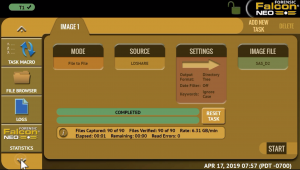
How To Launch 18 Simultaneous Wiping Sessions And Reach 18TB/h Overall Speed With Atola TaskForce
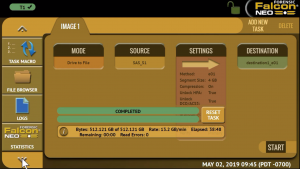
Thanks to its ability to perform 18 simultaneous imaging sessions, TaskForce is the most capable evidence acquisition in the forensics market. Atola’s team of engineers have equipped the device with a server-grade motherboard and CPU, thus allowing TaskForce to multitask