AD Enterprise allows investigators to collect, preserve and analyse data from various sources remotely from Windows and Mac computers, as well as to parse and review mobile data.
As a holistic tool which encompasses many features, Enterprise at its core allows an investigator to preview live data from an endpoint, then filter on specific attributes, which saves a lot of time in investigations. By deploying the remote Enterprise agent, collections from endpoints can be achieved in multiple locations which can be running an extensive range of operating systems including Windows, Mac and Linux.
In corporate environments, discretion is crucial within investigations, since open knowledge about the investigation can impede the end result. With this in mind, AD Enterprise allows an investigator to monitor content, scan networks for violations, investigate IP theft and track employee misconduct unobtrusively.
With Enterprise 7.4.2, there is an emphasis on network investigations and post-breach analysis. In previous releases, the ability to support mass deployment of Mac agents remotely was introduced, and now with the use of network file system technology, the collection of data with Mac agents is significantly faster.
The latest version also includes enhanced collection of volatile data, Q-View integration, facial and image detection, portable case enhancements, updated support for UFDR (file extension native to files created by UFED Physical Analyzer), and easy mobile chat data and multimedia review.
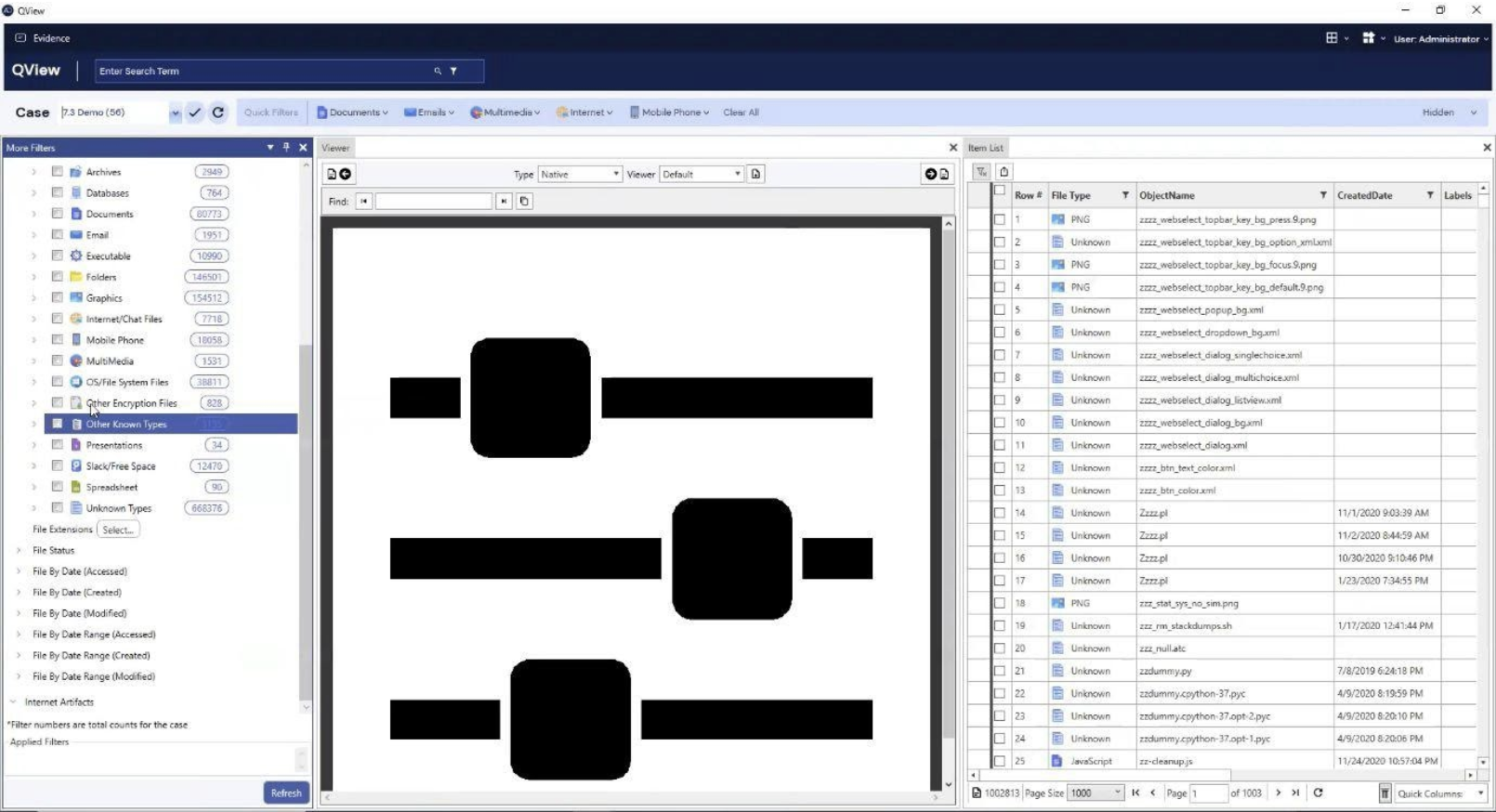
Enterprise Off-Network Agent and Cloud Data Collection
The COVID-19 pandemic has meant that more professionals are now having to work from home, sometimes on their own personal devices. This raises a variety of security concerns, and corporations could be more vulnerable to fraud, IP theft etc., among other security risks. It is therefore important that investigators are able to collect data from computers which are not connected to a corporate network or VPN.
With AD Enterprise 7.4.2, as long as the computer has internet access, it will be possible to collect data from these endpoints. This is only available for Windows for the time being, but AccessData are actively working on a solution for Mac users.
The key differentiator AccessData leads the market with is its maturity over time for this feature. AccessData has had technology to collect data from off-network machines for over 4 years now (part of eDiscovery solution) but in order to help the corporations during these tough times, the capabilities were extended to FTK Enterprise as well.
FTK Enterprise 7.4.2 also introduced collections from structured data connectors and cloud repositories. Off network data collection is a free service, however collecting data from Google Drive, SharePoint and Microsoft Teams will require a purchase. Building on existing Site Server technology, a new auto resume function is now available, meaning that if data collection is interrupted (endpoint is turned off, disconnected from internet, IP address changes, FQDN changes or there is just a network glitch) then it will resume automatically once the connection is back up and running. Again, something which not many offer in the market today.
QView Enhancements
QView is an independent review platform: a scaled back version of Enterprise, which can be used by non-technical staff. This allows for easier review of data.
QView is completely adjustable, so users can change the view to suit their requirements, adding or removing panels and changing configurations. Bulk labelling and bookmarking is an option in QView, and any labels or bookmarks will be made available when synced to Enterprise. QView can be downloaded from the AccessData folder within Program Files.
QView provides the best filters and views for reviewing mobile data. The user is able to choose how to view a chat message and can also apply a bookmark or label to chat messages from within the viewer itself.
If the chat message had an attachment, for example a document sent within a Microsoft Teams chat, this can also be reviewed here. Users will also be able to view the whole message chain and see whether there were any replies to specific messages.
Further support for multiple languages has also been added in QView, and it is now possible to add manual translations of text.
Extended System Information
Usually in an investigation it is necessary to search the registry and other repositories for relevant system information and forensic artifacts. Providing operating system information offers key insights and a clear direction for an investigation.
With a focus on making reviewing this information much easier for the users, AccessData previously introduced a ‘System Information’ tab which automatically searched and presented data of evidentiary value. However, this tab only presented a few key categories and users were not able to bookmark or label the data, needing instead to take screenshots to include in reports.
The Research & Development team at AccessData has carried out extensive research into different operating systems (Windows 8 through to Windows Server 2019) and the information available in each. Now, more than 70 forensic artifacts have been added to improve and enhance what is now known as the ‘Extended System Information’ tab.
In version 7.4.2, system information can be extracted more accurately and OS data will be presented in newly created categories (Applications, Browsers, Device Interaction, Networks, Operating System Information, Recent Files and Windows Events – each with a multitude of sub-categories).
The benefits are immediately obvious, with the ability now to be able to bookmark and label any item within the Extended System Information tab and include it within reporting; and with the columns auto-adjusted to ensure that the user is reviewing the data effectively.
Device Interaction in Enterprise 7.4.2 is not just limited to USBs. This category has recently been enhanced to include more operating systems, and it now shows more metadata than before, including data from smart TVs.
Operating System Information includes group/user accounts, owner information, timezone info, the Windows notification center and Windows timeline data. Recent Files already included shell bags, but now also includes AmCache shortcuts, jump lists, keyword searches, link files, MRU folder access, recent files and folders, open and saved files, and run commands.
AmCache and ShimCache forensics can provide a timeline of which program was executed, when it was first run, and when it was last modified. These artifacts are also included in the newly improved Extended System Information.
Windows Events include SRUM network connections and usage/push notifications. (SRUM is the System Resource Usage Monitor which first appeared in Windows 8). It monitors Windows applications, programs, services and network connections.
There are many forensic uses for SRUM, including providing answers into which user launched a process; network statistics application run times; and deleted/uninstalled/external program tracking. These kinds of information are particularly beneficial in cases of corporate espionage.[1]
APFS File Vault 2 Decryption Support
AD Enterprise 7.4.2 will include support for the decryption of File Vault 2 volumes from APFS file systems. If there is a password for a File Vault 2 volume which has been added to the disk, the user will be able to enter the password during image ingestion and check it to make sure it is correct.
Decryption is also available for AFF4 files. The process is simple: the user will add AFF4 as a file and adjust the refinement options (evidence processing), and will then be prompted to enter a password. If no password is entered, the user has the option to continue without decrypting any encrypted volumes in the container. If a password is entered, the user is then able to test the password first before the processing commences.
Enhancements to the Evidence Processing Engine have improved AFF4 processing speeds. For example, an Apple MacBook Pro APFS computer in previous versions of AD Enterprise would have taken over five hours to process once processing,
post-processing and indexing had been taken into account. Now the same processing can be achieved in just over an hour.
Portable Case Enhancements
The ability to create portable cases in Enterprise was launched in version 7.4 and allowed users to export data into a portable case file. Feedback received suggested that this process used to be slow and unable to cope with large quantities of items. In the latest release, the speed of export has been increased by enabling multiple thread support and now portable cases are better equipped to handle large quantities of items. Previously, it could handle up to 2 million items; now it is able to handle approximately 5-6 million items.
Exporting native files in a portable case also has more options in the new release: users can now convert unknown extensions to .pdf and export the native file if .pdf fails.
Column selections have been introduced so that users can organize items more efficiently. Creating labels and applying bulk labelling are both still available. There is now an option to choose where to save the portable case: either in the case folder or a custom destination path. A portable case consists of files, an index folder, a QView folder, a thumbnails folder and .bat files which are used to start up QView Offline.
Conclusion
AccessData continues to go above and beyond to meet customers’ needs and requirements. Enterprise 7.4.2 provides their most advanced tool yet, with an increased emphasis on processing and reviewing capabilities.
Jade James BSc (Hons) is currently a Cyber Security and Forensics Postgraduate Student. She has previous professional digital forensic experience from working at the UK’s Serious Fraud Office, IntaForensics, the Home Office Centre for Applied Science and Technology and the City of London Police. Jade has experience of conducting computer and mobile device examinations as well as drone forensics, and has been involved with ISO 17025 & Quality Standards both as a digital forensic practitioner and quality manager.
References
- Khatri, Y. (2021). SRUM Forensics. Sans.org. Available from
https://digital-forensics.sans.org/summit-archives/file/summit-archive-1492184583.pdf [Accessed 23 January 2021].
- Singh, B. and Singh, U. (2016). Leveraging the Windows Amcache.hve File in Forensic Investigations. Journal of Digital Forensics, Security and Law. Available from https://doi.org/10.15394/jdfsl.2016.1429 [Accessed 23 January 2021].