A little while back Chad Tilbury, a SANS trainer and talented forensicator, was kind enough to write a blog post about our free tool EDD (Encrypted Disk Detector) and ask his readers to fill out a survey to indicate which additional encryption support they wanted added to EDD.
The response was great and made it easy to decide which encryption products to add support for. Today we are excited to release EDD v2 with improved encryption detection support for the already supported products (Truecrypt, Bitlocker, PGP, Safeboot), and added support for Checkpoint Endpoint Security FDE, Sophos Safeguard FDE, Symantec Endpoint Encryption FDE, and Bestcrypt.Other minor improvements were also added, including requiring the executable to run as Administrator (to ensure the tool doesn’t fail because it didn’t have Admin rights), and more intuitive colours for certain notifications (yellow = warning, red = encryption detected). Below is a screenshot showing EDD detect Symantec full disk encryption.
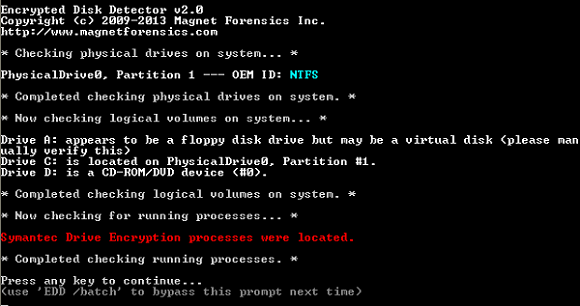
For those who are not familiar with EDD, it is a command line tool intended to be used on a live system that checks for full disk encryption or mounted encrypted volumes. The intention is that EDD is used when doing live response forensics to detect the presence of encryption before “pulling the plug” (and possibly losing all the data if the encryption password is not known). It takes a couple seconds to run so the process is not lengthy and it can easily be included in a batch file/script. Note that EDD does not search all files on the drive to detect entropy, it only looks for mounted encrypted volumes/FDE.
How does EDD detect the mounted encrypted volumes/FDE? Some of the FDE products out there leave a signature on the drive somewhere, either a volume boot sector or master boot record. The text/bytes they leave in places like that are helpful in identifying that the FDE product is present on the drive/volume, so those areas are checked by EDD. Some don’t leave these signatures, or the signature is only accessible when the hard drive is in an encrypted state (not helpful in a live scenario), so the best way to detect that they are running is to check for specific processes that are active when those FDE products are present. In some cases (when possible), we’ve implemented checks for both signatures and process detection in EDD v2.
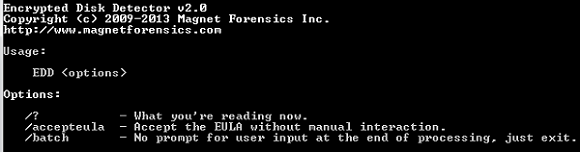
EDD does not make any changes to drives or files on the live system, all of its operations are completed in a read-only mode. Running EDD is simple, simply run it without any parameters or use one of the below options when running in a script:
Download Encrypted Disk Detector now.
If you have any questions , please don’t hesitate to contact us on our Magnet Support site.
Thanks for your support!
Jad and the Magnet Team














