Reviewed by by Jonathan Krause, Forensic Control Ltd.
Advanced Live Forensics & RAM Analysis Training
Worcester University, UK, Oct 20th – 22nd 2009
Course run by Nick Furneaux, CSI Tech.
www.csitech.co.uk
Perhaps the biggest changes and advances in computer forensics over the last few years have come from the collection and subsequent analysis of volatile data from running systems. Look back just 3 years ago or so and you’ll see a profession where the widely accepted view was that if you were to find your target computer on, you’d pull the power. The turnaround in approach is such that to take that approach now could even be considered negligent; for by pulling the power before you’ve collected the volatile data you’re quite likely to be destroying a whole mass of incredibly useful data.One of the main instigators of this advance in computer forensics has been Nick Furneaux who’s been involved in the research, development and training of tools and methodologies in this new discipline of forensics. Nick has been at the forefront of changing the concept of what constitutes best practice and best evidence in the harvesting and examination of digital evidence. With this mind, and having met Nick on a couple of occasions previously where his enthusiasm and ability to successfully communicate complex ideas stood out, I had no hesitation whatsoever in booking myself on to his three-day Advanced Live Forensics & RAM Analysis Training course.
Taking time to browse through the course syllabus certainly whetted my appetite; the imaging of XP, Vista and Linux RAM, both locally and over the network; the extraction of GMail contacts and other data from RAM; the extraction of executables from memory dumps for malware analysis; the locating and extracting of any registry key; creating and scripting your own USB toolkits, and a lot more besides. Having told my clients I’d be away for 3 days I packed my bags and headed expectantly to Worcester.
On the first morning of the course after we entered the (rather-tired-looking) training room at Worcester University and following the usual introductions we received our goodies; a 8GB Corsair Survivor USB stick (very cool) pre-loaded with example images and the tools we were to use, a Helix 2.0 CD, a Helix Pro CD to play with whilst on the course and a printed – thankfully not PDF – 300 page manual. All good stuff, though I think the trainees would definitely benefit from a comprehensive index in the manual; during some of the later exercises I spent a fair amount of time flicking back and forth looking for that elusive command line that I knew I saw before.
It may come as a surprise to some to know that the Helix distributions are still being used on this course owing to e-fense’s somewhat uncertain future. Regardless of e-fense’s state, both Helix 2.0 and Helix Pro remain very solid tools, however free alternatives to do much the same are alternatively available – for example imaging RAM is now a feature of the popular FTK Imager and FTK Imager Lite.
The style of the course was a good combination of being both informal and very hands on with Nick introducing a topic then going through examples on the display (which were replicated in the manual) and then it would be our turn to run through the processes with Nick wandering around the class answering any questions and dealing with any problems. As you may expect from the course title some concepts and procedures were relatively complex, however this was eased by Nick introducing simpler concepts first and then building on these, enabling the understanding and use of the more complicated routines. Programming experience is not necessary, but this is certainly not a beginner’s course, and any prospective attendees should have a solid background in computer forensics techniques; as a very rough guide I would think around 3 years experience of technical forensic analysis would ensure that you’d get the most out of this course.
A little gripe of mine would be the location chosen for the course; while Worcester is a very pleasant small town, it doesn’t offer the visitor the best selection of hotels and while being quite close to London it’s unfortunately very poorly served by the rail network; direct trains take around 160 minutes and only run once every 2 hours. The University itself is not in the town centre and is a good 30-40 minute walk away. Of course most of this could be alleviated if you decide to drive, unlike myself! My gratitude goes to Mike Dickson of the Scottish Crime & Drug Enforcement Agency for giving me a lift in and out of town on the final day after I mentioned that I was walking in.
Nick has a very clear manner in explaining technical details in an understandable way, and has plenty of examples he uses from personal experience which definitely makes things more interesting and assists comprehension. Luckily for some (i.e. me!) he’s very patient at answering lots of questions, and in fact questions were encouraged which is always a good sign. We were instructed to bring our own laptops to use in the exercises which turned out to be more useful than I expected as although there were computers at the desk in the training room there were a couple of problems (no showstoppers, mind) in using the University’s computers. As touched on earlier, the training room we were in wasn’t the most modern but on the third and final day the class had to move to another room for some reason or other. Initially I thought ‘what a pain’, as all my tools/exercises had been installed on a desktop PC in the first room – however it only took me 10 minutes to transfer them to my USB stick and we did benefit from the move to a brighter and better equipped room, so no complaints there.
The excellent F-Response Field Kit Edition was used several times during the course to connect to remote machines, and then mount the target machine’s RAM as a physical disk on the local machine. With RAM appearing to your analysis machine as a physical disk, you can use various tools to parse data from it. For example you can aim Craig Wilson’s HstEx tool at the mounted RAM which enables the extraction of any internet history records, or by using Jad Software’s Internet Evidence Finder the extraction of Facebook, Yahoo and Gmail is possible. If finding something in the subject’s internet history or chat programs is important to your investigation yet you find nothing in caches or unallocated space it’s entirely possible the data you need may exist in RAM and this course shows you just how easy and quick this is to do.
Another very useful item was Nick going though how to put together your choice of applications and trusted binaries to make a USB toolkit, then to automate the data collection process by using simple batch scripts – if you never tried this before then I’d recommend you should, not only is it extremely useful and simple to do, it’s quite an empowering exercise. The batch files examples we used allowed us to image RAM, to image a disk, to search a disk and retrieve data and to send the output to a Netcat listener. Using simple tools like Foremost and Strings, we were able to carve all sorts of files from RAM and to create a list of all text strings. The resultant list of text strings from RAM can then be used, amongst other things as part of a password attack dictionary when used by a tool such as the AccessData’s PRTK.
Apart from the F-Response product, a great thing about this course is that all the tools used in the class are freely available. From Python, to the Volatility Framework which works within it, to Sysinternals’ Process Monitor and Process Explorer, to FTK Imager Lite all the tools are out there and won’t cost you a penny. Volatility for those who aren’t aware is an excellent framework enabling investigation and carving of many elements from RAM. Volatility plug-ins are being released by a variety of people which bring further opportunities to obtain more useful artefacts from RAM. An example of one basic use of Volatility is its ability to extract all running processes, the process ID and when the process started, very similar to the PsList tool from the PsTools suite from Mark Russinovich. Using the output of something even this simple can give an examiner a quick indication if suspicious services may be running and whether further investigation of a breach or malware attack is worthwhile.
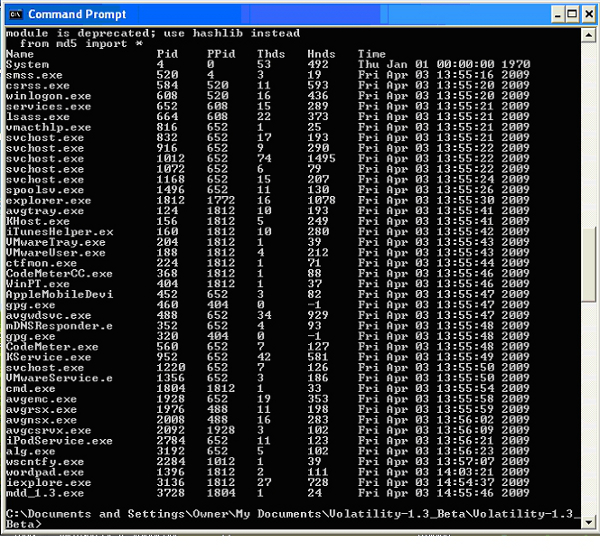
The output from a Volatility command showing running processes on a target machine
Highlighted on this course and unbeknown to many is that the entire registry is loaded into RAM at boot up. By using a series of relatively simple Volatility commands Nick illustrated how a user’s SAM file could be extracted from RAM which would then allow the analyst to use tools such as Cain & Able, SAMInside and Ophcrack against it in order to attempt to crack the password.
Of course the SAM files can be obtained from a hard drive image, but the point here and throughout the course is that if you need to quickly triage a machine without causing too much disruption, a huge amount of useful information can be retrieved from a machine’s RAM. With a typical size of 4GB for RAM against 500GB for a hard disk, the implications for imaging time are clear to see.
Nick illustrated the use of some of the most interesting uses of Volatility on the course’s final day. Using a plug-in called cryptoscan enabled the searching for Truecrypt passphrases. There are also Volatility plug-ins and parsers to extract data from Skype and information from the use of GMail and the new Yahoo mail both of which cache very little to the disk. Using these tools I imaged my partner’s RAM over the training room LAN and parsed it for GMail information. Lo and behold, I was able to view all my partner’s contact details and the subject line and the initial part of some of his emails including times and dates. Pretty amazing stuff. I’ve provided a screen shot below of some of the results after doing the same GMail ‘magic’ on an image of Nick’s RAM:
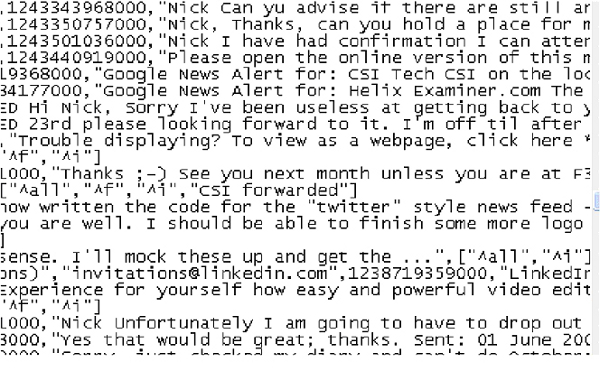
The results of running a Gmail parser though Volatility on a RAM image
Some of us had more success running these final exercises than others, which for me underlines the point that RAM analysis by its very nature is something of a hit and miss affair. Regardless of this I absolutely believe that analysis of volatile data should become part of standard forensic analysis procedures. There was so much on this course which was fascinating and useful of which this review only covers some selected parts. A lot of what was taught would be revelatory to those of us who’ve been used to more ‘traditional’, non-volatile data analysis. Personally I was already confident of my capabilities as a computer forensic analyst, but after finishing this course I feel that a whole new world of opportunity in computer forensic analysis lies ahead; it really was that useful.
Costs and further information
Law Enforcement £1150 + VAT incl. disk and USB key
£1350 + VAT incl. above and F-Response Field edition
Private £1300 + VAT incl. disk and USB key
£1500 + VAT incl. above and F-Response Field edition:
Web: www.csitech.co.uk
This review can be discussed here.
Review written by Jonathan Krause of Forensic Control.
Based in central London but working throughout the United Kingdom and beyond, Forensic Control provides computer forensics services to the legal and accountancy professions, corporate clients and private individuals.
Web: www.forensiccontrol.com
Email: info@forensiccontrol.com
Telephone: +44 (0)207 19 333 24
Tel: +44 (0)845 3884697