I have a friends iPhone 4s which apple "genius's" have managed to damage beyond repair. It appears that they were careless when removing the battery and have actually ripped the solder mount points for the battery connector off the logic board. There is also some damage around that area so re soldering the battery connector is not going to be possible.
I have no experience in chip off or jtag so I'm not sure what my other option are here.
I'm not sure what her budget is but thought I'd find out if there is another way to go first.
Can iPhone 4s be downloaded via jtag?
You acquire encoded dump. Can you decode this dump?
The data are encrypted for iPhone 4s etc so it is not worth performing chip removal. As Igor comments what would be decode solution for the dump via JTAG.
It would be useful to have more examples of chip/pcb mapping that may assist finding solutions not yet considered when faced with examining a dead/damaged iPhone e.g.
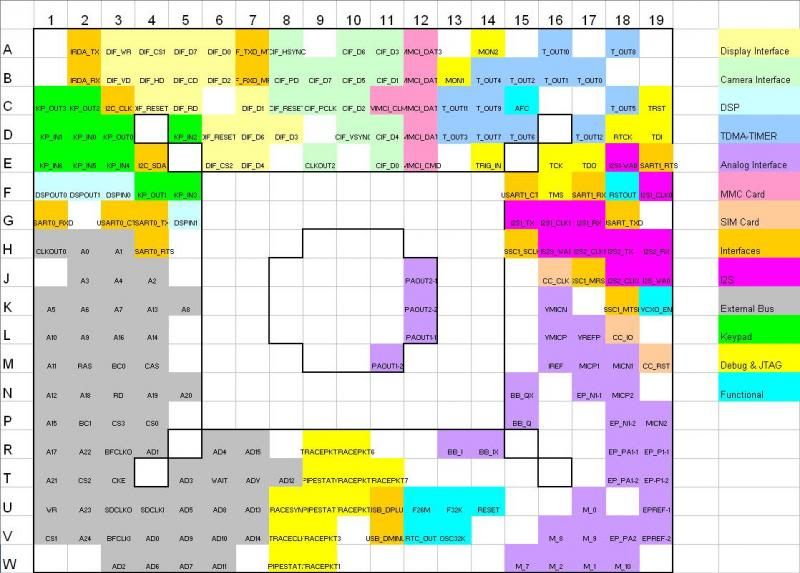
Problem with Apple phones is that they use ASICs, so anything about their design and pin out has to be reverse engineered. This is not the case with most other embedded solutions (yet).
Just my experience. mrgreen
Thanks gents, I had sort of figured by the lack of available information I could find that it would be unlikely.
Given how popular iPhones are if it could be done easily I would have expected to find lots of information around the place about it.
Given that it's a friends phone and not life and death I suspect she will have to bite the bullet and kiss the data goodbye.
Trewmte given my lack of experience in the area of Jtag I didn't really have any solution or thoughts as to how to decode, I was more wondering if it's even possible to get a dump this way. If I read the comments correctly Jtag dump of the iPhone is 'technically' possible, but finding the Jtag points on the logic board is not easy or known. Is that right?
This is an area I'm very interested in and am currently putting a business case together to try and get some training but given 90% of phones I see in my role are iPhones it sounds like it might be a waste of time and money if none of the newer models can be decoded yet.
Trewmte given my lack of experience in the area of Jtag I didn't really have any solution or thoughts as to how to decode, I was more wondering if it's even possible to get a dump this way. If I read the comments correctly Jtag dump of the iPhone is 'technically' possible, but finding the Jtag points on the logic board is not easy or known. Is that right?
Hi Adam10541, my comments are not the best of answers to encourage or discourage you undertaking the training your mentionjed. My comments were overlaid to Igor comments. If JTAG were possible could the output be decoded? I do not yet have the answer to the decoding.
The possibility/potential for JTAG access much of the research/forum coverage out there suggests it isn't possible to use JTAG. There are some alternative observations, which I haven't verified as yet, but are worth noting.
1) Riff Box promotes the RIFF JTAG – Apple iPhone 4S Unlock via USB cable, World First ! ! !
( http//
Is there something that can be developed by USB?; is the use of JTAG in the product name being misunderstood and just a marketing name?
2) In January 2014 a contributor to the gsmhosting forum suggests having identified what appears to be JTAG connections are sent to the "dock, ..TDO,TDI,TMS,TCK etc." from literature the contributor had read. Later on in the same thread the same contributor refers to "trace usb BB debug and BBjtag connections" and confirms
" found them -
next to sim socket -
TP82_RF - BB UART TXD
TP89_RF - BB UART RXD
TP28_RF - BB UART RTS N
TP29_RF - BB UART CTS N
Easy access for soldering connections"
( http//
The contributor seems to be referring to baseband but it maybe with further digging around as there maybe more isolated research that could prove useful. I am just about to read some new research papers which may shed more light on this matter.
Generally, the evidence is against using JTAG for access but it could be by widening the search area for JTAG access on the iPhone maybe required.
I second Gregg's (trewmte) caution.
Just because you got the raw data off of the device. be it JTAG, chip-off or some other method, it does not resolve your issue with the encryption.
Imagine iPhone's functioning like TPM enabled Bitlocker encryption in Windows environment. What would you do if you got the image of the encrypted volume and no key?
I believe by default since iPhone 3GS, the iPhones are encrypted, and part of the key is baked into the hardware.





