Digital forensic analysts are self-made through years of dedication to their area of specialization. Passion and patience are the key ingredients that make them good professionals.
After successfully completing the 100 days of digital forensics quiz I thought that there should be more interaction between the experts and the new entrants in the field of digital forensics. Learning is a never-ending process and it continues until you give up. Many new entrants into the field regularly ask me some basic questions, which I answer with all the experience I have gained over the last two decades. I also come across many professionals who need some clarity and guidance on the day-to-day tasks which are carried out in the field of digital forensics. Hence, I thought that it would be better to discuss important questions, non-technical in nature, with the digital forensic community and find answers which could also enhance my knowledge.
On 18 August 2020 this initiative was started on LinkedIn. Every day a question was posed to the enthusiastic digital forensic community, and the next day I posted my comments/views on the same. The idea of the 25 days, 25 questions (#25Days25Questions) initiative was to achieve three major purposes:
- Creating a common forum for DFIR professionals to interact and share their thoughts
- Increasing the core knowledge base in an interactive mode
- Networking with professionals who are working in this niche area
I have summarised all the responses, including mine, to get a consolidated reply to the question posed. Everyone who has responded has equal credit to the final answer.
Editor’s note: the original 25 questions and answers have been grouped by subject matter across four articles:
- Process & Practice
- Professional Qualifications
- Professional Qualifications in Court
- Lab Standards
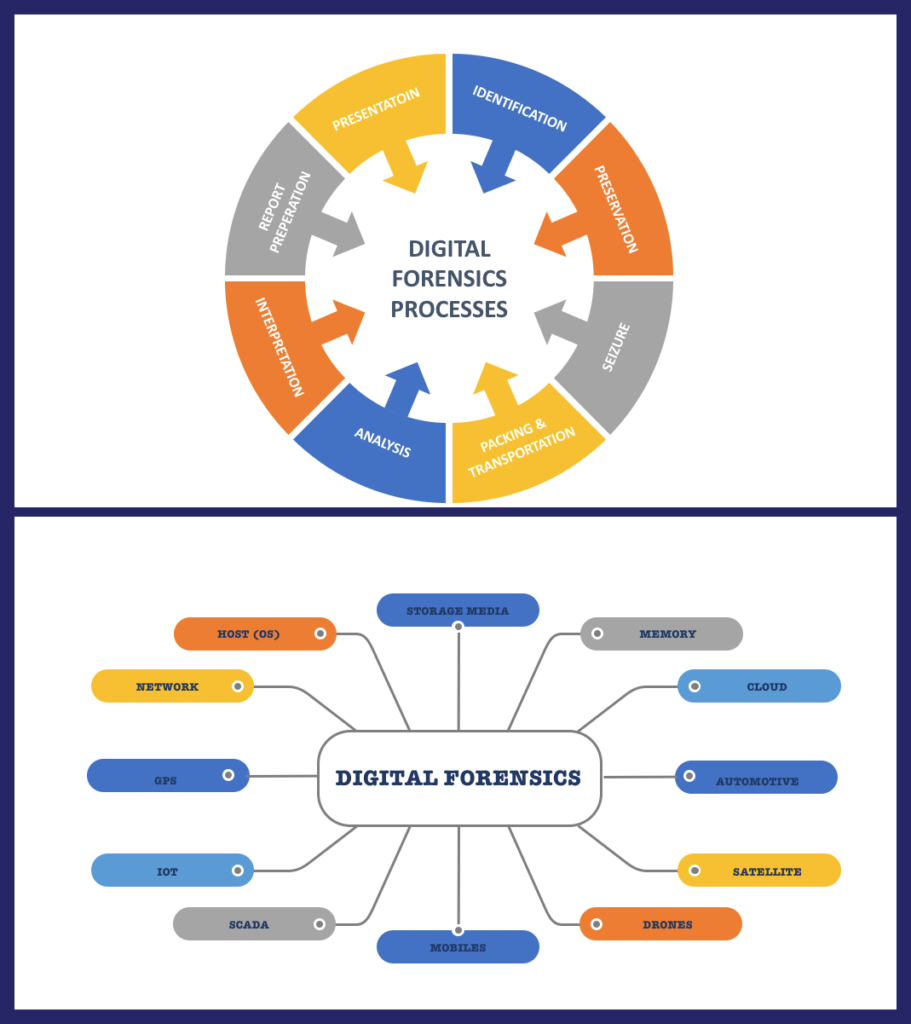
How can we preserve volatile evidence at the crime scene?
(originally asked on day 13)
Computer memory called “Random Access Memory” (RAM) is used by the operating system and its applications when the computer is in operation. The system utilizes this RAM to write the current processes it is using as a form of virtual clipboard. The information is there for immediate reference and use by the process.
“Volatile data” vanishes into thin air when the system is switched off. Volatile data stored in the RAM can contain information of interest to the investigator. It is important to collect the most volatile information first, in order of volatility. This information could include, for example, running processes, executed console commands, passwords in clear text, unencrypted data, instant messages (IMs), internet protocol (IP) addresses, encryption keys (vaults or of ransomware), and so on.
While collecting the volatile data, an investigator should follow these steps:
- Maintain a log of all actions conducted on a running machine
- Photograph the screen of the running system to document its state
- Identify the operating system running on the suspect machine
- Note date and time, if shown on screen, and record with the current actual time
- Dump the RAM from the system to a removable storage device
- Check the system for the use of whole disk or file encryption
- Collect other volatile operating system data and save to a removable storage device
- Determine evidence seizure method (of hardware and any additional artifacts on the hard drive that may be determined to be of evidentiary value)
- Complete a full report documenting all steps and actions taken
There are various open and closed source tools available in market for RAM capturing / collection. A few that are extensively used include:
- Magnet RAM capture
- Belkasoft RAM capture
- FTK Imager
- WinLift
- Command line tools
Other important points to keep in mind:
- Maintain a chain of custody
- Maintain integrity of the evidence collected
- In an Indian context, prepare a 65B certificate under Indian Evidence Act (IEA) for admissibility of the evidence in a court of law
How can we make use of Artificial Intelligence (AI) and Machine Learning (ML) in digital forensics?
(originally asked on day 17)
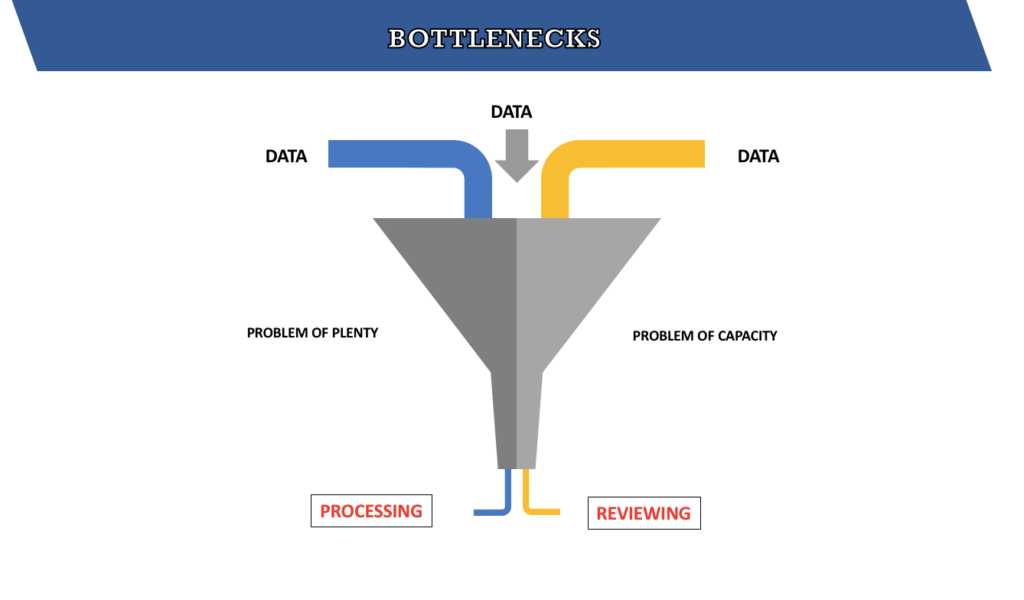
In the present-day scenario we have a problem of plenty (increase in number of devices) and a problem of capacity (size of storage) leading to processing and reviewing issues, in turn creating bottlenecks and delays in analysis. Also when it comes to malware analysis, deep fakes, steganography and so on, we require skills, tools and time.
AI and ML are nowadays used in almost all technology areas. DFIR and ediscovery are also becoming dependent on these principles. One of the major areas within digital forensics, where we can find AI useful, is biometric recognition and deep fake identification. Another is in the detection of pornographic contents on disk images and memory.
AI is also used nowadays for forensic investigations involving malware. In addition, AI can be used in digital forensics for generating forensic analysis and report preparation to solve the problem of plenty and the problem of capacity.
Can blockchain technology be used in digital forensics, e.g. for maintaining chain of custody or preservation of evidence?
(originally asked on day 18)
The answers to this genre of question depend on when we ask them. For example, in the late 1980s a question like “Can we buy platform-as-a-service (PaaS) for a few days?” would have had a different answer than it does today. So when we answer questions about the current state of affairs, our answer often seems to be a hesitant yes/no with a plethora of possibilities and challenges.
But a decade from now, the answer will be an explicit “Yes”. To quote an example, it is well established that the IoT ecosystem has introduced complexities in cyberspace, however, incident responders should value the fact that blockchain offers itself as a “digital witness”. Logs generated by IoT devices can help in the process of event reconstruction, but their integrity and admissibility can be achieved only if a Chain-of-Custody (CoC) is maintained.
Many ongoing works exploit the peculiar characteristic of blockchain (BC) to apply admissibility of digital evidence in a court of law through chronological documentation. Also works like the IoT forensic chain (IoTFC) offer a guarantee of tracking the provenance of evidence items. Proof of concepts in Hyperledger Composer are also available and eventually, whenever BLOCKCHAIN X.0 (MACHINA ECONOMICUS) is realized, it will all be blockchained.
To start with, blockchain as a technology can and should be used in Chain of Custody (CoC).
It is sometimes seen that the CoC, which is a legal document, is tampered with. Sometimes multiple copies are even prepared for the same case. Also in the current pandemic, where e-courts will be held and the accused will be tried via video conferencing and the documents will be shared in digital form, BC implementation in CoC will be very useful.
So let’s get ready for blockchain technology.
Many say MD5 hash has been compromised and should not be used for an integrity check in digital forensics. What is your opinion? If yes, what is your solution?
(originally asked on day 19)
A hash function takes an input value (example, a string) and returns a fixed-length value. An ideal hash function should have these properties:
- fast
- generates unique values for every input (i.e. no collision)
- generates different values for similar input values
- should not follow any pattern
MD5 (128 bit) or SHA1 (160 bit) are hash functions and in digital forensics they are only used for integrity checks and not for encryption purposes. Yes, collision attack (for a file) has been demonstrated for MD5, and weakness of SHA1 has also been demonstrated as a proof of concept. But in digital forensics they are used only for integrity checks.
Globally, MD5 is still used and accepted in courts for hashing of digital artifacts and digital evidence. It is next to impossible to have two storage media with the same hash value. For the time being, if you accept it exists, then you can never find the same contents within it.
One more thing: we also hash the evidence file, along with that of the storage media which contained it. Secondly, mostly tools give us two hashes for a device (MD5 and SHA); again, it is impossible that a collision attack could take place in both cases on the same storage media.
In short, MD5 can still be used as a hashing algorithm for proving integrity in a court of law, but it is recommended that you provide two hashes (if possible) in your report, rather than depending on one hashing algorithm.
Is it possible to extract and decrypt WhatsApp data without an original phone and a SIM? If so, how?
(originally asked on day 20)
WhatsApp data can be decrypted easily if you have the database and the key. If you know the phone number, then a simulator with the same Android version or above can be created and registered. Once the simulator is ready, then the WhatsApp database can be copied or loaded into the simulator phone and opened using the key available.
More information can be found at:
What is the difference between artifacts and evidence? Can they be the same?
(originally asked on day 22)
Artifacts are potential evidence items which are determined as evidence post-analysis if they support the investigation. All digital data that have a potential evidentiary value based on the case requirements can be called digital artifacts. While all evidence is composed of artifacts, all artifacts need not be evidence.
What is digital forensic readiness? Should every entity be forensics ready?
(originally asked on day 23)
Forensic readiness is a proactive step taken by an organisation so that they have a plan in place if an incident occurs. Forensic readiness should be part of the work culture and should be implemented by the IT team. It not only assists during digital forensic analysis in the case of a cyber incident, but also during cyber security checks carried out in the organisation.
Anything and everything that is done today could assist a forensic investigation tomorrow. This is not limited to technology like configurations and data availability, but also includes people and processes. I have seen the evidence being spoiled by IT guys, more than anyone else, due to ignorance.
‘Forensic readiness’ should be part of every organisation’s preparedness, just as security is. Unfortunately no one seems to be interested in preparing for a post-mortem. When we look at infosec holistically, we find a cycle. You protect, they breach, you analyse it and reprotect. Without forensic readiness, one may not be able to understand the anatomy of an attack or exploitation methodologies.
Concluding Thoughts
The 25 days when the questions were posed and answers were received were a true learning experience for all those who not only participated but also observed the whole process. I started my article with a quote, “Listening is talking and sharing is learning”, and that’s what has been achieved at the end. The enthusiasts who did not express their views in writing but only supported in terms of re-sharing or liking the posts must have also learnt a lot from the discussion that took place between the new entrants, the professionals, and the experts in the field of digital forensics. But I would like to tell them they should participate in discussions and put forth their views, as nothing is wrong or right when a discussion is in progress.
Digital forensics is a very niche field and there is a requirement to build a community that can not only network but also voice futuristic ideas for the overall improvement of this field. There is a requirement for mentors who can guide both new entrants and current professionals.
Participation in #25Days25Answers
As anticipated, a wide spectrum of participants including enthusiasts, new entrants, professionals, experts, mentors and academics took an interest and put forth their views in these 25 days. A few of the participants and their designations are as mentioned below.
- Barath Rajagopalan J Iyer, ACIArb, CMO, Founder & Director – SourceData Consulting
- Prince Boonlia, Editor In Chief at Digital Forensics (4N6) Journal
- Heather Mahalik, Senior Director of Digital Intelligence at Cellebrite & SANS Senior Instructor, DFIR Co-Curriculum Lead and Author
- Richard Saylor, Computer Crimes Program Manager at U.S. Army Criminal Investigation Command
- Venkatesan Owner, Lab Systems India Pvt Ltd
- Jessica Hyde, Director, Forensics at Magnet Forensics
- Michael Smith, Cybersecurity, Privacy & Disaster Response
- Rajesh Kumar, Certified Cyber Forensic Professional at State Forensic Science Laboratory, Patna
- Anupam Tiwari , IT Security Enthusiast and Blockchain Learner
- Patrick Siewert, Founder & Principal Consultant, Expert Witness, Nationwide Instructor
- Patrick Eller, CEO – Digital Forensic Examiner – Expert Witness
- Amrit Chhetri, DFIR & AI Researcher
- Aman Agarwal, Cyber Crime Investigator and Incident Responder
- Nikhil Sood, Information Security Auditor
- Om Salamkayala, Digital Forensics Professional
- Kashish Srivastava, Intern @Noida CyberCell
- Rohit Tiwari, SOC Trainee at SOC Experts
- Vipin George, Cyber Forensic Consultant, Kerala Police Academy
- Piyush Kohli, Cyber Threat Engineer – Global Threat Operations
- Bikash Halder, Cyber Security Analyst
- Atoshe Lohe, Managing Director at INsoftware & Solution/Institute of Information Security and Computer Forensic.
- Shreya Koley, Summer Intern at KPMG
- Shubham Sangwan, Intern at Gurugram Police
- Kanishka Joshi, Actively seeking opportunities in Auditing and Compliance
Bibliography
- Khadsare, S. (2020) Grouping of Professionals in Cyber Forensics. Digital Forensics (4N6), 2(3), p. 82
- Khadsare, S. (2020) 4N6 Sunday: Grouping of Professionals in Cyber Forensics [Accessed 24 Sep 2020]
- ISO/IEC (2015) ISO Standard 44405 [Accessed 24 Sep 2020]
- ISO/IEC (2017) ISO/IEC 17025 Testing and Calibration Laboratories [Accessed 24 Sep 2020]
- ISO/IEC (2012) ISO Standard 44381 [Accessed 24 Sep 2020]
- ISO/IEC (2015) ISO Standard 44406 [Accessed 24 Sep 2020]
- ISO/IEC (2015) ISO Standard 44407 [Accessed 24 Sep 2020]
About The Author

Mr. Santosh Khadsare is a digital forensics expert from India with two decades of experience and presently is heading a digital forensic laboratory in New Delhi, India. In addition to his Bachelor’s degree, he possesses additional qualifications such as CHFI, CEH, RHCSA, Advance Cyber Forensic Course (CDAC), Cyber Crime Investigator, IVTA (CMU, Pittsburgh USA), and so on. He has rich experience in the fields of information security, digital forensics, cyber audit, cyber laws and incident response. He has been a speaker in various national and international conferences, and has also authored various articles on information security and digital forensics in reputed publications.
Contact details:
Email: santoshkhadsare@gmail.com
LinkedIn
















Great!!! and the part 3? i d´nt found it