Hi,
I have executed a "fdisk -lu" command on a NTFS image. The second to last column lists the "System ID" (which are 70,43, 72 and 0). I know that 72 is the extended partition and 0 empty partition. I am mostly familiar with FAT and NTFS filesystems only on Windows. What are the partition IDs 70 and 43? Are they widely used?
Thank you in advance.
K
========================================================
You must set cylinders.
You can do this from the extra functions menu.
Disk windows-ntfs.img 0 MB, 0 bytes
windows-ntfs.img1 ? 6579571 1924427647 958924038+ 70
DiskSecure Multi-Boot
windows-ntfs.img2 ? 1953251627 3771827541 909287957+ 43 Unknown
windows-ntfs.img3 ? 225735265 225735274 5 72 Unknown
windows-ntfs.img4 2642411520 2642463409 25945 0 Empty
[root@linux images]#
========================================================
72? 😯
As you can see that is UNKNOWN, not "extended".
Forget for one moment the grep, just run fdisk -lu
You are talking about the "subtype", not about "Ptype" in a screen like this

(BSD)
Or about the Partition ID, in a screen like this?
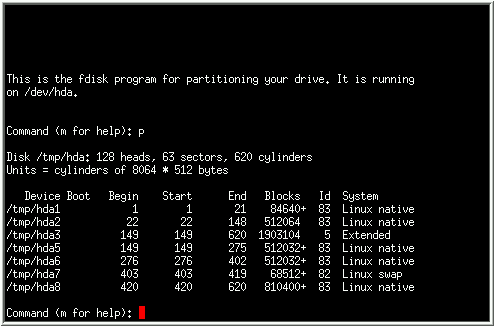
(Linux)
Here
http//
What do you mean a "NTFS" image?
It is either a "full disk" image (i.e. containing the MBR, i.e. the partition table) or a "partition image" (or "superfloppy) that can be a "NTFS" image, in which case you have NOT the MBR, not the partition tables, and in this case it is possible that what fdisk -lu is simply "senseless" data coming form the bootsector.
jaclaz
The NTFS img file is that has been captured using dd (or similar tool). The image file can be of an entire disk or a partition.
I have been to that URL which lists all the partition IDs. I use, analyze and repair only a subset of these partitions for my Windows and Linux boxes. The main question is, are the partitions 70 and 43 widely used? And where?
These partition IDs are from a forensics image (not a real case) that needs to be analyzed. I need to figure out what type of computer or file systems types that the end user is using.
K
I'll try to rephrase
IF the image is that of an entire disk, THEN
1. it is NOT a "NTFS" image
2. the data you can get with fdisk is accurate
IF the image is that of a Partition, THEN
1. it can be a "NTFS" image
2. the data you can get with fdisk is senseless, as there is no partition table in it
or again, fdisk ONLY makes sense on a whole disk image, NOT on a partition image.
jaclaz
P.S. You may want to read here
http//
http//
http//
as you can see on a NTFS bootsector, in the place where partition tables are in a MBR there is OTHER CODE.
Coincidentally, where partition types are, in the English NTFS bootsectors are values
72
74
65
00
and next to them
70
43
72
00
does this ring any bell?
Why would you run a partition application against a logical image file? You shouldn't expect to read accurate partition image when running 'fdisk' against a file system image. Against a physical image, yes. Logical, no.
So, if this is a logical image that is solely a NTFS file system then that may be the source of the 'fdisk' information oddity.
Cheers!
farmerdude
Thank you for explaining this!
What tools should I use against partition images to get the partition layout? I am looking for files, directories and their metadata.
K
Thank you for explaining this!
What tools should I use against partition images to get the partition layout? I am looking for files, directories and their metadata.
K
Why don't you mount the image file?
And then use "normal" filesystem tools?
Or (for some data) you may want to use TESTDISK
http//
Or you may want to use some Forensic utilities….
http//
Read related tutorials articles
http//www.forensicfocus.com/hidden-data-analysis-ntfs
In other words
WHAT EXACTLY are you trying to do/WHAT EXACT data you need to retrieve/look at?
Then, after having read and understood the basics of the filesystems/partitioning, etc., you could ask specific questions about something that you still have not clear.
A tool is, well, a tool, nothing more, it is the knowledge, the skill and experience of the user of the tool that makes it useful. wink
Don't take it the wrong way, but it seems to me like you asked
What do I use to shorten a wooden plank?
To which anyone can answer ANY of the following
a saw
a hacksaw
a circular saw
a band saw
a jig saw
an axe
a hatchet
They are all valid answers, but each of them has it's own advantages and drawbacks, there may be a "better" answer among them for your particular case.
And however, using the "right" tool does not guarantee that the wooden plank will be shortened to the right measure and with a clean cut if you don't know how to use the tool properly….
jaclaz
kleanchap,
If you want to dump file system meta data and file metadata and data then you would call upon file system and file tools. The NTFSPROGS package has a number of file system metadata tools. Various forensics applications do as well.
You could use a mount tool such as SMART MOUNT to mount the file system image and then your normal operating system environment to analyze the data.
Cheers!
farmerdude
Some more ideas - that I often refer to
http//
Also have a look at the start of the partition, can often indicate what it is
Just a suggestion but you might get more assistance if you posted the hex from the start of the image rather than the ouput from some tool.



