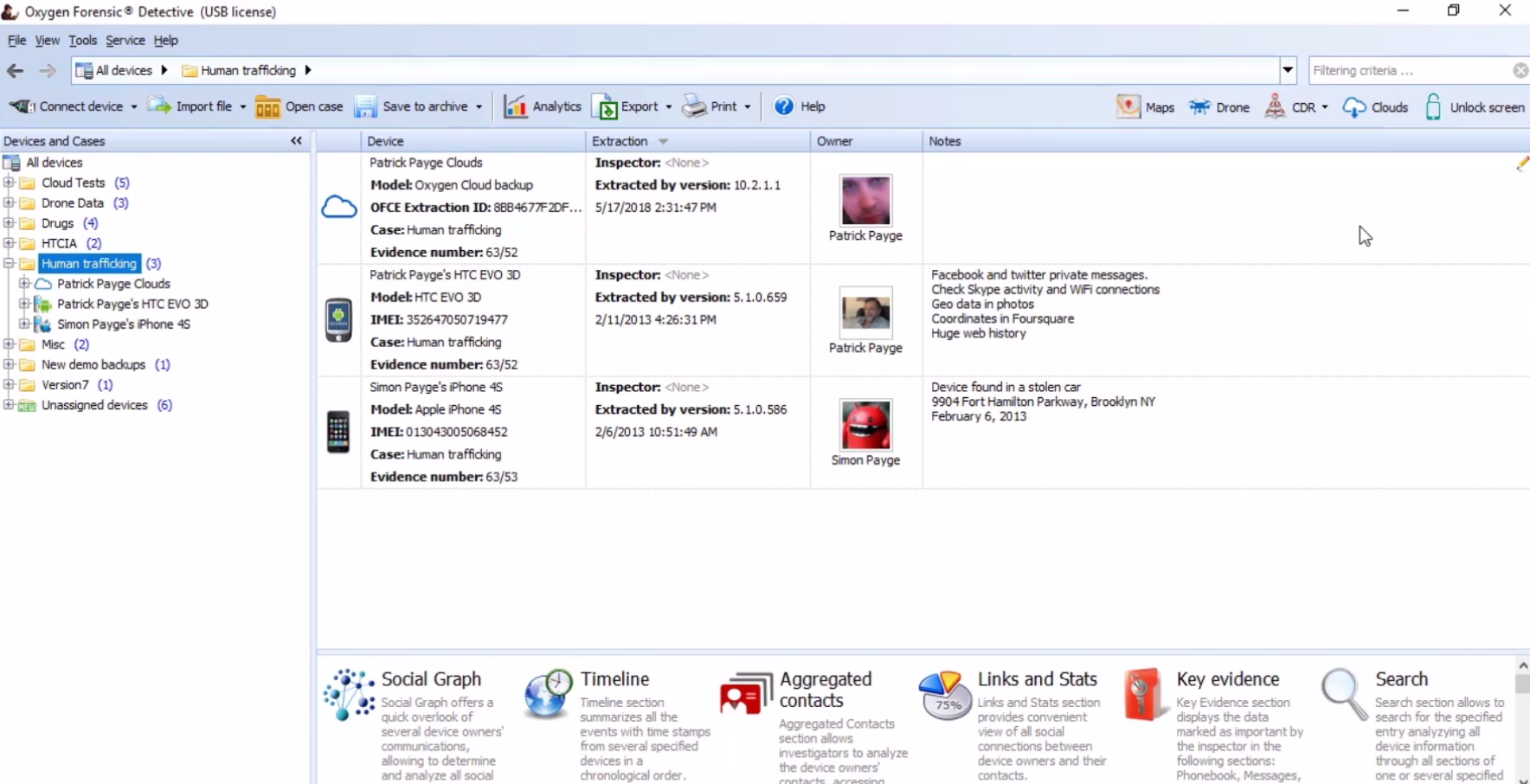
Within Oxygen, you’re able to not only connect one device, but several devices, and image them simultaneously. Oxygen’s extractor runs independently of Oxygen Detective, and that’s what allows you to run several different extractions at the same time, and there is no limit other than what the machine you were using will allow.
So again, with Oxygen Extractor, you’re able to open them up and have several open at the same time, and begin multiple device acquisitions. One of the other things that we’re able to do with our imaging is with drones, specifically DJI drones. We can get a full physical from a DJI drone by simply connecting to the device, applying an exploit, and then extracting the physical image from that drone via the micro USB port that is on the drone itself.
Oxygen was the first to start extracting data from cloud services, and now, with that, just like device extractions, we can now have multiple cloud extractions going at the same time. So, just like with devices, you’re able to extract data on several different cases if they all involve cloud data. And you again are only going to be limited to what machine you are using and the capabilities of that.
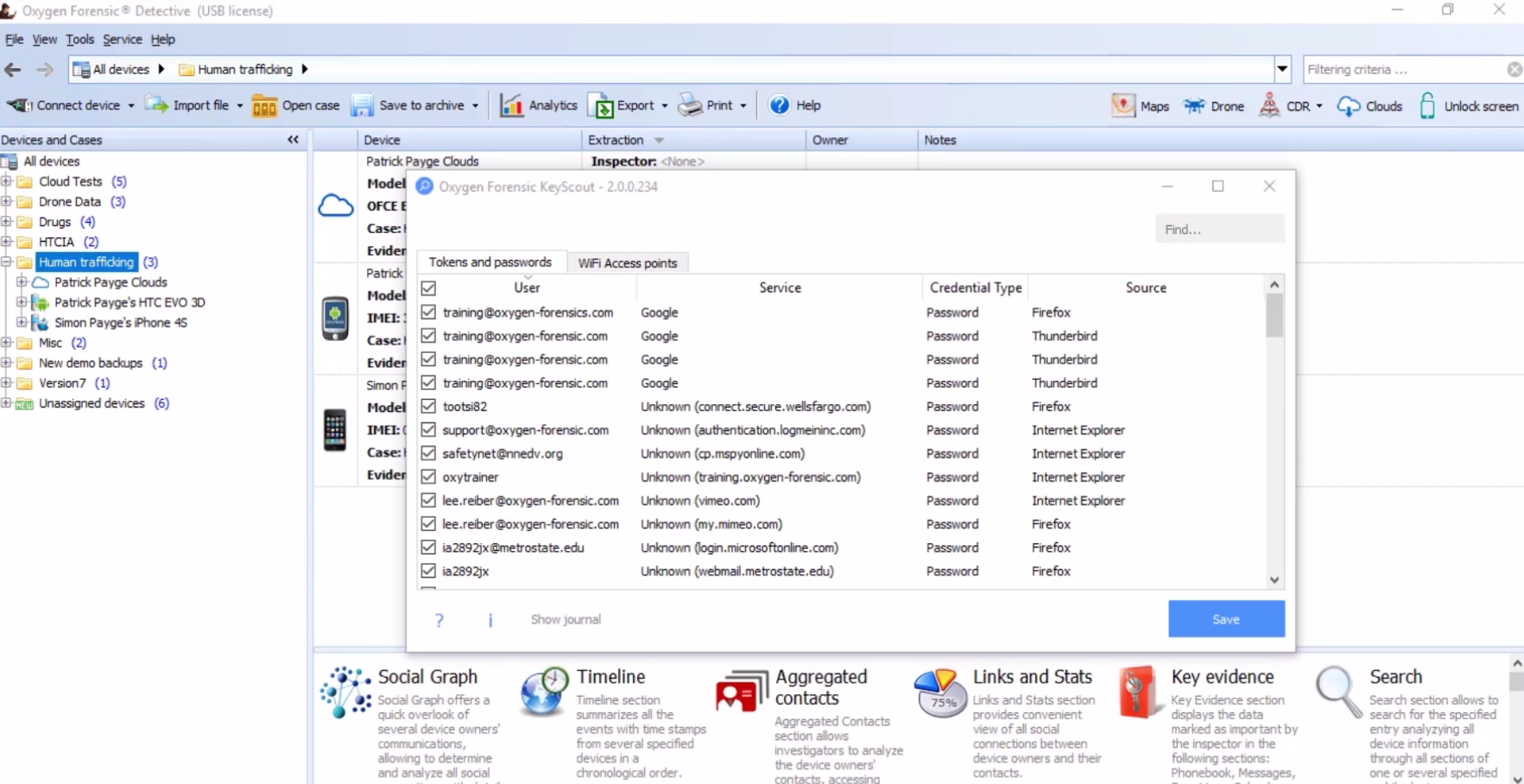
Next, I’m going to talk about one of the newest programs that are available within Oxygen Forensic Detective is our KeyScout program, which allows you to go on to a machine and extract all of the usernames and passwords. And in addition, you’re able to get Wi-Fi names and passwords as well. You can either start KeyScout on a machine that you’re operating on or you can add it to a removable media device and plug it into a target machine, and then run it, and it’s going to produce all the usernames and passwords.
So, when it’s up and running, if we hit Search, it’s now going to search across this computer and identify all of the usernames and passwords. Now, this is going to use all of the major browsers, like Chrome, Firefox, Internet Explorer, so not always is this going to be what was specifically typed on this machine, but could be carry-overs from other accounts that those browsers may use. And with this, you’re going to get tokens or passwords, and the program will tell you if it was a token or a password, and then again, you can also click on the tab the Wi-Fi access points, and this is going to give you all of the Wi-Fi that has been connected with the passwords. And again, this doesn’t always mean this computer was necessarily connected to these Wi-Fi access points, but the user was connected to these Wi-Fi access points, and that could be from a number of different devices as well.
Now, with Oxygen KeyScout, we would then save this file into what’s called an Oxygen credentials package. We save that, and then we’re able to take that file and bring it into our cloud extractions, and go across and search for all of the possible services that these usernames or passwords may work for in getting cloud data.
Within Oxygen Forensic Detective, there are several ways to go about extracting data from the cloud. You can open up Oxygen Forensic Cloud Extractor and you can start a new extraction, you can import that credentials package that you would have created using Oxygen Forensic KeyScout, you can extract iCloud tokens from a Windows PC if they’re … with the Windows application installed. You can search for credentials on a target computer within the extractor. And then the fifth option is also to be able to decrypt WhatsApp backup files that maybe you have found on an SD card or an internal memory of an Android device.
So, if we open up a new extraction, this is where we’d enter in all of our case details. Once we do that, then we’re able to select which platforms we want to extract data from, based on what usernames and passwords we have, or tokens. And all we have to do is simply click, add credentials, type in the username and password, hit Apply. And then it’s going to try to go out and validate that username and password, or, if you have the token, to try to extract that data.
So, if we go out, enter in our target account, and then enter in the password, we apply that – it now puts an indicator that we’re searching for one account on Facebook. And we can do this for any of these accounts that are available for cloud extraction. We hit Next, this is where it goes out and tries to validate our credentials or that token. If we get the green checkmark, it’s going to say … that means it’s good to go. And then, here we can also add any other additional cloud services, now that we know that that username and password does in fact work.
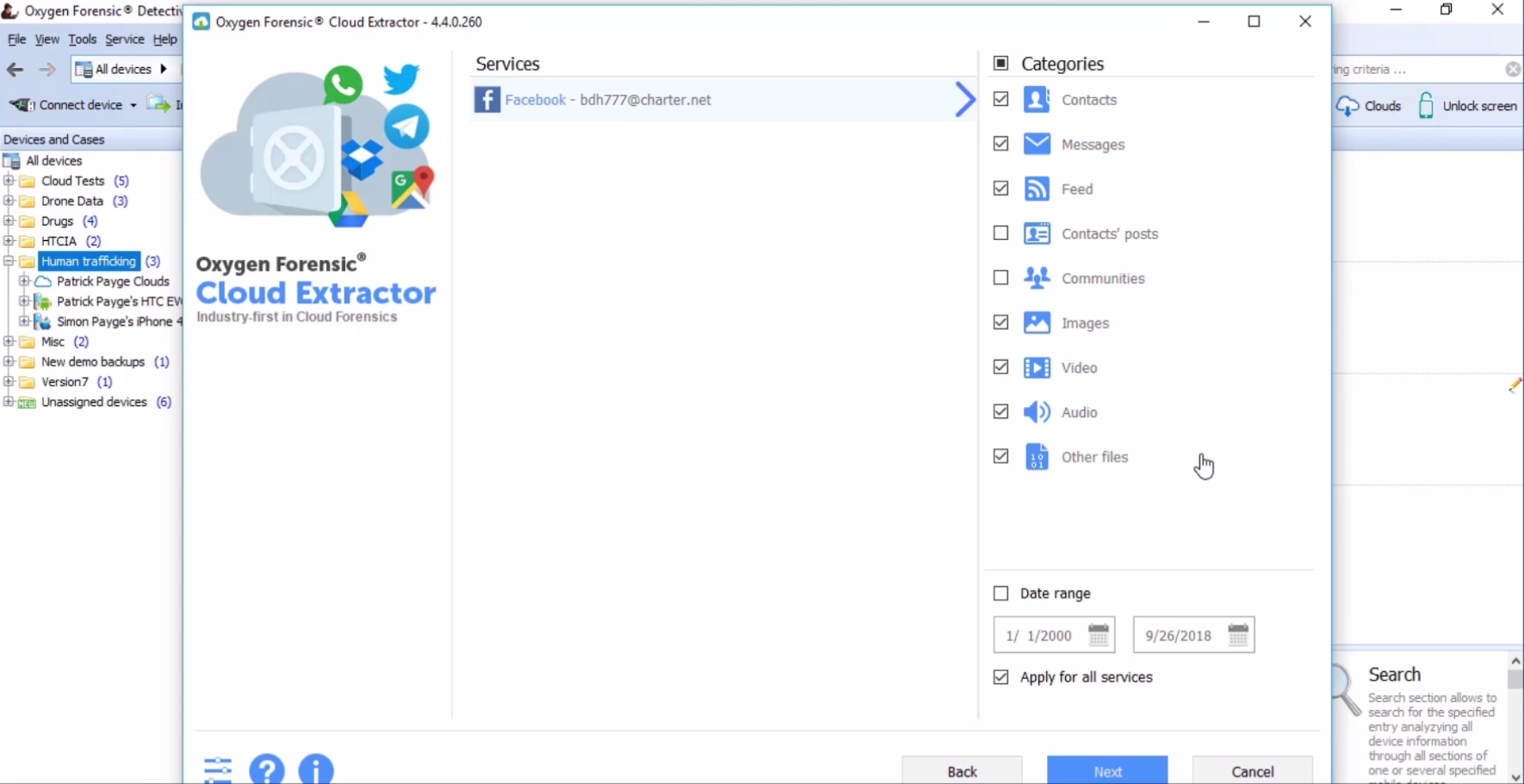
When we hit Next, it’s going to show based on what services we’re trying to extract from. So, this being Facebook, it’s going to show us all the different categories of data that could be available from Facebook cloud. Also, one of the important things that we can do is we can set a date range. And this could be very important for use on the criminal side, being if they’re very limited to the date range based on the incident that took place; or if this is on a civil case, what potential date range is important. Being able to go out and extract only the date range that is pertinent to your case. And with a lot of these cloud services, you definitely would want to put a date range, because there potentially could be years and years’ worth of data.
Now, that was one way to access cloud data. If you’ve extracted a device, whether it’s an Android or an iOS device, you potentially are going to have cloud accounts available on there. Within Oxygen Detective, it’s going to identify those cloud accounts for you. When you go in there, it’s going to tell you the service, the account with the usernames, and whether we were able to extract a password or a token.
Now, from here, we can either save this account data – and that’s going to save it, just like KeyScout did, into an Oxygen credentials package that we can then later import into our cloud extractor. Or, we can, right from here, extract with our cloud extractor, and what that’s going to do for us is it’s going to put in all of the case details for us, as you can see. And then, we can change this data or we can add data to it based on our case.
We hit Next. Now it’s going to automatically go out and identify all the potential services that we can extract data from. And again, it’s going to identify whether it was a username and password or if it was an authentication token. Once we have that, we can now hit Next, and it’s going to identify it, by the numbers, indicating how many accounts we’re possibly going to get with these different services.
Now, at this point, if we knew a username and password for some of these other accounts – for example, Dropbox or OneDrive – we could then enter in those credentials now as well. And again, if we hit Next, it’s going to take us to that same menu, where it’s going to identify and validate these accounts. Once they’re validated, we can then go into the extraction process, which is going to identify what data types we’re going to get from these different services. And also, we can then select our date range as well.
Also, one of the big additions to Oxygen Forensic Detective is for law enforcement, who utilizes Grayshift’s tool, the GrayKey – we can bring in those images as well by simply navigating to the Import GrayKey Image, and then being able to parse all of that great data that we’re able to get from a GrayKey.