Hello guys i got 2 unlocked iPhones with no Security Codes and took a backup with UFED TOUCH, however physical anaylyser could not parse the image and asks for encryption password, while i have not set any password.
I tried to take a backup using itunes too, it can only take encrypted backups, i cannot untick the option.
both iphone 6 are running 10.2.1
Any thoughts?
Try 1234
I contacted Cellebrite they told me the same, unfortunately it did not work.
This is interesting.
The user enabled iTunes backup encryption, this is independent from the passcode.
1234 is the default password which is set by Physical Analyzer if there has not been set a password by the user and you tick the "encrypt backup" box during the extraction process. So in this case this will not work of course.
As far as I know you have these options
a) Jailbreak it (if possible) and extract data with method 3 in Physical Analyzer. It will not be encrypted.
b) Use Elcomesoft Phone breaker and try brute forcing the password. Or you can create a list of passwords and throw it in Physical Analyser if asked for a password.
This probably won't work because Apple changed the password hashing algorithm with iOS 10. Brute forcing is now very very very slow. So basically this is not really working anymore.
c) Ask the owner of the phone for the password
Very informative.
Oxygen Forensic Detective can also help you to find the password to the encrypted iTunes backup. The built-in Passware module uses the latest algorithms and technologies including distributed processing and GPU acceleration with ATI and NVIDIA boards. The software offers varoius attacks such as brute-force, dictionary, Xieve, etc.
iPhone uses PBKDF/HMAC2-SHA256 (+10 million iterations) and you can BF it with free HashCat - https://
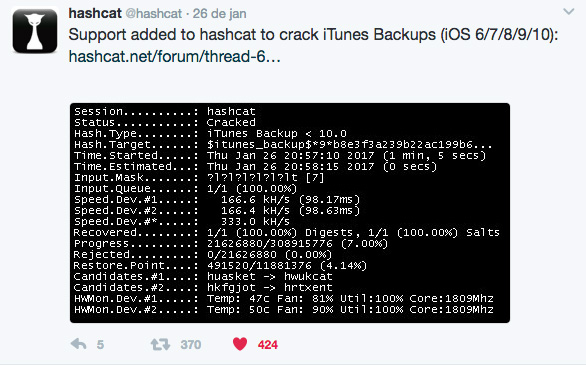
That's really good, I've never used hashcat to break iTunes backup before, do you have commands or a guide so I can try and explore?
Thanks.
That's really good, I've never used hashcat to break iTunes backup before, do you have commands or a guide so I can try and explore?
Thanks.
@Bolo I'm interest too, and I think I'm not the only one.
It doesn't seem that complex to use, after having extracted the hash
https://
https://
jaclaz





