With the latest version of TACTICAL v2.7.4, you can now acquire 152 types of digital evidence out of the box, adding almost 30 new types.
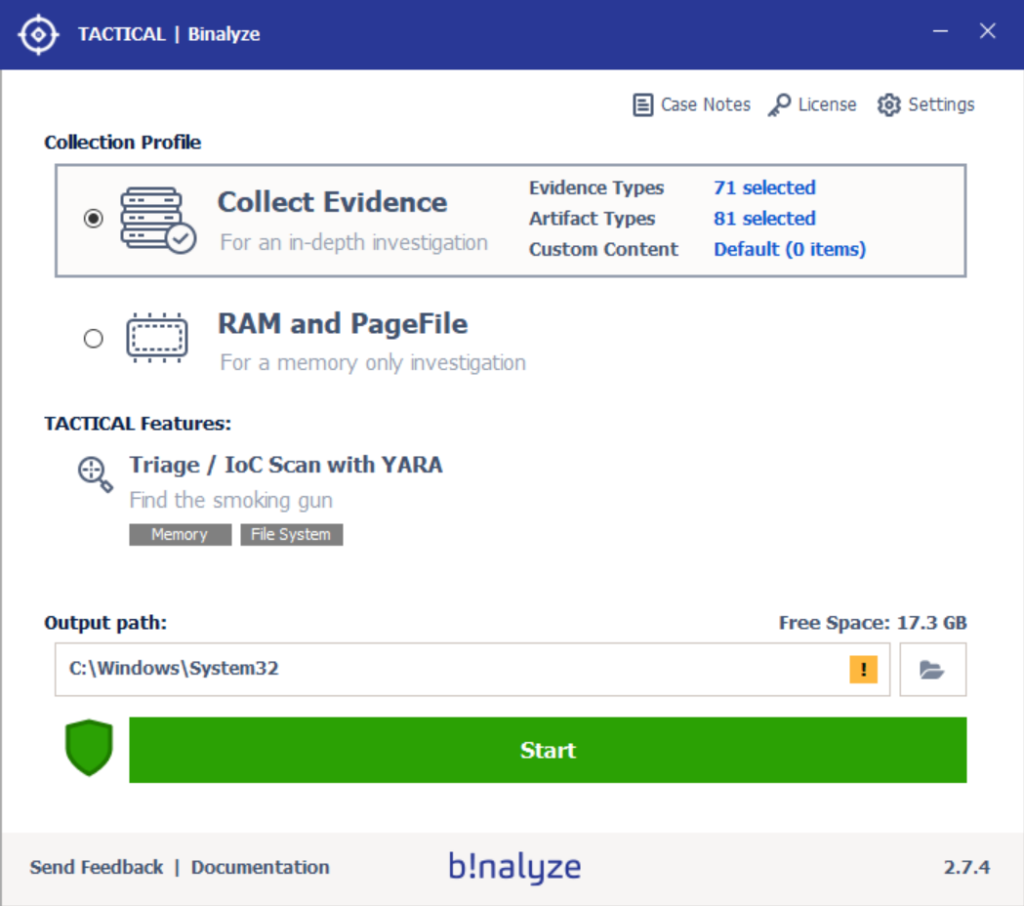
Binalyze TACTICAL was already the fastest and most comprehensive forensic evidence collector available. Now we have extended the quality and quantity of evidence types you collect with just one single click. Additionally, here are some other release highlights that will further enhance your digital forensics practices:
USB History
Whether you are investigating an endpoint in your corporate environment or you are part of a criminal investigation, you will need to investigate the USB device history of an endpoint. Knowing what USB devices were connected to the computer is the essential information and of great importance to a forensic examiner.
This feature is mostly provided by traditional desktop forensic solutions or specifically designed standalone solutions but in our case, with the newest version of TACTICAL, it is combined into the product so you get the full forensic image + USB storage history with one solution.
Added support for MFT as CSV collection from all drives
With this version of TACTICAL, you can collect all files from the MFT including the deleted ones. Previously TACTICAL was only collecting MFT from the system volume but with this version, it is collecting from all attached volumes. Besides enumerating deleted files in this version we further enrich the MFT by adding support for alternate data streams which is a feature of NTFS that may be abused by hackers to hide additional data that is not visible to the end-user. It is a great place to hide suspicious data and with this version, TACTICAL collects those fields as well.
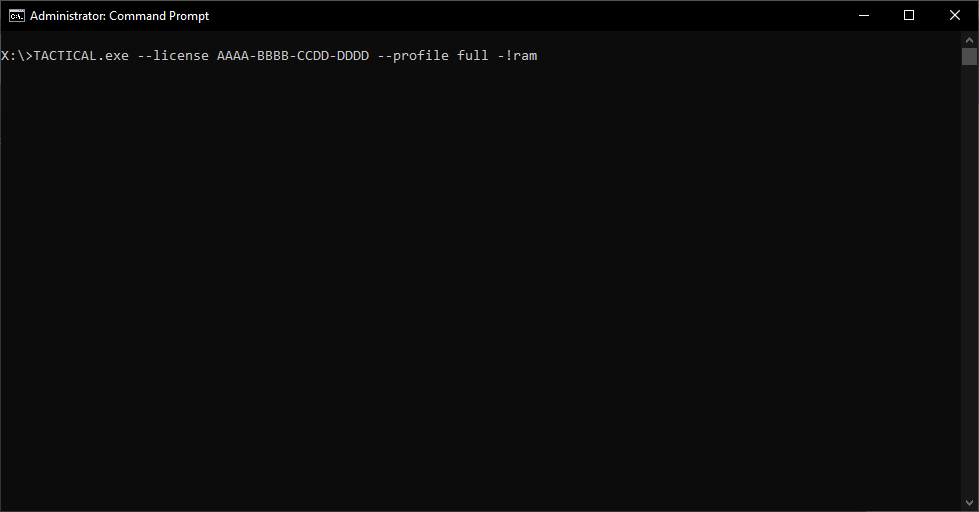
Added support for evidence exclusion at the command line parameters
Sometimes you just know what you are looking for and just want to get straight to it. From this release, we have added the ability to exclude the evidence types you don’t need, simply, from the command line.
Below you can find an example:
Remote evidence acquisition from command-line
Instead of just using the solution on machines in person, TACTICAL gives you the possibility to run the evidence collection remotely from the command line. This feature adds flexibility to your digital forensics investigation strategy by being able to collect evidence remotely and quickly, whenever you need it.
Offline mode
For additional security and applications where the endpoint is already isolated, TACTICAL provides the ability to collect digital evidence in Offline mode without a license check. All evidence collected in offline mode stays encrypted until you connect to the license server at a later time and decrypt the evidence to examine it.
How to get TACTICAL?
If you would like to try the TACTICAL, please visit www.binalyze.com/tactical.















