Jordan: Hello everyone, Jordan Portfleet here with the Oxygen Forensic training team. Today’s topic is going to be KeyDiver. Now, what is KeyDiver, you ask? Well, the time has come to introduce our new brute force module, the Oxygen Forensic KeyDiver. This is available to you at no additional cost inside of Oxygen Forensic Detective.
So, this module is actually designed to find passwords to decrypt partitions with BitLocker protection, partitions protected with FileVault 2, encrypted zip files, encrypted Apple Notes, passcode-locked Telegram Desktop app, and with Oxygen Forensic KeyDiver, you can create hash cracking attacks in a format supported by the Hashcat utility using various dictionaries and masks. You can run sequential attacks until the password is successfully guessed. You can also export the obtained password to decrypt the original data or use it for other purposes.
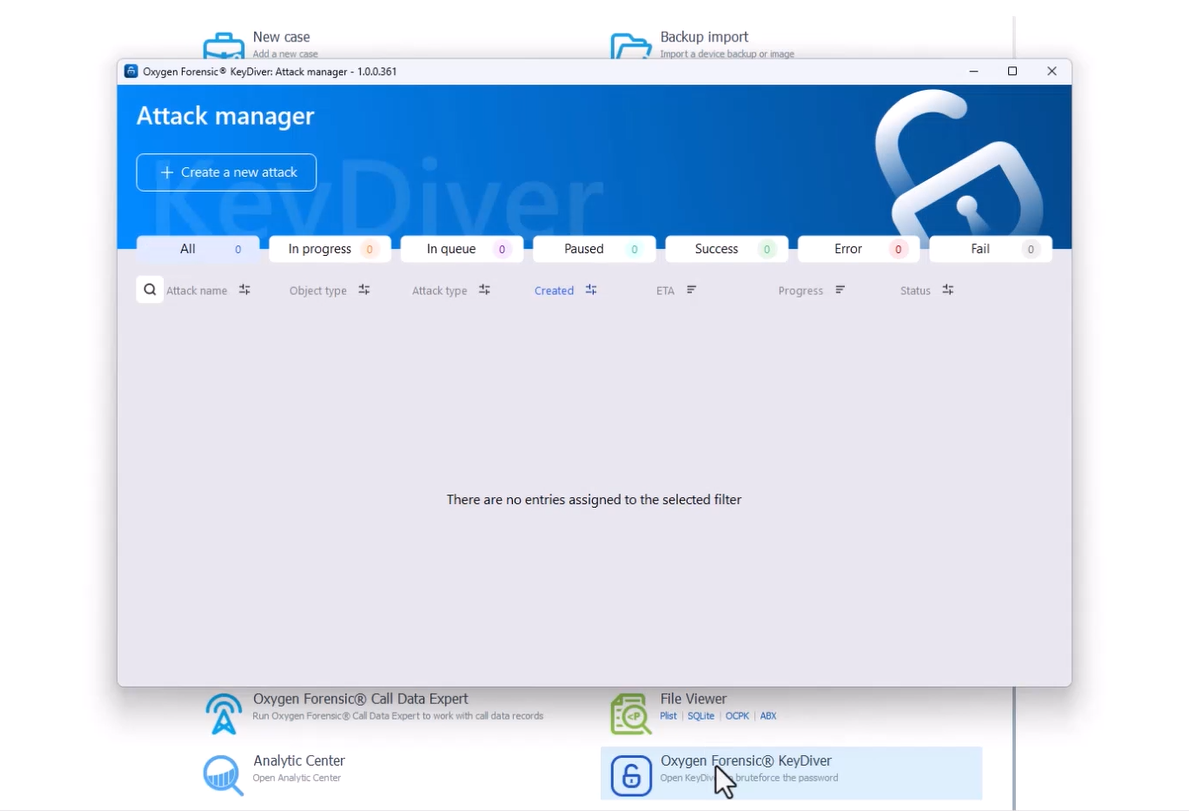
To access Oxygen Forensic KeyDiver, we can simply go to the homepage and Oxygen Forensics Detective, and it’s going to be listed under “Tools”. Now that I’m inside of the attack manager, I can see there are no entries assigned to the selected filter. I can also select the tabs at the top and look at “All”, “In progress”, “In queue”, “Paused”, “Success”, “Error”, and “Fail”. To create a new attack, all I need to do is click the “Create a new attack” button at the top.
Now we have a message here, “To create a new attack, upload an attack settings file (.json) or select a supported object type from the list.” So if I wanted to load, I could go ahead and just grab my .json file, and now I want to take a look at my list.
Different attack types here; type number one is going to be Encrypted ZIP file. “An archive in .zip format containing compressed files. When creating an archive, the user can set a password. This password can be bruteforced by extracting the encryption information from the archive.”
Next we have 7-zip encryption. “When creating an archive, the user can set a password. This password can be bruteforced by extracting the encryption information from the archive.”
Next, I have iTunes backup. “To protect the iTunes backup, the user can use a password and encryption. This password can be matched by extracting the encryption information of the backup. You can load the manifest.plist from your iTunes backup to automatically calculate the hash or paste the hash manually.”
Next we have Apple Notes Encryption. “Apple secret notes Brute Force. Secret notes are protected with end-to-end encryption using a user-generated password that makes it impossible to view the notes on iOS devices, iPadOS, macOS, and the iCloud website. Each iCloud account can have a different password.”
FileVault 2 volume encryption. “A partition of a disk or an entire disk can be protected using FileVault encryption. Data decryption requires a password set by the user when encryption was enabled. This password can be guessed using the encryption information extracted from the disk.”
Next we have BitLocker volume encryption. “A partition of a drive or an entire drive can be protected using BitLocker encryption. Data decryption requires a password set by the user when the encryption was enabled. If the disk has not been additionally protected with TPM, it is possible to guess the password using the encryption information extracted from the disk.”
Last but not least, we have Telegram Desktop encryption. “Telegram Passcode Lock brute force. This Passcode lock is local and used to protect a specific device, not an account. If a user uses a Telegram account on different devices, he/she needs to set up an individual code password on each of them.”
Now that we’ve seen some of our attack options, let’s take a closer look at creating a new attack. Like all Oxygen Forensics products, we do supply or provide a user-friendly interface to export the file with all the necessary information already stored in it. Once you have that file, you can transfer it to another PC, you can transfer it to another user, or you can run another password-cracking attack outside the PC where the disk image is stored and processed. All you have to do is click the “Import” button in the “Create new attack window” to upload the .json file in a key driver. Then you can proceed to specify the method of attack for the imported hash.
So, now we know all we have to do is either grab our .json file, or we can select from a list. One thing I did want to point out though, is if we do know the hash, what we have to do is specify the hash in hashcat format. So, you can see an example of exactly what that looks like in the gray bar.
Now, let’s take a look at how we can use Oxygen Forensic KeyScout to leverage KeyDiver. What I did was I went ahead and set up BitLocker encryption on my USB Drive (D:) here. Now what I’m going to do is I’m going to go to Oxygen
Forensic KeyScout and I want to acquire the external drive. Now I have my KeyScout open, I’m going to go to “New search” and I’m going to select “Drive”. Now all I have to do is point to the drive that I want to select and I’m going to select my USB flash disk.
Now I want to make sure I’m choosing the right partition here. I can see I have a BitLocker container and I need to enter the password. Now when I just double-click on that particular partition, I have this Decryption BitLocker. I have a couple different options here. If I know the password, I can put the password in. I can also start an attack or export my attack. Now we are in our attack window.
There are a couple of other things that I can do here before we get into the specific type of methods. I can grab a .json file and the hash for that encrypted BitLocker. If I just close this out, again, I could choose to decrypt if I wanted to. I’m going to select “Export attack”. I’m just going to go ahead and create a new folder. I’ll just call this folder “Bit Locker Webinar”. And that is where I’m going to be saving my .json file. You can see right there that .json.
So, I could either grab that .json file now and pull it into KeyDiver just by hitting “Load”. I could go in and grab the .json. Or I can grab the hash and because this is going to be an encrypted BitLocker what I’m going to do is select from “List”, go to my “BitLocker” option, And I’ll grab the hash.
So now what I’m going to do is just select start attack. And before we get into “Mask”, “Dictionary” and “Extraction-based dictionary”, we are going to take a look at how to grab the .json file and how to grab the hash. So, I’m going to open up my Oxygen Forensic KeyDiver, I could select “Create a new attack”. So I could load that .json that we just saved to our new folder, I could load that, or I could select from “List”, and I want to go into my .json file now, and I want to grab the hash that’s in there. So I’m just going to open up my .json file with Notepad, and now I can see I have my hash at the very top of my screen. I’m just going to copy that and paste it into the little gray bar, where we have to list our hash in the hashcap format. Get rid of my windows here. And now I can just right-click and paste and select “Next”.
Now I’m back in my BitLocker attack window. Now that we’re in our attack window, we have a couple of different attack methods that we can choose from. Method number one is a mask attack. So this is going to try to guess the target password by generating all possible character combinations of a specified length that matches a predefined pattern.
Method number two is going to be a dictionary attack. This uses a dictionary file that contains a pre-selected list of passwords, arranged one per line. Each password from the file is tested sequentially.
If a user is going to select the mask attack method, they have two different options. So they can set attack parameters or set a custom mask rule. If going with option one, the user should specify the number of characters and choose the language and character set that should be used. The password length is going to be anywhere between 4 and 60 characters, and if the same number is assigned to both from and to parameters, only passwords of the specified length will be generated.
Here we can see some of our parameters for mask attack, such as the character count from and to. We can specify the language we want, select character sets, so I could choose a symbol character set, I could choose custom variant, I could choose between lowercase symbols, uppercase, as well as numbers.
If a user wants to select option two for the mask attack, it’s going to be the custom mask rule. They can create their own rules for just like it says, a custom mask attack. In order to do that though, they must set a mask in the hashcat-supported format.
If the user chooses to run a dictionary attack instead of a mask attack, they can check their password candidates without any modifications using a dictionary file, or can apply additional password changes. To do this, all you need to do is hover over the dropdown in the dictionary field. The selected dictionary will be marked with a tick and will appear in the field to the right. The user adds their custom dictionary. After selecting the dictionary, the user can set these additional parameters. So we have “Characters case”, “Prefix”, “Suffix”, “Characters order” and “Characters skip”.
Now we can take a look at these system settings. This is where a user can set a temperature threshold to stop an attack. They can also choose one or more video cards. There are four different efficiency modes: “Low”, “Average”, “High”, and “Maximum” that the user can choose from.
Like many of the Oxygen Forensic tools, the system settings are going to be based on preference. So if you choose, say, maximum efficiency, that’s going to provide you with the best hash rate and maximize your hardware utilization, but it can also lead to higher temperatures and high power consumption. So KeyDiver does monitor the GPU temperature, and if the temperature threshold is higher than what you had set, the attack will stop, or KeyDiver will stop the attack. And this is just to prevent the GPU from becoming damaged.
So now we want to start our attack. As soon as you have selected your attack settings and at least one GPU, all you need to do now is select “Start”. You can only run one attack at a time and the attack will be “in progress” status. You can also add the current attack or new attack to a queue. They’ll be processed automatically and the next attack will start as soon as your previous attack is finished. Once you start your attack, you can monitor your progress in a separate window. This separate window is the attack manager window and this is where a user can view all ongoing, finished, paused, and queued attacks, manage them, and sort them by various parameters.
So when managing an attack, here are the following statuses. “In progress” means the attack is currently running. “In queue” means attacks that will be launched automatically once the current task is finished. “Paused”: attacks that were paused by the user. These attacks do not change their status automatically and should be resumed manually. “Success” means attacks that have finished with the password guest successfully. “Error” means attacks that encountered an error during their execution. User action is usually required before an attack can be resumed. “Not guessed” means attacks that have tried all the passwords possible for the selected attack method, but none of the password candidates match the hash.
So if a user selects the three dots at the right end of the line on the “In progress tab”, the user can view details of a particular attack, pause the attack, cue the attack, rename the attack, use the attack as a template, delete the attack. Once attacks are deleted, it is not possible to recover them.
Say you ran your attacks and the password was not guessed successfully. All you have to do now is run another attack and adjust your settings. You could try another dictionary or change your attack method. KeyDiver enables the user to utilize any existing attack as a template for a new attack. All you have to do is click that little “Template” button at the top of the screen.
If you were successful in your attack, the password is going to be displayed in the corresponding field. It can then be copied by clicking the corresponding icon in the password field. It is possible to save the password on the current device in .txt format using the “Save” button, or you can export the attack results in .json format using the “Export” button.
Let’s take another look at our BitLocker attack here. So I’m going to open up my KeyDiver, I’m going to go to “Create new attack”, and I’m just going to load up the .json file. You can see here my .json file. Go ahead and select “Open”, and now I can choose my method. So if I click on “Mask dictionary” or “Extraction-based dictionary”, I’m going to have a couple of different options below. So here I’m going to select “Mask”, pick “Parameters”, “Next”. For character set, I’m going to choose “Lowercase”, “Uppercase”, and “Numbers”. My character count can be anywhere from 4-60 characters. Now I’ll select “Next”, I’m going to change my hash rate and GPU load to “Maximum”, and I’m going to select my GPU. Now I can go ahead and select “Start”.
So with this mask that I had chosen, this mask attack, this is going to take a considerable amount of time. You’re going to see over on the right-hand side the amount of passwords that I need to attempt or that KeyDiver is going to attempt to use. So you’ll see here that it’s going to take something like two days. Yeah, two days it looks like.
So now what I want to do is I’m actually going to go ahead and pause this because we’re not going to wait two days to get the password for my BitLocker. So I’m going to go ahead and pause this extraction. Now, once I paused this attack, I can start taking a look at some other attack methods here.
Okay, so I can see that it’s on pause. If I wanted to export, all I’d have to do is hit that little button at the top of the screen to export and I can also delete, as well. So I can make a template, delete and export.
So now I’m going to explore some additional attack methods. I can see here that my attack has been paused by the attack manager. So now I’m just going to load up my .json file again, and I am going to take a look at some additional options here.
So let’s try a dictionary. So I just selected the most popular dictionary attack here. To try for some uppercase, I’m going to take a look at my other options: character order, fix, and we have the option to skip characters as well. So I’m going to choose not to mess with the prefix, suffix or character order, and I don’t really want to skip anything right now. So I’m just going to select “Next” and now I’m running this dictionary attack. This attack is going to take a considerable amount of time, but with some internet magic, we will get through this quickly.
So now I’m inside of my attack window. I can see the progress here currently at 0%. It should take about 20 minutes and 38 seconds. So we will speed this up a little bit and check in in just a moment.
So if I take a look back at my attack, I can see we’re at 98% and now I get a notification that my attack was not successful. So now all I have to do is just get back into my KeyDiver. I’m going to explore some additional attack options. So the first thing I’m going to do is load up my .json file. Now I can pick my parameters and let it take a little bit longer or I can use a custom variant. I also have the option when I select “method” and “Mask”, I can either pick parameters like we just saw, or through social engineering, I can obtain the password and write out the password myself. There’s absolutely nothing wrong with pausing an extraction and taking a guess on a password based on the information you’ve already gathered on a person.
Now I’ve done my social engineering, I have all this biographical data from this individual, I have street names, children’s names, likes and interests, job information, so I can start putting together a password list that I can try to run in KeyDiver. Once my attack is finished, I can see it was successful, I can see my password is listed out as “Password123”, I can also create a template, delete this attack or export this attack. I can save it out, as well.
Thank you everyone for joining me. Again, my name is Jordan Portfleet with the Oxygen Forensic training team. If you have any questions or concerns about anything that you’ve seen today, please reach out to us at Training@OxygenForensics.com. Thank you.