Anyone had issues using the checkma8 exploit using Cellebrite to get the full file system extraction? Have a 6+ that it gets to about 13% then goes no higher. Shows still running but never gets past 8.69GB after several hours. Left it running when I left work so I hope it gets passed whatever is holding it up.
Just in case, the iOS version above 12.3, yeah?
Anyone had issues using the checkma8 exploit using Cellebrite to get the full file system extraction? Have a 6+ that it gets to about 13% then goes no higher. Shows still running but never gets past 8.69GB after several hours. Left it running when I left work so I hope it gets passed whatever is holding it up.
Just in case, the iOS version above 12.3, yeah?
Yes, it was 13.3. When I got in to work it had finished.
I am curious, how did you add the dar file into PA? Did you just select the ufd file or select the dar artifact? Did you break the dar file into chunks or keep it as a flat file?
I created a dump from the UFED touch to a USB and made the files into 2GB chunks. When I brought it into UFED PA, i had to carve to get the data.
Go into the bottom folder of your acquisition folder and find the FullFileSystem1.dar file; next to it should be a UFED Dump file. Click on the UFED dump to load the .dar into PA.
I took some screen shots for you, cant figure out how to add them to this reply - please PM your email and I will send right over.
Cheers
Rory
This weekend I did more testing with the new Checkm8 exploit, this time with an iPhone 6s, iPhone 7 Plus, and iPhone XR. I will post notes on 6s in future; there is no Checkm8 option for the iPhone XR currently (see below), even after updating iOS from 12.1.2 to 13.3.1.
So below I will cover the test iPhone 7 Plus.
-iPhone 7 Plus Model A1661
running iOS 13.3
- 32 GB capacity
-Available space 11.52 GB
-I tried both with and without access to the phone passcode
I ran Logical Method 1 in Physical Analyzer; it collected a 13.9 GB .tar
Ran Logical Method 2 in Physical Analyzer; it collected a 17.7 GB .tar
Opened Physical Analyzer and loaded Method 1 and Method 2.
Opened Physical Analyzer and loaded Method 1 & Method 2.
Next I took same test phone and opened UFED 4PC
Plug in phone and auto detect; check model in phone’s settings to confirm correct; select
Advanced Logical then Full File System Checkm8*.
Put phone in DFU mode**
When it finished, loaded in Physical Analyzer.
*This will only be an option if the phone is within the models and iOS ranges described
**The iPhone 7 Plus was no problem, but it took me numerous attempts to get the iPhone 6s into DFU mode. It was finally accomplished with the help of this video (753)
https://
Same for iPhone 8 timing is tricky so practice, this one helped me
https://
Checkm8 will run (see pics) and you will be prompted on your machine for phone’s passcode.
Phone showed 73.28 GB extraction as it was in progress.
Advanced Logical Full File System Checkm8 acquisition with passcode collected a 35.8 GB .dar
Opened Physical Analyzer and loaded Advanced Logical Full File System Checkm8 acquisition.
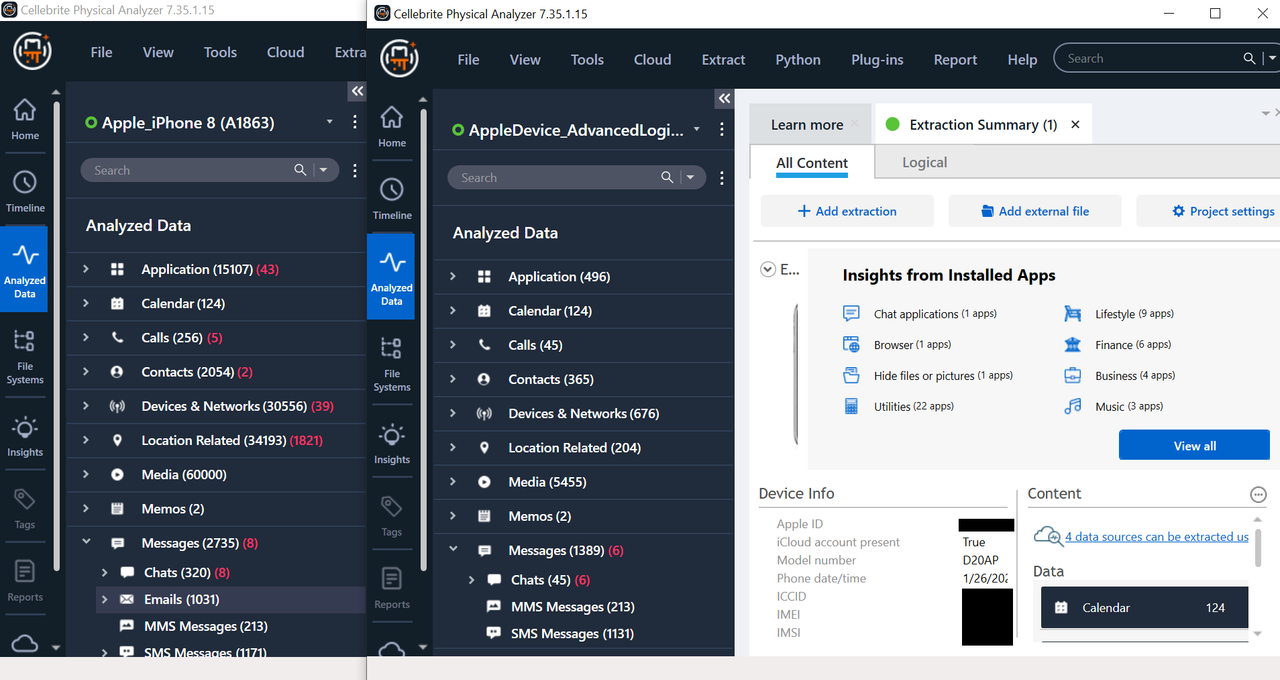
Comparison photos – same as last time, on the left is the combined Logical Method 1 & Method 2 using PA. On the right is Advanced Logical Full File System Checkm8 using UFED. Also posted cropped together photos showing all data sets pulled. The results speak for themselves.
Also included photos of when the Checkm8 exploit starts and the extraction screen. Photos available here
https://
I tried following the guide I linked to above to obtain a partial file system (Before-First-Unlock) with no passcode. I changed the passcode and then did not enter the correct passcode again. After several tries and poking around for forums & articles, and a million failed attempts and reboots, I called it a night but will try again. If anyone can share their method or any good articles/guides/forum posts on checkra1n/ Checkm8 BFU, it would be greatly appreciated. Interested in seeing what it collects.
Rory
@grizzlydigital I've searched for this everywhere and I feel like this post is the most informational and could help me out. You mentioned that Checkm8 allowed you to pull emails. Did you mean that you can now extract emails from accounts logged in to the Apple mail app or any 3rd party mail app? Would it be possible to pull emails from an specific email app such as Yahoo Mail app or Gmail app using UCEF method 1 and 2? Or will Method 1 and 2 not pull emails at all? Thanks.
@authoxic Glad I could be of help! Checkm8 has evolved since it came out, and my experience has given me a few interesting anecdotes - I included at end after answering your questions.
Did you mean that you can now extract emails from accounts logged in to the Apple mail app or any 3rd party mail app?
The testing I did when I posted that included phones that had a few emails accounts, and yes Checkm8 successfully parsed 3rd party mail apps. If you direct message me, I will send you some photos.
Would it be possible to pull emails from an specific email app such as Yahoo Mail app or Gmail app using UCEF method 1 and 2?
The full file system extraction successfully identified and included all email accounts on the test phones, and full body messages, dates, times, subject line, etc.
Or will Method 1 and 2 not pull emails at all?
Current (as of 9/23/20) Method 1 and 2 extractions will routinely pull emails, but my experience is that the email data Cellebrite pulls is incomplete - it does not contain the body of the email - but it will pull the date, time, sender, recipient, and even subject line data, but I cannot recall seeing unencrypted, email body messages with Method 1 and 2 extractions; I have seen with Checkm8. Also - even though Method 1 and 2 does get you the limited data I mentioned, it is incomplete (i.e. not a 1:1 as compared to the user's actual mail box). Why? There are too many variables to render an opinion.
I have run into a scenario where Checkm8 was outperformed by Logical Method 1 & 2.
The objective was to obtain text messages/chats/SMS/MMS; Logical Method 1 and 2 had been previously run on phone 6+ months ago and obtained a significant number of messages. The phone was then placed in storage/off state. With the release of (and spreading awareness of) the Advanced Logical Full File System Checkm8 method, it was requested for a phone to be reacquired with the new Checkm8 method. However, the Checmk8 acquisition did not collect any messages. Why did this happen? It may have to do with whether the phone is “hot” or “cold” – the recovery of data (especially deleted data) is enhanced if the phone has not been powered off.
Before COVID, while at Cellebrite’s CCO+CCPA course earlier this year, we discussed Checkm8, live file system analysis, and why the best answer for “Can you get deleted texts?” is “…Possibly”
We covered the fact that Cellebrite can dump a Live File System. As I understand it, the best methods available by Cellebrite are:
- Physical (Only available for iPhone 4 or older)
- Full File System (you can Possibly retrieve recently deleted information, but no unallocated space)
- Logical
Live: After First Unlock (AFU) “Hot”
- The phone has been kept on since it was unlocked (not powered off)
- Encryption keys are still in RAM
Restart: Before First Unlock (BFU) “Cold”
- The phone has been turned off or battery died (such as when phone is stored or shipped)
- iOS provides some data
Since the phone’s processor is needed to decrypt data, keeping the processor available is critical after seizure. Since the decryption keys are still present in RAM, we can exploit phone and access decrypted data. If the phone has been turned off or battery died, phone is in cold state, and only unencrypted data within the file system is available.
Checkm8 is very powerful, and it has its place in the toolbox. For cold cases/old cases, however, it may not provide the expected result of a massive increase of extracted data.
Thanks for all that information! You were finally able to answer the question I had been searching an answer for, and in great detail, I really appreciate it! Now just one more question if you have time, will UFED Method 1 and 2 be able to get me any attachments on any emails? I believe I read that checkm8 will extract downloaded attachments, but will UFED Method 1 and 2 yield any? Thanks I'm advance!
@authoxic
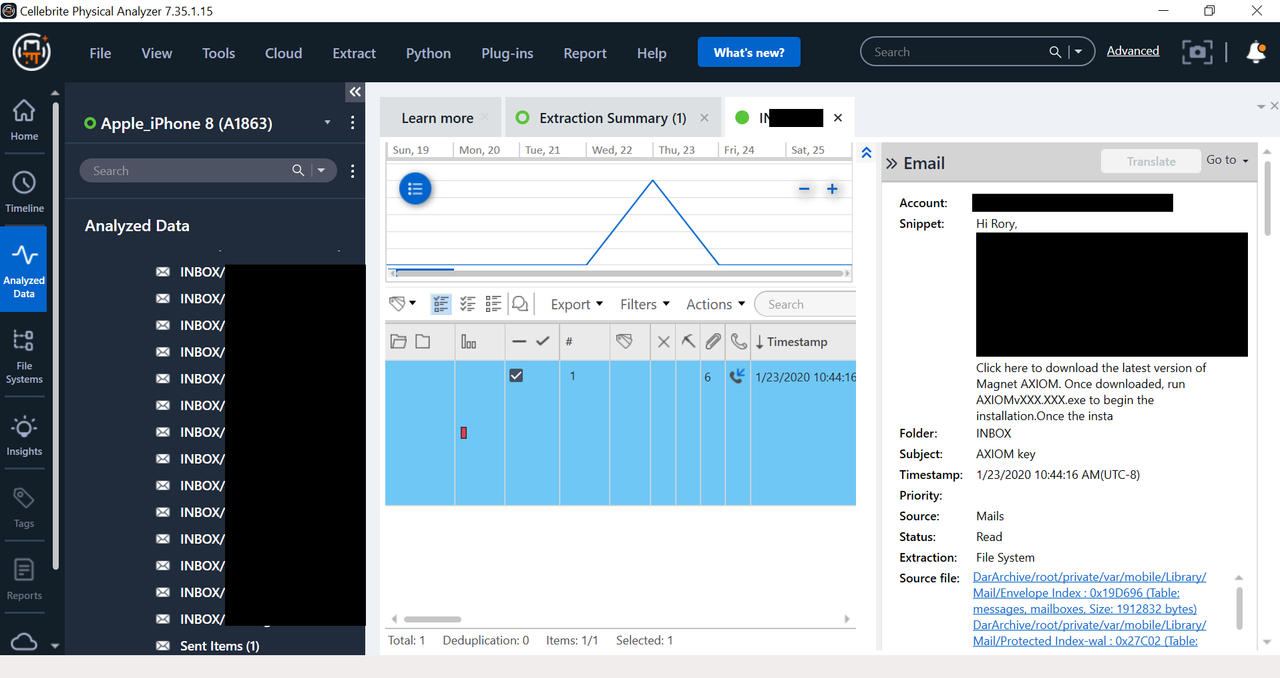
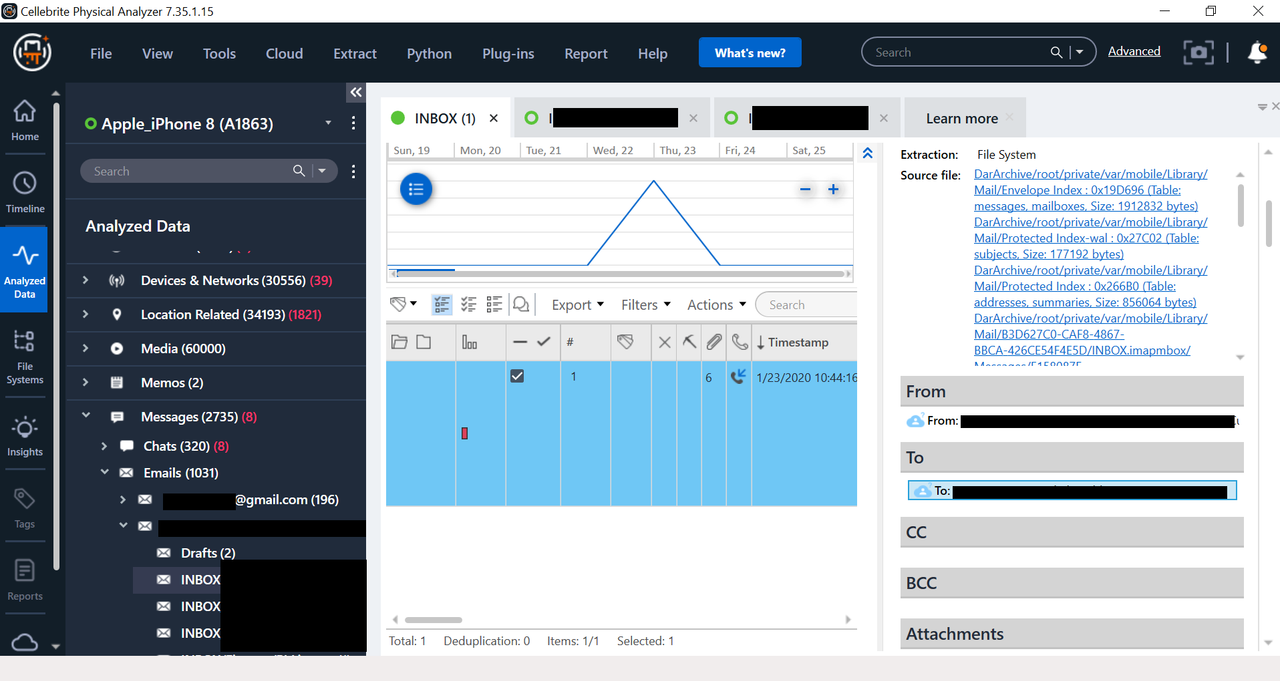
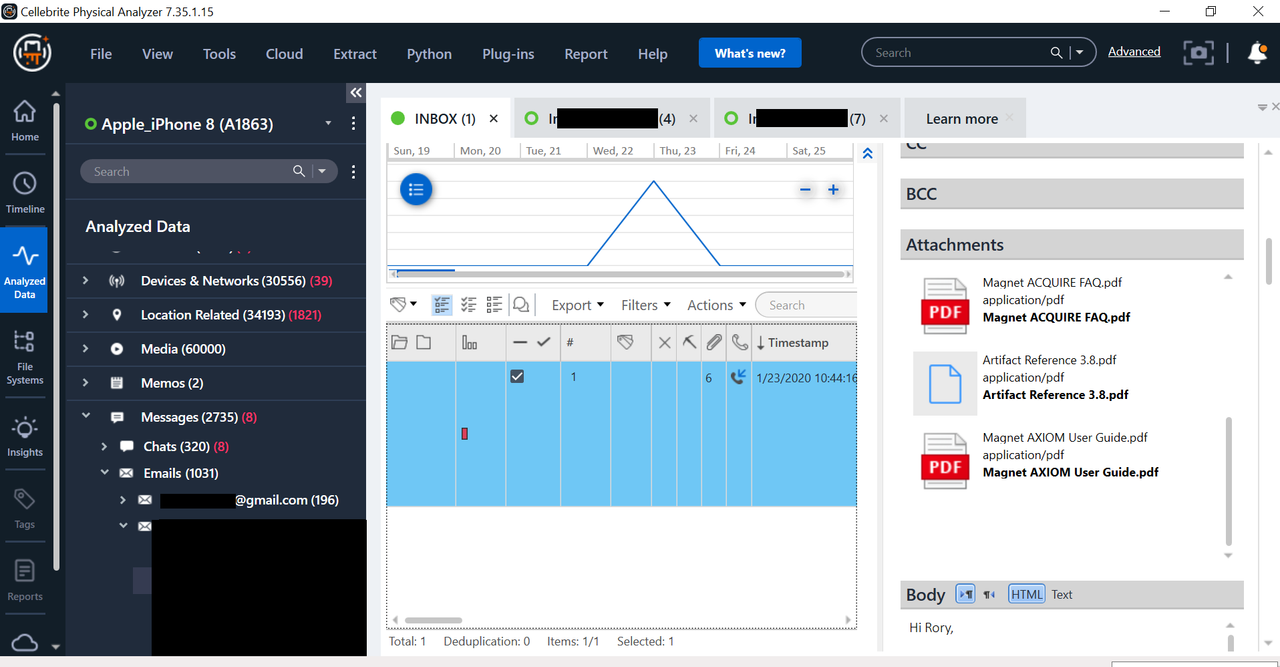
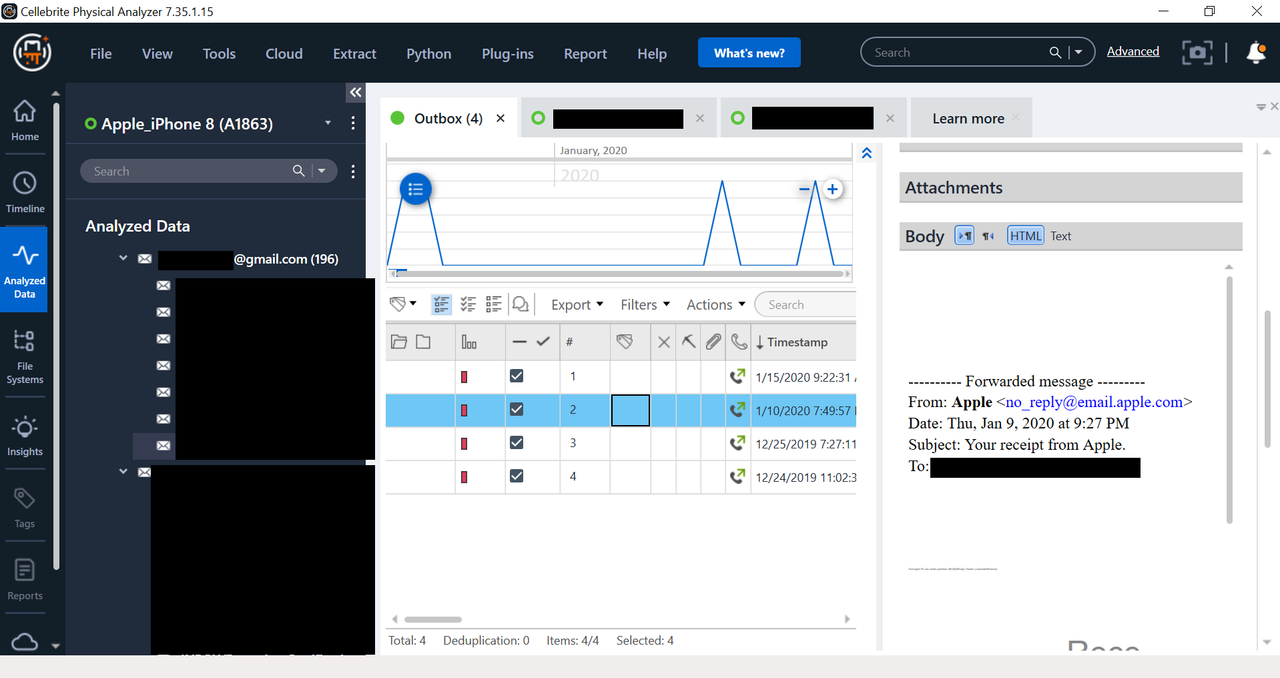
Here are screenshots for you of the same phone an iPhone 8, I ran Checkm8 and also ran Logical Method 1 and 2.
These photos show full body text of a private SMTP email account, as well as attachments. I blacked out some data, but you can even see full folder structure of email.
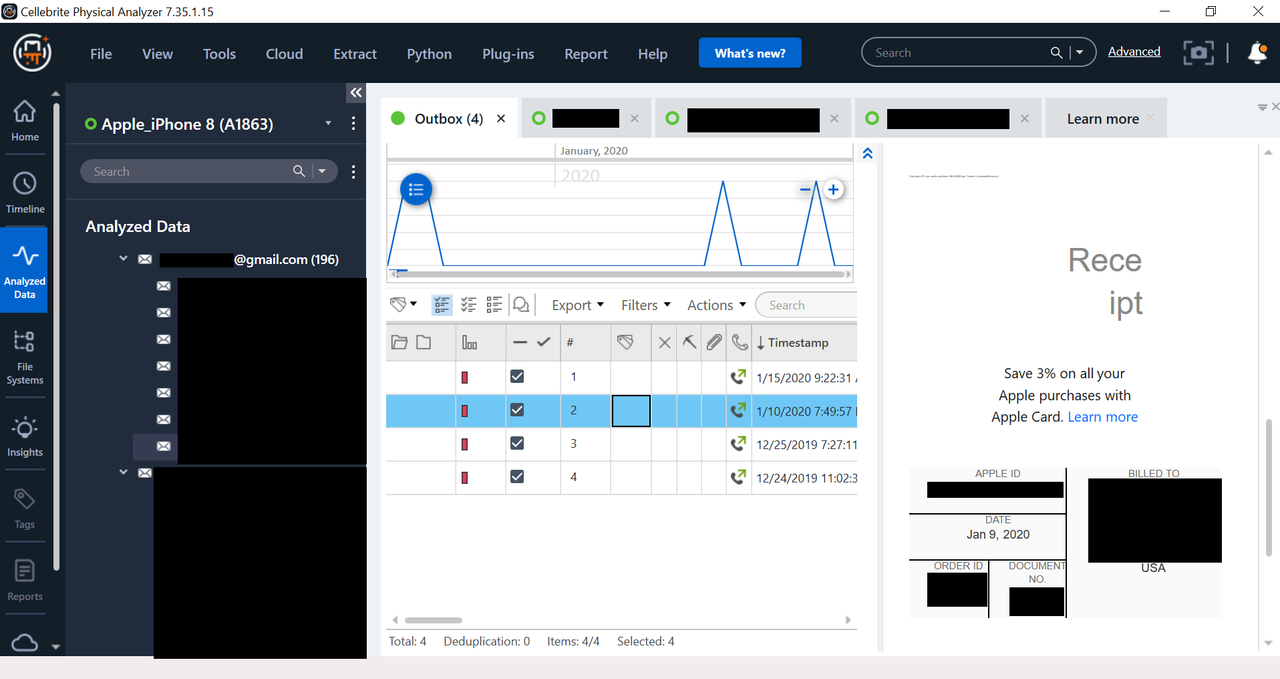
Additional photos show a Gmail account. Full body text of email, but in this example the photo did not show up under "Attachments" but is visible in the screenshot as embedded in the email body. These photos are of the same phone, Logical Method 1 and 2 extraction. As you can see, no emails.
I checked one other TEST Logical Method 1 and 2 extraction (an iPhone 6s), no emails or attachments. But a Checkm8 extraction on same phone identified and parsed full emails with attachments (no photos provided)
I have seen Logical Method 1 and 2 pick up emails, but like I mentioned the body of the email is not available, nor attachments. Cannot post screenshots, those are real cases.
Hope this helps!
EDIT: Cannot figure out how to upload the photos to forensic focus. I will PM you.
EDIT: Cannot figure out how to upload the photos to forensic focus. I will PM you.
I noted you have mentioned this a couple of times. Having photos connected to your posts would be helpful.
Here is free service that allows you to posts your photos at FF using various weblinks depending on the website/forum you are posting messages.
https://i.postimg.cc/
https://postimages.org/
Examples of images posted previously. Use the Thumbnail and Hotlink for websites. The Forum link seems not to work at FF
Oh man, you are awesome! Ok great! I will upload the photos 🙂
Here are screenshots for you of the same phone an iPhone 8, I ran Checkm8 and also ran Logical Method 1 and 2.
These photos show full body text of a private SMTP email account, as well as attachments. I blacked out some data, but you can even see full folder structure of email.
Additional photos show a Gmail account. Full body text of email, but in this example the photo did not show up under "Attachments" but is visible in the screenshot as embedded in the email body.
These photos are of the same phone, Logical Method 1 and 2 extraction. As you can see in last photo, no emails.
I checked one other TEST Logical Method 1 and 2 extraction (an iPhone 6s), no emails or attachments. But a Checkm8 extraction on same phone identified and parsed full emails with attachments (no photos provided)
I have seen Logical Method 1 and 2 pick up emails, but like I mentioned the body of the email is not available, nor attachments. Cannot post screenshots, those are real cases.
Hope this helps!
Link to gallery of photos: