The Passware team has analyzed over 4 billion real user passwords and gathered data on the latest trends on password use.
ABOUT THE RESEARCH
As sources of passwords, we have merged leaked passwords databases available over the internet, passwords recovered by our software, and passwords uploaded to our Password Exchange server into a single database. In total, the database contains over 4 billion passwords. We have removed duplicates and invalid records, and we are now happy to share this database with our customers so that they can leverage it as a dictionary in their password recovery processes! The dictionary consists of 3.2 billion real passwords, and it is 8.4 GB in size. This is 30% more than our previous proprietary leaked passwords dictionary, compiled in 2018.PASSWORD LENGTHS
Over 80% of the passwords in the database have lengths of 8, 9, 10, 12, 11, 7, and 13 characters in descending order.
8-character passwords account for 20% of the passwords, while 9-character passwords account for 15%.
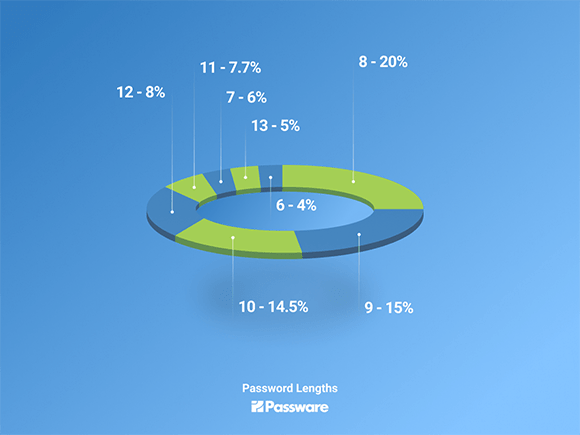
Compared to the data we gathered in 2017, we see that passwords now tend to be longer in general. For example, 6-character passwords accounted for over 20% of the cases in 2017, and now they account for less than 4%.
Some of the reasons for this change are:
- stricter security policies;
- password managers – users no longer need to memorize passwords;
- more efficient decryption tools that recover stronger and longer passwords.
- letters + digits + letters (passwords like “strong2019password”) – 5.7%;
- letters + symbols + letters (passwords like “strong!password”) – 5.3%;
- digits + letters (passwords like “2019password”) – 5.3%;
- digits only – 4%.
- letters ( length 8 ) – 6.7%;
- letters + digits ( length 10 ) – 5.5%;
- letters + digits ( length 8 ) – 5.3%;
- letters + digits ( length 9 ) – 4.5%;
- letters + digits ( length 11 ) – 3.1%;
- letters ( length 9 ) – 2.7%;
- letters ( length 10 ) – 2.6%;
- letters + digits ( length 12 ) – 2.6%;
- letters + digits ( length 13 ) – 2.2%.
[/list:u]
PASSWORD PATTERNS
A password pattern is a certain combination of letters, digits, and symbols used in a password in accordance with user preferences. Awareness of the suspect’s preferences allows computer forensics to apply a pattern to a password recovery process and to make the brute-force process more efficient.
Over 55%(!) of the passwords have the following two patterns: letters + digits (29.5%) and letters only (26%). Other popular patterns include:
[/list:u]
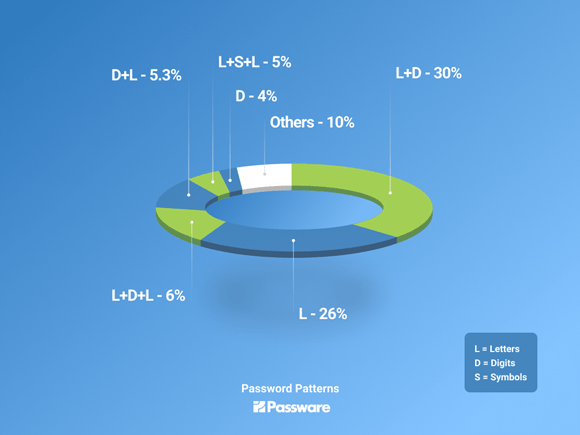
The patterns above cover over 85% of the cases.
The leading password by a large margin is a word followed by 2-4 digits, e.g., “password2019”.
There is a significant change in password patterns compared to data gathered in 2017. The “digits only” and “digits + letters” patterns have dropped in prevalence a lot, while complex patterns, such as “letters + digits + letters” and “letters + symbols + letters,” have increased in popularity.

DETAILED PASSWORD SETTINGS
35% of the cases cover the following combinations of password length and pattern:
[/list:u]
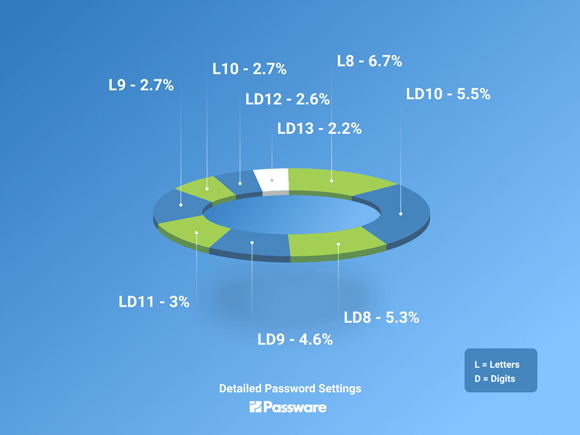
Thus, the top four combinations, which account for 22% of cases, are:
8-character passwords of letters only, 10-character passwords of letters and digits, 8-character passwords of letters and digits, and 9-character passwords of letters and digits.
NUMERICAL PASSWORDS
It is important to mention that numerical-only passwords have become obsolete. None of the password types that contain digits only accounts for more than 1% of cases.
Does this mean that we need to exclude such types from a brute-force password recovery process?
Our answer is “No.” On the contrary, such patterns should necessarily be present in brute-force settings. There are only 100 million 8-digit passwords in total, and although this represents only 2.5% of all the passwords in the database (remember we have over 4 billion passwords in total), this brute-force attack for digits only finds more than a half the numerical passwords in the database, i.e., its success rate is over 50%. This is why numerical passwords should not be excluded from password recovery attacks.
DOWNLOAD LEAKED PASSWORDS DICTIONARY
All Passware Kit Business and Passware Kit Forensic users have access to our leaked passwords dictionary, which we have compiled during this research. The dictionary is available for download (8.4 GB) in Passware Account, on the “Free Dictionaries” tab.














