Discover how tailored, culturally aware mental health support can help digital forensic investigators cope with the hidden trauma of their work....

20th August 2025
Read the latest digital forensics news – SANS releases DFIR Summit playlist, UAC launches v3.2.0, Neal Ysart discusses the Coalition of Cyber Investigators, and more....read more

20th August 2025
Explore S21 Transcriber: a fully offline, court-ready tool with free 30-day access and training....read more

19th August 2025
Retailers face rising cyber threats—join Exterro's Sept 4 webinar to learn fast, modern forensic response strategies and protect your brand....read more
There has been a lot of buzz around Tor, Bitcoin, and the so-called “dark web” (or “deep web”) since the FBI shut down the underground website “Silk Road” on Oct 1st.
As many of you already know, Tor is a network of encrypted, virtual tunnels that allows people to use the internet anonymously, hiding their identity and network traffic. Using Tor’s hidden service protocol, people can also host websites anonymously that are only accessible by those on the Tor network. Enter Silk Road.
Silk Road was an online black market where you could buy virtually anything, including but not limited to drugs, weapons, credit card data, contract killers, and more. One of the key “features” of Silk Road was that it was only accessible via the Tor network, hidden from the mainstream web.
With $1.2 billion in sales and nearly a million customers, business was good. The other key privacy aspect of Silk Road is that all transactions on the site were via Bitcoin, a distributed, peer-to-peer, and anonymous digital currency that is based on cryptography principles.
Silk Road is gone but there are other online black marketplaces that will take its place, like the Sheep Marketplace or Black Market Reloaded:
These sites are also only accessible via Tor and use Bitcoin to conduct transactions.
Using Bitcoin is fairly easy. You need a Bitcoin client/digital wallet installed on your computer or mobile device. You then need to obtain bitcoins from a Bitcoin exchange such as Mt. Gox and Bitstamp.
To send someone money, you instruct your Bitcoin client to send an amount of bitcoins to a Bitcoin address which will look something like this: 1N52cffvJp8jZRRamegywrLrD7aLjQbapF.
A transaction message is created and electronically signed by the Bitcoin client using your private key. This transaction is broadcast to the Bitcoin P2P network and is “verified” in a few minutes (sometimes up to 10). Once verified, the transaction is complete.
All Bitcoin transactions are stored publicly and permanently on the Bitcoin network – the balance and transactions of any Bitcoin address are visible to anyone. New addresses can be created for each transaction, however, further increasing the anonymity of Bitcoin transactions.
Support for recovering Bitcoin artifacts was added to IEF in version 6.1 (released this past June). Bitcoin addresses can be recovered from a Bitcoin wallet, as well as queries on the Bitcoin network from log files created by the Bitcoin client software.
Here you can see addresses from a Bitcoin wallet, including labels (if applicable) and whether or not the address has been active. When you create a wallet, a number of addresses are automatically created and put in the “thread pool”.
In this screenshot you can see queries on the Bitcoin P2P network. These may or may not relate to the local user’s activity.
In the IEF Report Viewer, when viewing Bitcoin records, you can right-click on a record and then click “Query Bitcoin Block Chain” to look up more information on that transaction/address on the web.
Above is an example of what you might see for a transaction or address. In this example, you can see the amount of Bitcoin (0.005), dates/times, and the recipient of the transfer.
As you can see, Bitcoin is a tough currency to track or investigate. However, knowing which addresses were in a suspect/victim’s Bitcoin wallet and details about transactions can help you piece the puzzle back together.
I hope you found this post useful and wish you luck in investigations involving these technologies.
Are there specific topics you’d like me to blog about? Please feel free to reach out to me directly at jad(at)magnetforensics(dot)com with any ideas you might have. I’m also always open to and appreciative of your feedback, good or bad, regarding our software and how we can make it better for you.
All the best,
Jad and the Magnet team
According to recently released statistics from ICAC, an agency whose aim is to make the internet safer for children, only 2% of reported child protection cases are investigated in the United States each year. Often the media seize every opportunity to disparage forensics organisations, child protection charities and law enforcement agencies for not coming up with more effective solutions to these cases, but the reality is that the investigation of illicit image distribution is a wide-ranging and complex area, fraught with difficulties.
Digital forensics professionals will undoubtedly come across such cases as part of their general workload. Sometimes a case will begin with an investigator specifically looking for suspicious images, whilst at other times the illicit nature of the images will be discovered in the course of an unrelated process. Regardless of the initial push, however, it is undoubtedly one of the most taxing and time-consuming parts of the job…
Oxygen Forensics announces the availability of a new edition of Oxygen Forensic Suite 2013. The Passware Edition of the company’s flagship mobile forensic product delivers investigators a complete evidence discovery solution providing integrated recovery of passwords protecting encrypted files discovered during the investigation.
When analyzing mobile devices, investigators often encounter different types of password protection. Extracting these passwords instantly with Oxygen Forensic Suite is not always possible due to one-way encryption or password hashing. In order to enable access to password-protected information, the new edition integrates two forensic products into a single package, and includes Oxygen Forensic Suite Analyst and Passware Kit Forensic. For a limited time, the new edition is available for a discount representing savings of $999 off the regular price. The discount expires on December 1, 2013. By placing an immediate order, forensic specialists may obtain two powerful set of forensic tools for the price of a single tool.Mobile Forensic Suite with Integrated Password Recovery
To facilitate the recovery of passwords protecting mobile devices backups, Oxygen Forensics integrates a powerful password recovery product into its mobile forensic solution. The new product named Oxygen Forensic Suite Passware Edition takes mobile forensics up to the next level, delivering investigators a fully featured suite that can automatically break or recover passwords protecting various types of information such as encrypted files and containers, password-protected backups, messages and attachments, Web site and social network accounts.
“A mobile device itself is not the only source of evidence. In some cases, it is not available to law enforcement at all” said Oleg Fedorov, CEO of Oxygen Forensics. “Experts have the need to forensically extract data from all possible sources including backups. Partnering with Passware gives our customers access to password-protected information stored in Android and iTunes backups through a single interface”.
Everyday passwords set by most smartphone users are limited in length and complexity due to the inconvenience of using on-screen keyboards. This fact combined with new password recovery capabilities implemented in Oxygen Forensic Suite Passware Edition can often deliver great success rate in reasonable timeframe.
“The proliferation of smartphones throughout enterprise and consumer users often allows criminal behavior to pass undetected without a tremendous amount of brute-forcing the password,” said Dmitry Sumin, CEO of Passware. “The expanded capabilities of Passware Kit Forensic help forensic experts gain access to protected information stored in Android phones quickly. This enables IT computer forensic professionals to easily gain access to data residing on the most widely used smartphones.”
The new product is offered for $999 off retail until December 1, 2013. Customers are encouraged to contact Oxygen Forensics for a quote for Oxygen Forensic Suite Passware Edition.
About Oxygen Forensic Suite 2013
Oxygen Forensic Suite 2013 helps investigators and forensic specialists access and analyze data from a variety of mobile devices such as cell phones, smartphones, communicators, PDA and tablet PCs. Currently supporting more than 7,000 different models, Oxygen Forensic Suite 2013 covers the widest range of mobile devices compared to competition, and allows fully automated acquisition and analysis of supported devices.
The unique Timeline feature offers convenient, single-place access to all activities and movements performed by the user arranged by date and time. Investigators can track user location at every moment, build and map their historic routes, and clearly see all activities performed by the user at each location. Timeline is now available for analyzing DMG images.
Another signature feature of Oxygen Forensic Suite allows investigators to perform a global search on all devices ever analyzed with the toolkit. The global search quickly reveals any connections (e.g. common contacts, exchanged calls, texts or emails) between the phone owners.
Oxygen’s statistical analysis tools allow investigators discover social connections between the users of multiple mobile devices. Calls, text messages and various messengers’ conversations are analyzed to produce charts and tables revealing the users’ closest circle at a glance.
Oxygen Forensic Suite 2013 guarantees zero-footprint operation, leaving no traces and making no modifications to the content of the devices. This makes it the tool of choice among government and law enforcement agencies, security services, and forensic organizations in more than fifty countries.
About Passware Kit Forensic
Passware Kit Forensic is Passware’s flagship forensic tool enabling accelerated recovery of passwords protecting more than 200 file types such as office documents and PDF files, encrypted archives, iTunes and Android backups, Windows system passwords, passwords to Web sites, social networks and mail accounts and many more types of data.
In addition to the recovery of plain-text passwords, Passware Kit Forensic can instantly decrypt encrypted volumes protected by popular crypto containers such as BitLocker, TrueCrypt, FileVault2, and PGP by automatically locating and extracting decryption keys stored in the computer’s volatile memory or contained in memory dump images.
About Oxygen Forensics, Inc.
Founded in 2000, Oxygen Forensics is the worldwide leading maker of the advanced forensic data examination tools for smartphones and other mobile devices. The company is dedicated to delivering the most universal forensic solution covering the widest range of mobile devices running Android, iOS, Blackberry, Windows Phone, Symbian and other operating systems. Law enforcement and government agencies, institutions, corporations and private investigators, help desk personnel and thousands of private consumers rely on Oxygen Forensics products to ensure evidence availability in the event of mobile device data analysis and recovery. Oxygen Forensics customers include various US and European federal and state agencies such as the IRS, US Army, US Department of Defense (DOD), US Department of Justice, US Department of Homeland Security, US Department of Transportation, US Postal Service, US Supreme Court, European Commission, London Metropolitan Police, French National Police and Gendarmerie, PricewaterhouseCoopers, Ernst & Young, and many others. As a result, Oxygen Forensic Suite receives great response at forensic conferences, exhibitions and trainings, and occupies a spot on the top of the list in relevant tests for extracting more data than competitors.
About Passware, Inc.
Founded in 1998, Passware, Inc. is the worldwide leading maker of password recovery and e-Discovery software for Federal and State agencies, Fortune 500 corporations, law enforcement, military organizations, help desk personnel, business and private consumers.
# # #
More information about Oxygen Forensics and its forensic solutions is available at www.oxygen-forensic.com
More information about Passware, Inc. and its password recovery solutions is available at www.lostpassword.com
As part of my third year studying Digital Security,Forensics & Ethical Hacking at GCU, I took part in a group research project to study the artifacts created when using the notes app on an iPad Mini, and if they could be used as evidence. This post is really just going to explain what I did, what I found and how you can go about doing it too.
Equipment used:
I jailbroke the iPads, solely because I wanted to use iFile to view what was happening in real-time, rather than examine the data by backing it up and viewing the file system that way.
I used two wireless access points, so that I could control access to the internet and thus, the ability for each iPad to sync. The computer was used to view the SQLite database that iOS stores the data in, however you can also view the SQLite database in iFile, if you’re lazy.
On the database manager front, I found that when using windows the “SQLite Manager” add-on for Firefox did the trick. On Ubuntu, “SQLite Manager” from the repository was my preferred option.
Overview of the Notes.sqlite file:
The Notes.sqlite file is a sqlite3 file, used by iOS to store all the data regarding each note and the device.
It consists of nine tables :
Methodology:
I carried out seven main tests, each test being based on a different action carried out on a note, repeating each one a handful of times in order to verify the results and findings:
Test 1:
When a note is created, a record is added to the ZNOTE & ZNOTEBODY tables respectively. The ZNOTE record containing information like the Author, Server ID, date created and date modified. the ZNOTEBODY record containing the actual content of the note, stored in HTML format. Before syncing, each non-synced not has a negative Server ID. After syncing, it has a new Server ID, the value of which is the same across both iPads. It’s also noteworthy to mention that syncing has no effect on the creation and modification date stored on iPad 2.
Test 2:
When a note is deleted from iPad 1, the record is dropped from the tables and that’s all that happens. I was hoping that the server i.d would be used to “mark” the note for deletion, but no, it’s simply dropped from existence. After syncing, the same happens on the second iPad. So apart from a missing private_key, there is no way to know that a note has been deleted and there is no way to recover deleted files using any traditional methods.
Test 3:
When a note is modified from the same device it was created on, the database is changed in two ways. The first is that the modification time stamp is updated to reflect the current time and the second is that the note content in the ZNOTEBODY table is updated to contain the new text.
Unfortunately, this means that there is no way to “roll back” to a previous version of the note.
Test 4:
When a note that was created on iPad 1 is modified from iPad 2, the same changed seen during test 3 were observed, however, what was a interesting, is the value stored in the ZAUTHOR field in the ZNOTE table. Before modification, on iPad 1, this had a value of “NULL” after the modification had synced it had a value of “Stewart Wallace […]” where […] is the iCloud email address the account is registered to.
Test 5:
When a note was accessed (but not edited) by the primary iPad, there was no changes to the database, or the modified time value.
Test 6:
When a note was accessed by the secondary device, there was once again, no changes to the database.
Conclusions
From the analysis of one device and its database, it is possible to determine if a note originated from that device and if it was edited from another secondary device.
If you have more than one device and database, you can cross reference them to deduce what device created the note, if a note has been edited, what device edited it, sadly, it is not possible to see what was edited or at the moment – recover any deleted notes.


Nuix, a worldwide provider of information management technologies, today announced it has appointed Rob Attoe as Senior Vice President of Investigations Training and Services. United States-based Attoe will be in charge of building and delivering training course content for Nuix customers and partners in the global digital investigations community.
Attoe has more than a decade of experience developing digital forensics and decryption training programs, most recently as Director of Training at AccessData. He has worked as a Computer Crime Specialist with the US National White Collar Crime Center, where his primary focus was developing a curriculum on file system analysis and automated forensic tools, and with the Kent Police as a Forensic Computer Analyst.“Rob’s experience will ensure our training curriculum meets the industry’s highest standards and we are delighted to welcome him,” said Dr Jim Kent, CEO, EMEA and Global Head of Investigations at Nuix. “Rob is the latest in a long line of digital forensic experts who have joined Nuix, making our investigation team an industry powerhouse.”
Attoe participates actively in the global digital investigation community. He is a certified member of the International Association of Computer Investigative Specialists (IACIS) and has instructed at its annual conference. He regularly presents at international digital forensics events including the High Technology Crime Investigation Association, Department of Defense Cyber Crime and F3 conferences.
“I am excited to join such a forward-thinking organization that is driven to deliver innovative solutions for the digital forensics community,” said Attoe. “With my experience and Nuix’s technology, I have an opportunity to deliver the industry’s highest quality instruction that prepares trainees for the challenges of processing, searching and understanding the vast amounts of data they will encounter.”
About Nuix
Nuix (nuix.com) is a worldwide provider of information management technologies, including eDiscovery, electronic investigation and information governance software. Nuix customers include the world’s leading advisory firms, litigation support providers, enterprises, government departments, law enforcement agencies, and all of the world’s major corporate regulatory bodies.
According to recently released statistics from ICAC, an agency whose aim is to make the internet safer for children, only 2% of reported child protection cases are investigated in the United States each year. Often the media seize every opportunity to disparage forensics organisations, child protection charities and law enforcement agencies for not coming up with more effective solutions to these cases, but the reality is that the investigation of illicit image distribution is a wide-ranging and complex area, fraught with difficulties.
Digital forensics professionals will undoubtedly come across such cases as part of their general workload. Sometimes a case will begin with an investigator specifically looking for suspicious images, whilst at other times the illicit nature of the images will be discovered in the course of an unrelated process. Regardless of the initial push, however, it is undoubtedly one of the most taxing and time-consuming parts of the job.
Internet Watch Foundation – on the frontline
The Internet Watch Foundation in the UK understands the issues around child protection investigation better than most. The IWF fields reports from the public about illicit imagery around the internet, and has been dealing with potentially criminal internet content since 1997. The organisation receives around forty thousand submissions per year, and manages to deal with around ten thousand of these.
The psychological repercussions of constantly viewing indecent images of children are not to be overlooked. Most of the cases submitted to the IWF involve more than one image, and the vast majority of content is recycled, popping up over and over again in multiple searches. There is perhaps a sense of becoming, if not immune, at least detached over time, purely to be able to deal with the type of content that must be viewed on a daily basis. A quick scan through any forensics forum will verify that many investigators find it ‘wears them down’ over time, and the need for some form of on the job counselling is widely discussed.
Recognising this, the IWF provides counselling sessions once a month for all employees who deal with child protection issues directly, and indeed frequent counselling seems to be standard procedure in many investigative and law enforcement agencies who regularly come across such content.
But it is not only the psychological challenges that create difficulties when dealing with child protection. The sheer volume of images to analyse, the often wide-ranging nature of the perpetrators, and the difficulty of actually identifying victims means that many such cases go unsolved.
Resource challenges
Investigators frequently have to wade through a huge number of images just to understand whether any inappropriate content is actually being consumed. This means that often, forensic organisations simply do not have the man power to scrutinise every file, analysing it for indecency of content, similarities with other cases, profiling of victims, and so on. We caught up with Ken Mizota from Guidance Software and asked what the main resource challenges are when dealing with child exploitation cases.
“Resources to investigate child exploitation cases are quite scarce relative to the volume of material to review”, Mizota remarks. “ We’ve learned from our customers doing live casework that child pornographers are quick to adopt and utilize new technology. If a child pornographer can add to their collection because the storage technology is more affordable, they will. If technology makes it easier to create or publish more child pornography, they will readily use it. As a result, even small cases easily contain hundreds of thousands of images. Not all images are evidence of child exploitation, but buried in the thousands of images, there may be a victim who needs help.”
Forensic software solutions
So what can be done? Unfortunately there is no one-size-fits-all solution. But there are some pieces of software available that can make scanning images easier, which ultimately reduces the size of each caseload from an entire hard drive’s worth of content down to a handful of images that have been marked as potentially relevant. Investigators can then scan through these for illicit content and ultimately decide whether to continue with the line of enquiry.
Companies such as Guidance Software and AccessData are constantly working to improve on these issues from a technological angle. Currently available packages such as EnCase, Image Analyzer and Forensic Toolkit (FTK) will scan a hard drive for images that appear to contain bare skin, for example, and bring back a number of results for an investigator to look into further. Mizota elaborates on the role of software in alleviating the consumption of pictures of child abuse:
“Digital investigation tools can help to not only expose important evidence, but focus the investigator’s precious energies on understanding the data. Sophisticated data recovery, file carving and signature-based detection expose evidence and categorize known content.
In contrast, a signature-based approach can only eliminate known content. Known content means previously identified exploitative material (e.g. images). Law enforcement agencies like DHS and FBI and even Interpol maintain libraries of hashes of previously identified child pornography. This helps them identify material that is being traded/collected.
So, what about the unknown or new? Digital investigation technologies are available that perform analysis of pornographic materials themselves, and do so faster and more efficiently than ever before. Technologies like EnCase, working together with Image Analyzer, focus the investigator’s effort on the most relevant data, to not only make a case, but shed light on unknown victims.”
And what does the future hold for this area of digital forensics? “I think it is safe to say that advances in technology and communications have outpaced investigative capabilities, factoring in tooling and resources. The percentage of cases that can be investigated promptly is increasing, but the volume marches on steadily. Increasing percentages is positive, but as volume grows, the gross amount of unsolved cases or unknown victims also grows.
The success or failure of child exploitation investigations within digital forensics hinges on cooperation and collaboration. Child exploitation is fostered by technology and also crosses borders and all walks of life. The only rational way to solve such problems is by working together across technologies (from hard disk investigation tools, to image and video analysis, to mobile device forensics) and organizations.
First, and I think foremost, there are initiatives underway within law enforcement communities to share information, collaborate on best practices and techniques, and work together in substantive, scalable ways, across municipalities, states, and even countries. These victim identification initiatives bear the promise of increasing the collective knowledge and expertise of child exploitation investigators. Second, organizations like Guidance Software that build technology, will recognize that through collaboration, and working together, such diverse mutagenic problems can be solved. EnCase and Image Analyzer working together are examples of this approach: Two leading technologies, that both excel at what they do, collaborating to make the work of investigators less laborious and more productive.”
A growing problem
Just how large a problem is the sharing of indecent images of children in the modern age, though? A recent article from the BBC notes that the consumption of pictures of child abuse is at an all-time high. Peter Davies, the director of the Child Exploitation and Online Protection Centre (CEOP), estimates that around fifty thousand people in the UK alone will possess indecent images of children this year, and that 81% of the children featured will be under the age of ten. In the USA, PROTECT’s latest figures show that 300,000 people are trading indecent images of children at any one moment.
Sobering statistics indeed. And according to those who work in the field, the problem only seems to be growing, thus making it even more important for new forensics software packages to take indecent image analysis into consideration. Of course, no piece of software is infallible, and it is possible for files to be missed during a search, but this could just as easily happen with human error, and at least the option of not searching an entire hard drive manually is now open to investigators in digital forensics cases.
Magnet Forensics has released the Internet Evidence Finder (IEF) Logical Evidence File Creator for EnCase v7. The IEF Logical Evidence File (LEF) Creator is an EnScript designed to create an LEF from a pre-existing IEF case folder. The goal of this EnScript is to allow an examiner who has run IEF separately from EnCase to later incorporate the findings into EnCase v7. Running this EnScript from EnCase v7 creates an LEF that is automatically added into EnCase.www.youtube.com/embed/UUazzKoJCoY” frameborder=”0″ allowfullscreen>
Download the Tool
If you already use IEF you can download IEF Logical Evidence File (LEF) Creator for EnCase v7 directly from the Magnet Forensics website here.
This is the third EnScript released by Magnet Forensics that allows you to integrate IEF into your EnCase workflow. The first one was released in May 2013 and was designed as a stand-alone EnScript for EnCase v6 & v7. You can read the details here.
The second was a module specifically designed to be installed and used as part of the EnCase v7 “Process Evidence” option. You can read more about that EnScript here.
Using the Tool
Let’s assume I have a case where I have run IEF separately from EnCase and searched for Internet artifacts:
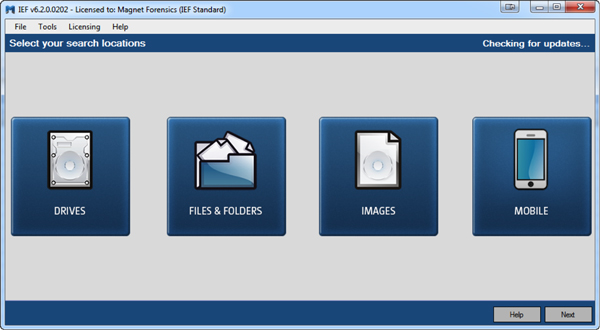
Once IEF is completed, I will be presented with the IEF report viewer screen to review the found artifacts:
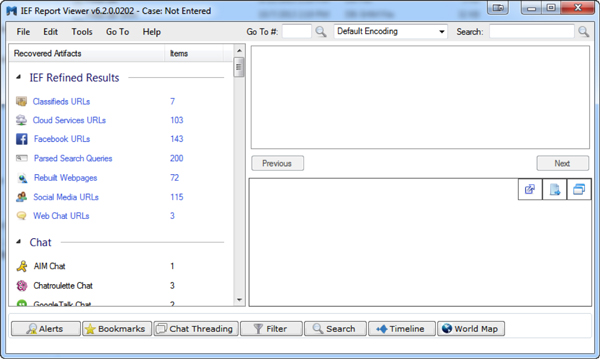
Let’s now assume there are some artifacts that IEF found that are relevant and I want to include them in my overall EnCase processing/searching/reporting. I can simply run the EnScript from EnCase v7 and it will ask me to point to the IEF case folder (the folder structure that IEF creates and places all the output files in):
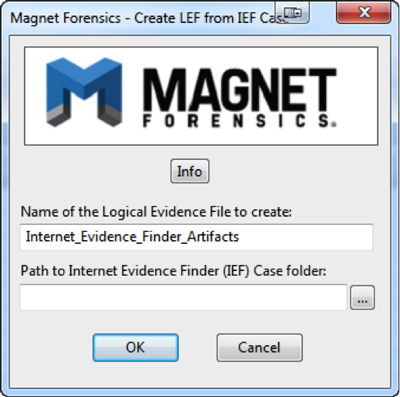
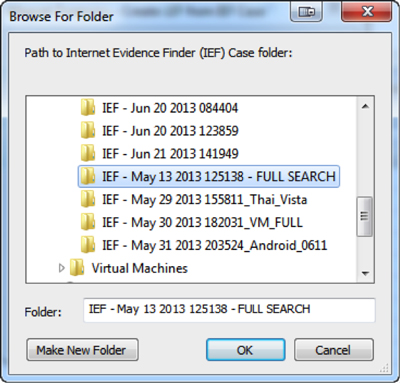
Once I have navigated to and selected an existing IEF case folder, the EnScript will create an LEF in that same folder and then try to add it into the current case.
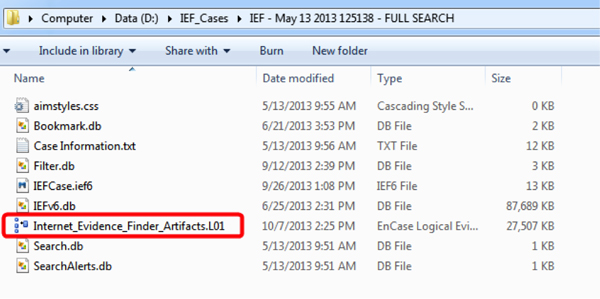
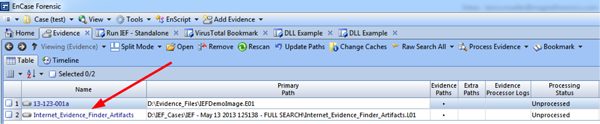
You can now process/review/search/bookmark any of the artifacts that IEF found when you ran it in a stand-alone mode, but have now incorporated the artifacts into EnCase via a logical evidence file.
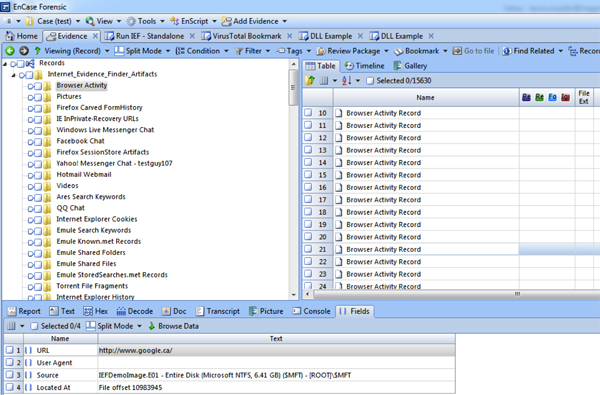
As always, I appreciate the feedback, comments or questions.
You can reach me anytime at lance(at)magnetforensics(dot)com
by Hannu Visti
Creating test material for computer forensic teaching or tool testing purposes has been a known problem. I encountered the issue in my studies of Computer Forensics at the University of Westminster. We were assigned a task to compare computer forensic tools and report results. Having already analysed test images by Brian Carrier (http://dftt.sourceforge.net) over and over again, I found myself creating images manually, which appears to be the best and only way of doing this. One of my lecturers, Sean Tohill, confirmed this is indeed the case and a test image generator is long overdue.
The need for such a tool is twofold. In educational setting, the problem of plagiarism can be mitigated by giving each student an individual image to analyse. In application quality testing, one of the tests should be to feed several similar but not identical images to the forensic tool, and compare results, which should be identical…
Introduction
Creating test material for computer forensic teaching or tool testing purposes has been a known problem. I encountered the issue in my studies of Computer Forensics at the University of Westminster. We were assigned a task to compare computer forensic tools and report results. Having already analysed test images by Brian Carrier (http://dftt.sourceforge.net) over and over again, I found myself creating images manually, which appears to be the best and only way of doing this. One of my lecturers, Sean Tohill, confirmed this is indeed the case and a test image generator is long overdue.
The need for such a tool is twofold. In educational setting, the problem of plagiarism can be mitigated by giving each student an individual image to analyse. In application quality testing, one of the tests should be to feed several similar but not identical images to the forensic tool, and compare results, which should be identical.
Designing and writing such a tool became my MSc dissertation project, which I have now completed, and Mr Tohill became the project supervisor. One of the outcomes was an application, which creates images based on a scenario defined by the user. Each image representing the scenario is slightly different but they should all be equal in complexity, allowing their use in education and software testing.
This article describes the project and introduces the resulting application, which I have released under GPL for anyone to use or modify. The tool is available on Github (https://github.com/hannuvisti/forge.git). It is guaranteed to work on Ubuntu 12.04 but other linuxes are probably ok as well as long as they have /dev/loopX devices for loopback mounts.
Design principles and choice of tools
The original design had two objectives: to create forensic test images based on scenarios with a random element added, and to design the tool in such a way that it can be easily extended without modifying existing code. This led to the following set of requirements:
NTFS suits well to object-oriented programming due to its design. Due to time constraints, programming languages and tools were not thoroughly evaluated. After a short period of tests and prototyping, I chose Python 2.7.x as the programming language over Java, mainly because of Java lacking unsigned variables.
User interface and database connectivity was built with Django. Django is a complex framework but its built-in “admin” interface gave the database administration part used in scenario design without programming effort.
Building a scenario
The only requisites and preparatory actions are database initialisation – in practice inserting file system and data hiding method information to the database for modularity purposes – and uploading of raw material files. The application provides means to complete these tasks. Database initialisation should be done once after initial installation. Raw files can be uploaded any time and shared between scenarios. Raw files are categorised to “trivial files” and “secret files”. Trivial files are used as bulk to populate the file system with irrelevant information. These files are categorised automatically by their kind; picture, audio, executable, document etc. Secret files are the ones used in data hiding methods. The user must assign a numerical “group” to these files, for reasons that will become apparent later.
Case
The core of a scenario in ForGe is called a case. Case defines file system level parameters. Currently only NTFS is supported, FAT is already in the pipeline. Each case can create several images that all fulfil the overall scenario but are not identical.
Trivial strategy
Trivial strategies instruct the creator how to build the bulk or uninteresting part of the image. There can be as many trivial strategies in a case as the scenario requires but at least one trivial strategy must be present. Secret strategies generally require “raw material” on the image and this raw material is provided by trivial strategies. Individual files are chosen randomly from the trivial file repository according to “kind” parameter.
Secret strategy
Secret strategies implement data hiding methods to images. Currently implemented data hiding methods are:
While a trivial strategy places several files to the image, a secret strategy always operates on exactly one file, which is chosen from the secret repository according to a “group” parameter. If a file is unique in its group, the file is always placed on the image. This allows scenarios where all students must locate certain files, but also scenarios, where the file is chosen randomly from a pool.
Hiding methods have additional “action” and “action time” parameters. If these are present, MACE timestamps are modified to correspond to the chosen file action, for example read, copy or rename.
Timeline management
ForGe manages timelines by modifying raw file system data on an unmounted image. This avoids contamination of timestamps, where a disk operation to modify files or timestamps change one or more timestamp parameters. On NTFS, both $STANDARD_INFORMATION and $FILE_NAME attribute are modified to correspond to file time or action time. The current version does not modify timestamps in directory indices but I will add this to a near-future version.
A case can contain “time variance”. If this is set to 0, every image gets an identical timeline. Upon a non-zero time variance parameter, a number is chosen randomly between 0 and time variance parameter to each individual image. This represents number of weeks added to each time attribute on the disk. The benefit to have time variance in weeks is in preservation of time of day and day of week. If an educational scenario were based on something happening on a night between Saturday and Sunday, this would be the case on every image, just different weeks.
Results
ForGe reports either success or failure for each created image. Failures can occur on some or all images if for example the file system runs out of space. ForGe can also be used to print a “cheat sheet” to display the contents of an image.
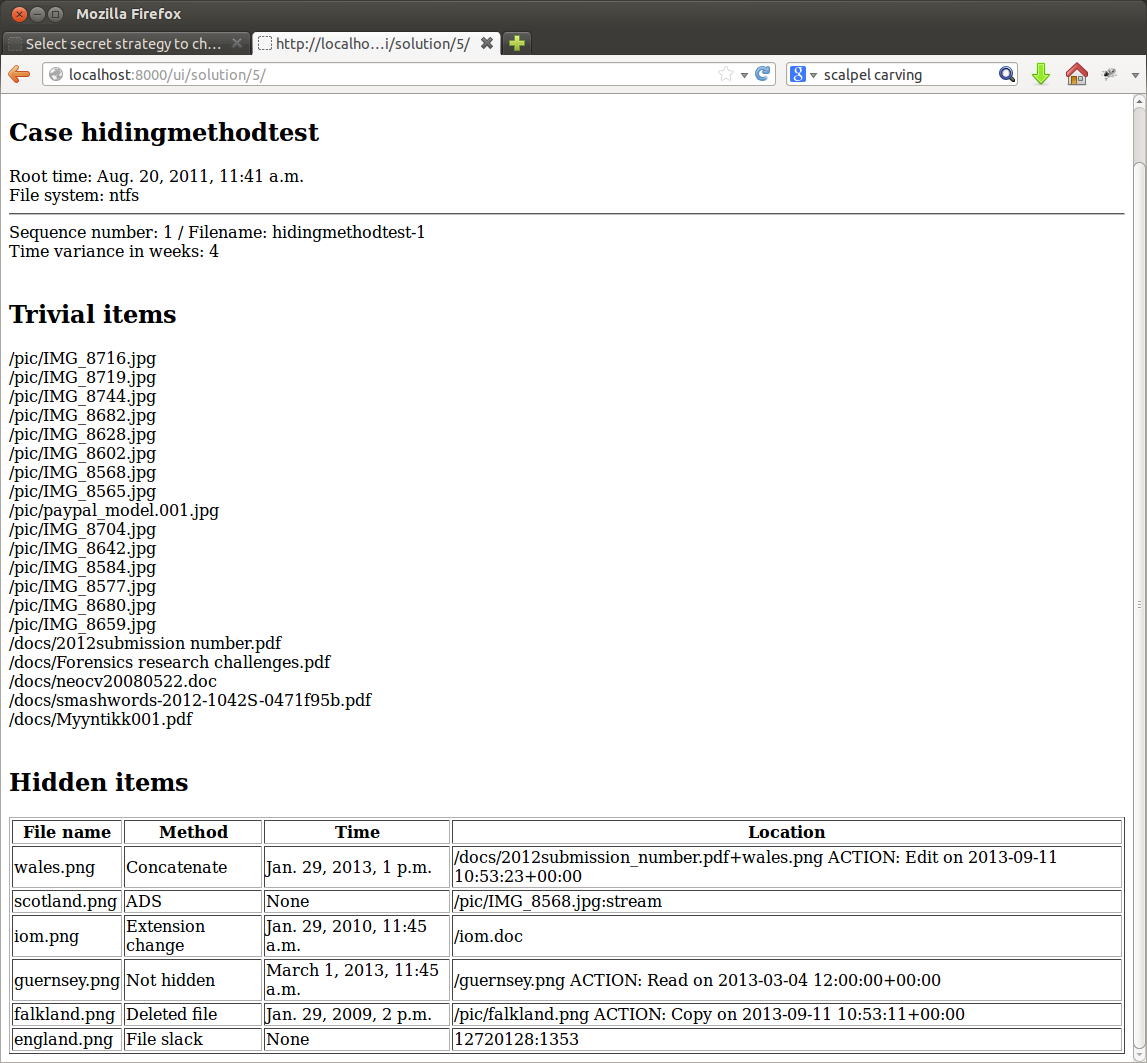
The cheat sheet displays the results of trivial strategies (/pic and /docs directories). Hidden items explain, which files have been hidden and where. For example, scotland.png can be found in an alternate data stream of file /pic/IMG_8568.jpg. England.png is hidden in file slack and could be extracted with command
dd if=hidingmethodtest-1 bs=1 skip=12720128 count=1353 of=england.png
Targets and locations for hidden items are chosen randomly, making each image representing the scenario similar but not identical. The images should be equal in complexity as well, as the same data hiding methods are used throughout the scenario, only locations, timestamps and possibly source files vary.
Extending ForGe
To create a new data hiding method, a new Python class must be created. The class interface is very simple and included in documentation. Basically, the class must implement a method hide_file that takes the file and parameter array as parameters, and returns a set of instructions or raises an exception in case of failure. This new class must be declared in database but existing code needs not be modified.
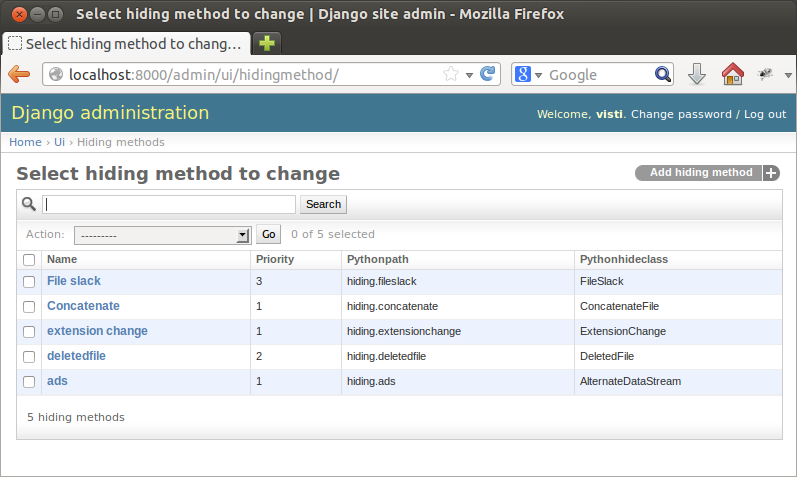
The image illustrates this. The required database elements are path to the file to be included and name of the data hiding class. Priority must be set as well and equal priorities are allowed. This is to ensure the image creation does not contaminate itself. For example, if a file were hidden into file slack and the file deleted, and then another file would be written on the image, it is possible the file would be overwritten. Thus, priority one methods are those that modify a mounted file system directly. Priority 2 handles deletions and priority 3 unmounted file system raw modifications. More priorities can be set if needed, this is the current setup.
File systems can be added in a similar way but the interface is more complex. Documentation to do so is included in ForGe documentation.
Conclusion
ForGe is a tool to create relatively simple test images rapidly. Creating ten images takes less than a minute. Its limitation currently is its focus on single files. If more complex structures, for example web browsing history, need to be included, ForGe is not able to do that with reasonable amount of work. Even in those cases, ForGe would speed up creation of the base images.
Pros:
Cons:
This was an interesting project to do and I am currently working on FAT16/32 extension. I will also add modification of directory index timestamps soon. NTFS is a versatile file system that allows complex timestamp manipulation; ForGe tries to leave timeline as uncontaminated as possible and is able to use some of the more complex NTFS timestamp oddities.
I would be delighted to hear comments and improvement requests.
Hannu Visti
The level of sexual abuse and violence carried out on children whose suffering is posted on the internet “seems to be getting worse”, [UK] MPs have heard. Child Exploitation and Online Protection Centre director Peter Davies said victims appeared “to be getting younger and younger”. He told the Culture, Media and Sport Committee the dissemination of pictures of abuse had become “industrialised”. Most victims were under the age of 10, with images including rape, MPs heard.
Mr Davies said the biggest transfer was directly from “peer to peer”. But much of the “worst we have seen” was distributed via the “hidden internet”, which required special software and evaded search engines – and was also used by criminal gangs to organise the drugs trade…
Welcome to this round-up of recent posts to the Forensic Focus forums
Forum user EricZimmerman shares some imager speed test results.
What are ‘advanced forensics concepts‘ within the digital forensics realm?
Forum users discuss digital evidence storage ideas.
Forum member trewmte explains why it’s important to use mobile forensics tools.
A poll about the most appropriate attire for working in forensics provokes discussion.
Is cell tower analysis ‘junk science’? Chime in on the forum.
What are the best forensic tools to use on Chinese phones?
Forum members discuss validating the integrity of data when testifying in court.
There has been increased coverage of cyber bullying in the media recently. How large a problem is cyber bullying? Is it really growing as fast as the media seem to suggest?
When the tragic deaths of young people such as Hannah Smith and Daniel Perry hit the headlines, the spotlight is rightly focused on social networking sites and how bad they are and what can be done to prevent further deaths. Because of the publicity, it appears that all of a sudden social media has become a problem, yet the truth is that concerns about young people inappropriately using social networking sites have never gone away. Schools can vouch for this in the increased number of incidents they deal with; almost always at the centre of bullying incidents is a social network site or messaging service such as Ask.fm. As was the case in the summer with Ask.fm, there was a public outcry to get the site closed down, but this is not the answer….
HEA STEM: Teaching Computer Forensics is the 8th workshop on Teaching Forensics, the last 4 of which have been held at Sunderland. The workshops have been successful at bringing academics together to discuss the particular challenges in teaching computer forensics, share best practice and discuss opportunities for collaboration in teaching and in research.
The focus for the 2014 event is to continue with the themes that have developed and evolved over the last few years and explore ways in which to enhance teaching and learning opportunities for students studying computer forensics, especially in assessment and feedback, employability and success. The workshop is an opportunity for academics and students in the computer forensics subject area to address the current issues and challenges in a number of themes including (but not exclusive to) student experience, student retention, computer forensics research, new technologies, new computer forensics themes, legal developments, ethics, accreditation and employability…
 Carole, you're currently a trustee for BulliesOut. How did you become involved with the charity?
Carole, you're currently a trustee for BulliesOut. How did you become involved with the charity?
I first heard of BulliesOut through being involved in the charity Children in Wales and contacted the CEO, Linda James, via LinkedIn. We met as I was interested in what the charity did and what involvement the charity had with schools and other professionals working with young people. I was impressed with the dedication of Linda and her desire to get the message out there to young people that no-one has to put up with bullying. The charity looks at all aspects of bullying, working with the bully as well as the victim and also the bystanders who have a crucial role to play. BulliesOut operates in other countries as well as the UK but it was encouraging to learn that it is a Wales based charity and one that is well respected. I was asked to become a Trustee, and although I was not sure what being a Trustee involved, I was happy to join the team. I promote the charity as much as I can with other professionals and young people and although my time is limited due to working full-time and my University studies, I do what I can.There has been increased coverage of cyber bullying in the media recently. How large a problem is cyber bullying? Is it really growing as fast as the media seem to suggest?
When the tragic deaths of young people such as Hannah Smith and Daniel Perry hit the headlines, the spotlight is rightly focused on social networking sites and how bad they are and what can be done to prevent further deaths. Because of the publicity, it appears that all of a sudden social media has become a problem, yet the truth is that concerns about young people inappropriately using social networking sites have never gone away. Schools can vouch for this in the increased number of incidents they deal with; almost always at the centre of bullying incidents is a social network site or messaging service such as Ask.fm. As was the case in the summer with Ask.fm, there was a public outcry to get the site closed down, but this is not the answer. Whilst publicity about messaging services pushes for stricter monitoring and moderation and to take more responsibility for the care of its primarily young users, educating young people about their behaviour online is vital in driving home the message about safer use.
Following the deaths in the summer of Hannah and Daniel, the media has been saturated with news stories about young people and social media and there is a danger of overloading the public with information and nothing being done. At the heart of all bullying incidents are the young people themselves who are both the victims and perpetrators, and it is this that needs to be addressed. If cyber bullying is allowed to continue online without any redress, the situation will only get worse as the speed of technological advances will continue to grow. The morality of young people is compromised when they communicate on social media sites and they have no boundaries. It is very easy to get carried away saying things to other people without realising the impact of their words.
You also teach internet safety to young people, parents and carers. What made you decide to pursue this role?
When CEOP was founded in April 2006, Facebook was in its infancy yet I had already started to deal with issues relating to the social networking site, but not on the scale that I am today. I attended a CEOP ThinkUKNow training course in 2007 which allowed me to deliver their resources to students in all Key Stages, and later that year I received the CEOP Ambassador training which enabled me to cascade the training to other professionals that allowed them to deliver resources to students. To date, I have delivered the CEOP program to over 2,754 students and have also developed my own resources to ensure that my lessons are kept up to date with the current trends which are evolving at a rapid pace. I also deliver assemblies to students when specific issues arise and I need to ensure my students are made aware of current concerns and know what to do to safeguard themselves. Students who are concerned about issues raised during assemblies or lessons I deliver will come to see me confidentially to discuss any worries they have about their online privacy and together we look at their networking site(s) to ensure they have adequately protected themselves online.
It also became evident through my involvement with young people and parents and carers, that their knowledge base of the usage of social networking sites was quite limited, so I started talking at Parents’ Evenings and plan to do more in October, both in the school I work in and the local Primary school. Year 7 students (aged 11-12 years) are entering secondary school already on Facebook and have been in possession of a mobile phone for many years, yet do not have the maturity to deal with problems when they go wrong and it is for this reason that I continually drive the message home to students, staff and parents about safer use online and what to do when things go wrong.
What are the main points you try to get across in your internet safety sessions?
Firstly I state that the internet is a fantastic place to explore and in safe hands, it is a harmless environment to be. There is a fine line to be drawn when teaching internet safety as you do not want to scare young people off using it or being fearful of it but at the same time, you need to equip them with the appropriate tools to safeguard them and give them an awareness of when things are not right. The lessons I deliver are interactive and get them to reflect on their own behaviour online and look at how their actions or their friends’ actions could potentially place them in danger or compromise their well-being. For instance, I advise them not to post pictures of themselves as their profile pictures on Facebook as it is public by default and even if their settings on the site are private, they can be traced just through their picture. I also strongly advise against posting a picture of them in their school uniform as they can be identified by their uniform, particularly their school tie.
It is often reported in the media that young people should report any inappropriate activity online to the relevant providers of the sites they are using. But rarely are the young people told how to do this and what happens when they have had to report, for instance, to Facebook. I cover this in my lessons and go through who they are reporting to, who reads the report, who will contact them and what happens following them being contacted. Young people are often put off from reporting as they are unsure what will happen and even if they are the victim of abuse online, they often feel they are to blame and will therefore not report it and will keep it to themselves. There is also a fear that the situation will be made worse if they report it, but they are reassured that they are doing the right thing by reporting it as not only are they preventing themselves from being a victim, they are also protecting peers who may go on to experience cyber bullying.
I encourage students to carry out vanity checks by searching for themselves to see what comes up and how easy it is to find them and also what information is out there about them. I address the level of privacy and demonstrate how to protect their social media sites by showing them how to navigate the platforms they are using. Following my lessons with the students they often come to see me privately to ask me to go through their settings with them. This gives me a great deal of satisfaction as I know they have taken on board the seriousness of my message which allows them to use the internet in the knowledge that they are keeping themselves safe. I also deliver lessons on sexting, trolling, safe passwords, grooming, geo location, messaging applications, and gaming, and address the privacy settings in each of these areas to maximise young people’s safety online.
You must come across some disturbing subject matter in the course of your work. How do you cope with this side of things?
It can be difficult at times and sometimes all I want to do is be alone to work issues through by myself. It is difficult to switch off your feelings when you leave work to go home. Due to the confidentiality aspects of the role, you cannot share what has occurred with anyone other than a line manager and this can be very isolating. However, I know that I have safeguarded a young person and that is my main priority as a child’s welfare is paramount, so in that respect, it gives me a sense of satisfaction that I have done a good job. The role requires a level of on the spot decision making and this can be stressful at times but the decision is made in the best interests of the child.
Do you think issues related to cyber bullying and internet safety will improve for future generations, or might they get worse as technology continues to evolve?
Technology is growing at an alarming rate but the maturity of young people using social media platforms is not, and therein lies the problem. There is an element of detachment from what young people are doing online; they are desensitised to the potential risks they are experiencing and feel that it is just something they have to put up with. They are afraid to report bullying incidents for fear of the situation getting worse, therefore they take on the problem themselves and keep quiet about it which only makes matters worse as the bully perceives this as weakness and continues to bully them. As educators, we need to instil morality online in the same way we do in the ‘real’ world. We would not treat anyone in the real world the same as we would online as it would not be accepted, yet this is what happens. The veil of anonymity gives a false sense of security for hiding one’s identity and a heightened sense of bravado to act in a bullying manner, yet they would not have the courage to do this face to face. The interactive lessons I deliver in school bring home the reality of the impact this has on a person on the receiving end of such behaviour and makes them think about the conduct of their own behaviour online.
Keeping parents and carers involved in education about internet use and the applications their children are using is key in educating and safeguarding young people. The internet is here to stay and the so called digital native and the digital immigrant of today must set the example for good behaviour to the future generations. Young people copy adult behaviour and if parents are attached to their mobile devices or constantly working on their laptop at home, it goes without saying that young people will perceive this as normal behaviour and react when told to not spend so much time using their devices when they see their parents doing exactly that. Lessons in school must concentrate on the adverse excessive usage of social media, what exactly their digital footprint means for them in the future and how negative behaviour online can jeopardise their future career plans. I recently ran an assembly on this with Year 10 & 11 and it gave them a different perspective on how negative behaviour can look to other people, especially if employers check their profiles when applying for a job; comments made to people on social networking sites that are threatening or bullying do not give a good impression about the character of that person.
Schools need to revise their anti-bullying policies and include action points regarding cyber bullying and what steps should be taken following reported incidents of cyber bullying. Students must be made aware of the consequences of their actions and that cyber bullying will not be tolerated in any shape or form. Open, transparent communication with service providers, educators, parents and most important of all, young people, on issues related to online conduct is needed so that cyber bullying is not something that only reaches the public attention when a tragedy occurs. We need to talk to our young people and encourage them to talk to an adult when things are going wrong, whether it be the bully or the victim.
What do you do to relax and unwind in your spare time?
Spare time? I rarely get any! I ensure I make the time to go to the gym several times a week, attend salsa classes a few evenings a week as well as walking and mountain climbing. I have just started running and am building up my time I spend running not walking at a fast pace! I enjoy attending a monthly philosophy café and will be speaking at the café in December on the philosophy of bullying. I actually research and read up on child protection and sexual exploitation of young people in my spare time as I never really switch off and I am in my final year of a criminology degree after 6 long years so maybe next year I will find more time to relax, though I plan to continue with my Masters so who knows when I will truly be able to relax and unwind. I do not like being idle so relaxing does not come easily for me and I use my ‘free time’ to update my lessons and literature to give myself a head start on the trends of social media currently being used by young people.
If you are concerned about issues related to cyberbullying or child protection, the following organisations can help:
BulliesOut – BulliesOut
CEOP – CEOP
Latest version of IEF uniquely addresses the challenge of identifying, recovering and analyzing mobile chat data.
Magnet Forensics, the global leader in the development of digital forensic software for the recovery and analysis of Internet evidence from computers, smartphones and tablets, today announced the release of INTERNET EVIDENCE FINDER™ (IEF) v6.2. The latest release adds new features, new Internet artifacts and artifact updates for both IEF Standard and IEF Advanced editions. Newly introduced in IEF v6.2 is the Dynamic App Finder feature. Available for IEF Advanced, it is a novel approach to data recovery from mobile chat applications that enables forensic professionals to find more evidence, faster.[image “http://www.magnetforensics.com/wp-content/themes/magnetforensics/_common/images/FF_banner_62announce.jpg” not found]
Dynamic App Finder
Data recovered from mobile chat apps is critical to many forensic investigations. However, with thousands of mobile chat apps in use today and a steady stream of new apps emerging, identifying, recovering and analyzing mobile chat data is a significant challenge and has become a time consuming duty for forensic professionals.
Dynamic App Finder is a new feature of IEF Advanced that searches for any potential mobile chat app databases that can be found on images or file dumps of iOS or Android mobile devices. It identifies the app name and maps the four key fields required to interpret results from most chat apps; sender, receiver, date/time and the message. At the conclusion of an IEF search, Dynamic App Finder displays the names of the discovered chat apps along with the recommended field mapping for each chat database. Field mappings can be accepted as displayed or modified, and are saved by IEF for use in future cases. Full search results with all recovered records for each chat app are displayed in IEF Report Viewer.
Dynamic App Finder enables examiners to find chat messages from potentially thousands of apps, regardless of how new or obscure they might be.
New IEF Platform Features
The platform enhancements in IEF v6.2 include:
IEF Standard Edition Updates
New Internet Artifacts:
Updated Internet Artifacts:
IEF Advanced Edition Updates
All IEF Standard artifacts are included in IEF Advanced.
New Mobile Artifacts:
Updated Mobile Artifacts:
Learn More:
Pricing and Availability:
The world of digital forensics involves the use of a very diverse array of tools, some highly specialized and technical and others pretty simple, as we all know, and these tools are constantly evolving as the digital landscape itself changes and becomes more complex (and more defensive if we’re also talking about those who try to cause harm or conceal their digital footprints). One of the latest of these tools to enter the market and become useful to analysts, educators and students of the computer forensics industry has been none other than the now famous Google Glass.
These voice controlled glasses, which basically act as a sort of very sophisticated wearable computer, with its own applications and OS interface, can be worn and used in any place with a wireless connection of some kind. Users can integrate their glass with their personal preferences in their Google accounts, use them to find directions, look at interactive maps and access a wide assortment of online information about the physical world that’s actually around them at any time.
In essence, the vast amount of data access available thanks to the Google Glass interface makes them an excellent tools for technical work of any kind and especially powerful tools for those working or studying in the STEM fields (Science, Technology, Engineering and Mathematics). Additionally this same quality, amongst others, makes Google Glass a potentially powerful tool when it comes to digital security in the private, government and corporate sectors. Here are a few reasons why.
Education
Prospective students of forensics are faced with the moderate but constant dilemma of absorbing theory and technical educational materials on data protection and recovery while then having to apply them in the real world in a way that fluidly flows off from what they’ve learned.
Google Glass by its very nature makes this process capable of being run much more smoothly and efficiently than ever before.
A student of computer science and forensics in particular can perform field training on damaged or compromised machines and breached corporate networks while simultaneously being able to capture photos of everything he does, take screen shots of his investigative probing work and then share all of this information with colleagues and instructors in real time over social media and cloud sharing platforms.
Furthermore, if stumped on a certain aspect of field training or data analytics, the ability to access online resources and previously downloaded instruction materials would let someone in training much more quickly resolve their problem.
As a basic example: Imagine a police forensics trainee with low level experience sent in to capture as much data from some captured laptops that have just been shut down: the drives themselves are covered by full AES encryption systems but there is a chance of recovering the passwords and other crucial data by performing techniques such as those explained here. By being armed with Google Glass, the trainee could deal with this odd sort of scenario much more effectively while keeping their hands free to work; they could examine research material such as the content of the above article, contact a more experienced instructor and directly get instructions on techniques such as flash freezing the RAM card with compressed air as soon as possible, and at the same time they could contact their lab and notify that a memory that needs to be kept cool until analyzed will be coming in.
General Forensic Documentation
We’ve just gone over the benefits of on the fly advice consultation and documentation of work for digital forensics students, but the same capacities apply to any other IT and digital security professional moving through a complex investigative or work environment.
Imagine being able to walk into a data security crime scene at a corporate office or some other large space with numerous pieces of evidence which need to be collected for collation and later scrutiny. The hassle of multiple pieces of equipment, such as scanning devices and disk imagers will be an inevitable part of your work, yes, but with voice and eye operated power of Google Glass on your face, a lot of your image and video capture needs will be enormously simplified. While imaging a drive or running queries on network servers’ code, you can capture constant video or photo evidence as you work in real time and without interrupting anything you’re doing with your hands. This is where Google Glass has a lot of potential as a major forensic workplace stress reliever.
Stephan Jukic writes for LWGConsulting, a global leader in forensic engineering & recovery solutions.