Passware Kit 2022 v2 – Password Recovery for bcrypt Hashes and OpenCL Acceleration on macOS
What’s new in Passware Kit 2022 v2:
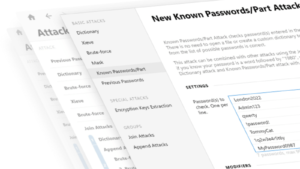
Password recovery for bcrypt hash
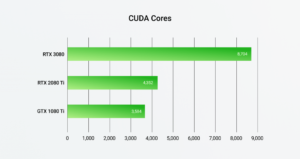
Passware Kit for Mac with GPU acceleration support
QuickBooks 2022 support
Windows Hello protectors bypass for Windows 11
OneNote Revision Store support
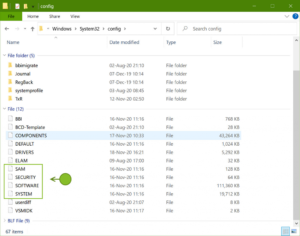
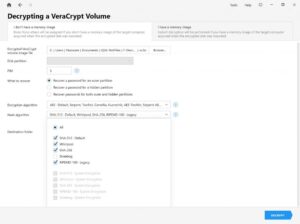
FDE decryption improvements
Password recovery for