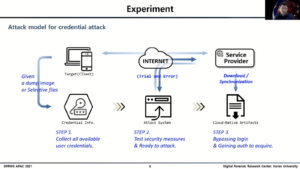
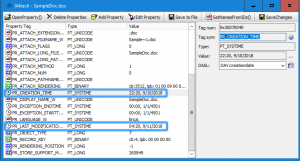
Devon & Cornwall Police’s Steve Slater on Implementing RASSO Changes in Digital Forensics Units
Christa: Welcome back to the Forensic Focus Podcast. I’m Christa Miller here with my co-host, Si Biles, and this week we’re with Steve Slater, Head of Digital Forensics at Devon and Cornwall Police in the United Kingdom to talk about… Read more