Leveraging DKIM In Email Forensics
by Arman Gungor
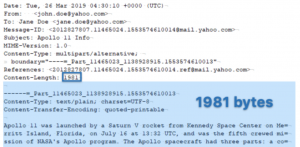
My last article was about using the Content-Length header field in email forensics. While the Content-Length header is very useful, it has a couple of major shortcomings:
Most email messages do not have the Content-Length header field… Read more