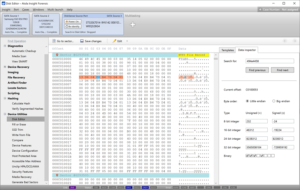
Atola Makes Byte-Level Analysis Easier In Insight Forensic 5.4
Atola Technology introduces a fully revamped Disk editor module for convenient in-depth evidence analysis in a new software update for Atola Insight Forensic, a fast forensic imaging system with the capacity to run 3 simultaneous imaging sessions and work with… Read more