Hey everyone, Trey Amick from Magnet Forensics here. Today we’re talking about Mac USB investigations, and what happens when we’ve been alerted that a USB has been inserted into an end point.
Different organisations handle USB policies differently. Some have alerting mechanisms in place for when USBs are detected, while others may encrypt the drive when it’s inserted into the end point. Other organisations may block the external drive from being mounted altogether, or may only allow specific external drives to be used by employees. Lastly, we have some organisations that tell staff it’s against policy to use USBs, but don’t take any additional steps to further protect the end point.
The different evidence [inaudible], but depending on the organisation you may be faced with identifying a USB that’s been inserted into a Mac in question for a possible data exfil. This investigation hinges on possible insider threats, where the associate may have attempted to copy files to a USB.
Here we have a MacBook Air image already processed in AXIOM. We’re going to go ahead and check the OS information. We can identify that for our report by going to the Artifacts view; we’ll navigate on down to Operating System, and we will look for ‘Operating System Information.’
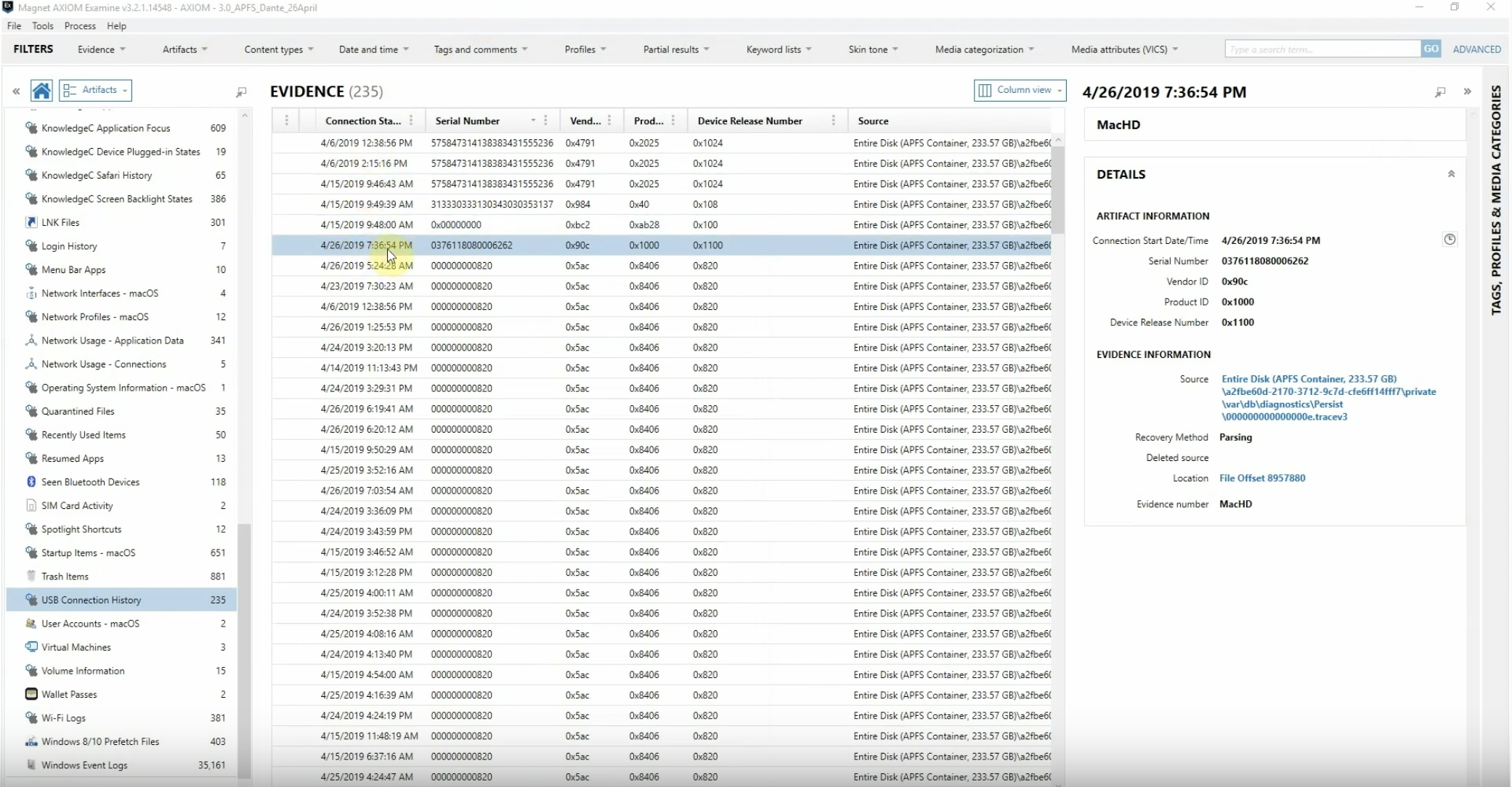
We can confirm that it’s 10.14.4 – I’m going to go ahead and add this as a tag. And since this case hinges on USB information, I’m actually going to keep scrolling down, and we’re going to start with the USB connection history, with 235 hits.
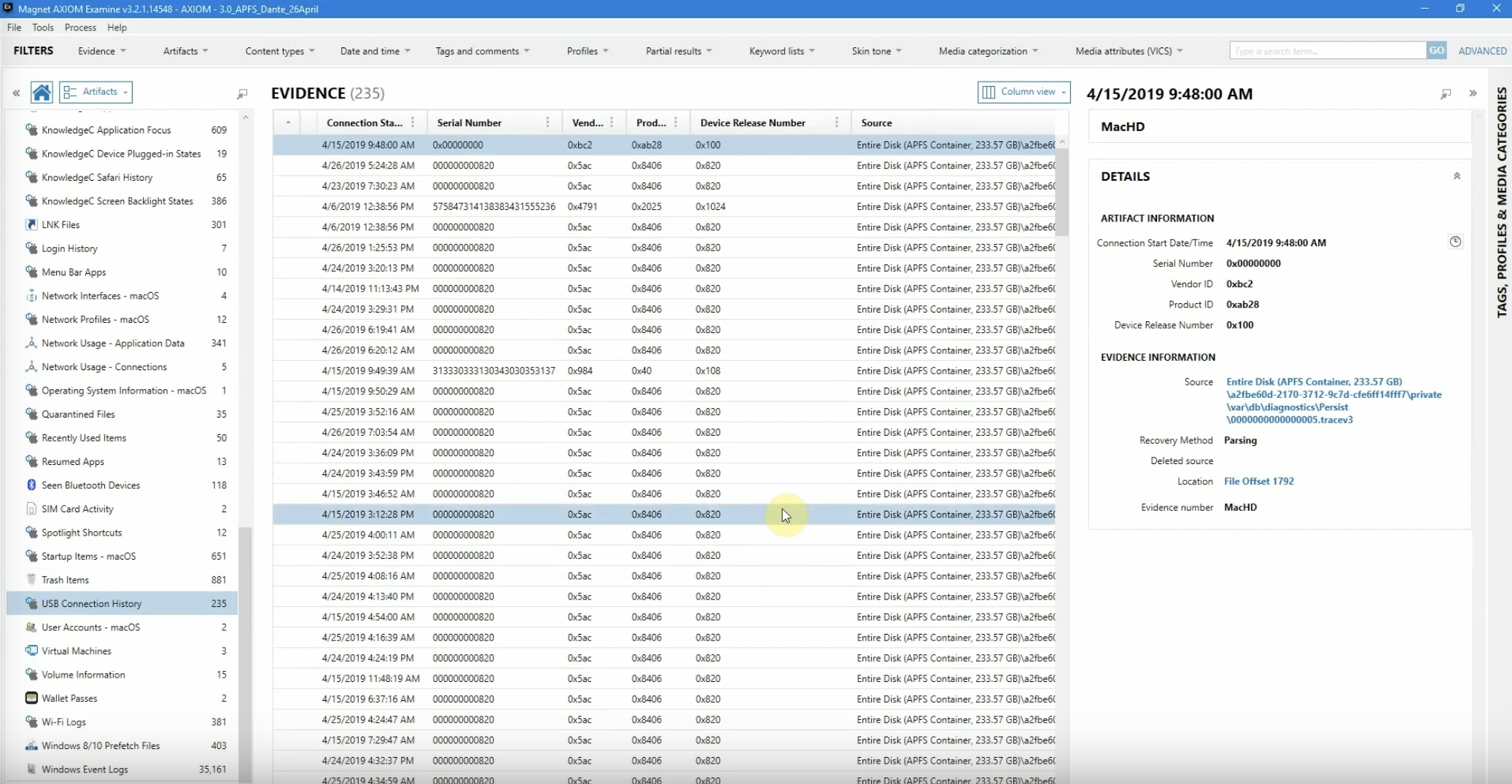
Now we can see all the different USB connections, and with there being 235 hits – which seems rather high – we’re going to actually try and identify some of this information.
And right off the bat, I’m seeing a lot of the same vendor ID codes here, with 0x5ac. So I want to be able to identify that.
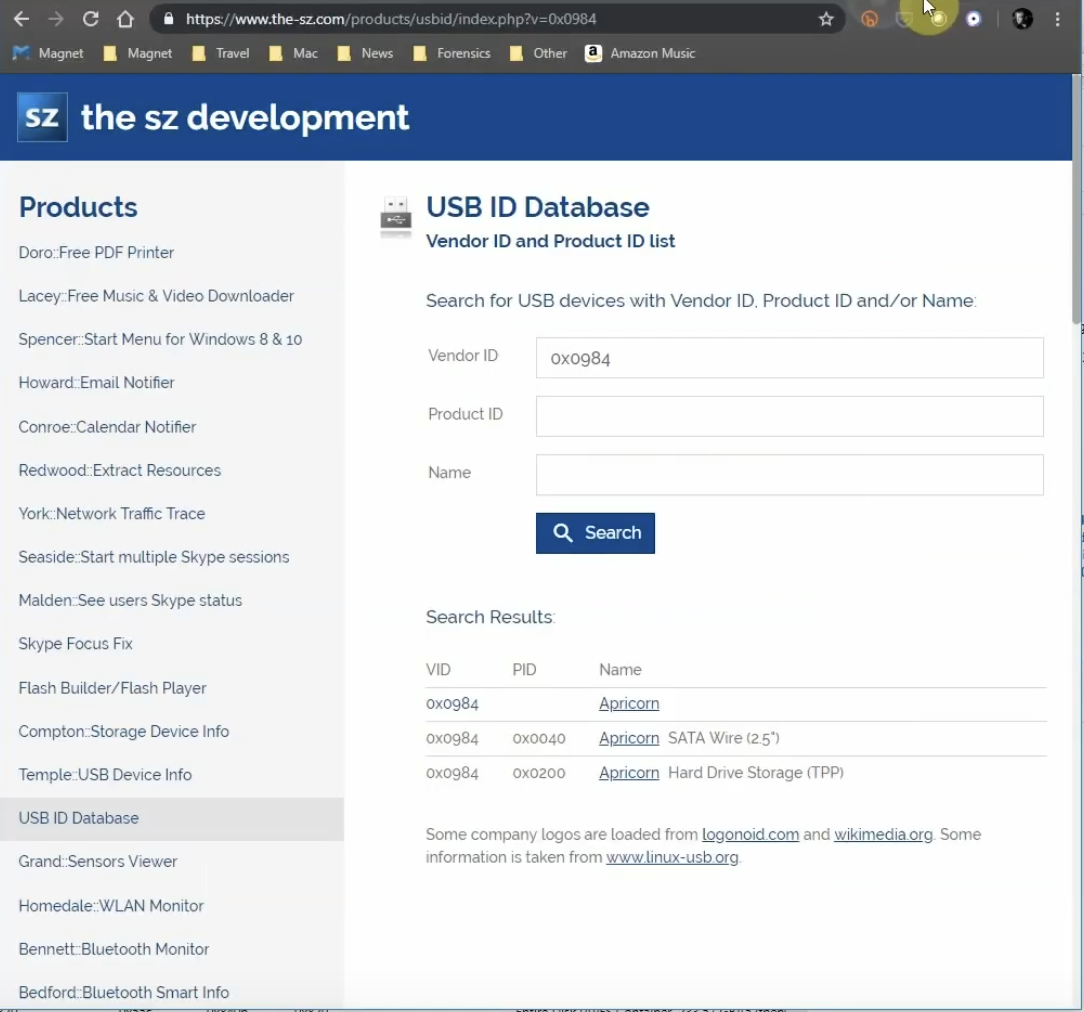
There’s nobody saying that we can’t use open-source intelligence gathering methods for our investigations, so I’m actually going to use a website to detect what that information is for that vendor information. And as we can see here, that is actually coming back to Apple, with a lot of their different product information pieces. So now we’ve confirmed that, we know that a lot of these hits are actually coming from Apple.
Let’s go ahead and we’re going to sort now on the serial number. We’re going to go ahead and get all of them grouped together. And now that we do that, we can start identifying what’s going on here.
So these first three: we’re getting the exact same serial number, vendor ID, product information. And this organisation in particular allows their employees to use one specific drive; and I’d be willing to bet that’s going to be this drive.
But just like we did before, we can check on that by using the same database and loading it in. And sure enough, we can see that it is a G-Tech Western Digital hard drive. So we can validate that they are using this drive on this machine, and that’s been approved by their organisation.
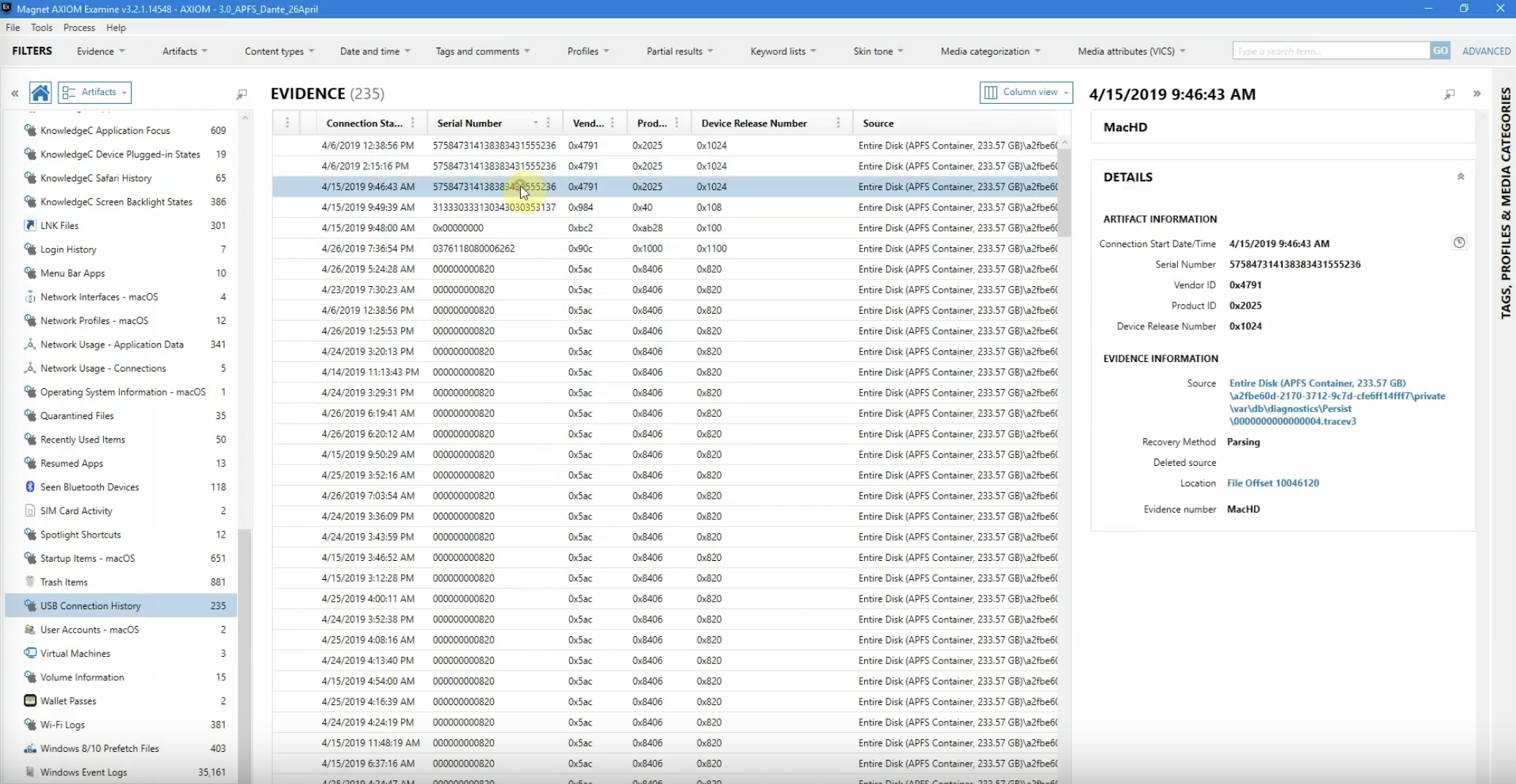
Next, though, as we look through the list here we see a couple of additional pieces to this USB history, and we can see that we’ve got a couple of identifiers here that… we need to identify what’s going on.
So the next one we’re going to take a look at is the 984 that’s on the list, 4/15. And when we go back to the same database, we can actually look and see that this is coming back to an Apricorn SATA wire, 2.5″. Now this tells me that this validates what was found in the IT system: that this machine was used and dropped off, and IT did support this machine on 4/15. And also we can identify this information using the same ID database. And then I further looked at it, and sure enough, there is the cable that the IT personnel use.
Lastly, on this list we can see that there’s one additional hit, and I want to go ahead and confirm that. And when I do, I can see that this is a Seagate drive, which is typically used for IT for this particular organisation.
So those I’m good with, and I understand what’s going on. But as we keep looking down now, we see we have this 0x90c, with a product ID of x1000. So one last time we’re going to actually look at this database, and when we do that we can see that this is coming back to a Silicon Motion, formerly of a different company, and that these are a USB disk and flash drives, looking at the same vendor information and product ID. So over here, let’s go ahead and dig a little bit further into what’s going on here.
This has happened on 4/26, approximately around the time when we got that alert. We do have a serial number, so that’s good. But let’s actually go over to the right-hand side of AXIOM now and build a quick relative time filter off this information.
So let’s go ahead and change this from two minutes, let’s actually say three minutes, and let’s keep our view in the current explorer, and let’s see everything that happened on this machine within three minutes before or after this USB being connected.
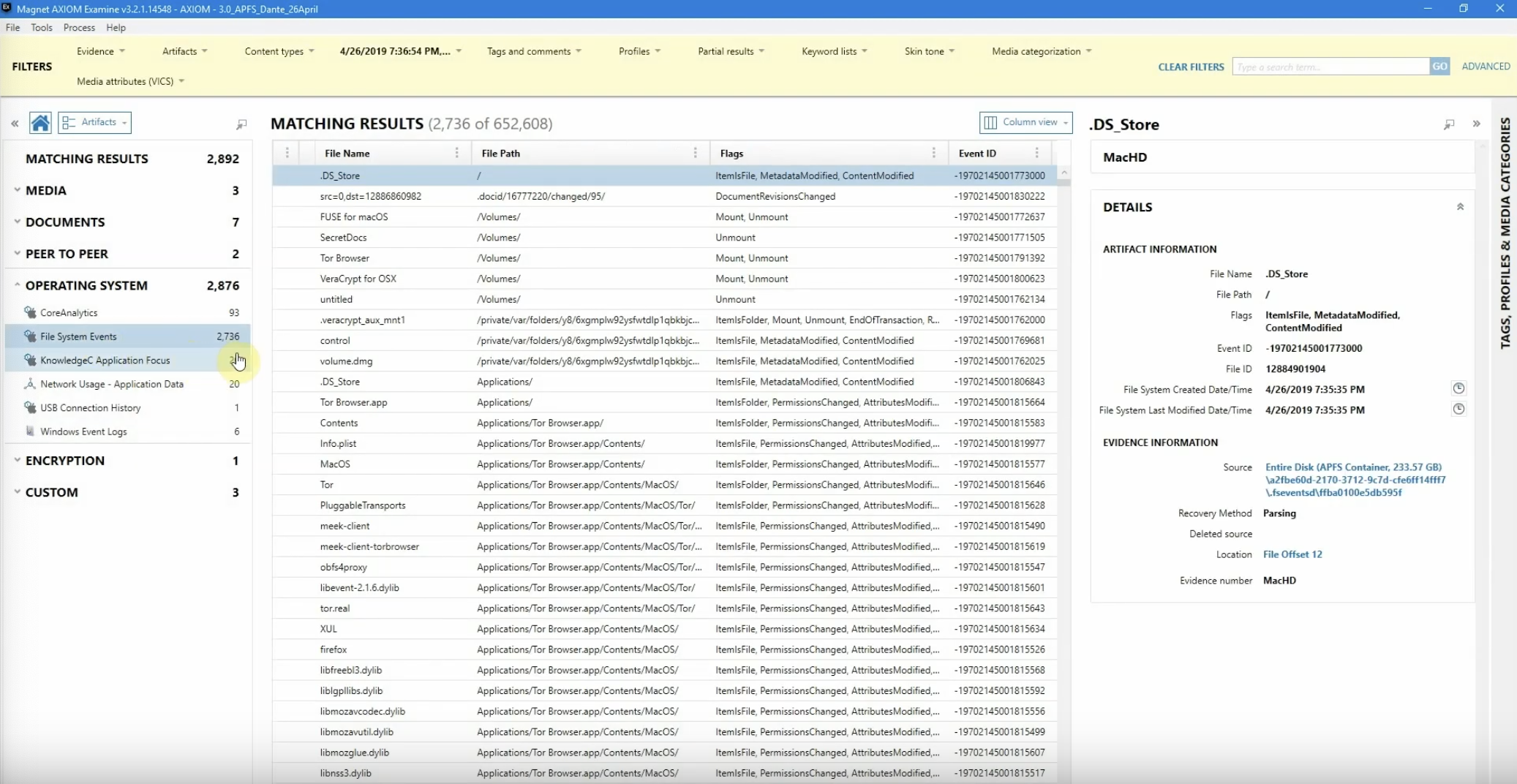
From here, we’ve got some more information we can look at. So let’s go ahead and hop over to file system events, or FS events.
From here there’s a couple of different options we can do. I’m actually going to build a quick filter off of flags, and I’m going to go ahead and say ‘Mount.’ So now we’re looking for mount points that are within three minutes before or after that original USB being connected.
And as I can see here, we’ve got several pieces here. Now typically, these are probably going to be coming from dmgs that are being mounted on the machine. Now we’ve identified an additional volume called ‘untitled,’ so let’s see if we can take that a little bit further and figure out what’s going on there.
So I’m actually going to go ahead and kill this first filter on the mount point; and next I’m actually going to go ahead and reset my relative time filter. We’re going to scroll right back down, though, and look under ‘Operating System’; and let’s look in one last place.
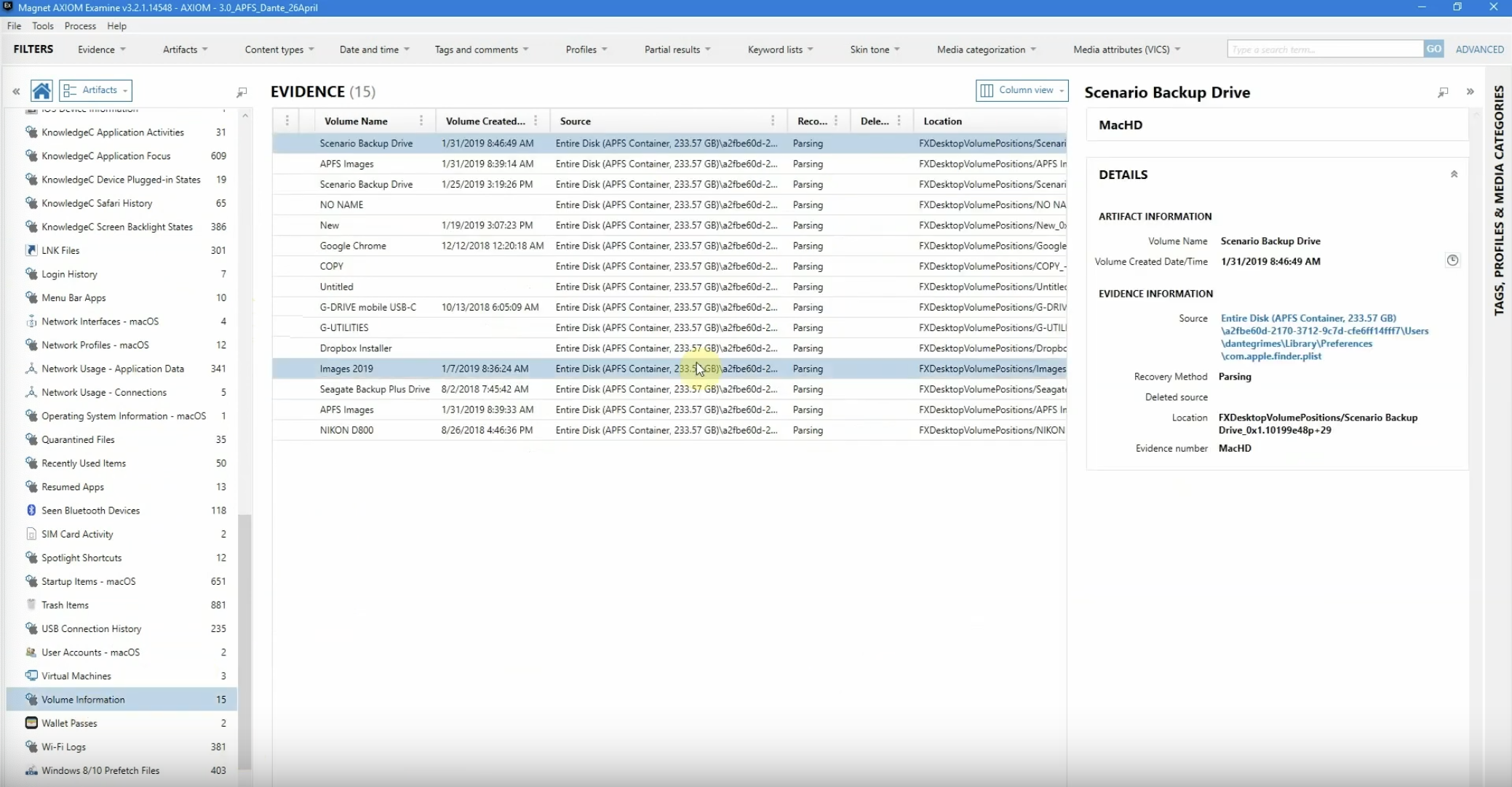
Let’s actually go on down, and we’ve already looked at USB connection information; we’ve already looked now at the file system events; let’s look at the volume information.
And from the volume information page, we can see that we’ve got a bunch of different volumes listed here, including the G-Drive that we’ve already identified as what they use, and are allowed to use, in this organisation. But sure enough, we do see this ‘Untitled’ volume one more time.
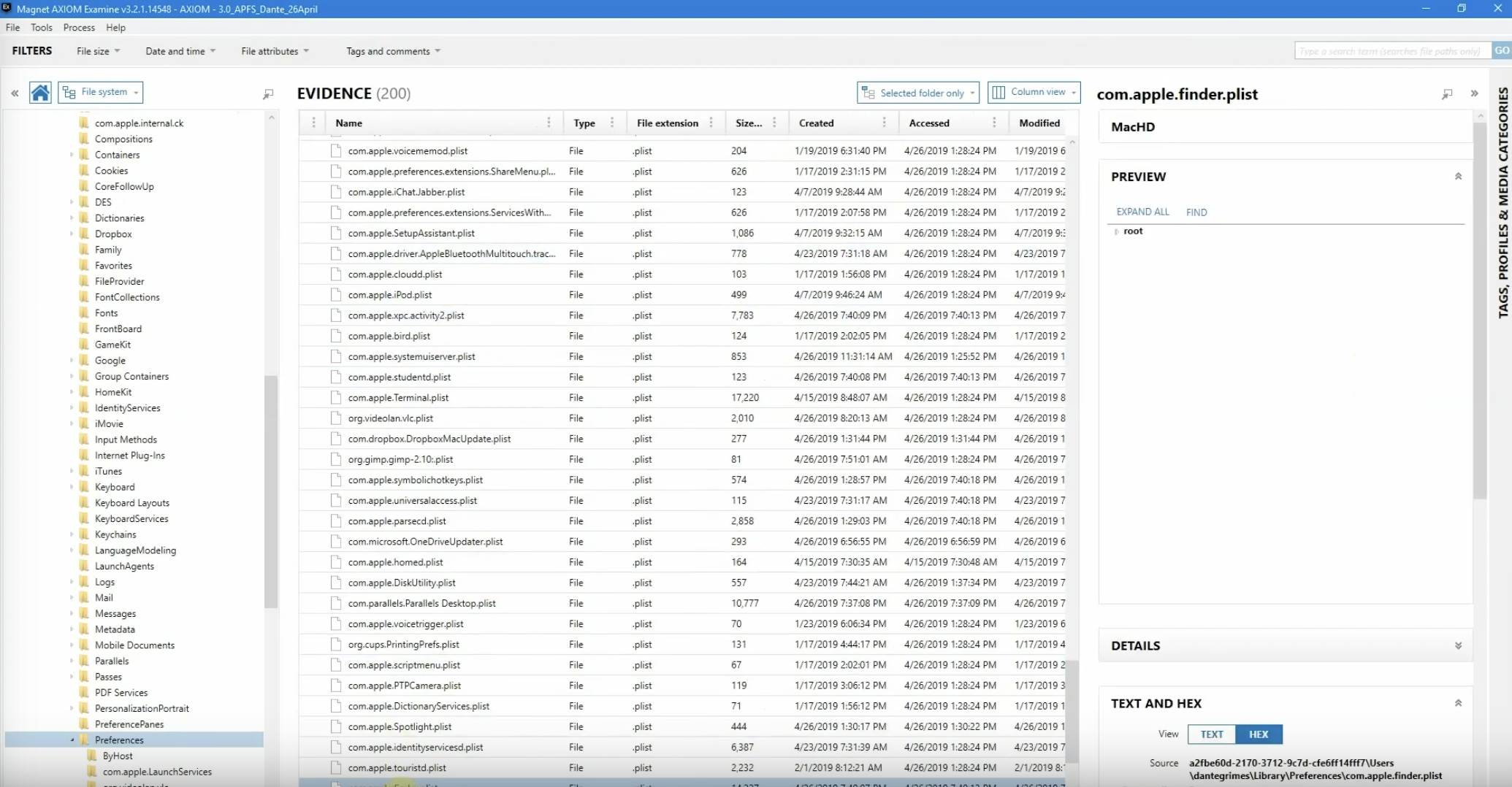
Now, one thing I love about AXIOM is that you really can dig in deep, and what I mean by that is we can actually go to the evidence information and click on the source link, which is going to take us to the Apple finder plist.
We’re going to let AXIOM load this in very quickly. We have that plist selected, so I’m going to let AXIOM expand that information out. And sure enough, right off the bat we can see recent move and copy destinations: we have a file, volumes, and titles. So this is telling me something was connected, we have the evidence to back that up; we are good to go that we have identified, more likely than not, what set off that original alert.
From here, we finish our report on this investigation, and then decide with investigation if we need to interview the associate and possibly locate that USB, to identify what was potentially placed on that.
Thanks for joining today, and as always if you have questions or would like to see additional features added on to AXIOM, please don’t hesitate to reach out. Thanks, have a great day.