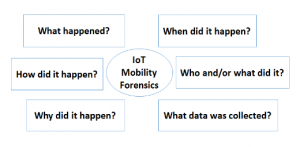
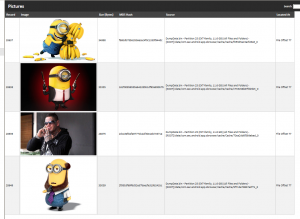
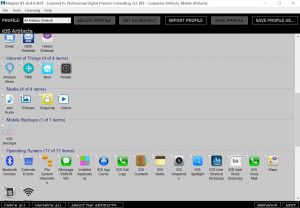
Remote Forensics Of Windows 10 Mobile Devices
by Oleg Afonin, Elcomsoft
Microsoft has developed Windows 10 as the one OS for all types of devices from servers to wearables. Desktops, laptops, two-in-ones, tablets and smartphones can (and do) run a version of Windows 10. There are countless