Hello,
I'm am new to computer forensics. I am currently enrolled in a Digital Forensics I course and am trying to explore outside the course material. I personally have been working as a system administrator for the past 3 years. In class we were given a test image to load into FTK. we are using a free version, which is v1.071 - DEMO. We are using the image to get an introduction to FTK, by using index search to find key data, bookmarking that info and then creating reports.
In the image I noticed that there are several files that FTK has marked as encrypted. Several word documents, and 2 PGP secret key rings. I exported all of the files and the word documents are password protected. My question is how can I decrypt those Word files to gain access? I've done a lot of googling but haven't found any concrete answers. What I have done so far is download PGP Desktop, and import the keys I have found. In an email from the test image the public PGP key was shared, so I have the public key and the private key. I'm stumped as to what to do next. A point in the right direction would be helpful, thank you.
For the Word documents, it depends on which version of Word was used to create it.
For example in Office 97 & 2000, only 40bit encryption was used and you can brute force the key in a reasonable amount of time (without ever knowing the password).
In Office 2007 and newer versions the encryption is much better, and often you are forced to guess the password or attempt to brute force the password. e.g. a dictionary attack. The typical AES 128bit key length is too long to be able to brute force the key itself.
Don't confuse the password and the encryption key, they aren't the same thing. The key is derived from the password, in the case of Office 2007, the password the user selects is subjected to 50,000 iterations of SHA-1 to turn it into a key. This also makes password brute forcing rather slow as you have to do 50,000 SHA1 calculations for each password you want to guess.
In a forensic scenario where you have obtained a suspect computer, and you encounter some encrypted files, what sort of process would you go through to try and decrypt them, or get the password to unlock them?
Followup what tools do you use to brute force or dictionary attack files?
Are you attending any FTK course? IF so, what you have to do is to use the word list. I have never used FTK but as I know there is an option to export word list, created when FTK index the case. Than use this word list as dictionary to run dictionary atack using AccessData password decryption tool PRTK
I am not. I am just in an Intro to Digital Forensics class. Any advice on free tools i can use? At the moment i do not have the $$$ to purchase a License for PRTK
I am just in an Intro to Digital Forensics class. Any advice on free tools i can use? At the moment i do not have the $$$ to purchase a License for PRTK
I'm honestly not sure if there are any free tools to break passwords protecting documents saved with recent versions of Microsoft Office. While there are tools that can remove passwords to modify or VBA project passwords, passwords to open are something completely different. These are used to encrypt the document with a secure key derived from the password itself.
We're making one of the password recovery tools, Elcomsoft Advanced Office Password Recovery (AOPR). In our lab, we measured the speed of recovering passwords for recent versions of MS Office. As you can see on the chart below, a single PC can enumerate some 370 passwords a second without using a GPU accelerator or about 8,000 to 24,000 passwords/sec with a GPU accelerator (basically, any gaming video card will pass as an accelerator).
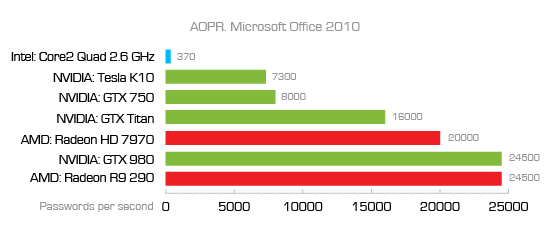
For Office 2013, the numbers are even lower.
Now, as you're saying you're in an Intro class, it should not be that difficult to break the actual password. Try looking for other passwords of that same user. Assemble a list. Are there any identical or similar passwords (e.g. password1, password2, password 3 etc.)? Try each password you've found to open that document. If the course is designed correctly, one of those can match.
You can't go wrong with John the Ripper (jumbo) and oclHashcat. The rules you can make in these programs are far more detailed than what you can get with commercial tools like PRTK, Passware, and Elcomsoft.
Even though we have licenses for the commercial ones, we still end up cracking most passwords with oclHashcat and then making a dictionary out of the .pot files and using it for bulk decryption.



