Ali Hadi and Jessica Hyde on Accessible, Affordable Digital Forensics Training
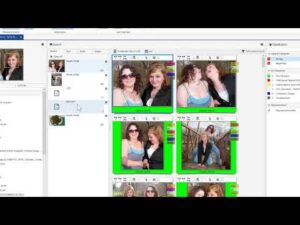
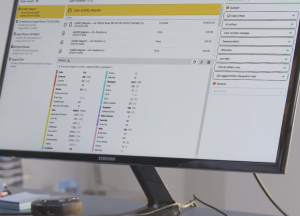
Christa: As cyber crimes and incidents rise, so does the need for well prepared, professional, digital forensics and incident response practitioners. However, while there’s no shortage of digital forensics training and education, whether it’s accessible enough and addresses enough of… Read more