by Jade James
Oxygen Forensics specialise in mobile device, cloud, drone and IoT data extraction. Oxygen pride themselves in giving law enforcement, federal agencies and enterprises access to data at top speeds, providing advanced digital forensic data extraction and analytical tools for criminal and corporate investigations.
Their flagship product, Oxygen Forensic Detective, allows users to extract, parse and decode data from different data sources.
Cloud Data Extractions
The built-in Oxygen Forensic Cloud Extractor allows investigators to gain access to cloud services such as iCloud (currently only possible with a known login and password, although token support will be added in the next release), Google Drive, OneDrive, Samsung Cloud, Huawei accounts and email servers. It can extract data from many other services such as Facebook, Twitter, Dropbox, and WhatsApp. The Cloud Extractor also acquires data, including voice recordings, from Amazon Echo and Google Home IoT devices. To complete these acquisitions, you will need to have available either account credentials or tokens.Mobile Data Extractions
Oxygen Forensic Detective (OFD) offers data extractions from iOS and Android devices, feature phones, smartwatches, SD cards and SIM cards. Using OFD, you can import backups and images including iTunes, Android, GrayKey, JTAG, chip-off, UFED and XRY. OFD uses proprietary methods to bypass or disable screen locks and automatically finds passwords to encrypted backups and images using a variety of decryption techniques.
Drone Data Extractions
Using the Drone Extractor option in OFD, you are able to parse and analyse data of physical dumps, flight logs, mobile applications and cloud services. You can also create and import drone physical dumps and parse GPS locations, route data and device telemetry (such as speed, direction, altitude and temperature). Various models of DJI Phantom and Parrot drones are supported by Oxygen. It is also possible to extract and parse data from the drone applications on iOS and Android devices, and from cloud services via login/password or token from DJI, SkyPixel or My Parrot clouds.
OFD JetEngine
This powerful built-in 64-bit forensic utility allows investigators to parse large volumes of data and make use of advanced analytical tools like Social Graph, which shows a user’s social connections and common contacts; Timeline, which shows all events in chronological order; aggregated contacts, which merges contacts from different sources; and Facial Recognition. Oxygen Forensic JetEngine parses and decodes data three times faster than other tools on the market, which is a great help when working with large datasets.
Oxygen Forensics’ software offers two types of licences for Oxygen Forensic Detective (OFD): Internet and USB Dongle. OFD supports USB cable and Bluetooth (Microsoft, Widcomm) connections. The software works on 32-bit or 64-bit versions of Windows 7, Windows 8 and Windows 10. The tool supports 5,703 Android applications, 4,372 iOS applications, 16 BlackBerry applications and 60 Windows applications. The full list of supported devices is available in the Help section of the tool itself.
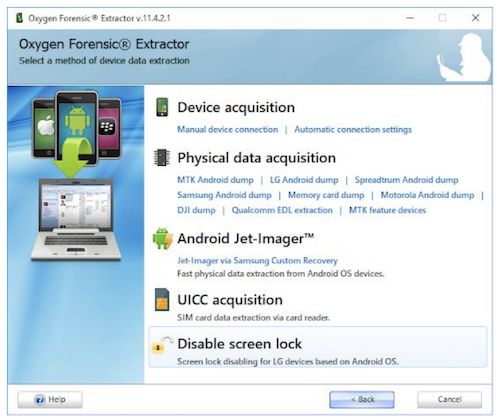
Once you have installed the software and the necessary drivers, it is very straightforward to perform an extraction from a mobile device. You can launch the Oxygen Forensic Extractor through Windows Explorer or launch it through Oxygen Forensic Detective by clicking on ‘Connect Device’. Here you will be presented with many options to perform extractions on different devices.
When you have selected the appropriate option, Oxygen Forensic Extractor will begin searching for the device automatically. You also have the option to search for the device manually in the supported device list. Once you have successfully connected the device, you can then enter more details about the device, the owner and the case.
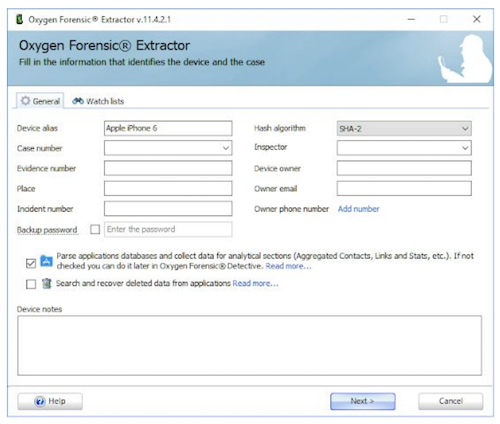
If necessary, you can enter a backup password. You also have the option to parse the applications database and collect data for analytical sections such as aggregated contacts, links and statistics, Social Graph, Timeline, and so on; but it is also possible to do this at a later stage, as it will save time in the initial extraction process.
When all the data has been extracted from the mobile device, you will then be prompted to either open the device to view the data, save the extracted device to a .ofb (Oxygen Forensic Suite file type) archive, or print/export a full device data report.
The process for the extraction of Android data is not as straightforward as extracting from an iOS device. When extracting from Android, you need to make sure that the device has been placed in Airplane mode; that there is enough battery power remaining to perform the extraction; that the device has been put into ‘Developer mode’; and that ADB (Android Debug Bridge) debugging has been enabled.
With the device I used, I had to go to Settings > About and tap on the build number of the device seven times, then go back to ‘Developer options’ and look for USB debugging and turn it on. You also have to accept the RSA key that allows the debugging. You are still able to extract basic data from an Android device, such as media, even if the device has not been successfully rooted.
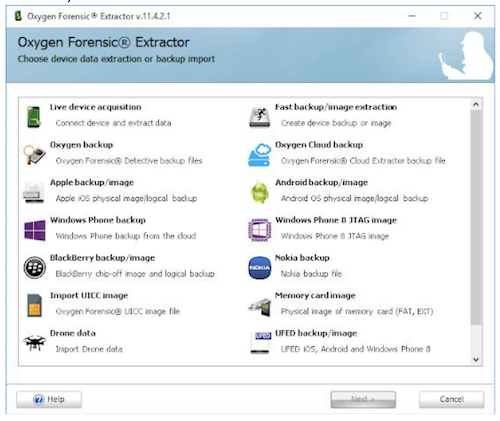
As well as extracting live data from devices, OFD gives you the opportunity to import various backups and device images which have been created using third party applications, such as:
● iTunes backups
● Various Apple backup/image such as non-encrypted .dmg images
● XRY DMG
● GrayKey extractions
● Windows Phone backups
● UFED backup/images
● Android backup/images
● BlackBerry backups
● Nokia backups
● Memory card images
● UICC (Universal Integrated Circuit Card) images
● Drone images
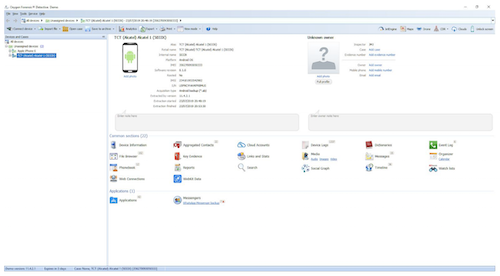
The Case Summary page will give you access to the all the data that was successfully extracted using the handy hyperlinks. A lot of the options from this page would have already been presented to you previously, but it is useful to have the options again if you need to add more devices to a case. You can also add information or notes about the device if you haven’t done so already. There are many ways of viewing the same data within the app, which is very useful.
Oxygen Cloud Extractor is available to use through OFD, and this allows the investigator to extract data from 69 different cloud storages — such as iCloud, Google, DJI Drone, Parrot Drone and SkyPixel Cloud data — using either account credentials or tokens. Oxygen can also find passwords and tokens from a user’s computer using the Oxygen Forensic KeyScout Utility.

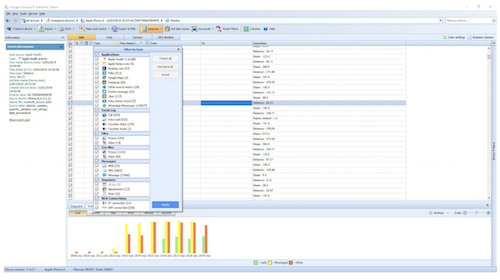
If OFD has already identified cloud accounts from a previous extraction, you can use the Oxygen Cloud Extractor to extract data from these accounts, or to target certain applications using known credentials or tokens. The extractor is useful as you are able to enter a specific date range and apply this to all the services you have selected. In my testing, I chose a few different services and some returned more successful results than others. Amazon Alexa, for example, returned particularly strong results.
Viewing messages from a device is as simple as clicking on the hyperlink which brings you to the ‘Show Messages’ page. From there you can view all SMS and MMS messages that have been sent, received and deleted (all deleted messages would be highlighted in blue and are marked with a basket icon). You can filter the messages by selecting iMessage, MMS or SMS; and there is an option to view whole conversations, which allows you to view conversations between individual contacts. You can filter the view so that you can see messages from specific folders, such as the inbox or the sent folder.
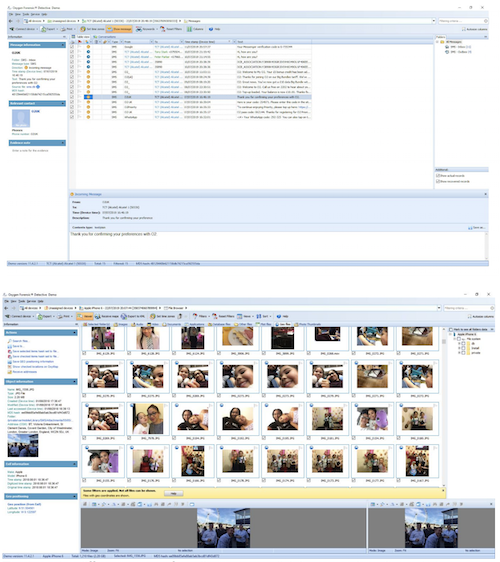
To show the different types of media, you can click between the tabs and choose to view images, audio, video, documents, applications, database files, plist files, geo files, or other files. A great feature of OFD is that you can save selected items as a hash set and then export it for use in another application. Geo files lets you view media which has exif data attached to it and gives you a lot of useful details, such as where the photo was taken.
The majority of the audio files I was able to extract from Android and iOS devices mainly consisted of voicemails and voice notes from WhatsApp, and I found these very valuable.
.opus files were unable to play in OFD, but when I double-clicked on them I found you can open them to play in a compatible application.
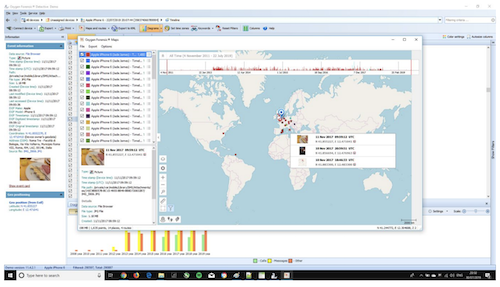
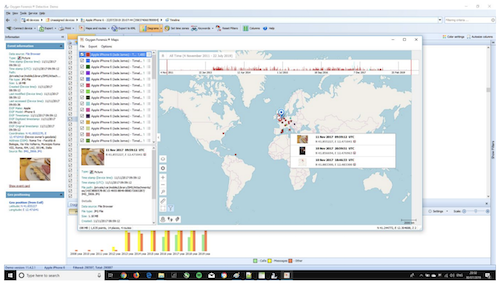
Viewing the Timeline for the iOS device allowed me to see all the event information. This section organises calls, messages, calendar events, application activities and web connections in a chronological way so that it is easy to analyse the data, without having to go to different pages within OFD. You can also view Oxygen Maps data in Timeline: this will display the data over geographical locations, so that you can see a visual representation of where and when data was sent or received.
The aggregated contacts screen allows you analyse contact information from different sources such as contacts, groups, phonebook, messages, event logs, various messengers and apps, and other social networks. It also shows cross device contacts, which may appear on multiple devices. Another handy feature is the ‘groups’ view which shows contacts that have been placed into specific groups in various applications.
There are a lot of different ways to view the same data within Oxygen Forensic Detective, but the tool manages to present the data in many different ways without it becoming overwhelming.
There is a lot of great functionality within this tool, and even as a practitioner I found it fascinating just how much data can be extracted and viewed in OFD. The simplicity of the tool means that it is fun to use and easy to navigate around all the sections and applications. Making connections between data and devices is also extremely intuitive.
In summary, OFD is very effective and straightforward, requires little training, and is very easy to set up. There are a huge wealth features which are advantageous to an investigation. Oxygen Forensic Detective is an essential tool for mobile device extractions for any digital forensic investigator or practitioner.
Find out more and order Oxygen Forensic Detective at oxygen-forensic.com.
About The Author
Jade James BSc (Hons) is currently a Digital Forensic Investigator at the Serious Fraud Office. She has previous professional digital forensic experience from working at IntaForensics, the Home Office Centre for Applied Science and Technology and the City of London Police. Jade has gained experience from conducting computer, mobile device examinations and drone forensics, and has been involved with ISO 17025 & Quality Standards both as a Digital Forensic Practitioner and Quality Manager.