Hi guys,
Im just in the early stages of learning about mobile phone forensics. My question is what is the partition system in SIM cards? I know that SIM & USIM are different types of sim cards sometimes used together on multi-application cards. Are the partitions therefore SIM & USIM? As simple as it sounds i cant find any clear information about this online.
Hi guys,
Im just in the early stages of learning about mobile phone forensics. My question is what is the partition system in SIM cards? I know that SIM & USIM are different types of sim cards sometimes used together on multi-application cards. Are the partitions therefore SIM & USIM? As simple as it sounds i cant find any clear information about this online.
SIM and USIM are separate modules.
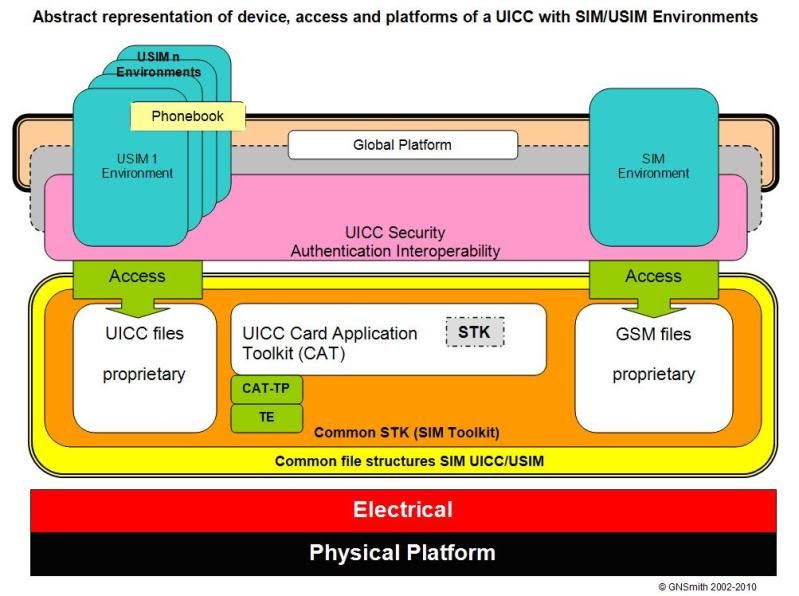
To see the full image
http//
I've not had to do much on SIM forensics as generally there is very little relevant stored on them.
The SIM partition is used to communicate on the GSM network (pre 3G) where as the USIM is used on the newer 3G network (and presumably the 4G as well).
In Australia most SIM cards will be dual partition, however the SIM cards I've seen from the US and UK were mostly USIM only and I believe in the not too distant future the dual band SIM cards will likely go the way of the dinosaur.
If you do a quick google around there are many good whitepapers around that you can read, and after reading a few of those that picture trewmte posted might actually make sense 😉
…..SIM forensics as generally there is very little relevant stored on them.
Adam10541, you do realise you have just opened a can of worms, don't you son?
I suppose if the only point of interest to an examiner is recovering user content and limiting mobile forensics to nothing more than 'plug-n-play' then the examiner will see little of importance in the (U)SIM or anything else, for that matter.
I have three questions for you based upon your comment 'little relevant', and hoping you can provide the answers by tomorrow, please?
1. Below is the link to 3GPP standards for USIM. Are you saying that you do not need these standards for identification of relevant information stored in (U)SIM?
http//
2. Below is the currently listing from UST (USIM Service Table) 3GPP 31.102. There are at minimum 1,900 pieces of examination, investigatory leads and evidential pieces of information that can be obtained from these UST entries. To be fair you said you had done little with SIM forensics, so perhaps you can provide just 25 examination, investigatory leads and evidence from your choice of services you wish to select from the services listed below?
Service n°1 Local Phone Book
Service n°2 Fixed Dialling Numbers (FDN)
Service n°3 Extension 2
Service n°4 Service Dialling Numbers (SDN)
Service n°5 Extension3
Service n°6 Barred Dialling Numbers (BDN)
Service n°7 Extension4
Service n°8 Outgoing Call Information (OCI and OCT)
Service n°9 Incoming Call Information (ICI and ICT)
Service n°10 Short Message Storage (SMS)
Service n°11 Short Message Status Reports (SMSR)
Service n°12 Short Message Service Parameters (SMSP)
Service n°13 Advice of Charge (AoC)
Service n°14 Capability Configuration Parameters 2 (CCP2)
Service n°15 Cell Broadcast Message Identifier
Service n°16 Cell Broadcast Message Identifier Ranges
Service n°17 Group Identifier Level 1
Service n°18 Group Identifier Level 2
Service n°19 Service Provider Name
Service n°20 User controlled PLMN selector with Access Technology
Service n°21 MSISDN
Service n°22 Image (IMG)
Service n°23 Support of Localised Service Areas (SoLSA)
Service n°24 Enhanced Multi Level Precedence and Pre emption Service
Service n°25 Automatic Answer for eMLPP
Service n°26 RFU
Service n°27 GSM Access
Service n°28 Data download via SMS-PP
Service n°29 Data download via SMS CB
Service n°30 Call Control by USIM
Service n°31 MO-SMS Control by USIM
Service n°32 RUN AT COMMAND command
Service n°33 shall be set to '1'
Service n°34 Enabled Services Table
Service n°35 APN Control List (ACL)
Service n°36 Depersonalisation Control Keys
Service n°37 Co-operative Network List
Service n°38 GSM security context
Service n°39 CPBCCH Information
Service n°40 Investigation Scan
Service n°41 MexE
Service n°42 Operator controlled PLMN selector with Access Technology
Service n°43 HPLMN selector with Access Technology
Service n°44 Extension 5
Service n°45 PLMN Network Name
Service n°46 Operator PLMN List
Service n°47 Mailbox Dialling Numbers
Service n°48 Message Waiting Indication Status
Service n°49 Call Forwarding Indication Status
Service n°50 Reserved and shall be ignored
Service n°51 Service Provider Display Information
Service n°52 Multimedia Messaging Service (MMS)
Service n°53 Extension 8
Service n°54 Call control on GPRS by USIM
Service n°55 MMS User Connectivity Parameters
Service n°56 Network's indication of alerting in the MS (NIA)
Service n°57 VGCS Group Identifier List (EFVGCS and EFVGCSS)
Service n°58 VBS Group Identifier List (EFVBS and EFVBSS)
Service n°59 Pseudonym
Service n°60 User Controlled PLMN selector for I-WLAN access
Service n°61 Operator Controlled PLMN selector for I-WLAN access
Service n°62 User controlled WSID list
Service n°63 Operator controlled WSID list
Service n°64 VGCS security
Service n°65 VBS security
Service n°66 WLAN Reauthentication Identity
Service n°67 Multimedia Messages Storage
Service n°68 Generic Bootstrapping Architecture (GBA)
Service n°69 MBMS security
Service n°70 Data download via USSD and USSD application mode
Service n°71 Equivalent HPLMN
Service n°72 Additional TERMINAL PROFILE after UICC activation
Service n°73 Equivalent HPLMN Presentation Indication
Service n°74 Last RPLMN Selection Indication
Service n°75 OMA BCAST Smart Card Profile
Service n°76 GBA-based Local Key Establishment Mechanism
Service n°77 Terminal Applications
Service n°78 Service Provider Name Icon
Service n°79 PLMN Network Name Icon
Service n°80 Connectivity Parameters for USIM IP connections
Service n°81 Home I-WLAN Specific Identifier List
Service n°82 I-WLAN Equivalent HPLMN Presentation Indication
Service n°83 I-WLAN HPLMN Priority Indication
Service n°84 I-WLAN Last Registered PLMN
Service n°85 EPS Mobility Management Information
Service n°86 Allowed CSG Lists and corresponding indications
Service n°87 Call control on EPS PDN connection by USIM
Service n°88 HPLMN Direct Access
Service n°89 eCall Data
Service n°90 Operator CSG Lists and corresponding indications
Service n°91 Support for SM-over-IP
Service n°92 Support of CSG Display Control
Service n°93 Communication Control for IMS by USIM
Service n°94 Extended Terminal Applications
Service n°95 Support of UICC access to IMS
Service n°96 Non-Access Stratum configuration by USIM
Service n°97 PWS configuration by USIM
3. An officer approaches you as the expert to investigate comminucations on an iPhone. There is known comms that have taken place but the twist is the comms at the distance end are being received by a Satellite phone. The user of the SatPhone is known to be trafficking in young children snatched from parents whilst on holiday. Your job is to provide evidence to help the police officer regarding which elementary files in the USIM would be used to permit mobile network usage (home and roaming) and any network artefacts that maybe connected to Satellite comms? To help you, a link below leads you to a piece of equipment that links iPhone to satellite
http//
Answers by tomorrow, please?
so many words….. )
Rather than trying to first read, then try and answer in a way that would make you happy I will offer this.
I have examined several thousand phones whilst I was a Police officer in Australia, and I can count on one hand the times the information on the (U)SIM was relevant, and one time when the last tower connected to was needed.
Real life experience tells me that the SIM is rarely relevant, not theories or conjecture. My analysis work on mobile phones was needs driven.
If in your work environment you are finding the SIM information highly relevant then you of course will have different needs and experiences to my own.
Perhaps I should have prefaced my post with "in my experience" but that has always seemed a bit silly when I see it written.
fight, fight, fight, twisted FIGHT!
mrgreen
I raised my observations to you because of what you were saying about your own understanding, which suggested mixed messages
I've not had to do much on SIM forensics…
So with little exposure you then make the qualification to suggest to someone else not to both
…generally there is very little relevant stored on them.
You then observe in your second post you have loads of experience compounding further the mixed messages you raised in your first post
I have examined several thousand phones
—-
Real life experience tells me that the SIM is rarely relevant, not theories or conjecture. My analysis work on mobile phones was needs driven.
So where did you get the IMSI, ADN, ICCID etc etc? Or are these not real life just theories or conjecture, too?
Perhaps I should have prefaced my post with "in my experience" but that has always seemed a bit silly when I see it written.
I do understand and respect that.
so many words….. )
Yes I know, but if you want to get involved in mobile phone forensics and evidence you have to read the standards no matter how uncomfortable it is, otherwise how do you know what is relevant and what is not?
To help out, can you show why these are not relevant
1. Have a look at the standards given in the 3GPP link above. Why would the physical, logical, formatting, EF identification, datasets etc information not assist you?
2. UST (USIM Service Table) 3GPP 31.102. There are at minimum 1,900 pieces of examination, investigatory leads and evidential pieces of information that can be obtained from these UST entries. Identify just 25 pieces of examination, investigatory leads and evidence from your choice of services you wish to select from the services listed above?
3. What USIM EFs would be updated when the iPhone switches from mobile network to satellite communications?
You know what, I just can't be bothered.
I had a big long post up here but just deleted it. You have more mobile/sim knowledge than me so you win.
However nothing changes the fact that in my experience there has rarely been anything of interest on a SIM card. Accept that, breath and move on, you take yourself far too seriously )
It always brightens up my day when reading these posts.
In my own experience, I always sit back when I cannot add any value.
Understanding and provide accurate/factual responses to an initial request is a foundation to a solid forensics career.
Lets see,
Several thousand phones to exam in the Force seems a lot, 1 per day (2 if you are lucky and never had any issues), make 365 per year, say your several thousand is 3 thousand, otherwise it would be a couple thousand right? This takes you 8 years without any holidays, a hard working force.
Going back 8 years, I would assume you must have a need to analyze SIM/USIM for private data? Maybe Trewmte can add what Private data is?
This post is an exception. oops
In my own experience, I always sit back when I cannot add any value.
Understanding and provide accurate/factual responses to an initial request is a foundation to a solid forensics career.
I did offer a very small contribution which was both accurate and factual, a simple outline of one of the differences between SIM and USIM which I felt might be helpful. I thought that the picture that was posted contained plenty of information, but was fairly technical in nature and didn't really answer the question the OP posted.
And I'm not sure what tool you use but if you can only download 1 or 2 phones per day then I would consider upgrading. 1 -2 phones per hour would be more realistic time frame for a basic download presuming things go smoothly.
have zero interest in becoming involved in an argument or e-fight, I'm far too old for that and I'm guessing trewmte is as well (his blog credits him with over 20 years experience so I'm guessing he's even older than me), so I will farewell this thread and hopefully someone can drag it back on topic to help the OP with some advice.




