Si Biles, co-host of the Forensic Focus podcast, reviews Cellebrite Enterprise Solutions’ Endpoint Inspector.
Device acquisition is an important topic, and as with cooking, results are only as good as the ingredients that you are using. Thus any tool that enables quick, efficient and accurate acquisition of devices for analysis to me is a really good thing, even if the other aspects – such as the device and the network – are beyond your control. This is where Cellebrite Enterprise Solutions’ Endpoint Inspector (EI) comes in – providing a high quality ingredient in a digital acquisition recipe.
Although in the pre-COVID world, remote work was “a thing”, during- and post-pandemic we are in a very different landscape, where employees may rarely be present in an organisational office or, conceivably, never in an organisational office. This new-normal that we are all enjoying presents us with a need, if we wish to examine in detail a given organisational device, to perform a remote acquisition of it, as sending someone round with a big USB drive isn’t really an option when your staff are stretched from Adelaide to Zurich. If your IT department isn’t into cobbling together a solution using a remote session, dd, two tin cans and a long bit of string, this has opened the market to some enterprising organisations to provide tools for doing just that – smooth, seamless and – most importantly – remote acquisitions of device.
Cellebrite is a name that I’m sure many people are familiar with. It’s an organisation that was established in Israel in 1999 and has since built a significant global presence. It’s probably best known for its Universal Forensic Extraction Device (UFED) for the imaging of mobile devices.
Cellebrite recognises that EI is a youthful product, and it’s currently on a steep trajectory for features being added in new releases – I started reviewing the product on version 1.4, and we’re now on version 1.6, having been through 1.5 and 1.5.1 in the interim. If you’re even slightly slow to the party after reading this, the product may well have changed significantly, but the base features discussed here, whilst perhaps sitting elsewhere in the user interface, are only going to be enhanced.
When we consider how we might go about performing a remote acquisition, there are two clear methodologies that we could attempt to go with – covert or overt. If we were attempting to be covert, the idea would be that we would be as undetectable as we could, surreptitiously sneaking our software onto the suspect device, hiding it from the users view and so on, with the objective of keeping them in the dark. If we are happy to act overtly, we make no effort to bamboozle the user and quite happily inform them of our intent and perhaps even co-opt them into the process. In an environment when the organisation owns the devices and has appropriate terms and conditions of use in place, either methodology can be considered to be legal, outside of such an environment legality drops off quickly without intercept and interference warrants. [NOTE: Your mileage may vary here depending upon your exact jurisdiction and your local laws!]
You can debate the merits of a covert methodology, and I’m sure that vendors who support it will have plenty to say on the matter, but for me, and for Cellebrite, overt is fine. There is no covert capability in Endpoint Inspector – everyone is treated like an adult and there’s no messing around – and this immediately removes a whole raft of concerns. Of course, the corollary of this is that someone who is skilled enough would be well aware of the required anti-forensics … It should also be noted that the default assumption from a non-responding remote agent is that the machine is turned off – there’s no active alerting on a non-responding agent. In the case of the skilled avoider, it could therefore be some time before you figure out that you’re not getting a response. It’s a design decision, not one that I disagree with, just one that you have to be aware of. It sure beats responding to a million false positives when people close their laptop for the day!
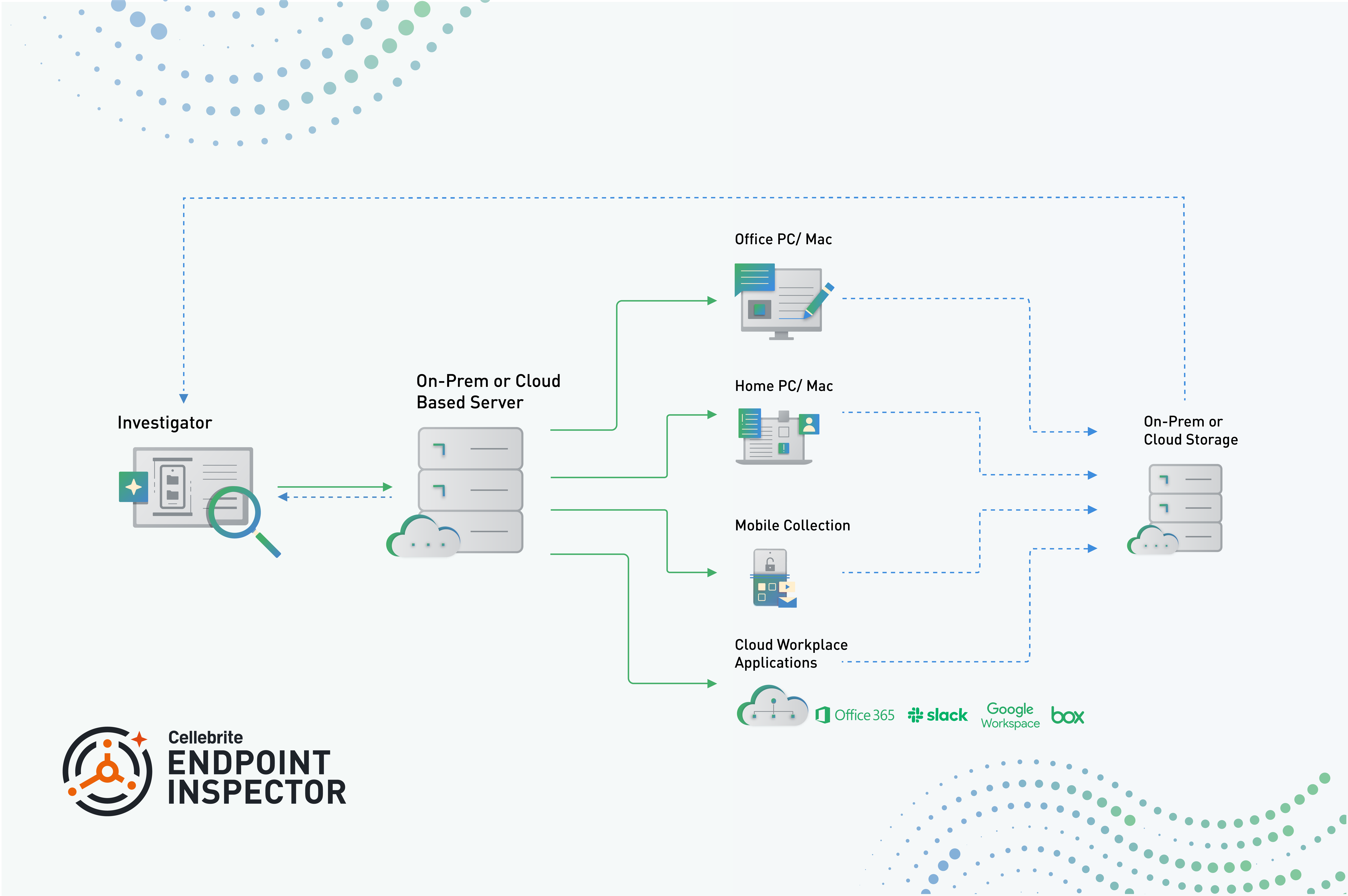
Endpoint Inspector is – as I think you would expect – a client/server product. The choice of cloud or on-prem server – the example seen by the reviewer was in an AWS environment for example – is down to the organisational strategy and the risk appetite.
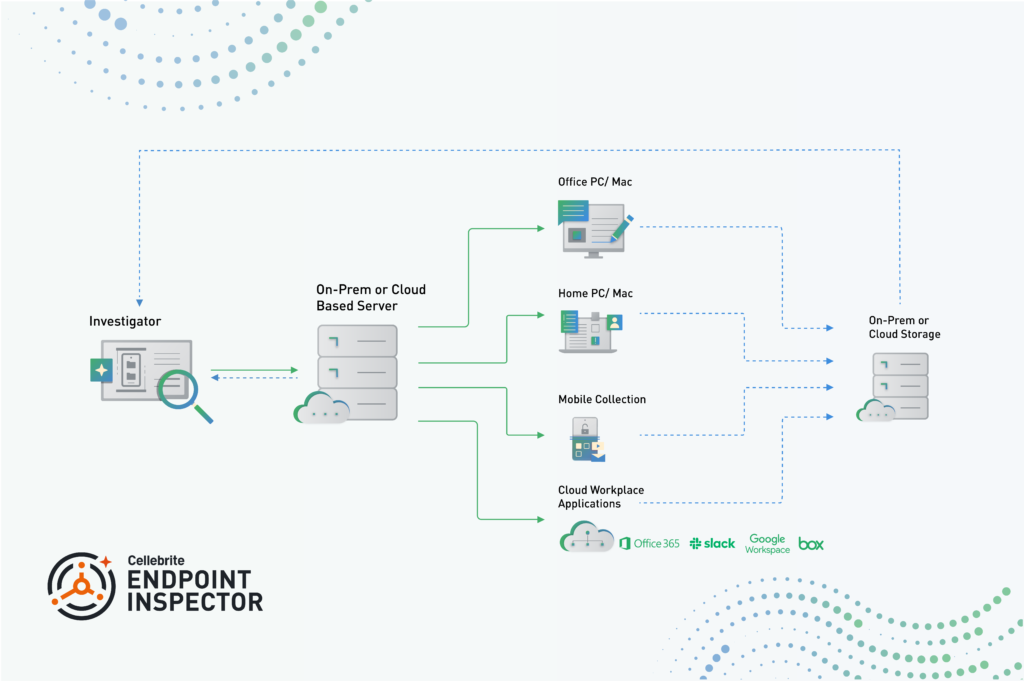
Figure 1: Solution Architecture
The data that you manage to acquire from your sources can be stored in a wide variety of data storage locations from S3 buckets to simple network shares or pushed over SFTP into whatever else you may desire. There are – self-evidently I think – restrictions based on your location within your network and your network boundaries – you’re not going to be pushing captured disk images into a UNC share from outside of your network, but a user within the firewall in the same Active Directory domain may well do just that. Further supported storage methodologies are to be implemented in future – so if your preferred solution isn’t there yet, it may well be soon. In case it’s something that you want to be able to do, you can also make an image to a locally attached storage device; if you happen to be using this methodology, you can use it to create a full .e01 disk image on Windows of a drive.
As you might imagine, squirting your data over the interwebs is not without risk – everything running back and forth is protected by TLS 1.3 with the appropriate certificates in place. Just in case you’re marginally more paranoid than this, you are also able to apply additional encryption and passwords on capture containers. As well as this encryption, the server is also busy doing all of the wonderful log management things that one would expect in a forensic oriented product – who’s done what, where to whom, etc.
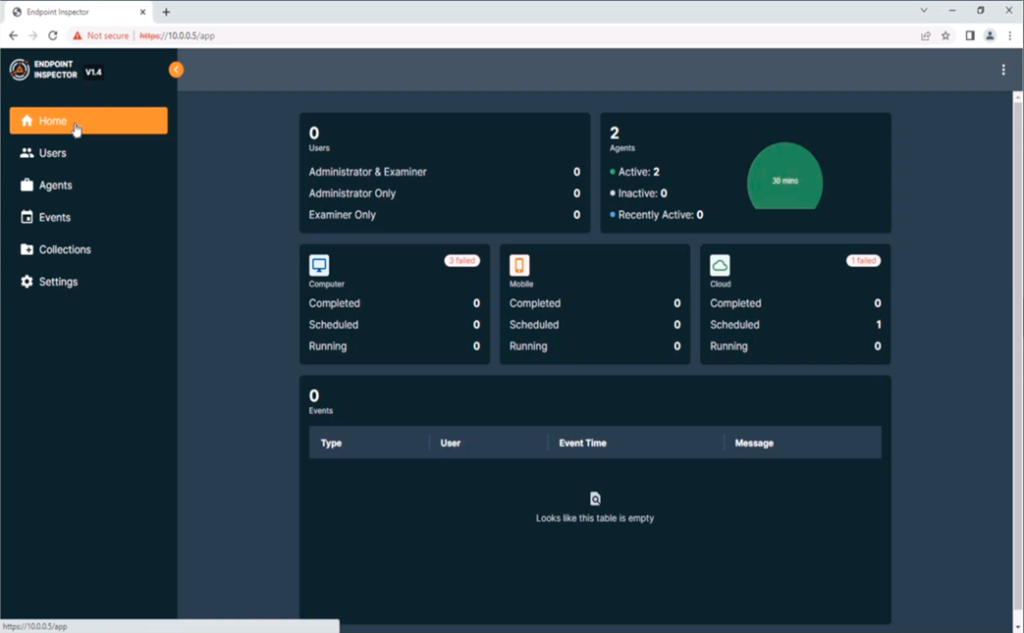
Figure 2: Home Page of Endpoint Inspector
Overall, the interface is clean and simple. At this iteration of the software, there are few choices that really need to be made, and thus configuration is straightforward. It’s a nicely designed and easy to navigate UI, and the UX is pretty good – not something that you can say about all forensic tools sadly. The product is undergoing a significant amount of development though, and I’ve been told that things won’t necessarily stay in the same places as evolution continues[1]. At the moment, it’s simple enough to get away with this, but I wonder if this might become more cluttered over time as features increase – only time will tell.
Computer collections are configurable – you can do some refinement of the things that you wish to capture, including file types and date ranges, and you can also schedule captures for a point in the future should you so wish. In the world that has the trusted employees, as discussed earlier, this means that you can schedule such collections out of hours so as not to impact upon network or machine performance for end users. In this same collection, you can specify the capture of volatile information from the memory on both Mac and PCs, a feature that I can see being particularly useful in the incident response arena – rapid remote acquisition of files and memory during an ongoing issue is one of those useful things.
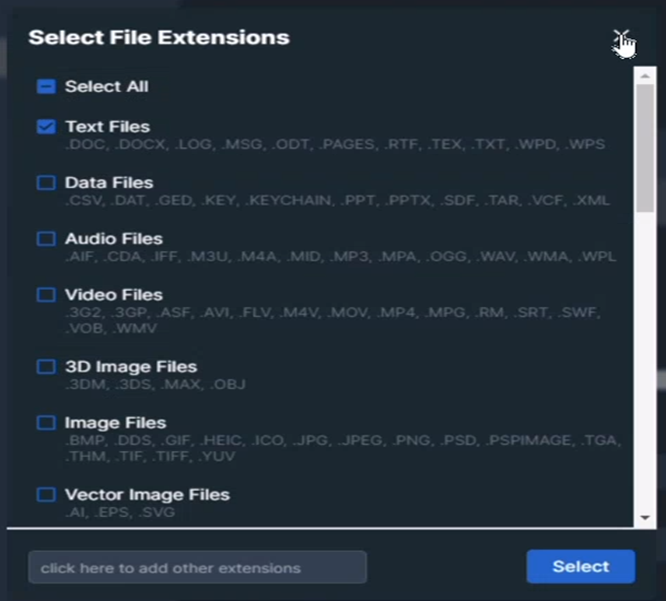
Figure 3: Select File Types for selective capture
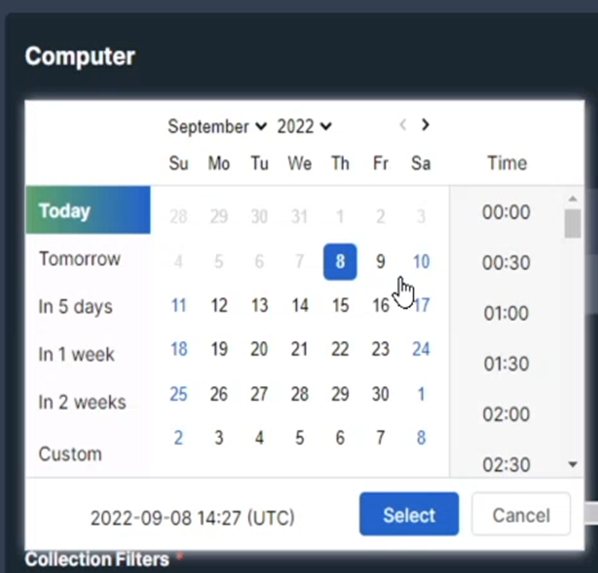
Figure 4: Schedule Capture Time
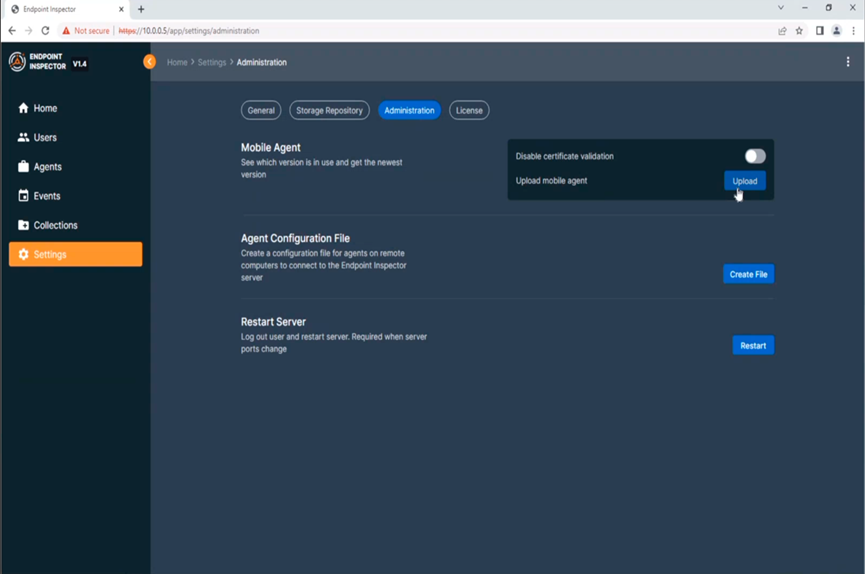
Figure 5: Some configuration options
That memory acquisition available on both Windows and Intel based MacOS computers, that, for the time being, is a limitation against the latest Apple devices on the M1/M2 chips, but, given the breakneck pace of change, I’m sure it will turn up in a version or two! The MacOS memory tools require that a system extension is installed (still signed by BlackBag Technologies Inc. I note – a smart purchase by Cellebrite there) before it can be used, which requires Security & Privacy system settings to be modified and a system restart. This isn’t an incident response tool for volatile data that you’ll be able to use without a little forward planning.
Whilst the computer acquisition is agent based, the mobile side of things isn’t. When the solution on the mobile side is the market leading Cellebrite suite of tools, this is somewhat understandable. Not only are you going to get better results, but the developers need only focus on providing the best product once. This does mean that “remote acquisition” as a definition gets a bit stretched – given that you need to plug the mobile into something else – but the other Cellebrite tools integrate with the Endpoint Inspector to pump all the data back to that central location from which the investigations side of things are then able to access it. To quote from my introduction to the tool given by Jeff Hedlesky, the mobile remote acquisition tool is “UFED boiled down so that it will fit on a cracker”. This is then easy to distribute to end-points for the process – and as Jeff rightly asserts, we’re all pretty familiar with the capabilities of UFED to do a good job.
There is a similar level of configurability as to the capture content on mobile as there is on the computer side – selection of file or media types – but scheduling is clearly not possible, as the device needs to be physically plugged in for the acquisition. That’s not to say that you have to suffer the bandwidth hit immediately though. Whilst the acquisition itself is dependant on the device, the upload of the image is not, and it can be comfortably cached on the acquisition endpoint and uploaded at a later time.
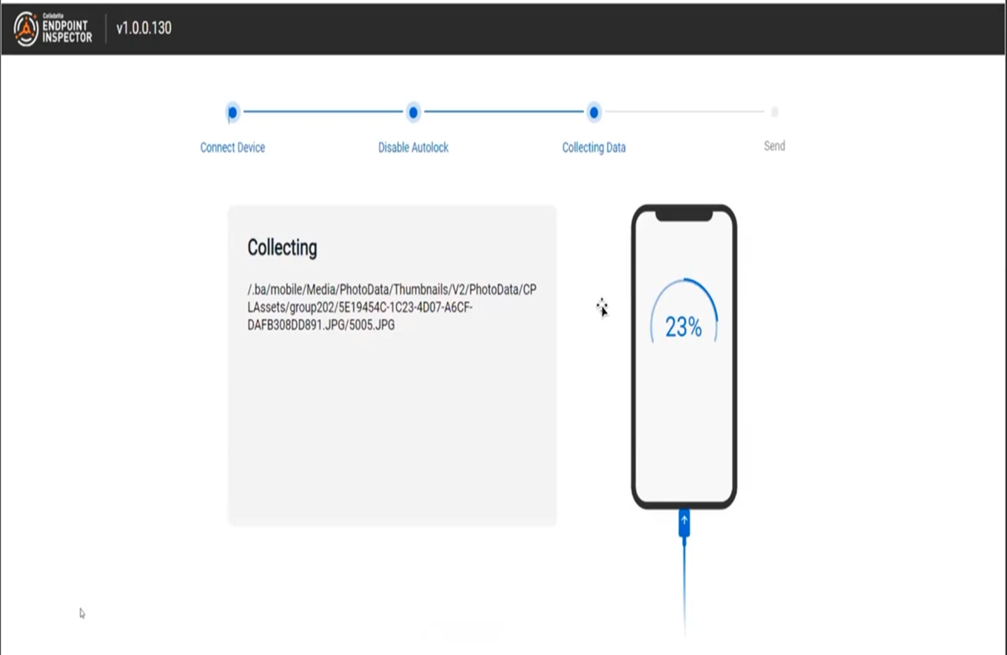
Figure 6: UFED based device capture
Unfortunately, this methodology for mobiles means that Endpoint Inspector’s other interesting party trick won’t work – but there is the possibility when using the computer client to carry out a live (“synchronous”) review of a client device. This was surprisingly sprightly over the network, and in many scenarios would be a hugely useful tool. The usual caveats apply with regard to doing data analysis on live systems though – things are in flux, and thus (speaking purely forensically), you’re standing in a river that’s never the same at two moments in time. So long as the examiner takes this into account, no one should get burned!
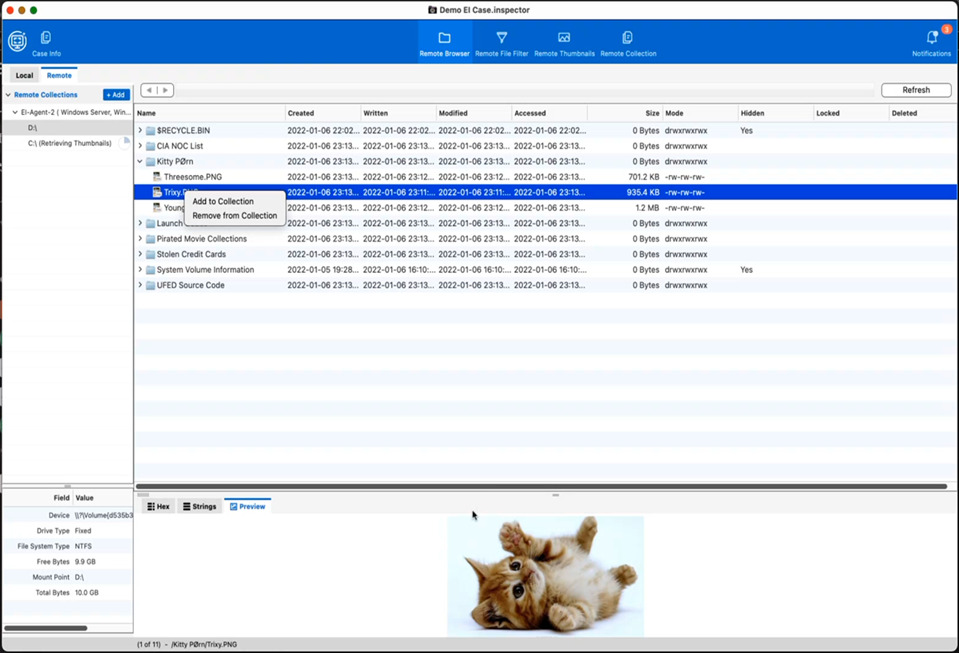
Figure 7: Live Analysis
EI supports the acquisition of data from what they call “Workplace Applications” on mobile devices. You’ll notice the usual roll call of suspects that you might expect – Google and Microsoft are both in there for example – and one or two that I hadn’t heard of – Box for Business and Egnyte. A nice feature in this is the ability to do what are effectively incremental collections – pulling down only the files that have been added or changed since the last imaging. On the cloud front, there is also support for collecting the last three months’ worth of WhatsApp data from a mobile device, along with three weeks’ worth of attachments.
To wrap it all up – Endpoint Inspector is a young product that does what it claims to. It currently isn’t cluttered up with bells and whistles, but actually I think that this is one of its finest strengths – it does what it is supposed to, and it does it without too much fuss and bother through a clean interface.
“…the height of sophistication is simplicity.” – Clare Boothe Luce
I hope that going forward it doesn’t succumb to trying to be too much and that it can retain its current simple but effective charm.
[1] Recommended reading from Jeff “Who Moved My Cheese: An Amazing Way to Deal with Change in Your Work and in Your Life”, Dr Spencer Johnson – https://amzn.to/3j1BeSx – because the interface is subject to change, because it’s young and developing.