Import Microsoft Outlook Data Files Into Oxygen Forensic® Detective
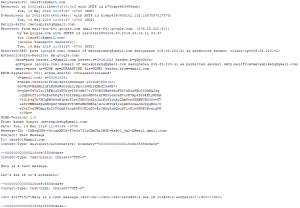
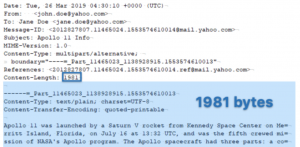
Email messages can be a goldmine of digital evidence both in criminal and corporate investigations. Oxygen Forensic® Detective enables email data extraction from mobile devices, computers, and from the cloud. Overall, utilizing various extraction methods, investigators can extract the following… Read more