Word Forensic Analysis And Compound File Binary Format
by Arman Gungor
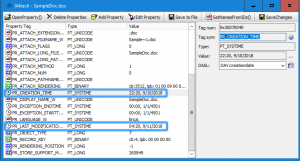
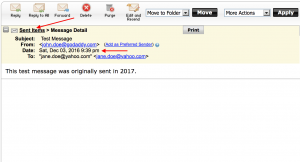
Microsoft Word forensic analysis is something digital forensic investigators do quite often for document authentication. Because of the great popularity of Microsoft Office, many important business documents such as contracts and memoranda are created using Word. When