The popularity of virtual digital assistants is growing at a pace never seen; the estimated number of people using digital assistants worldwide is projected to reach 1.8 billion by 2021. These “assistants” make our lives easier and relevant but they also can equate to a serious privacy concern. From issues of assistants recording conversations by error and sending to uninvolved contacts, to documenting and storing all voice commands; investigators as well as users should be privy to the consequences, or evidence. Today, digital assistants are becoming one of the more valuable sources of evidence to investigators and have already been used to solve several noteworthy crimes.
As of January 2019, Amazon’s development devices team announced they had sold over one-hundred million Alexa-enabled devices which is now available in over forty countries. When an Alexa user utters the wake word to perform a skill a recording of the query is sent to the user’s Amazon cloud account. The user specific request is processed and a response is returned to the device. Investigators, armed with Oxygen Forensic Cloud Extractor, can extract Amazon Alexa data to include these valuable recordings of that actual utterance by the user.
How to gain access
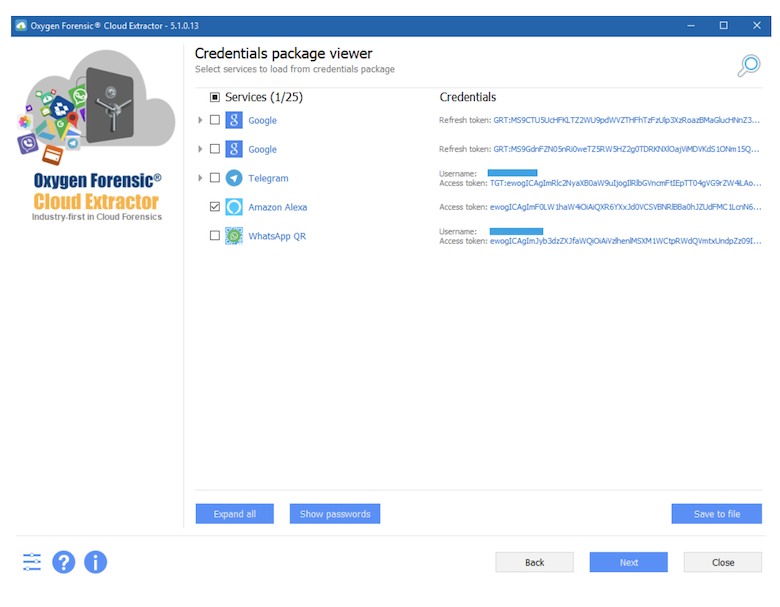
Oxygen Forensic Cloud Extractor can obtain access to the Amazon Alexa account using either login/password or user token. A user’s token can be extracted from either the mobile device(s) or PC(s) Alexa is currently paired to. The Amazon Alexa token can be found in the Cloud Account section in Oxygen Forensic Detective after the mobile device has been acquired. If using a PC to locate the Amazon Alexa, simply run our Oxygen Forensic KeyScout utility. Using our powerful KeyScout utility a user’s token can be recovered if the user has logged into their Amazon Alexa account in their PC’s web browser. It should be noted that using a token will allow an investigator to bypass 2-factor authentication that had been set within the Amazon Alexa account.
Data from cloud
Once the cloud extraction has completed the investigator can either elect to import the collected evidence to Oxygen Forensic Detective or to our new Oxygen Forensic JetEngine module. The lion’s share of data from mobile applications are stored within the cloud. With this being said, it should be understandable that there is a massive amount of user data available for collection. Without question, Oxygen Forensic Cloud Extractor acquires more data from these services than any other competing tool, hands down. The valuable data extracted can contain a wealth of information to include: account and device details, contacts, user activity, incoming and outgoing messages, calendars, notifications, user created lists, created/installed skills, preferences, and more. One amazing feature in the software is the ability to extract the stored voice commands given to Alexa by the user. The users actual voice! The information extracted from Amazon will undoubtedly give tremendous insights into the user’s everyday activity, their contacts, shared messages, and valuable voice commands.
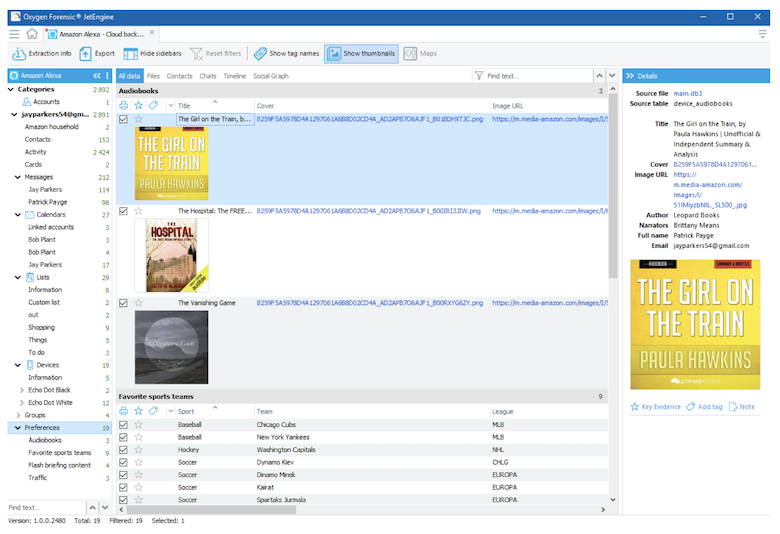
Like Amazon, Google has to bring to market their own digital assistant. Today’s documentation says that there were 52 million Google Home devices sold in 2018. Oxygen Forensic Detective arms investigators with tools to extract data from Google Home from both mobile devices and the associated cloud service.
How to gain access
Oxygen Forensic Cloud Extractor allows access to a user’s Google Home account by entering either the login/password or a Google master token. Our robust software is also capable of finding Google credentials both in a mobile devices’ image and on an associated PC. Finding Google credentials extracted from a mobile device is easy; simply navigate to the Cloud Accounts. Also, using our KeyScout built-in utility the investigator can collect the token information from the associated PC if the user had used the PC to log into their account.

Data from cloud
Once armed with credentials, the investigator can use the Oxygen Forensic Cloud Extractor to access the Google Home account. Like in our many other supported cloud services, the token will allow you to bypass 2-factor authentication if enabled. If your investigated user utilizes a username and password for login authentication simply be prepared to verify the identity by one of the available methods: SMS, Google Authenticator, backup codes, prompt or USB token. Google cloud provides investigators with a tremendous amount of data that is generated by a Google Home user. Data includes, but is not limited to: account and device details, voice commands, and verbose information about users. Again, like Alexa, investigators can listen to all the voice recordings created by the Google home users directly in Oxygen Forensic Detective.
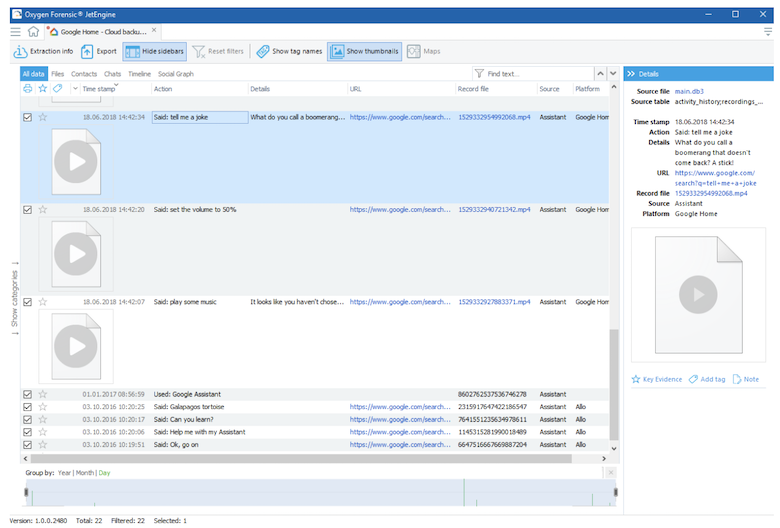
Many users of a Google Home device use the Google Home to set up, manage and control a Google Home device. Oxygen Forensic Detective supports the parsing and decoding of the Google Home app data from both Apple iOS and Android devices. Data is available from iOS devices that have been jailbroken or those collected physically by Grayshift's GrayKey. Android devices must have root access or physical access to recover the database file for Google Home. Oxygen Forensics, Inc. offers a wide range of physical collection methods that are successful on a large set of Android devices.
Extracted information from the mobile app, once obtained, will include: account and device details, cache, cookies, nearby devices, and other valuable user data. It should be understood that the mobile app for Google is an active application and the app contains far less data than what is stored in the user’s associated cloud account. A user’s cloud account is recommended if the investigation calls for the recovery the user’s complete stored history.














