
“We ultimately landed with Amped Replay, as that was the one that was mostly able to meet our requirements around ...
“Magnet AXIOM is a great tool when it comes to filtering in and filtering out the important data that investigators need to review, which really reduces the overall time to evidence.”
Detective Chad Gish, CID, SISU, Metropolitan Nashville Police Department
Magnet AXIOM is one of Detective Gish’s go-to tools and it’s part of what allows him to create the story of what has happened based on the data collected from digital devices. Today, it’s rare, according to Detective Gish, that “we see a crime committed by someone without a computer in their pocket.” With Magnet AXIOM, Gish is able to collect data from multiple sources all in one case file, whether it be data from mobile extractions from Grayshift’s GrayKey, cloud data from an iCloud backup or a Google warrant return, or vehicle data from Berla iVe. With the geolocation data reviewed in AXIOM, it can also be used to locate likely locations to acquire CCTV footage with Magnet DVR Examiner.
Detective Chad Gish of the Metropolitan Nashville Police Department, digital forensics veteran of 17+ years – with total service time of more than 24 years – has been working cases with digital evidence before the boom of modern digital forensic investigations. When Detective Gish first joined the Cybercrime and Digital Forensics (CID) unit, building a case that included digital evidence with the tools at the time was challenging, even though the devices under investigation were much simpler.
Detective Gish remembers how difficult it was to determine where specific image files came from before forensic tools were able to acquire extended attribute and spotlight metadata. When that data wasn’t available, all that could be proven was that a suspect possessed an illicit image. Examiners couldn’t always prove how the picture ended up on the device, show how it was airdropped onto that device, or attribute the image to the suspect’s account. In some scenarios, this could be the difference between conviction and acquittal based on lack of evidence.
Now, digital forensic tools are benefitting from broader advancements in technology, allowing examiners to streamline their workflows and cut through the digital noise to locate, recover, and collect evidence faster. During the transition from largely computer-based to mobile-first investigations, Detective Gish has witnessed how the way officers investigate digital evidence has changed. The advancements in technology have afforded examiners like him new tools to reduce the time it takes examiners and investigators to uncover evidence on digital devices.
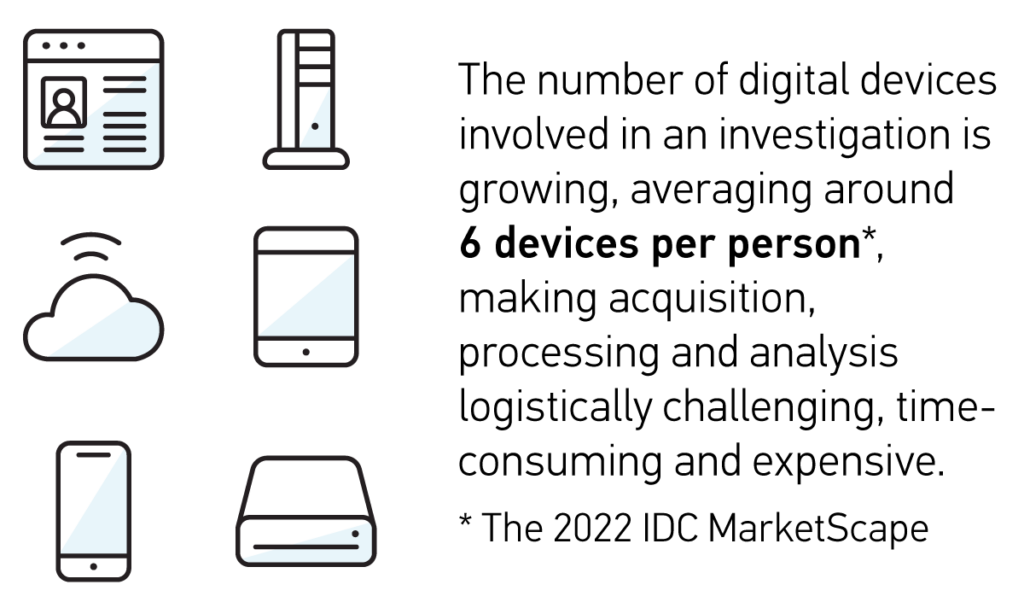
“Even though phones used to be a lot smaller and store less data, it could take 2 or 3 months sometimes to get access to the data,” said Detective Gish. “With today’s tools, often times we can get the data we need in less than a day. We need ways to recover data quickly, especially for those high-profile, priority cases, and the technology needs to evolve to allow us to do so.”
Computer forensics experts have formally been a part of law enforcement agencies for over 40 years. Specialized computer forensic groups were established in the mid-1980s, such as the FBI’s Computer Analysis and Response team and the Met’s Computer Crime Department, but the rise of the modern digital forensics lab can be more closely aligned with the emergence of the smart phone. The landscape of policing changed with the launch of the first iPhone in January 2007 and the first Android device, the HTC Dream in 2008. Now, some 15 years later, about 90% of devices entering digital forensics labs are smart phones according to digital examiners.
Adapting to changing technology has more or less been a mandate of the role for Detective Gish, necessitated in large part by the need to reduce time to evidence, while leveraging technology to bridge the gap between demand for and the shortage of digital forensic examiners. With today’s case backlogs, it’s unrealistic to expect that examiners could go through every single detail of every single device on every case.
“Just this year, we’ve probably investigated 500 cases, and I’m currently working on one case that has about 50 phones that need to be processed,” said Detective Gish.
The storage capacity of mobile devices has also grown exponentially with each passing year and device security has grown in complexity posing significant challenges to investigators. In a recent case, Detective Gish processed two phones that had over 250 gigabytes of data each for a single suspect.
“This is becoming common for almost every case now,” said Detective Gish. “It’s a lot. Even though there’s way more data these days, I only need a small amount of it. Today’s tools allow me to go get that data much more easily.”
Advancing the capabilities of new tools also helps to offset the experience gap. Detective Gish points out that a lot of the new examiners haven’t necessarily grown up in digital forensics or don’t have a lot of experience yet, so if the tools can be designed to pick up some of the slack, to be easy to use, and to be reliable now and into the future, it helps to overcome the experience gap as new examiners are onboarded.
For Detective Gish, it’s especially important that digital forensic tools continue to develop new solutions to reduce time to evidence, because in the backlog there’s evidence that can save a life, that can protect a child. It’s even more important when evidence is received for a high priority case and digital forensic examiners are already stretched thin. When the pace of the clock marches forward incessantly, being able to get any advantage is necessary.
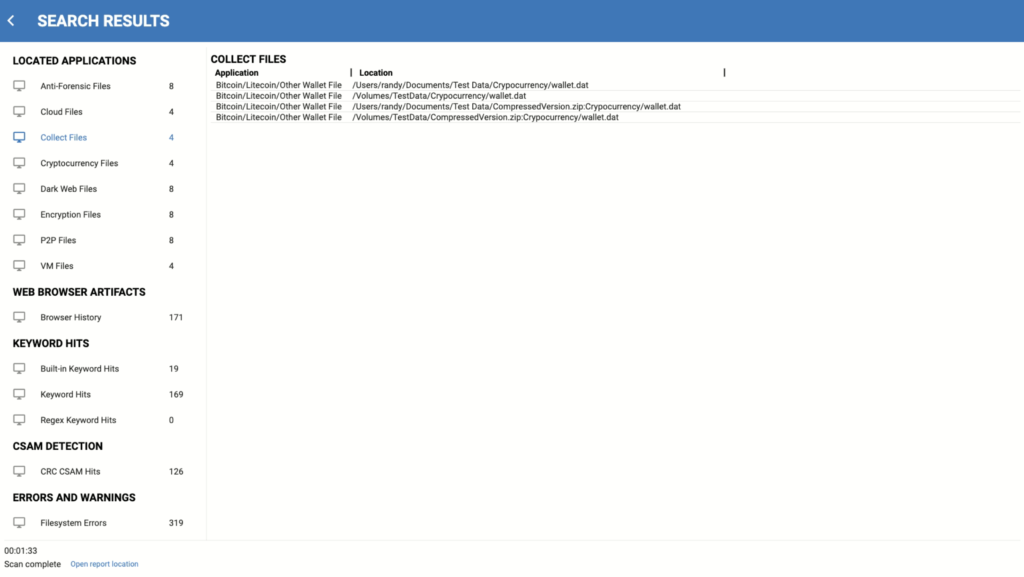
“Triage is another tool we have, where we can quickly scan a device before breaking it down,” Gish said. “We can review triage reports, so we know where the needle in the haystack is before we even start the search.”
Triage reports, provided by tools like Magnet OUTRIDER, become a starting line for Gish, especially when it comes to CSAM cases. When the case includes multiple devices, Magnet OUTRIDER helps to identify some basic but very useful things to reduce the overall time to evidence, such as which device was used most recently and what cloud accounts have been accessed from that device. Once some of this information has been uncovered, it’s easier to prioritize which of those devices to analyze first, and then search warrants can also be written right away for the specific cloud accounts identified.
Not only are new tools changing the way that Detective Gish approaches cases, but so too are emerging sources of data.
“If someone said to me, you could have five unlocked iPhones or you could have the cloud data associated with those phones, if this were 2013, I’d have taken the phones hands down. But, now, I’d have to really think about that. It’s a much tougher decision today.”
In the last 7 or 8 years, as more data has moved to the cloud, Gish has been impressed by the amount of evidence you can collect from cloud packages that are acquired with a warrant return or things like iOS backups from iCloud. In some cases, Gish suggested, albeit rather facetiously, that if you hand that data to an investigator, they may think they have the data from the phone itself.
Nevertheless, with the data that’s being stored by cloud service providers, such as Google, WhatsApp, Microsoft O365, etc., not only can you get data from the different messaging apps, but you can also get additional data for the user, like waypoint data. Gish shared an example where in one homicide investigation he could see the exact moment the trigger was pulled. The victim was murdered while driving, so Gish was able to see waypoint data that was registering consistent speed until the time the victim was shot, and then he could see the speed immediately drop until the car stopped where it was found on the side of the highway.
Leveraging cloud data to identify the moment that the car began to slow was a critical discovery for Detective Gish. Doing so allowed him to quickly establish time of death, expediting the investigative process, and reducing the overall time to evidence. In this case, it allowed Detective Gish to quickly understand that by the time he had arrived at the scene, the victim had already been there for a few hours. In turn, this afforded his team more information for when they were canvassing the area for witnesses.
As new data sources become available, being able to correlate data between sources becomes increasingly important, as is capitalizing on new data sources that become available to find not only more evidence, but also more pertinent evidence.
According to Gish, on one case where there were several car-jackings, he and his team we were able to acquire data from the vehicles once they were recovered, plus they were able to recover the phones from the suspects. What they did to piece the sequence of events together was acquire the waypoint data from the suspect’s cloud accounts, correlate that with the route data from the vehicles, and then they used that to identify where the best locations would be to recover video from CCTV.
“The case came together by using data from different sources to layer the evidence together, which gave us the story of what was happening.”
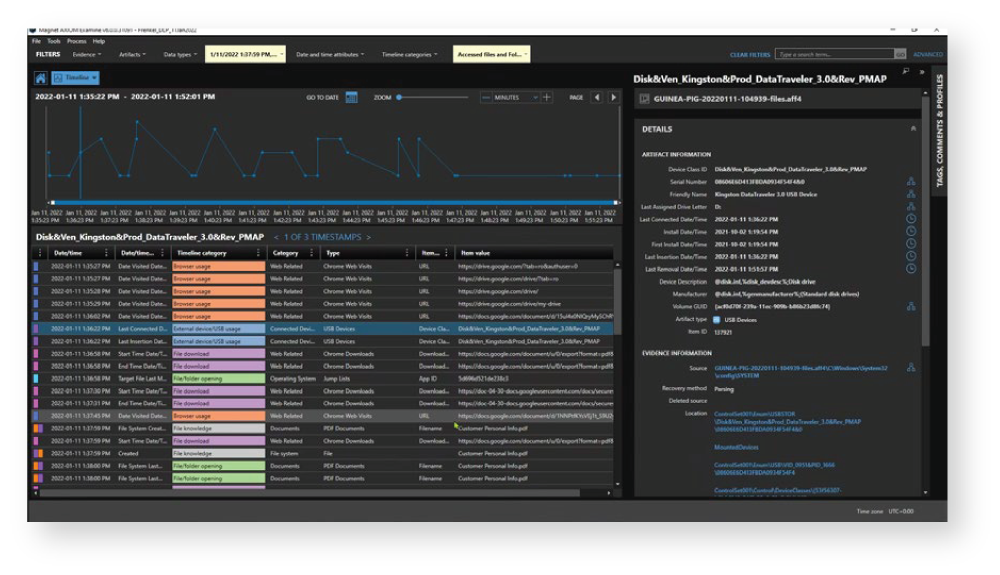
Magnet AXIOM is one of Detective Gish’s go-to tools, and it’s part of what allows him to create the story of what has happened based on the data collected from digital devices. Today, it’s rare, according to Detective Gish, that “we see a crime committed by someone without a computer in their pocket.”
With AXIOM, Gish is able to collect data from multiple sources all in one case file, whether it be data from mobile extractions from Grayshift’s GrayKey, cloud data from an iCloud backup or a Google warrant return, or vehicle data from Berla iVe. With the geolocation data reviewed in AXIOM, it can also be used to locate likely locations acquire CCTV footage with Magnet DVR Examiner.
According to Detective Gish, “Magnet AXIOM is a great tool when it comes to filtering in and filtering out the important data that investigators need to review, which really reduces the overall time to evidence.”
As technology evolves, investigators must adapt to get the best data possible to conduct efficient investigations and to reduce the overall time to evidence. The next stage of technological advancement is underway as cloud infrastructure is offering examiners and investigators automated workflows to churn through backlogs of digital evidence and new tools to share evidence between the lab and non-technical stakeholders.
While Detective Gish notes that these new technologies certainly require updated regulatory oversight and new legal precedents to be set, given the option to return to the ‘good ol’ days’ of digital forensics or to press forward with new tools, he’ll take the latter.
“If you can get to the evidence quickly, and reduce the time it takes to get there, it just makes sense,” said Detective Gish.
Watch the full interview now!
On the evening of February 25, 2022, Ms. Clair Ablewhite was found with multiple stab wounds at her residence in Hall Lane, Colston Bassett, Nottinghamshire. She was 47 years old.
After the end of her marriage, Ms. Ablewhite relocated to Colston Bassett with the intention of beginning a new life and establishing a business providing dog walking and boarding services.
The couple had three sons, and two of them have previously praised their mother as a unique and exceptional person.
Upon conducting their investigation, the Nottinghamshire Police discovered that Ms. Ablewhite had utilized a dating website upon relocating to Colston Bassett. Upon checking her Whatsapp messages, law enforcement officials uncovered proof that John Jessop of Sherwood Avenue in Newark had been communicating with the 47-year-old woman and was the sole individual who failed to come forward and assist authorities in their inquiry.
In September 2021, the couple began an intimate relationship that came to a close on February 19, 2022, mere days before her passing. Detective Inspector Mel Crutchley of Nottinghamshire Police disclosed that the reason for their separation was primarily due to apprehension regarding their age disparity. Nevertheless, he also noted that Jessop had visited Ms. Ablewhite’s residence – which was situated approximately 17 miles away from his own – indicating some level of continued involvement between them.
Nottinghamshire Police released CCTV footage of Jessop’s 17-mile bike ride from his residence in Newark to Colston Bassett. The video shows him cycling toward Ms. Ablewhite’s home, with multiple security cameras capturing the journey. After stopping to purchase a pasty on the way to Rushcliffe village, police were able to link Jessop’s clothing and bike to other CCTV footage. Shortly before stabbing the mother-of-three in her home, he was caught hiding his bike in a nearby bush and walking along Hall Lane near Ms. Ablewhite’s house. According to police, audio from the fatal attack was captured by CCTV belonging to Ms. Ablewhite’s neighbor before Jessop retrieved his bike and cycled back 17 miles to Newark.

Credit: Nottinghamshire Police
According to reports, Jessop attempted to conceal his movements by leaving his mobile phone at home and using cash to make purchases during his journey. However, he was apprehended and charged soon after Ms. Ablewhite’s discovery in February. As a result of pleading guilty, he has been sentenced to life imprisonment.
It is important to notice that, according to Paul Hopcroft, Certified Forensic Video Technician at Nottinghamshire Police, the quality of the video evidence was not too bad. The video surveillance system was set up properly and it was an NVR (Network Video Recorder). On a normal day, investigators would have done a “Reverse Projection”, but while they removed the hard drive and got back to their office, the main camera had gone down. It did turn out in the end that a maintenance team that was on the property doing some landscaping work had actually tarnished the wiring. The view they had was the nighttime view and some daytime footage. That was everything they had to work with.
Investigators were struggling to process the files in the first instance, but they managed to do that within Amped FIVE.
On this occasion, because they didn’t have that camera to go back to and comb through, that threw Reverse Projection completely out of the equation. The video analyst’s only option was then to use the Measure 3D filter in Amped FIVE.
Learn here what filters to use when measuring the height of an unknown person.
Let’s see now how Paul Hopcroft used Amped FIVE to measure the height of the suspect caught on the CCTV camera and helped to solve the murder investigation.
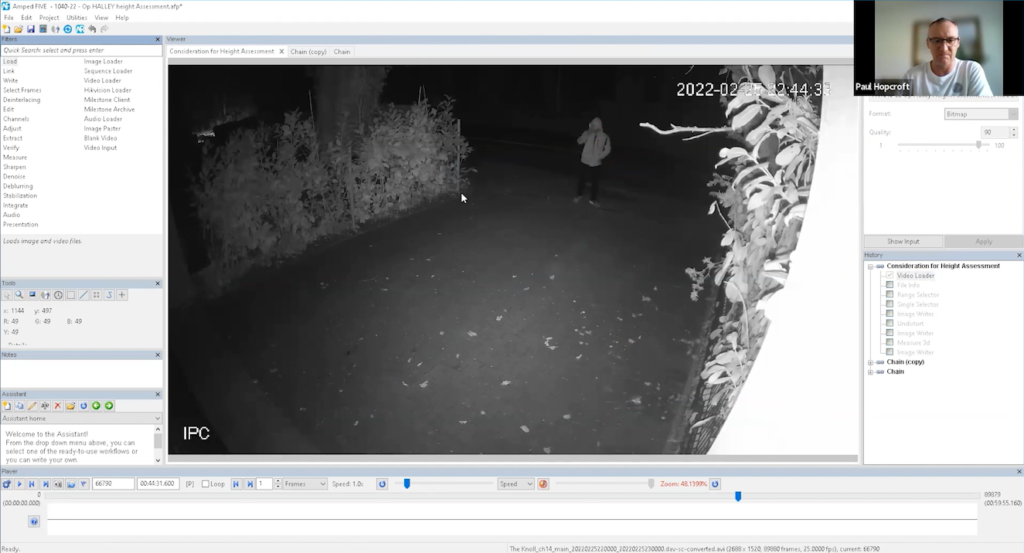
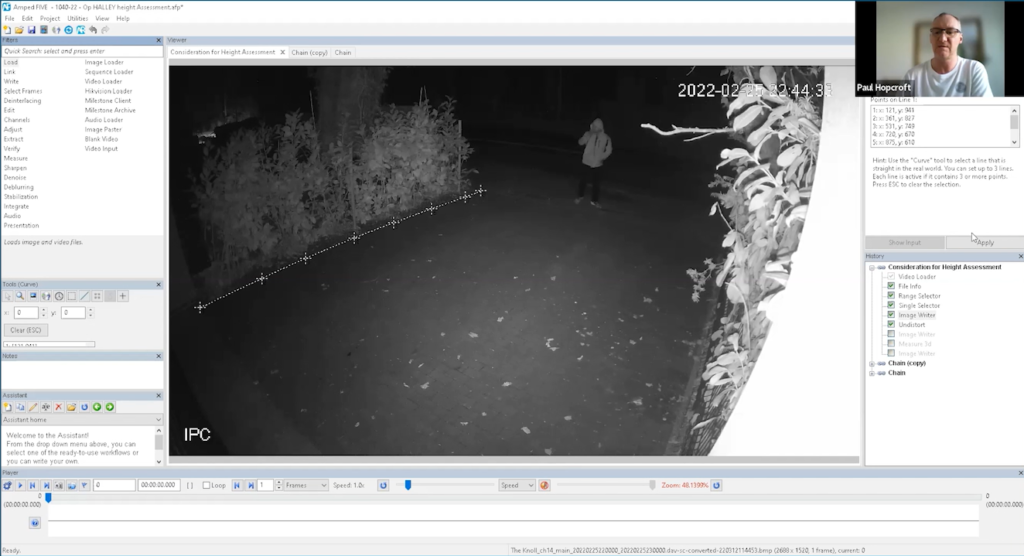
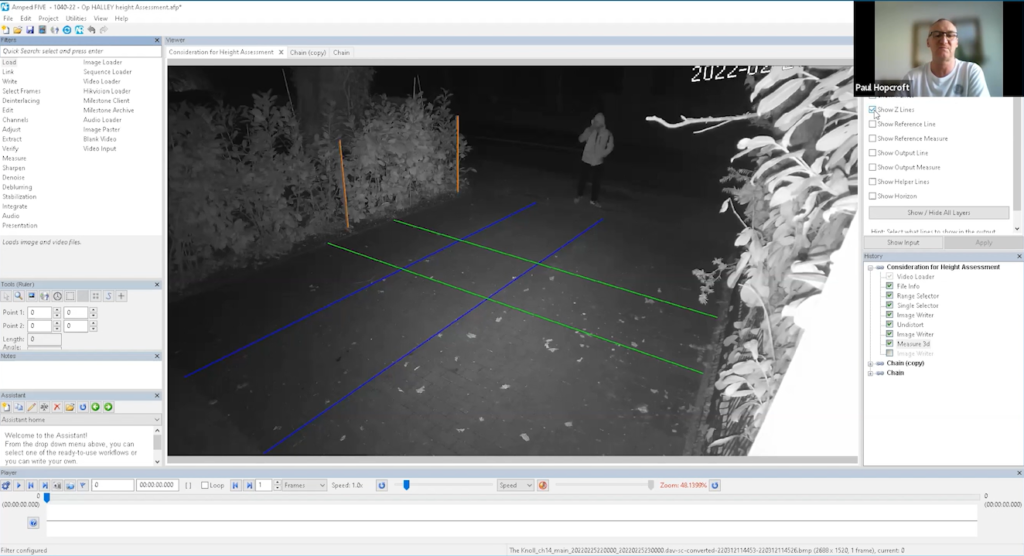
The initial step was to identify a measuring point. Paul opted for the bar on the right side of the suspect as it was closest and provided a reasonable comparison. This reference point is now known as Post A, with the second bar being referred to as Post B.
Lens distortion also needed addressing, as it was particularly evident looking at the right-hand side of the CCTV camera image.
In order to rectify the issue of lens distortion, Paul employed a specific line that was known to him to be straight due to his on-site experience. This line runs straight across the bottom of the bushes and intersects all relevant reference points. By utilizing “File info” and subsequently narrowing it down via “Range selector”, he was able to isolate a small group for processing purposes using “Single selector”. The next step involved implementing the “Undistort” filter which effectively addressed the problem of lens distortion by utilizing the straight line he pulled across the bottom of the bushes. This way he got rid of distortion.
Once he had saved his work, he clicked on Image Writer and selected Measure 3D. The block pavement appeared perfectly straight all along its length. Although it was difficult to see the pavement’s blocks clearly, he compared their position with a daytime view to trace their path accurately.
He felt confident in most of what he had done so far. Starting from one end of the driveway and moving towards where his subject stood, he drew two lines to mark out his measurements.
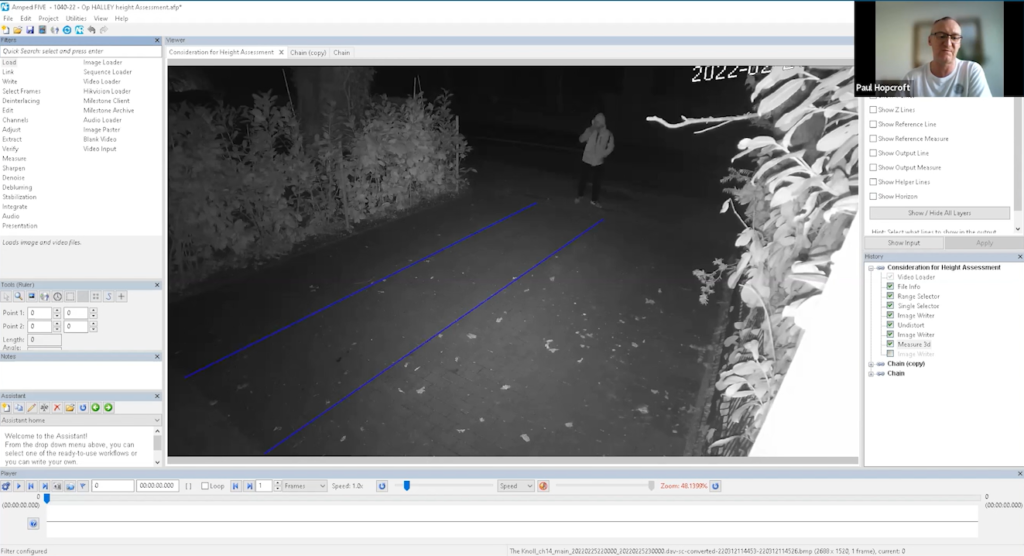
He then carried on by adding the two lines across the pavement.
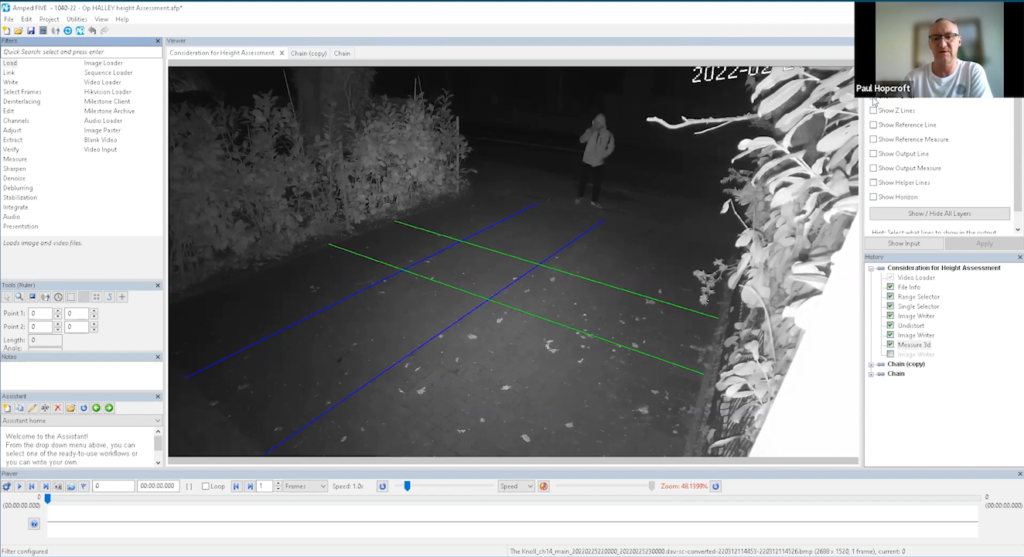
He then added the vertical lines.
The bars are the straightest objects he could find in the scene. He first used Post A as a fixed reference line, which he knew was 1.445 cm tall.
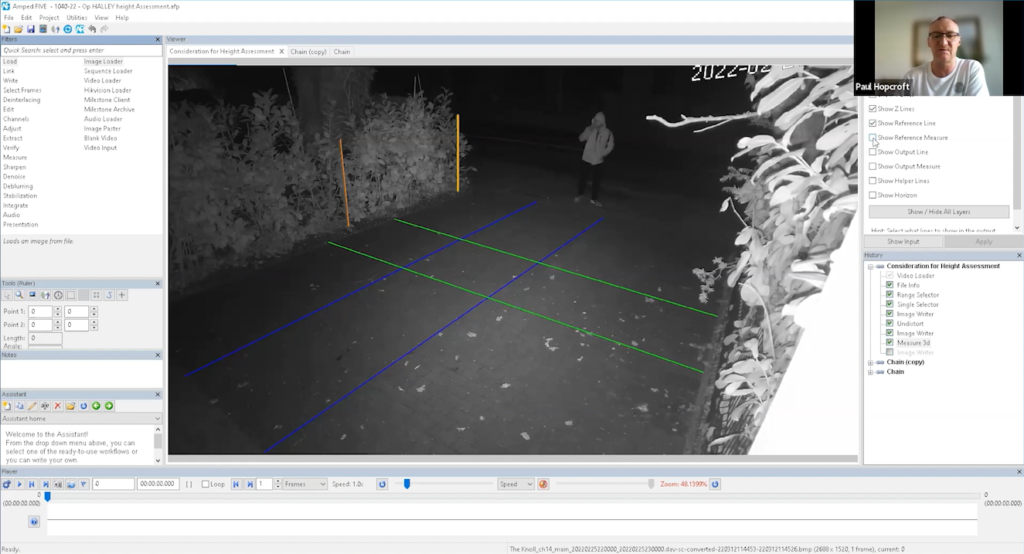
He then proceeded in calculating the height of the suspect which was determined from top to bottom, with a small black mark placed at the post’s base for verification purposes. This provides a fixed reference point at the bottom and allows one to easily locate the bar’s top.
Next, he attempted to measure from the subject’s feet up through their body, aligning as closely as possible with their center line all the way to their head.
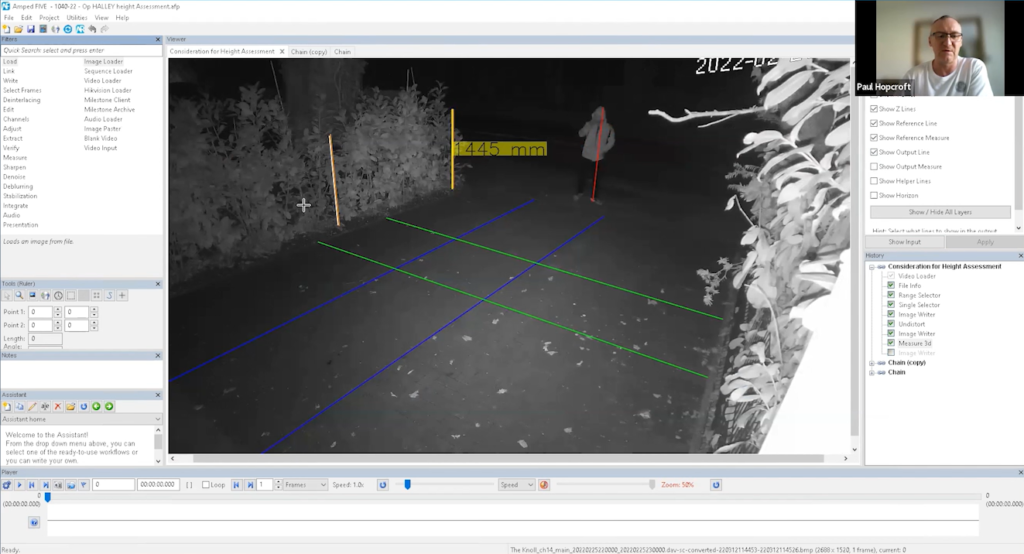
He proceeded to draw the second line using the same technique of marking a small black spot at the base of the post and measuring up to its top.
Upon selecting “Show Output Measure,” he confirmed that both lines were accurately drawn.
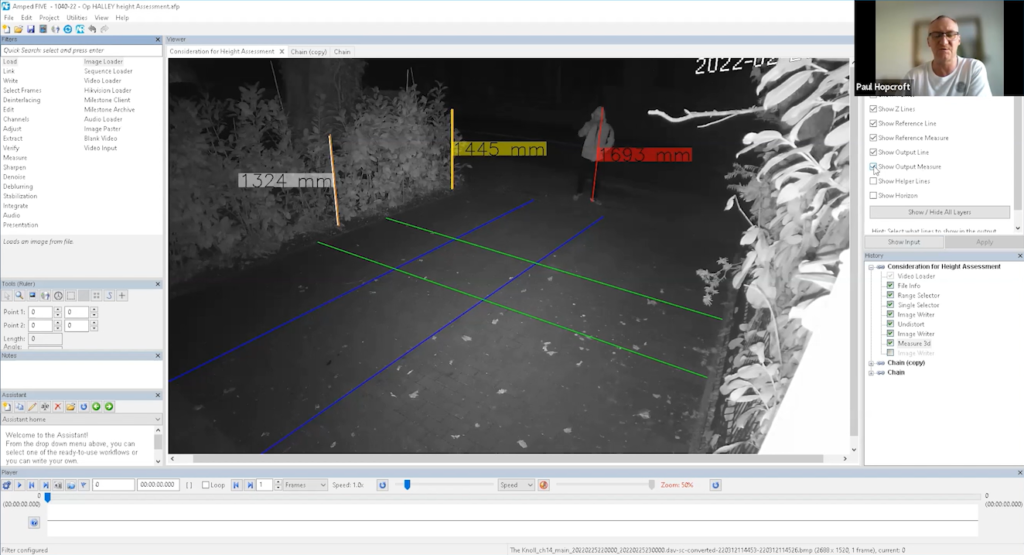
The subject’s height was found to be slightly less than 1.7 meters.
It has been discovered that Post B’s measurement is actually 1.319 cm, which means it deviates by a mere 5 millimeters from the expected value.
While reviewing the evening view, one issue that emerged was the effect of wind on a leaf positioned at the top, an element that had not been accounted for during daytime observations.
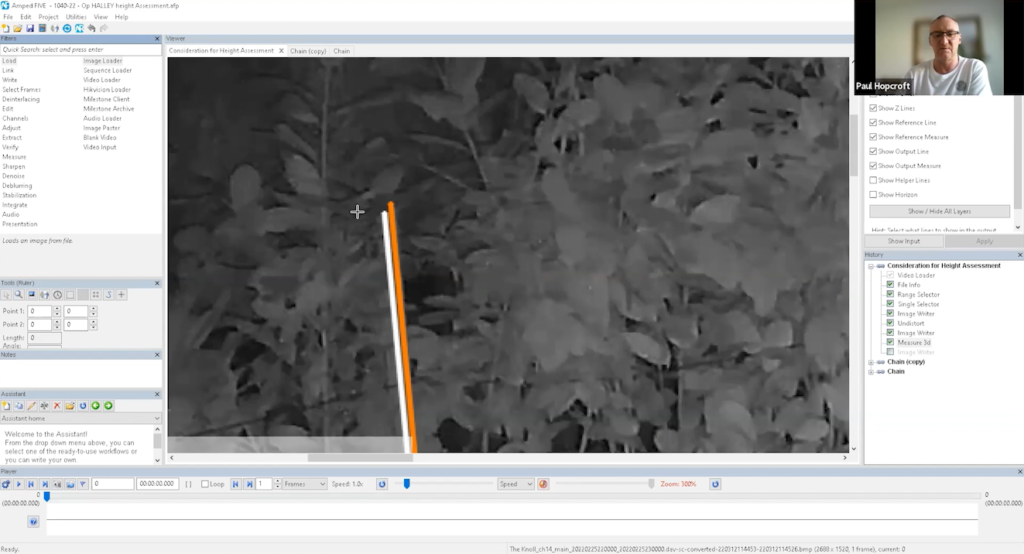
He had difficulty selecting the top of the post, so he settled on the nearest visible point.
This step was taken to evaluate and limit potential suspects. It proved useful as it eliminated shorter individuals from consideration. A comprehensive report was compiled for use in court, incorporating data from Amped FIVE that Paul included and cited appropriately.
The investigation progressed with typical procedures: tracing a person who rode a bike 17 miles before abandoning it three-quarters of a mile away from the scene, followed by additional inquiries and interviews leading to a successful prosecution.
Initially, the file format posed a challenge, but Amped FIVE was already able to resolve it. Paul reports that the project proceeded smoothly from there. Attention to detail in measuring is crucial, ensuring accurate measurements of all points. According to Paul, an on-site survey plays a critical role in achieving this accuracy later on.
The brick pavement markings are slightly off and can cause a 6-millimeter height discrepancy for subjects. To mitigate this issue, one can double-check the calibration lines using daytime recording, since lines are often more visible in that condition. So if daytime recording from the same camera is available, you can load it in FIVE and simply copy-paste the Measure 3D filter into that chain, and check that calibration lines are well positioned.
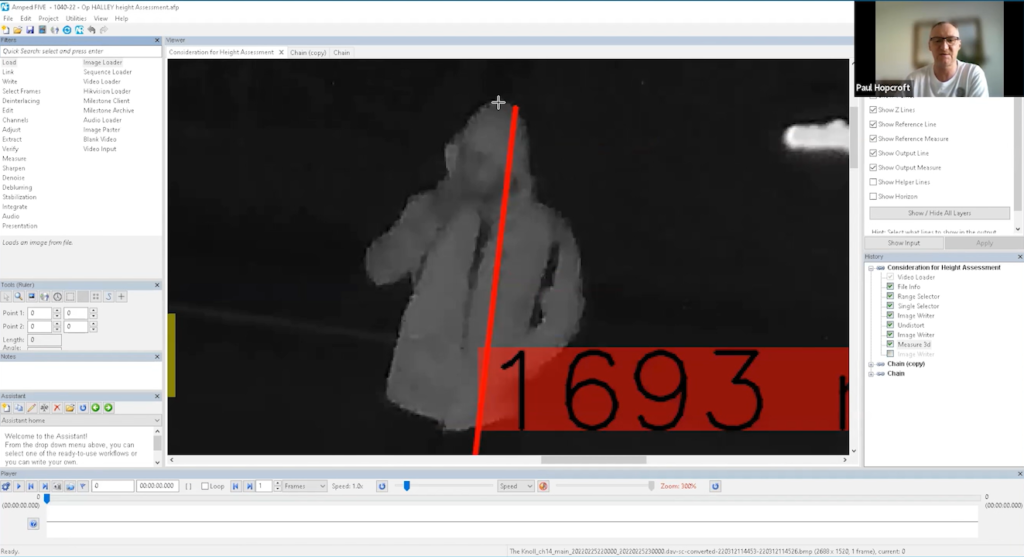
Overall, Paul found the process fairly easy after completing the Amped FIVE training and recommends others do so as well. Clothing and posture must also be taken into account when analyzing images; for example, in the following image where the subject wears a hooded jacket, Paul believes his head may not align with the red line marker above them.
Paul utilized the Undistort function to rectify lens distortion, but Amped FIVE also offers the Correct Fisheye filter. Despite this, Paul opted for Undistort as he could easily identify a straight line and had greater control over his adjustments. He did not experiment with the Correct Fisheye filter because he achieved satisfactory results using his chosen method. Having personally visited the location and observed its daytime view, Paul was familiar with where he needed to begin his corrections.
However, if presented with an unfamiliar case, Paul would test both features to determine which yielded better outcomes. Ultimately, being present at the scene gave him an advantage in making informed decisions about image correction techniques. Learn more about lens distortion here.
Paul and the Nottinghamshire Police Department ventured into uncharted territory for their unit, as they employed the Measure 3D filter in Amped FIVE for the first time during this murder trial. The pressure was on them to provide swift answers, but it was crucial to take their time and ensure everything was done correctly. By doing so, if needed, they could have confidently addressed any questions or concerns raised by other agencies down the line.
In cases like these, attention to detail is of utmost importance. It’s imperative to approach each step methodically and make full use of available training resources. If necessary, seek guidance from others who may offer fresh perspectives that can simplify your work. Ultimately, you must do the legwork yourself but tapping into outside knowledge can be invaluable in achieving success.
In conclusion, measuring the height of a suspect in 3D with Amped FIVE is an incredibly useful tool for law enforcement professionals. With its advanced capabilities, this software makes it easy to accurately determine the height of suspects from any angle or distance. Whether you are investigating a crime scene or conducting surveillance operations, Amped FIVE can help you obtain reliable measurements that can make all the difference in your case.
Amped Software strongly recommends that law enforcement agencies invest in this powerful software to enhance their investigative capabilities and improve their overall effectiveness. The ability to quickly and accurately measure suspect heights can be invaluable when trying to identify potential suspects or gather evidence for criminal investigations.
Lastly, training is essential for any law enforcement departments and agencies that want to stay ahead of the curve and effectively investigate crimes. The training provides officers with the skills and knowledge needed to properly collect, enhance, analyze, and present video evidence in court. By investing in this type of training, departments and agencies can increase their success rates when it comes to solving cases and bringing criminals to justice. Remember, every piece of evidence counts when it comes to catching criminals and keeping communities safe!
So if you’re looking for a powerful tool that will give you an edge in your investigations, look no further than Amped FIVE. With its cutting-edge technology and ease of use, it’s sure to become an essential part of your toolkit. Thanks for reading!
8th July 2022 by Magnet Forensics
Our customers need these answers as quickly as possible to minimize business interruption and Magnet IGNITE has enabled us to provide them hours—and sometimes days—earlier.”
— Michael Nelson, Managing Partner , CYBIR

CYBIR is a cybersecurity, digital forensics & incident response consulting firm serving clients across the United States.
HEADQUARTERS: Philadelphia, PA
SPECIALTIES:
When a business suffers a breach, they turn to CYBIR to investigate the incident. CYBIR needs to be able to move quickly and gather insights on the breach and determine the course of action required to guide the company through the incident.
With time in short supply, CYBIR needs to identify which endpoints were affected quickly. They also need to provide answers to the business and legal counsel on how the attack occurred and what data was accessed or exfiltrated. To ensure the speed and efficiency of their triage, CYBIR uses Magnet IGNITE, a cloud-based tool that enables concurrent, targeted collections from remote endpoints.
Prior to using IGNITE, a breach required CYBIR to travel to the client site, send drives overnight to and from the client to gather full disk images, or use various scripts to extract data. Between transportation timelines and the volume of data that needed to be processed and investigated, it could take days or weeks to reach the required answers.
With the constantly evolving nature of breach investigations, speed is important not only at the onset of the investigation but also when a development takes the case in an entirely new direction. The efficiency of IGNITE allows CYBIR to deploy additional agents and review evidence at speed—maintaining the momentum and progress of their investigation.
Magnet IGNITE enables the rapid triage of remote client endpoints to identify where malicious activity has taken place so examiners can determine the required next steps. Using a single agent configuration, examiners can triage multiple endpoints at the same time to quickly gather insights into an incident and determine where a full forensic analysis is needed.
Triage results are presented in IGNITE’s intuitive interface to allow for preliminary analysis of artifacts, as they are being collected. Keyword searches and time filters can be applied to the results to provide many of the answers that are required in data breach cases. Where a deep forensic analysis of an endpoint is required, IGNITE can export evidence in a file format that can be ingested into Magnet AXIOM Cyber.
With teams and projects geographically spread across multiple states or internationally, IGNITE provides hybrid teams with access to the data no matter where they are located. As a cloud-based tool, IGNITE can be accessed from any location with an internet connection to quickly triage endpoints. And because IGNITE operates completely in the Cloud, it doesn’t require processing time or additional hardware in your forensics lab.
“Data breaches can happen anywhere in the world and one of the most powerful features of Magnet IGNITE is that it allows us to investigate how they happened, actions the threat actors took and what data was exfiltrated, from any remote location.”
— Michael Nelson, Managing Partner , CYBIR
See IGNITE in action for yourself.
To learn more about Magnet IGNITE and get started with a free trial visit magnetforensics.com/magnet-ignite.
Detego’s customer* is one of the largest tax authorities in Europe and employs more than 50,000 staff. The authority’s main responsibilities include the assessment, determination, collection and imposition of tax across its jurisdiction.
With instances of tax evasion and tax fraud on the rise, the authority set out to enhance its investigative capabilities by providing its teams with digital forensics tools to assist in both office-based and field-based investigations.
The tax authority required a solution that could extract and analyse data from numerous digital devices including computers, laptops, mobile phones, loose media, servers and devices connected to networks. As the focus was on using these tools in both field-based and office-based investigations, there was a need for tools that could rapidly detect instances of fraud and tax evasion without requiring extensive data extraction and analytical processes.
Another key consideration was the ease of use and the ability to automate tasks as the initial elements of investigations were performed by team members who didn’t have a deep technological know-how.
After reviewing the digital forensics solutions available in the market, the customer chose Detego’s Unified Digital Forensics Platform due to its advanced capabilities, ease of deployment and intuitive interface.
Historically, the team was only able to extract data from computers, laptops and a handful of mobile devices. The support of specialist labs had to be sought if they encountered any other device type that needed to be investigated.
Detego’s all-in-one functionality instantly extended the team’s capabilities, and enabled them to rapidly gather and analyse data from a range of devices including removable media, smart devices and tens of thousands of phone models including burner phones and over 2,000 apps.
Thanks to Detego, the team was able to rapidly bypass passwords and encryption to access data from devices in a matter of seconds – helping play a key role in reducing case backlogs. And within three months of implementing Detego, the team was able to reduce backlogs by more than 45 percent.
The team used Detego’s frontline solutions to bolster their on-scene investigation capabilities. As the solutions required minimal user input and expertise in digital forensics, the team was able to easily enable frontline agents to carry out sting operations to identify devices with data that’s related to investigations.
It’s been nearly five years since the customer implemented Detego’s Unified Digital Forensics Platform. And most recently, the authority has been exploring the possibility of implementing Case Manager, a central platform that enables the management of every aspect of investigations – from investigations, incidents and risks to evidence and compliance.
*This case study was anonymised due to the sensitive nature of the investigations carried out by the customer.
See how Detego’s award-winning Digital Forensics Platform can work for you. Request a free, fully-functional trial today: https://detegoglobal.com/request-a-trial/
“Magnet AXIOM is a great tool when it comes to filtering in and filtering out the important data that investigators need to review, which really reduces the overall time to evidence.”
— Detective Chad Gish, CID, SISU, Metropolitan Nashville Police Department

CASE OVERVIEW:
PRODUCTS:
SPECIALTIES:
Magnet AXIOM is one of Detective Gish’s go-to tools and it’s part of what allows him to create the story of what has happened based on the data collected from digital devices. Today, it’s rare, according to Gish, that “we see a crime committed by someone without a computer in their pocket.”
With Magnet AXIOM, Gish is able to collect data from multiple sources all-in-one case file, whether it be data from mobile extractions from Grayshift’s GrayKey, cloud data from an iCloud backup or a Google warrant return, or vehicle data from Berla iVe. With the geolocation data reviewed in AXIOM, it can also be used to locate likely locations to acquire CCTV footage with Magnet DVR Examiner.
Detective Chad Gish of the Metropolitan Nashville Police Department, digital forensics veteran of 17+ years – with total service time of more than 24 years – has been working cases with digital evidence before the boom of modern digital forensic investigations.
When Gish first joined the Cybercrime and Digital Forensics (CID) unit, building a case that included digital evidence with the tools at the time was challenging, even though the devices under investigation were much simpler.
Gish remembers how difficult it was to determine where specific image files came from before forensic tools were able to acquire extended attribute and spotlight metadata.
When that data wasn’t available, all that could be proven was that a suspect possessed an illicit image. Examiners couldn’t always prove how the picture ended up on the device, show how it was airdropped onto that device, or attribute the image to the suspect’s account. In some scenarios, this could be the difference between conviction and acquittal based on lack of evidence.

Now, digital forensic tools are benefitting from broader advancements in technology, allowing examiners to streamline their workflows and cut through the digital noise to locate, recover, and collect evidence faster. During the transition from largely computer-based to mobile-first investigations, Gish has witnessed the way officers investigate digital evidence has changed. The advancements in technology have afforded examiners like him new tools to reduce the time it takes examiners and investigators to uncover evidence on digital devices.
“We need ways to recover data quickly, especially for those high-profile, priority cases, and the technology needs to evolve to allow us to do so.”
— Detective Chad Gish, CID, SISU, Metropolitan Nashville Police Department
“Even though phones used to be a lot smaller and store less data, it could take 2 or 3 months sometimes to get access to the data,” said Gish. “With today’s tools, often times we can get the data we need in less than a day. We need ways to recover data quickly, especially for those high-profile, priority cases, and the technology needs to evolve to allow us to do so.”
Computer forensics experts have formally been a part of law enforcement agencies for over 40 years. Specialized computer forensic groups were established in the mid-1980s, such as the FBI’s Computer Analysis and Response team and the London Met’s Computer Crime Department, but the rise of the modern digital forensics lab can be more closely aligned with the emergence of the smart phone. The landscape of policing changed with the launch of the first iPhone in January 2007 and the first Android device, the HTC Dream in 2008. Now, some 15 years later, about 90% of devices entering digital forensics labs are smart phones according to digital examiners.
Adapting to changing technology has more or less been a mandate of the role for Detective Gish, necessitated in large part by the need to reduce time to evidence, while leveraging technology to bridge the gap between demand for and the shortage of digital forensic examiners. With today’s case backlogs, it’s unrealistic to expect that examiners could go through every single detail of every single device on every case.
“Even though there’s way more data these days, I only need a small amount of it. Today’s tools allow me to go get that data much more easily.”
— Detective Chad Gish, CID, SISU, Metropolitan Nashville Police Department
“Just this year, we’ve probably investigated 500 cases, and I’m currently working on one case that has about 50 phones that need to be processed,” said Gish.
The storage capacity of mobile devices has also grown exponentially with each passing year and device security has grown in complexity posing significant challenges to investigators. In a recent case, Gish processed two phones that had over 250 gigabytes of data each for a single suspect.
“This is becoming common for almost every case now,” said Gish. “It’s a lot. Even though there’s way more data these days, I only need a small amount of it. Today’s tools allow me to go get that data much more easily.”
Advancing the capabilities of new tools also helps to offset the experience gap. Gish points out that a lot of the new examiners haven’t necessarily grown up in digital forensics or don’t have a lot of experience yet, so if the tools can be designed to pick up some of the slack, to be easy to use, and to be reliable now and into the future, it helps to overcome the experience gap as new examiners are onboarded.
For Gish, it’s especially important that digital forensic tools continue to develop new solutions to reduce time to evidence, because in the backlog there’s evidence that can save a life, that can protect a child. It’s even more important when evidence is received for a high priority case and digital forensic examiners are already stretched thin. When the pace of the clock marches forward incessantly, being able to get any advantage is necessary.
“Triage is another tool we have, where we can quickly scan a device before breaking it down,” Detective Gish said. “We can review triage reports, so we know where the needle in the haystack is before we even start the search.”
Triage reports, provided by tools like Magnet OUTRIDER, become a starting line for Gish, especially when it comes to CSAM cases. When the case includes multiple devices, Magnet OUTRIDER helps to identify some basic but very useful things to reduce the overall time to evidence, such as which device was used most recently and what cloud accounts have been accessed from that device.
Once some of this information has been uncovered, it’s easier to prioritize which of those devices to analyze first and then search warrants can also be written right away for the specific cloud accounts identified.
Not only are new tools changing the way that Detective Gish approaches cases, but so too are emerging sources of data.
“If someone said to me, you could have five unlocked iPhones or you could have the cloud data associated with those phones, if this were 2013, I’d have taken the phones hands down. But, now, I’d have to really think about that. It’s a much tougher decision today.”
In the last 7 or 8 years, as more data has moved to the cloud, Gish has been impressed by the amount of evidence you can collect from cloud packages that are acquired with a warrant return or things like iOS backups from iCloud. In some cases, Gish suggested, albeit rather facetiously, that if you hand that data to an investigator, they may think they have the data from the phone itself.
“The case came together by using data from different sources to layer the evidence together, which gave us the story of what was happening.”
— Detective Chad Gish, CID, SISU, Metropolitan Nashville Police Department
Nevertheless, with the data that’s being stored by cloud service providers, such as Google, WhatsApp, Microsoft O365, etc., not only can you get data from the different messaging apps, but you can also get additional data for the user, like waypoint data.
Gish shared an example where in one homicide investigation he could see the exact moment the trigger was pulled. The victim was murdered while driving, so Gish was able to see waypoint data that was registering consistent speed until the time the victim was shot and then he could see the speed immediately drop until the car stopped where it was found on the side of the highway.
Leveraging cloud data to identify the moment that the car began to slow was a critical discovery for Gish. Doing so allowed him to quickly establish time of death, expediting the investigative process, and reducing the overall time to evidence.
In this case, it allowed Gish to quickly understand that by the time he had arrived at the scene, the victim had already been there for a few hours. In turn, this afforded his team more information for when they were canvassing the area for witnesses.
As new data sources become available, being able to correlate data between sources becomes increasingly important, as is capitalizing on new data sources that become available to find not only more evidence, but also more pertinent evidence.
According to Gish, on one case where there were several carjackings, he and his team we were able to acquire data from the vehicles once they were recovered, plus they were able to recover the phones from the suspects.
What they did to piece the sequence of events together was acquire the waypoint data from the suspect’s cloud accounts, correlate that with the route data from the vehicles, and then they used that to identify where the best locations would be to recover video from CCTV.
“The case came together by using data from different sources to layer the evidence together, which gave us the story of what was happening.”
Magnet AXIOM is one of Detective Gish’s go-to tools and it’s part of what allows him to create the story of what has happened based on the data collected from digital devices. Today, it’s rare, according to Gish, that “we see a crime committed by someone without a computer in their pocket.”
With AXIOM, Gish is able to collect data from multiple sources all-in-one case file, whether it be data from mobile extractions from Grayshift’s GrayKey, cloud data from an iCloud backup or a Google warrant return, or vehicle data from Berla iVe. With the geolocation data reviewed in AXIOM, it can also be used to locate likely locations acquire CCTV footage with Magnet DVR Examiner.
According to Gish, “Magnet AXIOM is a great tool when it comes to filtering in and filtering out the important data that investigators need to review, which really reduces the overall time to evidence.”
As technology evolves, investigators must adapt to get the best data possible to conduct efficient investigations and to reduce the overall time to evidence. The next stage of technological advancement is underway as cloud infrastructure is offering examiners and investigators automated workflows to churn through backlogs of digital evidence and new tools to share evidence between the lab and non-technical stakeholders.
“If you can get to the evidence quickly, and reduce the time it takes to get there, it just makes sense.”
— Detective Chad Gish, CID, SISU, Metropolitan Nashville Police Department
While Detective Gish notes that these new technologies certainly require updated regulatory oversight and new legal precedents to be set, given the option to return to the ‘good ol’ days’ of digital forensics or to press forward with new tools, he’ll take the latter.
“If you can get to the evidence quickly, and reduce the time it takes to get there, it just makes sense,” said Gish.
Learn more at magnetforensics.com
For additional information call us at 1-844-638-7884
or email sales@magnetforensics.com
Operator: Calling all units. A2 11, 675 Main. Backup needed.
Speaker 1: So we had two police forces combining their digital forensics to save money and increase efficiency. However, we soon realized we had a situation that we weren’t prepared for.
We had about 200 police officers in the team, and we were not prepared for the increasing amount of data that we needed to be extracted. There was no efficient way to share files from collected devices, which led to a slowed down incorporation across the departments.
This generated a backlog of units at the lab. We had no analytics or statistics for managers or users on the machines and computers were running out of storage with all the data we knew we had to do something
Operator: Standby. Calling all units. A2 11 675 Main. Backup needed.
Speaker 1: That was when we implemented Frontline solutions from MSAB. By training our officers to use the kiosk and tablet, we managed to have more frontline personnel using the tools, increasing the efficiency of each investigation.
With the data being stored on the central server, the files were accessible almost instantaneously. So departments could cooperate. This also eliminated the risk of hard drives running out of storage.
Together with XEC, all the hardware was networked, which made it possible to push out updates to all stations with one click and thereby keeping all the stations up to date.
And with the tailor-made workflow, all officers were forced to follow the same step-by-step process, securing a high level of consistency, making sure all forensic procedures are complacent with local laws.
Moving to the MSAB Kiosk and networking system was the best decision we ever made. Today, for example, we are better able to support high-risk victims of domestic violence. Before, relying on the lab delayed the process by at least a month.
Using the Kiosk now enables us to confront the abuser with the extracted evidence in the interview, and a charge could be pressed within the first eight hours. We can now solve more crimes and help more people.
Unique Wire, a digital forensics and e-discovery business focused on helping service providers, corporations, law firms, and law enforcement agencies, headquartered in Oregon, spent years battling with solutions that were not compatible with one another. In many instances, their forensics engineering team had to write their own code to solve business and law enforcement challenges. In 2020, they decided to standardize their entire operation using Cellebrite products. Doing so has ensured total compatibility across all solutions and has helped expedite e-discovery for their clients.
Brian Feucht, Managing Partner at Unique Wire, had a very unique beginning with his own lawsuit. Feucht had started a company in Alaska to develop next-generation mobile devices, but a competitor stole much of the business’s intellectual property.
“We won a $53 million verdict, but then a judge said there wasn’t enough available evidence to support the damages, and she reversed the verdict,” Feucht recalls. “That cost me $670,000 in damages. We weren’t able to gather the necessary electronic evidence. I realized that given my knowledge of technology, I could have filled a gap in for electronic discovery. I just did not know what could have been done. Thankfully, at the end of the day, the Alaska Supreme Court reversed the judge’s decision, but damages were reduced to $1. That $1 check hangs on my wall to remind us that we treat every case as if it were our own.”
That realization led to the launch of Unique Wire, a company that provides Digital Intelligence—the data extracted from digital sources and data types—smartphones, computer, and the Cloud—and the processes by which companies access, manage and leverage data to more efficiently run their operations for their clients. Their clientele now includes corporations, law firms, and law enforcement agencies.
Unique Wire’s staff comes from law enforcement and government, bringing extensive resources and knowledge to the task of digital forensics. The company has three divisions, serving civil cases such as corporate IP theft; criminal defense; and law enforcement. Corporate clients tend to be larger, established organizations that are concerned about protecting intellectual property, but Unique Wire has seen a significant influx of smaller clients during the COVID pandemic.
“We see what we’re doing as bringing resources and knowledge to bear that typically weren’t found in the private sector—finding out what happened, why it happened, and providing our clients with insights into that information,” says Feucht.
Corporate investigations typically involve human resources issues or theft of intellectual property. “On the government side, we serve both defense attorneys as well as assisting the law enforcement side whenever they have questions and require some assistance,”
To provide e-discovery services across a multitude of device types and platforms, Unique Wire’s technology experts had to build several dozen applications needed to derive digital evidence from phones, computers, and other devices supplied by clients. The team typically used platform developer tools, such as the Android SDK, to manually parse data.
“We always try to go above and beyond for our clients,” Feucht says. “If they bring us a cell phone and we can’t hear any audio, we have staff that knows how to do audio. If you’re doing one component of getting information, you should be taking it to the next level—like ripping apart the audio and the video to see if it’s being manipulated, or analyze what we can hear in the background. We want to give clients a fundamental understanding of what that data is telling us.”
“We realized right away that Cellebrite would save us hours of work.”
— Brian Feucht, Managing Partner
While the homegrown approach worked, allowing Unique Wire to satisfy a growing group of clients, it wasn’t as efficient as it could be. Creating in-house applications was time-consuming and required three full-time engineers to manage. Preparing and presenting evidence for court was also time-consuming; since Unique Wire wasn’t using tools typically found on the market, analysts frequently had to explain to judges and opposing counsel how the homegrown solutions were created.
“Every time you write code, everyone at court questions it,” says Feucht. “Plus, we were tired of building software—we wanted to put that time toward billable hours.”
As Unique Wire planned out its future expansion, the business’s leaders realized that the dozens of homegrown forensics solutions and the corresponding engineering maintenance would slow Unique Wire’s growth. The business hopes to have 25 analysts on staff by 2022, and is building out a 4,700-square-foot new office space that includes a secure 2,000-square-foot data extraction lab, nicknamed “The Cracklab.”
“We looked at who the players were, who was doing stuff in the space,” Feucht says. “We had some contacts in law enforcement on the federal side, and they were like, ‘Hey, you should use this tool.’ We realized right away that Cellebrite would save us hours of work.”
To derive Digital Intelligence for its clients, Unique Wire replaced its homegrown applications with a full suite of digital tools, including several Cellebrite solutions, such as Pathfinder for automatically surfacing digital evidence; UFED for unlocking, extracting, and analyzing data; UFED Cloud for extracting and preserving cloud content such as messaging data; Inspector for analysis of macOS and Windows computer volumes; and Digital Collector for data acquisition from Mac computers. We also use Cellebrite Legalview to transmit data directly into our clients’ case management solution.
With Cellebrite solutions, Unique Wire can take on more corporate investigations, and deliver results to clients faster. The Cellebrite solutions will also help Unique Wire achieve its ambitious growth goals, as well as a shift from a business that spent resources developing its own code to one that can rely on best-of-breed Cellebrite solutions.
Unique Wire now gains more time to spend on urgent client work—and to increase the billable hours crucial to business growth. The company was also able to reduce its reliance on engineering and programming assistance, saving $400,000 annually.
“We see what we’re doing as bringing resources and knowledge to bear that typically weren’t found in the public sector—finding out what happened, why it happened, and providing our clients with insights into that information.”
— Brian Feucht, Managing Partner
For corporate clients, a key benefit of standardizing on Cellebrite is the ability to prepare evidence for court. Cellebrite’s corporate investigation and eDiscovery solutions, such as Cellebrite Pathfinder, help clients’ legal counsel present evidence that is convincing and understandable to judges and juries.
“By using Cellebrite, our clients get fewer questions in court,” Feucht says. “In the past in many cases, we were using tools that weren’t commonly found in the commercial space, so we’d get a lot of grief from the opposing side about ‘What is this tool? Where did you get it? How does it work?’ By bringing everything under the Cellebrite roof, we don’t have those questions anymore. The brand itself is highly credible, which helps us a lot.”
The compatible Cellebrite solutions also help Unique Wire not simply extract and preserve data but also supply clients with high-level Digital Intelligence that ties together people, discussions, and content to shed light on cases.
We look at conversations, we look at what people are saying in the public space and in their internal communications,” Feucht says. “It’s the way to provide fundamental understanding of what the data is telling us. We dig into the complexity of the situation, so clients know what’s happening.”
The search becomes even more detailed when Unique Wire analysts work to analyze cloud data, as well as internal documents, such as in cases involving employee terminations.
“Cellebrite has saved us time, it’s recognized as the standard in the industry, and the support has been great. When we have a problem, we can actually pick up the phone and there’s someone to talk to.”
— Brian Feucht, Managing Partner
“We might expand the scope to include finding out who someone’s friends are,” Feucht says. “We start looking at the conversations that are happening in the public space. Then we start looking at what’s available on a business network, like internal communications.”
“Cellebrite has saved us time, it’s recognized as the standard in the industry, and the support has been great,” Feucht adds. “When we have a problem, we can actually pick up the phone and there’s someone to talk to. We’ll continue as a Cellebrite shop because it makes good sense for us as a business, and good sense for our clients. They’re now paying for our good work instead of paying us for custom programming.”
For more information on Cellebrite Enterprise Solutions, contact us at https://enterprise.cellebrite.com/sales-inquiry/
Detego’s customer* is a tier 1 bank in Africa which employs over 12,000 agents and supports customers through an extensive network of more than 200 branches. Faced with the constant risk of fraud, data breaches, money laundering and insider trading, the bank was looking to upgrade policies and procedures to improve its line of defence against these threats.
The compliance and fraud investigation teams already had a backlog of cases stemming from legacy data extraction processes and depended on multiple systems to extract data from different types of devices. The teams were also met with the added complexity of having to forensically secure data from non-brand mobile devices which weren’t supported by existing forensic tools.
*This case study was anonymised due to the sensitive nature of the investigations carried out by the customer.
After carefully reviewing the digital forensics tools in the market, the bank selected Detego’s Unified Digital Forensics Platform. Ease of deployment, advanced capabilities and the intuitive design, which enabled it to be used by team members with little to no technical knowledge, were among the standout features of Detego’s solution.
Detego’s Digital Forensics Platform presented the bank’s compliance and fraud teams with a single platform to forensically extract data from a range of devices including non-brand phones — saving them the hassle of switching systems to gather data from different sources. The platform’s ballistic imaging technology saw the teams forensically securing data up to 4 times faster, enabling them to improve case turnaround times.
The platform significantly improved the bank’s ability to pre-empt data breaches, fraud and insider trading with Detego’s Field Triage tool. It enabled teams to stealthily scan devices used by suspects for pre-configured search terms, files and activity that could result in potential threats.
In the last two years, the solution has helped the bank’s teams successfully identify and neutralise over 900 internal fraud attempts, helping the bank safeguard its customers, employees and reputation.
The bank’s proactive approach to handling fraud has been applauded by the international banking community. These measures have helped the bank climb nearly 200 places in The Banker’s Top 1,000 World Banks list in a little over two years.
Visit Detegoglobal.com to find out how Detego’s solutions can help.
Protecting residents since 1937, Nebraska State Patrol (NSP) is a police agency covering 77,000 square miles with 400 sworn officers serving a population of more than 1.9 million. NSP’s Special Operations Division, The Nebraska State Patrol Technical Crimes Unit, provides full computer and cell phone examination services for all state, local and federal agencies for free.
Tasked with investigations covering serious offences including Indecent Images of Children (ICAC), human trafficking and terrorism, and faced with the growing mass of digital devices and resource limitations, the team needed to implement a digital forensics solution that could simplify processes and extend their capabilities.
Increasing the speed in which data is extracted and analyzed, swiftly generating reports that are widely accepted by courts, supporting multi-platform setups and being efficient and cost-effective to run, were all part of the key requirements put forward by the team.
After evaluating the solutions in the market and getting a first-hand experience of Detego’s capabilities through a detailed demo, the Nebraska State Police chose Detego’s all-in-one digital forensics platform. Its ability to deliver rapid data extraction and analysis with greater accuracy, coupled with the inclusion of validated processes and ease-of-use, were clear differentiators.
The training and onboarding support provided by Detego helped the team get to grips with Detego’s technology.
The training and onboarding support provided by Detego helped the team master Detego’s technology in a short time. And thanks to the solution’s intuitive design and simplicity, team members were able to carry out forensically sound investigations with minimal technical knowledge and training.
By tapping into Detego’s automation capabilities, teams were able to automate time consuming imaging and processing workflows. This helped the team increase the rate in which evidence is processed by nearly 70%. Detego’s solution also enabled the team to gain access to a wider range of devices, including 1,000s of new mobiles, apps and platforms.
Prior to the introduction of Detego’s all-in-one digital forensics platform, the team were nearly 7 months behind mobile investigations and had a near 2 year backlog on computer data investigations.
Detego technology has enabled them to deliver crucial evidence to case officers in a matter of weeks and not months, and ever since implementing the solution, the team has been able to keep investigation lead times under 30 days.
“Like any other Law Enforcement Agency, we were falling behind and failing in overwhelming backlogs. We were able to leverage the speed, ease-of-use and capabilities that Detego has to reimagine and refine our process to become successful and increase our services. Detego increased our efficiency, provided a multiplatform solution and saved our agency tens of thousands of dollars in manpower, licenses and equipment.” – Sgt. Scott Haugaard, Special Operations, Nebraska State Patrol
Request a fully-functional 30-day trial of Detego and find out more information about the special discounts available for law enforcement teams here: https://www.mcmsolutions.co.uk/request-a-trial/
by Scott Hettinger
From a very early age, I was always interested in the work of law enforcement officers. I often found myself watching shows or movies about police, and every time I saw a police officer, I was so interested in what they were doing and wanted to know more. I looked up to police officers and always thought the job was exciting and interesting, with the benefits of making a difference in the community and the people who loved and visited my community. As I grew older and my parents knew of my aspirations, they let me know law enforcement was in my blood with multiple people in my family in some capacity in law enforcement.
One day, my parents gave me a book called “The Onion Field,” a story written about two Law Enforcement Officers with the Los Angeles Police Department, one of whom I was distantly related to, Karl Hettinger. After reading the book and ultimately watching the movie about the incident, I found myself even more interested in police work and wondered what I would do in that situation. I knew the second I was old enough to become a law enforcement officer I would jump at the chance. I entered the police academy and never looked back, with my first job as a patrol officer. I found the job very rewarding and exciting, and became interested in investigations. This is where I found my love for using digital evidence to further my investigations.
My passion for digital forensics started ten years ago while working as a Vice/Narcotics Investigator. I found terrific value in viewing the communication, media, and historical connections for the subjects in my investigation. The information I gathered through digital forensics allowed me to develop my criminal cases much quicker and more efficiently compared to investigators who were not using digital evidence at the time. Building and figuring out the integral network of criminal organizations is organically challenging, and digital evidence is often the key to investigators understanding the network or organization. As I began working in general investigations, it became more common for investigations to include some aspect of digital evidence. Digital devices are an extension of a person, and the evidence contained in those devices often makes the difference when it’s time for court.
Today, receiving or finding digital evidence is not only common. It’s expected. It’s rare in any case that a phone, computer, call detail records, or social media information aren’t submitted for examination or review in the attempt to locate case-related evidence. But working with digital evidence has its challenges, namely encryption, and backlog, which lead to the inability to get information to investigators promptly to further or complete investigations. “Normal” forensic software isn’t as useful or efficient when it comes to mobile devices as it used to be.
This changed when rumors began to spread about a special device called GrayKey. The release of GrayKey was a solution for a vast majority of devices we had in backlog during my time in law enforcement. The ability to gain same-day access to locked devices, under proper legal authority, is critical in providing complete, accurate, and actionable data to investigators or prosecutors assigned to a case. The GrayKey has proven repeatedly to be a valuable and necessary tool in the digital forensics lab.
In the case of the State of N.C. v. Titus Lee, the challenge was accessing a locked device. This device sat in an evidence locker for a long time as investigators built their case for court. After receiving a call from investigators on whether the lab could access the device or not, we were confident that GrayKey would be the forensic extraction tool we would use and result in a solid extraction of data. The ability for GrayKey to access the device in this case was extremely important. The extracted data provided evidence in the investigation that was paramount in the prosecution of the case.
When I met the team at Grayshift, I was surprised by their passion to help law enforcement and be a global partner that law enforcement could rely on to make their communities safer. I also saw engineers working tirelessly to provide support for the newest phones and software available. The Grayshift team is always working towards making the job of the investigator and examiner easier. When presented with the opportunity to join the team, I jumped at the chance to get involved and continue impacting the law enforcement profession and its mission.
The value of having digital evidence in a case is to have the whole picture of the crime. Watch how GrayKey provided critical evidence in State of N.C. v. Titus Lee case.
Watch the Video.
Detego’s client* is one of the busiest airports in London and handles close to 30 million passengers each year. Used by a large number of the region’s budget airlines, the airport facilitates travel to over 200 destinations in 40 countries. In recent years, the vast majority of Jihadi fighters attempting to enter the United Kingdom from Syria have arrived at this airport, making border security and early detection of terror-related threats a top priority.
The airport has Counter Terrorism Officers operating permanently as part of the wider Counter Terrorism Border Policing Group. In their role, these officers need to comprehensively examine and forensically secure data from digital devices which are in the possession of suspects. And with a limited window to gather critical evidence, officers needed a solution that can perform this task within minutes.
*This case study was anonymised due to the sensitive nature of the investigations carried out by the customer.
After carrying out an extensive evaluation of the digital forensics tools in the market, Detego’s Unified Digital Forensic Platform was chosen by the unit. The platform’s simplicity and ability to provide the quickest results for analysis were clear differentiators.
As a part of the deployment, Detego also delivered a training programme that was tailored around the needs of the team.
Since deployment, the solution has helped officers easily identify and neutralise a multitude of terror-related threats. The platform has enabled investigators to carry out data extractions in minutes – drastically reducing investigation lead times.
Detego’s field triage solution, which alerts users of files containing potential threats through a traffic light system, has enabled officers to seize suspicious devices for further investigation without the need to run resource intensive multi-stage data extractions.
The platform’s Ballistic Imager technology has helped officers forensically secure data from computers – recording up to 1 TB of data in less than eight minutes. Detego’s all-in-one platform has also enabled investigators to extract and analyse data from a range of devices including phones, laptops, loose media and drones. The team has also been able to gain access to internet browsing history and passwords on devices in under 30 seconds.
Sharing his thoughts on the solution, a senior member of the unit said: “We’re getting to grips with the software and love it! Great piece of kit…I have been singing its praises from a national perspective.”
Visit Detegoglobal.com to find out how Detego’s solutions can help.
Editor’s note: the information in this article has been reformatted for flow and clarity.
Detego’s client* is one of the biggest e-commerce businesses in the world that also has an extensive focus on artificial intelligence and cloud computing. The company’s UK operation employs more than 50,000 people across a network of nationwide delivery stations, and customer service, development and fulfilment centres.
Due to the complex nature of its logistical operations which see millions of products processed each month, the company’s e-commerce division was regularly met with internal and external threats including theft, arson and sabotage. While the company invested heavily on an internal investigations team, there were significant barriers to their success arising from resource limitations, dependence on disparate systems, a lack of documented procedures and case backlogs.
*This case study was anonymised due to the sensitive nature of the investigations carried out by the customer.
The company needed an all-in-one solution that could drive efficiencies by automating tasks and ensuring company-wide policies were followed when carrying out investigations. Detego’s Case Manager was chosen by the customer due to its user-friendliness, advanced automation functions and ability to create custom workflows based on the company’s policies and procedures.
Detego’s Case Manager provided the customer’s investigations teams with a single cloud-based platform that enabled them to create, assign and manage cases collaboratively. The team was able to map out processes for individual case types ensuring set procedures were followed. Detego Case Manager’s automation features helped generate automatic alerts when an incident was recorded – saving investigators valuable time. The simple, easy-to-use interface and the clearly documented workflows enabled even the more junior members of the team to carry out comprehensive investigations that were in line with the company’s policies.
Implementing Detego’s Case Manager helped the teams see a drastic reduction in investigation lead times, provided better visibility of ongoing cases and enabled better collaboration across the board. Case turnaround times were reduced by 37% and investigators were able to respond to incidents up to five times faster thanks to Detego Case Manager’s automated alert generation and escalation capabilities.
I’m responsible for the Department of Forensic Sciences, which has four divisions. There are CSIs of course, like in the movie shows, but they need a little bit more than one hour and a half to solve the cases.
Also the Division of Cybercrime, we develop knowledge competencies and infrastructure, not only for Geneva, but also for all the states for Western Switzerland, which is very exciting.
We have had EnCase for nearly two decades. You need a state police. We were the first one in Switzerland. So the concept of EnCase, the GUI, the training, the EnCE certification also was always a goal and a prerequisite for the people working in this division. One of the main subjects we deal with is chapter number three, of course, and cases used mainly for doing the research and trying to find back some evidence in those kinds of cases.
Also, for some encrypted data we use EnCase for those kinds of encrypted data, to try to find out some evidence. So the main part of this tool is to find evidence to solve crime and to find the people. Of course, I’m very excited for what’s going on in Switzerland right now. And this Regional Cybercrime Competence Centre is something very exciting. And the goal behind this is to put together forces, resources, people to fight for the same goal.
Internet Child Exploitation Unit (ICE) turns to OpenText EnCase Forensic to close cases faster and prosecute more offenders.
When child exploitation materials are uploaded to the Internet, websites often report those uploads to the National Center for Missing and Exploited Children (NCMEC) in the United States. If it is determined the upload of the exploitation material originated in Alberta, Canada, ICE gets called into action.
The Internet Child Exploitation (ICE) Unit, part of the Southern Alberta Law Enforcement Response team in Canada, is one of many agencies across North America that investigates offences related to the exploitation of children over the Internet that originate in the province of Alberta. This could include but is not limited to: the possession, distribution, importation and manufacturing of any child pornography and any computer-related child sexual abuse materials; luring children over the Internet; and voyeurism involving victims under the age of 18.
In addition to working with Canadian law enforcement units, ICE works closely with other law enforcement agencies in North America, including the FBI and Department of Homeland Security. Within the last year, in Alberta alone, ICE conducted 25 child interventions, identified 976,569 child exploitation photos/videos, seized 1,494 exhibits and devices and analyzed 153TB of data.
Typically, when a law enforcement agency is called upon to investigate a crime, they set about doing a background investigation on the subject and obtain a warrant that allows them to seize digital devices from the suspect’s possession. Because of the proliferation of electronic devices such as mobile phones, laptops, tablets and all of the other devices associated with the IoT (internet of things), forensic examiners and investigators are tasked with collecting numerous devices when investigating crimes and wading through the information on those devices to determine what information is applicable as potential evidence in their case. Often, suspect devices are taken from the crime scene to labs for analysis.
The process from evidence collection to reporting and prosecution can be a long one. To help bring their cases successfully to closure, investigators and examiners need tools that help them to quickly and reliably collect, analyze and store digital evidence that can be used in the arrest and prosecution process.
As an example, when ICE received a complaint about an unknown subject who was suspected of assaulting a young female, they searched his house and found 25 electronic devices that were likely to contain information relevant to their case. Needing to quickly identify potential digital evidence at the scene and obtain the information to effectively interview the suspect, they turned to OpenText EnCase Forensic Software. Designed for law enforcement, government agencies and corporations, EnCase Forensic provides the ability to quickly and reliably preview, collect and analyze relevant digital evidence.
“We use OpenText EnCase every day on every case we establish,” said Allen LaFontaine, Forensic Examiner with the Southern Alberta Internet Child Exploitation Unit. “In this particular case, thanks to EnCase, we were immediately able to determine that only 3 of the 25 devices we seized contained evidence relevant to our case, saving us precious time and resources in the investigation process,” said LaFontaine.

One of the issues facing the ICE team is the lengthy investigation process. It can be weeks or even months from the time they get the complaint, secure the warrants, seize devices, collect and analyze evidence, and prepare reports for investigators, attorneys and judges. “We need to be able to trim that down to hours or days in order to bring offenders to justice sooner and close more cases”. Examiners are also concerned about the efficiency of the evidence collection and analysis process. “Ideally, we’d want to have some clues from the devices we seize before we even start interviewing the suspect so that we can put together an airtight case as quickly as possible,” said LaFontaine.
“OpenText EnCase is a terrific tool for both the field and the lab, and in this case meant we didn’t have to spend time acquiring the devices and then taking them back to a lab to examine them. We were able to use EnCase’s preview capability to look at the devices at the scene within an hour after we received our search warrants. This meant we were able to start collecting evidence within seconds instead of hours,” said LaFontaine.
The quicker the team can capture evidence, the more likely they are to be able to apprehend the suspect. “We were also able to use some of the features in EnCase that grab the memory from those devices, build a dictionary of key words and then use those key words to break passwords the suspect had set on the devices. EnCase really helps us get to the meat of what we need quickly,” LaFontaine explained.
Unfortunately, ICE receives far more complaints than they are able to pursue. However, according to LaFontaine, “With EnCase, we see a significant improvement in our efficiency, allowing us to investigate more complaints and bring more offenders to justice.”
In this particular case, ICE examiners and investigators were able to use EnCase to collect evidence that proved the suspect was not only assaulting his daughter but was also assaulting additional under-age daughters.
Sadly, NCMEC received over 1 million complaints last year, leaving our law enforcement agencies worldwide buckling under the pressure to pursue all of these cases. With EnCase Forensic, law enforcement is able to reduce the strain on their resources, reduce the time to case closure, investigate more cases, and prosecute more offenders to ultimately make the world a safer place.
Digital Exploitation complexities face the modern combat soldier (DOMEX/MEDEX MPE). This Special Ops Unit is charged with overseeing the various Special Operations Component Commands of the Army, Marine Corps, Navy, and Air Force.
The Executive Office is responsible for the acquisition, fielding, and sustainment of intelligence and exploit systems for Special Operations Forces (SOF). The systems contribute directly to the Client’s priorities to deter, disrupt, and defeat terrorist threats and sustain and modernise the force. The current and projected threats to this region continue to evolve in response to the increased technological sophistication and effectiveness of fielded capabilities.
Acquisition strategies relying primarily on innovative contracting approaches, evolutionary technology insertions, and a prudent balance of cost, schedule and performance requirements are required.
Digital exploitation is a growing concern with over 2 billion laptops and PCs in the world and a staggering 5 billion phones, plus countless portable storage, and removable media devices. The necessity to be able to exploit devices on discreet or direct-action missions is essential both at the frontline on the battlefield and within Labs.
Common related issues to effectively achieving this are: device types, encryption, counter forensics, time, data size, technical skill requirement, forensic integrity, skill depletion, SWAP, operator friendly technology, innovative solutions to complex problems, flexibility, reactive technology, need for multi-disciplines, organisation rollout size and associated training complexities.
Detego is proud to be placed as the key technology selected in order to meet the commander’s intent. The Client’s Program is tasked with finding globally the best solutions at the highest levels for Special Operations success. The effective project is headed by a programme lead with a budget in excess of $20 million/ £14.4 million PA.
Detego Field Triage, Ballistic rapid imaging coupled with link analysis, powerful A.I and automated forensics processes all assisted in Detego beating competition in a crowded technology field. Detego even removed a previous incumbent tool, proving why it is the number one choice for Militaries, Police and Intelligence agencies around the globe.
The Client’s process of selection involved rigorous testing from technical, commercial and operation standpoints culminating in acceptance and agreement across multiple varied component units which make up the overall organisation – no small task!
The Special Operations unrelenting pursuit of excellence for a better DOMEX solution is continuously being assessed and evolving, with development in Detego matching the required pace and currently an estimated 700 units out to investigators.
Training and roll out on such a large deployment of technology has been approached in a collaborative and positive manner. This had enabled Detego technology to be devolved to both frontline operational users and Exploitation LAB specialists.