of information that is release into the web everyday, these models built of deep learning and data science principles are needed more than ever to help combat the issue.

Like all conferences though, I think the best part was the watercooler chats. The in-between talks gave an opportunity to really dive into the presenters’ content more and offered a chance to make connections with other attendees. It also allowed me to find potential guests for the podcast and make contacts relevant to my own interests and job.
In terms of cyber security conferences, it is unique, and since it’s accessible wherever you are in the world, I would highly recommend it to anyone that has the chance to check it out.
A trend has started to form with the international version of this conference, where every five years it visits South Africa. Details will be added to the ACI website soon.
Follow the conference on any of these:
The Techno Security and Digital Forensics Conference changes venues from the Marriott in Myrtle Beach, to its new location in Wilmington, North Carolina at the convention center. Running Monday, June 5th through Thursday, June 8th, the conference continues to offer the high qualify line up of topics and speakers the industry has come to expect from Techno. Primary session tracks will see the addition of eDiscovery to the line-up of digital forensics, information security and related fields.
Event Director, Jennifer Salvadori, said that the 24th edition of the flagship conference has a sold out expo hall, and already two of the three hotels offering discounted conference room rates are at capacity. Salvadori reports that a record number of submissions were received during the open Call for Speakers, and that the educational program has been expanded to start earlier on the first conference day. The schedule change allows for more content, as requested via feedback received on attendee surveys over the years.
Here’s a look at some of what to expect this year in Wilmington within the Techno East conference program.
The conference will start earlier on Monday, June 5th – kicking off with three two-hour sessions from 9:30 to 11:30. This “bonus” content will feature:
“Google Geofences: Understanding the Fundamentals & Dealing with Rejection”, presented by Crime Analysts, Romy Haas and Danielle Ponce de Leon from the Los Angeles County Sheriff’s Department, will share how a Google Reverse Location Search (Geofence) search warrant works and the challenges geofences are facing in court. A brief homicide case study will be presented.
Ken Cutler, Ken Cutler & Associates will identify the control points in a DevOps, associated risks (including supply chain risks), and a DevSecOps overlay to promote end-to-end integrated and automated testing, controls, and enforcement, in his session “Securing and Auditing the DevOps Software Development Life Cycle – Stopping a Runaway Train.”
“What Data Do Google and Apple REALLY Collect?”will be presented by Jerry Hatchett and Chip Koon, Veracity Forensics. During this session, they will do a deep dive into the information mobile devices collect about us on a daily basis, what happens to that data, and the implications for both users and investigators.
On Monday, June 5th, Joseph “Rich” Baich, the CIA’s Chief Information Security Officer (CISO) and Director of the Office of Cyber Security (OCS), will deliver the keynote presentation,n where he will discuss how cyber defense is the new offense. He’ll share how the future geopolitical and armed conflicts will fall to public private cooperation to defend and how organizations need to move towards more proactive cyber defense.
On Monday, Carlos Baradat, The Baradat Group, LLC, will present “Winning Cases with eDiscovery and Digital Forensics”. This session will take us from the collection stage of legally defensible data, through the processing, analyzing, and production phases, all the while highlighting best practices and potential pitfalls that every litigator ought to know in today’s legal realm.
“Enter the Metaverse: How to Survive in the “The Wild West “of Web 3.0” will be presented by Ray Rivard and Nana Safo, Federal Deposit Insurance Corporation. The presentation will explore challenges of the Metaverse and how it will impact eDiscovery.
Thursday will feature, “Understanding How to Use eDiscovery Tools and Analytics for DFIRInvestigations”with speakers William Odom, III and Andrew Hunniford, Orbital Data Consulting Group to share the tools that can be used to assist in an investigation, including incident response, data privacy and breach reporting.
On Wednesday, June 7th at 8:30 AM, the United States Secret Service will present a panel discussion on “Cryptocurrency: A Case Study from Inception of Investigation to Successful Seizure”, a case study of a cryptocurrency investigation.
“Investigating the Dark Web and Cryptocurrencies” will be presented on Thursday, June 8th by Keven Hendricks, New Brunswick Police Department/Law Enforcement. He will share best practices when conducting dark web investigations, understanding the end-to-end encryption apps and email services commonly used.
“iOS Forensics – The Good, The Bad, and The Ugly” will be presented on Tuesday, June 6th, by Jared Luebbert, Belkasoft, where he will we discuss the lifecycle of iOS versions and devices, including major changes in iOS updates and what implications they bring to examiners.
Chris Vance, Magnet Forensics, will present “I Didn’t Put That File There! – Understanding the iOS Files Application” on Tuesday, June 6th, where he will explore file attribution, storage across multiple areas of the file system, and where to look for the context behind a key application in iOS.
Jared Barnhart, Cellebrite and Heather Mahalik, Cellebrite / SANS Institute will present “eXXXamining Mobile Web Browsers” on Monday, June 5th where they will break down web browsers and their artifacts for both iOS and Android.
On Wednesday, June 7th, Jared will also present “Courtroom Strategies for Mobile Forensics” where he will break down some of the core components of mobile device forensics to strengthen testimony and make sure the jurors don’t get lost in 1’s and 0’s.
On Wednesday, June 7th, Dan Dollarhide, Oxygen Forensics will present “Data Blackouts: Examining the Causes and Challenges for Law Enforcement When Collecting Digital Evidence and Cloud Stored Evidence Data”. The session will discuss the causes and challenges of the Data Blackout created by cloud storage, encryption that investigators face, and steps to solve these forensic challenges.
Jessica Hyde, Hexordia and Joshua Hickman, Kroll will present “Gen X: Effective Methods and Best Practices for the Generation of Test Data for Digital Forensics” also on Wednesday, June 7th. They will share how to dig into the nuance of effectively creating data sets for a multitude of uses for your lab.
Thursday, June 8th, Joe Perez, NC Dept of Health & Human Services will discuss whether data should be driving our decision-making in forensics, in his session, “Driving Decisions with Data: Delight or Disaster?”
Wednesday, June 7th, “Future (and current) Threats Posed by Drones” presented by David Kovar, URSA Inc. will educate the audience on the not-so-distant future threats posed by drones and the regulatory and policy challenges we face to deploy and operate systems designed to detect, identify, and counter malicious drones.
Drones will also be discussed on Tuesday, June 6th in the session “The Rising Drone Threat and the Need for Forensic Solutions” with Joshua Smith, SkySafe, Inc. where he’ll share their research effort dedicated to developing the tools needed most by law enforcement for performing digital forensic extraction from multiple UAV devices across vendors, makes and models.
Brian Carrier, Cyber Triage will present “User Login Forensics – Merging Artifacts To Find Anomalous Activity” on Tuesday, June 6th covering the logical steps of logons, dive into events that occur at each step and identify patterns of login activity to identify anomalous hosts and user accounts.
“Zero Trust Illustrated: A Guide for Network and Infosec Pros” will be presented by Jennifer Minella, Viszen Security on Tuesday, June 6th. In this session,n she will share real world examples of zero trust journeys, explain and illustrate architectures, plus untangle ZTA, ZTNA, SASE, SSE, and more.
The full conference line up of 120+ sessions and product demos, including the above and tracks from the four Titanium sponsors (Belkasoft, Cellebrite, Magnet Forensics and Oxygen Forensics) is expected to be available on the event web site www.TechnoSecurity.us/east by the first week of March. Forensic Focus members who attend will receive a 10% discount on their registration. To access the discount (not valid on already reduced government rates), enter Promo Code FOR23 during the registration process.
by Si Biles, co-host of the Forensic Focus podcast
Warwick University hosted the 18th Teaching Digital Forensics Workshop on Wednesday 23rd November 2022. Largely owing to the big “C”, the last in-person event was back in 2019. As you’d expect from the title, this is an academic conference in the UK that aims to bring together those teaching or researching digital forensics with the objectives of sharing ideas and techniques, fostering collaboration and sharing some of the interesting things that people are working on. It also acts as an opportunity for departments to advertise their needs in the way of supervisors, markers, guest speakers and the like.
Our opening lecture really highlighted why this is so important – Dr Harjinder Lallie, from our hosts, Warwick[1], began proceedings by running down the current “state of the nation” as it stands with regard to Digital Forensics courses that are available. His research on the matter is a little disturbing, as there has been a significant reduction in the number of available courses that contain forensics in the title in any way. As it stands at time of writing, there are 14 Digital Forensics degrees. Of course, there are still going to be some courses where a module of forensics crops up (Warwick is one of these – the Undergraduate course had an IRDF course included – and there are 25 of these “other” courses) where the title is misleading. But we’re talking about proper hard-core Digital Forensics here – you know, the sort of thing that we actually have a profession in!
I’m aware that this number is likely to change – not least because of the recent appointment of Dr Sarah Morris to Southampton as Professor of Digital Forensics extending their offering – but we’ll come back to Sarah in a bit, as she gave a great talk too … In reality, this means that the representation of nine universities in the room probably covered a good proportion of the aforementioned course providers …
Next up was Dr Mohamed Chahine Ghanem of London Metropolitan University. Dr Ghanem numbers some of the Met Police amongst his students and makes good use of the knowledge that they bring (as does he from his previous life in Law Enforcement) to research in the Dark Web. He gave us a very interesting talk around the artifacts available from accessing assorted items on the dark web using the Tor Browser on a selection of devices and the success (or otherwise) of tools to hide said traces. Great work – that gave a few of us who’ve filled out ethical approval forms palpitations – but great work none the less!
Dr Adrian Winckles from Anglia Ruskin University followed. Adrian’s name is one that I’ve seen many a time on e-mails from the BCS Cybercrime Forensics Specialist Group but only met for the first time in person at this event. Adrian gave an interesting talk on his ideas surrounding the creation of forensic images for teaching. Anyone who does teach forensics knows the pain joy of creating scenarios and images to give to students. His raiding of his junk draw provided an intriguing idea of how to create some – using some rather outdated equipment (iPod Nano and DVR – both FAT32 and some weird smart watch) to create a slightly disturbing scenario with multiple devices to investigate [albeit blowing up the DVR in the process!].
Continuing on the pedagogical path, aforementioned Professor Morris took us through her teaching scenarios. Anyone who has knowledge of “The Twisted Pair” will be happy to see that their legacy lives on. I am honestly in awe of the amount of effort that has been put in in creating such an immersive environment and experience for the students. We all love a bit of cheese with our scenarios – we deal with the real world far too much in DF and it often is not the nicest of worlds – but the immersive world created had me laughing out loud. A particular favourite was a virtual helpdesk call that kept you on hold … I was wondering if it would ever get answered! The use of generated speech, cartoon characters and modular building blocks means that immense variation is possible as the world grows -but with reduced effort for each subsequent creation.
A break for lunch – the usual academic conference fare of sandwiches and pizza, fine by all measures, but hardly ground-breaking or Michelin star winning. The coffee was lousy though – but we’re there for enriching our minds, not our bodies!
In the always difficult after lunch slot, Dr Paul Stephens and Danny Werb from Canterbury Christ Church University did a fabulous double act – rudely interrupted by the fire alarm – discussing “Is the Digital Forensic Tool User Interface Broken?” Personally, I think that we can answer this with a resounding yes, but that doesn’t actually solve the problem. Danny’s research into VR-based interfaces drawing from gaming (“Heavy Rain”) and film (“Minority Report”) postulates a more interactive environment that allows for a more joined up investigation approach rather than being heavily flat UI and bogged down with HEX. It’s a very interesting concept and it certainly made for a very interesting presentation. I can’t deny that there are plenty of awful UIs in the industry, but I’m not sure I fancy doing my job in VR! In any case, any discussion of the topic is most valid and will push us forward in interesting ways!
CyberWomen@Warwick hosted their very own, and very successful, conference earlier this year – Sophie Powell and Sarah Tipper (two Warwick BSc Cyber Security students I have been lucky enough to have had the pleasure of teaching) gave an entertaining talk through what their experiences were from the process, what they’ve taken away from it and also the possibility of scaling it out to other Universities to help advance Women in Cyber fields. They’re becoming quite accomplished speakers and other students would do well to take them up on their offer of advice and assistance should it be required in similar events. (If – in reading this – this sounds like it may relate to you, then feel free to drop me a line to si@forensicfocus.com and I’ll make appropriate introductions.)
A brief break from some more of that “coffee” and we were into the home straight – as always, the breaks are a great opportunity to network with the other attendees – there seems to be a bit of a people deficit in the field, as there was a little in the way of poaching people as markers and guest lecturers to fill out various department’s staffing…
Damola Lawal (a PhD candidate from Greenwich) talked to us about his experimental work with regard to some very interesting USB devices – research which has led to a very healthy level of paranoia in him regarding borrowing other people’s USB cables. Very interesting findings regarding the evidence (or lack of it) left behind from the surreptitious use of devices like the “Rubber Ducky” and the O.MG cable. I suspect that this could have filled a much longer slot, and I think a fair few of us would have been very interested to listen to it.
We come, at last, to the closing talk given by a few more Warwick students, this time from the MSc module. The module contains a “Digital Forensics Project Day” – a day-long group project with a task to solve accounting for 20% of the module mark. It’s an interesting task for them to work their way through, and they certainly seem to have valued it as part of their learning experience. The main speaker, Sarah Aktaa, is now a teaching fellow at Warwick, having gained her MSc earlier this year – she was joined by two other students who are in the current cohort.
It was a great opportunity to get together with others in the field and to have an opportunity to hear about the ways that we’re addressing the challenges that we’re all facing. Good to see old friends, and to make some new ones too. I look forward to next year’s event – as soon as I know where and when it is, I’ll share it here!
To see the list of speakers and learn more about them, click here.
[1] It should be noted for transparency, I left Warwick University at the beginning of this year where I had been teaching Digital Forensics amongst other things …
The Digital Forensics Research Workshop was back in virtual format for its USA edition running Monday, July 11th through Thursday, July 14th. Six sessions on memory forensics, similarity hashing, application forensics, live and static system analysis, multimedia forensics, and miscellaneous topics highlighted the 13 papers accepted for presentation. In addition, two presentation sessions showcased six additional topics.
Want to volunteer to be a peer reviewer? The organizers encourage you to reach out here!
As always, the conference made plenty of room for social connection and fun via Monday night’s virtual pub quiz, Tuesday’s three simultaneous Birds of a Feather sessions, and Wednesday’s Digital Forensics Rodeo CTF. Birds of a Feather sessions made way for brainstorming around three topics:
Crypto Harlem’s Matt Mitchell kicked off the event with “Digital Forensics Duty to Protect,” about the need for practitioners to use their skills to find the artifacts needed to effect justice and positive change in the world.
A unique talk relative to previous keynotes Mitchell has given, the content focused on the weaponization of digital forensics. “Digital dictatorship” in particular involves the use of mercenary surveillance malware such as Pegasus and NetWire to allow governments to plant evidence on devices of reporters, activists, lawyers before using forensics to find “irrefutable” evidence of wrongdoing.
Thus, said Mitchell, the need to verify information through open source and traditional digital forensics alike, as well as the need to encourage truly fair trials by making tools and methods available to non-law enforcement entities. Mitchell encouraged researchers’ involvement with organizations like Mnemonic, WITNESS, and the 5am Coalition in Ukraine, saying that any level of skillset is always needed.
The conference’s second keynote came from Samuel Cava, of the FBI’s Multimedia Exploitation Unit which was created in response to the 2013 Boston Marathon bombing. By way of some of the FBI’s biggest cases – the Las Vegas shooting and January 6 among them – Cava spoke about how digital forensics research was integrated and applied to FBI investigations.
Owing to the pace, scale, and scope of massive critical incidents – each one, said Cava, getting bigger and harder to manage, including the risk of damage from deepfakes – there is a dual need:
First, practitioners themselves need open source intelligence (OSINT) type skills to piece together data from many sources, including images, geolocation, suspicious purchases, motor vehicle information, etc. in context of each piece’s collection and use.
Second, to manage all this is the need for automated tools to help investigators organize and track evidence, versus the use of pen and paper; to enable collaborative review with the ability to tag and annotate evidence, as well as organize around the review; and to build more exposable (declassified) systems for multiagency sharing and disclosure.
Cava solicited researchers to contribute to the Multimedia Processing Framework as well as the Triage Import Export Schema (TIES) at GitHub.
Memory forensics was the topic of the first paper session.
In “Memory Analysis of .NET and .Net Core Applications” – winner of this year’s DFRWS-USA Best Paper Award – Andrew Case focused on the evolution of malware and the resulting effort to develop memory analysis capabilities for the “very powerful and widely abused” .NET Framework and its replacement, .NET Core. Case discussed new Volatility plugins that automatically and repeatably target key areas in these runtimes and report suspicious and/or malicious artifacts.

Enoch Wang then followed with “Juicing V8: A Primary Account for the Memory Forensics of the V8 JavaScript Engine.” This talk introduced the first generalizable account of the memory forensics of the engine behind V8, Google’s open source interpreter which enables JavaScript functionality in Chrome. In addition, the researchers offered the V8MapScan Volatility plugin, which helps to reconstruct most V8 objects from a memory image.
These talks were followed by the second paper session, which focused on similarity hashing – as opposed to cryptographic hashing, which detects only identical copies – across big data.
First, Thomas Göbel presented “FRASHER — A Framework for Automated Evaluation of Similarity Hashing.” FRASHER extends the nearly 10-year-old FRASH framework by modernizing it, enabling the evaluation of efficiency in terms of generation, comparison, and compression; sensitivity and robustness; and adversarial resilience.
“ssdeeper: Evaluating and Improving ssdeep” followed with a focus on the first and most common context-triggered piecewise hashing algorithm. Presenter Carlo Jakobs discussed the research team’s assessment of ssdeep, configurations ideally suited for ssdeep’s typical applications, and proposed improvements to make for more stable hash values, a better runtime performance, and a better detection rate.
The third paper session, offered on Tuesday, consisted of two papers that examined application forensics, specifically “alt tech” social networking and instant messaging.
In “Alt-Tech Social Forensics: Forensic Analysis of Alternative Social Networking Applications,” Hailey Johnson described an analysis of Android and iOS versions of Parler, MeWe, CloutHub, and similar apps. She also introduced the Alternative Social Networking Applications Analysis Tool (ASNAAT), which automatically aggregates forensically relevant data from a mobile device forensic image containing alt-tech social applications.
Then, Megan Davis described the “Forensic Investigation of Instant Messaging Services on Linux OS: Discord and Slack as Case Studies,” meant to close a gap in research on Discord and Slack apps on Linux operating systems. The research described a number of accessible artifacts stored in memory, which could be important, Davis said, owing to the pandemic-era trend of people organizing game nights and other activities via these two apps.
Three papers on Live and Static System Analysis featured in the conference’s fourth session, also on Tuesday.
First, Thanh Nguyen presented “Live System Call Trace Reconstruction on Linux,” a description of how his research team’s method non-intrusively enables the analysis of system calls performed by mature ransomware in real time on Linux-based systems.
Then, Stewart Sentanoe presented “KVMIveggur: Flexible, secure, and efficient support for self-service virtual machine introspection.” This architecture uses containers, virtual machines, and network remote access to isolate virtual machine introspection (VMI) in cloud environments, removing speed, functionality, and implementation obstacles in existing research prototypes.
Finally, in “LibDroid: Summarizing information flow of Android Native Libraries via Static Analysis,” Chen Shi described the LibDroid analysis framework designed to compute data flow and summarize taint propagation for Android native libraries, thus closing a gap in other Android static analysis tools by allowing users to identify app security issues such as the use of private user data or hidden functions.
Wednesday’s first paper session featured two papers that fell outside the other categories.
First, in “Digital Forensics-AI: on Explainability and Interpretability of Evidence Mining Techniques,” Abiodun Abdullahi Solanke presented a nontechnical perspective on artificial intelligence, law, and digital forensics strategies toward mitigating mistrust. Solanke covered explainability versus interpretability of closed-box AI models, proposing recommendations for interpretable AI-based digital forensics methods.
Then, Janine Schneider presented “Ambiguous File System Partitions,” which suggested that steganographic data hiding could be applied when two fully functional file systems coexist within a single file system partition. This research integrated “guest” file systems into the structures of a “host” file system in order to test how forensic tools handled the ambiguity. In addition, the research distinguished host from guest based on essential data at fixed positions.
The sixth and final paper session of the conference featured two talks on multimedia forensics. In “Deepfake Noise Investigation and Detection,” Tyanyi Wang proposed a deep neural network as a means to develop a noise-based deepfake detection model. By visualizing deepfake forensic noise traces, the research team demonstrated a distinction between synthesized faces and any unmodified area in a way that statistical evaluation cannot achieve.
Audio background noise was the topic of the following talk, “BlackFeather: A framework for Background Noise Forensics.” There, Qi Li discussed new methods of automatically extracting, separating, and classifying background noises in complex environments via software, thus offering potential new lead sources to investigators.
Following Monday’s and Tuesday’s paper sessions were the presentations: research of interest to the committee which has not (yet) been submitted for peer review.
On Monday, NIST’s Alex Nelson presented “Discovery of digital forensic dataset characteristics with CASE-Corpora.” This community index of available forensic reference and training datasets relies on the Cyber-investigation Analysis and Standard Expression (CASE) Ontology and the Unified Cyber Ontology (UCO) to describe datasets’ forensically relevant qualities: not only where to find data, but also why – in essence, to reconstruct data provenance.
Future plans include integrating CASE Corpora with the Computer Forensics Reference Dataset (CFREDs). Additionally, Nelson encouraged community members to join the CASE development community to help, as well as to download the datasets from GitHub to work with.
Then, Mitch Kajzer presented “Offline iOS Tracking and Remote Wiping” via the “always on” Apple Ultra Wideband (U1) chip, which relies on a short-range, low energy, wireless communications protocol to provide accurate spatial and directional data even when a device is powered off.
Calling the functionality “GPS at the scale of your living room,” Kajzer described the implications for evidence handling and chain of custody, notably whether the U1 chip can accept wipe commands.
On Tuesday, “A Distributed Digital Body Farm for Collecting Deleted File Decay Data” described a remote software agent, the DDBF, which collects content-free and privacy-preserving data about deleted file decay on an active computer system. In this talk, Omoche Cheche Agada described how to use the agent to collect deleted file decay data from geographically dispersed computers, at which point the data can be aggregated and analyzed for patterns of decay – thus whether file recovery is possible.
Following with another perspective on file decay was Dominique Calder with “Building and decaying a file corpus for sub-sector analysis,” which detailed the development of a scalable algorithm that can accurately infer the past presence of a file given arbitrary sectors. Being built to address the problem of big data triage and antiforensic or tampering, the research focuses on sector rather than file hashes to improve data correlation.
The presentation sessions both days also offered “showcase” content from DFIR Review. Tuesday, veteran law enforcement officer and digital forensics analyst Scott Koenig presented “iOS Settings Display Auto-Lock & Require Passcode,” an extensive testing project he started to help out a fellow analyst. His short video reviewed device activity, plists of interest, and overall results. His research can be found here and here.
Wednesday’s showcase featured Geraldine Blay and Alexis Brignoni, whose “Peeking at User Notification Events in iOS 15” explored notification logs for artifacts that can show content even when it is no longer present in the phone. Parsing and reporting were covered as well.
Four workshops ranging from two to four hours were offered between Wednesday and Thursday.
On Wednesday, Forensic Focus attended the two-hour “CASEWorks! by Eoghan Casey and Alex Nelson. Building on Nelson’s presentation about the CASE Corpora, this workshop focused on data mapping, validation, and customization, along with ontology development practices for better community collaboration and an example of how the Hansken project is implementing CASE.
Casey emphasized the need for data provenance in particular to show a full chain of custody. Currently, output can be incomplete or missing, impacting its interpretability and thus its effectiveness in decision-making.
Concurrently on Wednesday was the “Leveling Up with YARA!” workshop, designed to help attendees learn the syntax of YARA rules to assess their accuracy and start to write their own. Volexity’s Tom Lancaster led attendees through a series of layered exercises that laid a foundation for extensibility and future contributions.
Thursday featured two additional four-hour workshops. In “Performing Linux Forensic Analysis and Why You Should Care,” Ali Hadi and Mariam Khader encouraged attendees to consider both incident response and criminal investigation scenarios involving the Linux operating system. Fundamentals of the Linux OS and EXT4 file system; log analysis; and the search, identification and collection of crucial data were covered.
Concurrently, in “Velociraptor – Digging deeper,” Michael Cohen introduced the open source, scalable digital forensic and incident response tool designed to enhance visibility into endpoints and hunt for forensic artifacts across large networks in minutes. Attendees learned how to do this via the Velociraptor Query Language (VQL) on both dead and live systems, as well as common scenarios such as lateral movement detection and hunting Cobalt Strike beacons in memory.
Planning for DFRWS 2023 conferences is underway, with the DFRWS-EU call for papers open until October 10 and presentations, workshops, and posters also available for consideration. DFRWS-EU will be held in Bonn, Germany and virtually during the week of March 20.