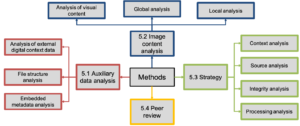
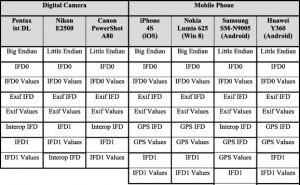
Amped Software’s Martino Jerian on Key Challenges and Opportunities for Video Evidence
Christa: Digital video is everywhere, but the complexities and challenges of using it as evidence in legal proceedings continue to advance. This week, Simon Biles and I talk to Martino Jerian, Founder and CEO of Amped Software. This is the… Read more