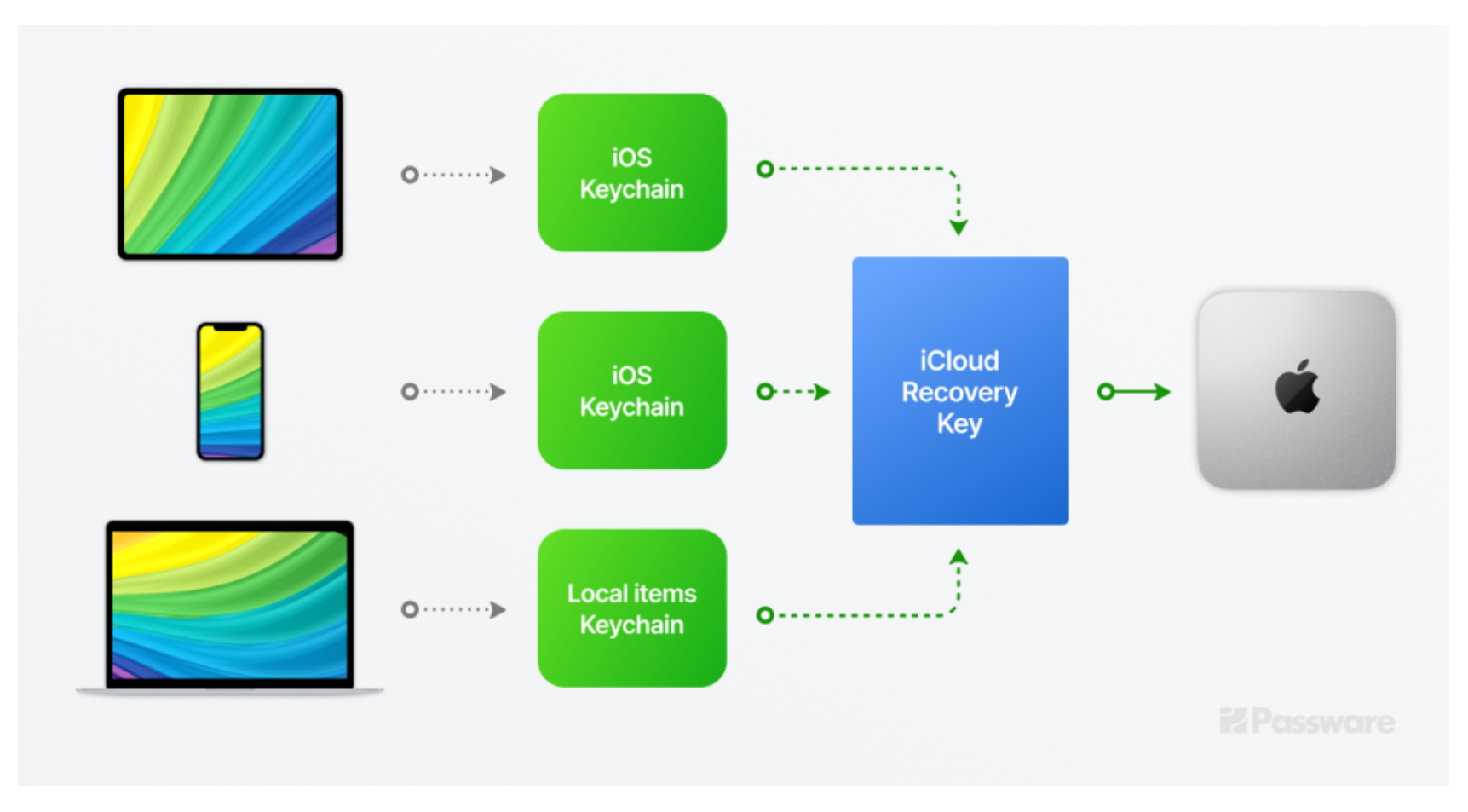
When it comes to the forensic investigation of Apple devices, a Keychain analysis is of particular importance. Not only does Keychain contain passwords from websites and applications, but it can also provide computer forensics with access to the same user’s other Apple devices. Let’s take a closer look.
Types of Keychains
Keychain or Keychain Services is the password management system in macOS and iOS. It stores account names, passwords, private keys, certificates, sensitive application data, payment data, and secure notes. These records are dynamically linked to users’ particular login passwords so that, when they log on to a Mac device, all of their various accounts and passwords are made available to the operating system and select applications.
The Keychain storage is located in:
- ~/Library/Keychains/ (and subfolders)
- /Library/Keychains/
- /Network/Library/Keychains.
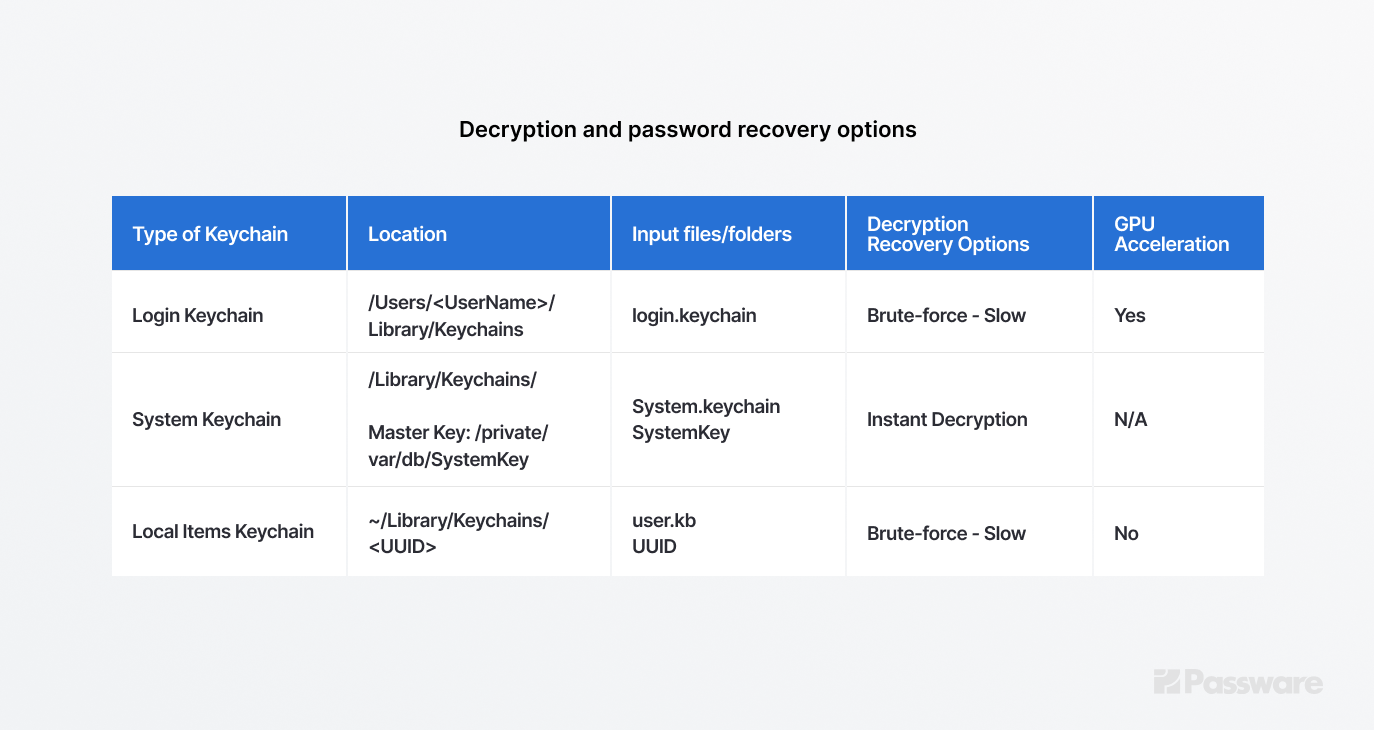
There are three types of Mac Keychains: Login Keychain, System Keychain, and Local Items (iCloud) Keychain.
Login Keychain
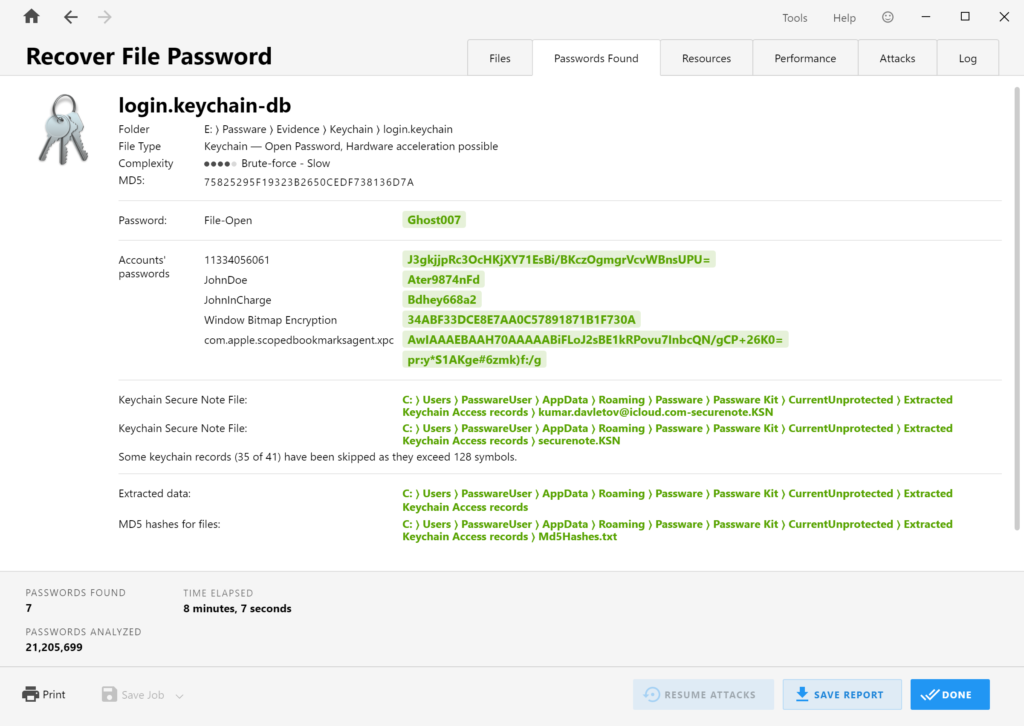
The Login Keychain is the default Keychain file that stores most of the passwords, secure notes, and other data. The data is stored in a file named login.keychain located in /Users/<UserName>/Library/Keychains.
By default, the Login Keychain password is the same as the Mac user password.
The password recovery process for this Keychain is time-consuming, but it can be accelerated by using GPU, reaching speeds of up to 1,200,000 passwords per second on an AMD 6900 XT.
System Keychain
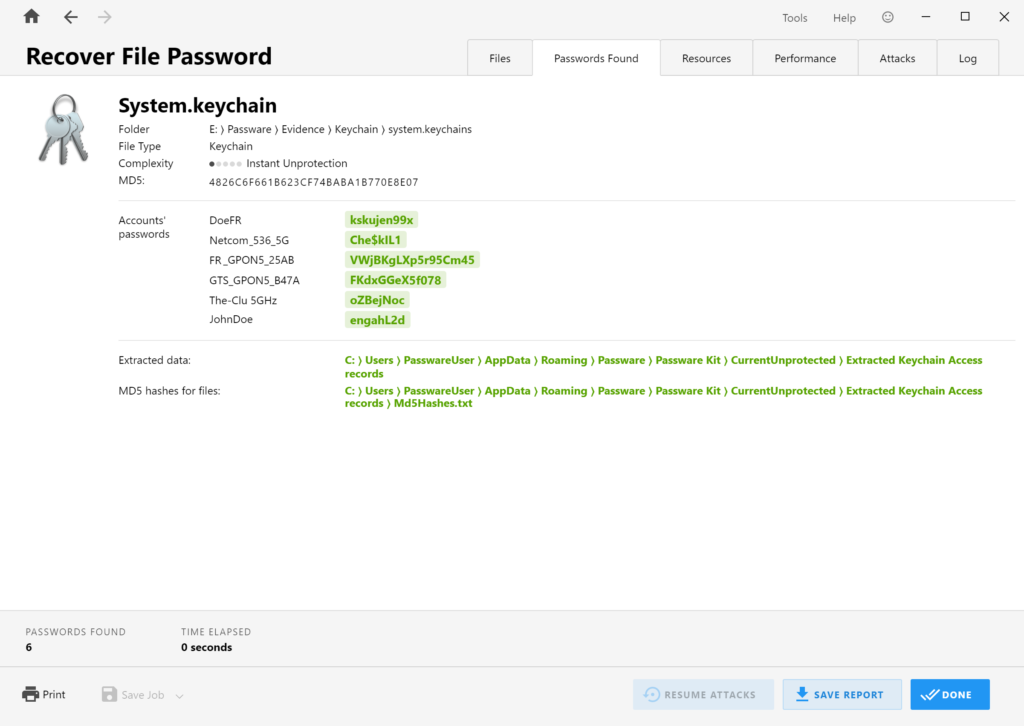
The System Keychain stores items that are accessed by the OS, such as Wi-Fi passwords, and shared among users. The file, which is usually located in /Library/Keychains/, can be decrypted instantly if a “Master Key” file is available (usually located in /private/var/db/SystemKey).
Local Items (iCloud) Keychain
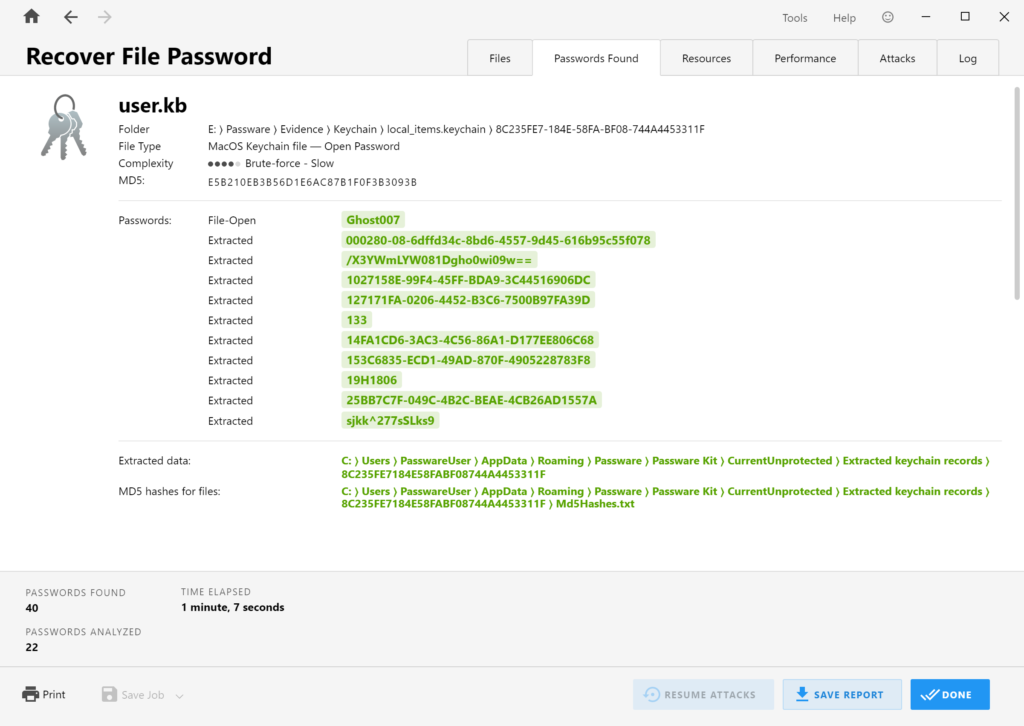
The Local Items Keychain is used for keychain items that can be synced with iCloud Keychain. It contains encryption keys, applications data, webform entries, and some iOS data synced with iCloud. It presents two files: a keybag (user.kb file) and an SQLite database with encrypted records (keychain-2.db). If the iCloud synchronization is turned on, the keychain-2.db may contain passwords from other devices as well. Passware Kit recovers a password for the user.kb file and then decrypts the keychain-2.db database. By default, the user.kb password is the same as the macOS user password.
To recover the user.kb password on a Mac without a T2 chip, Passware Kit requires the 128-bit universally unique identifier number (UUID), which is the same as the name of the Keychain folder. Unfortunately, the password recovery for Local Items Keychain cannot be accelerated on GPU. After the successful recovery of a password, Passware Kit extracts all records that appear readable and saves the rest of the data in a file. Strings shorter than 128 symbols are considered passwords and saved to a Passwords.txt file, while json and bplist binary files are extracted as-is. Passware Kit also creates an extracted-records.json file with the complete extracted data.
Use Cases
It is extremely important to analyze as many Apple devices linked to the same iCloud account as possible. A decrypted Keychain from one device can gain entry into a device with stronger encryption, such as a Mac with a T2 chip.
If there are no additional devices to extract the Keychain from, Passware offers a T2 Decryption Add-on to decrypt APFS disks from Mac computers protected with an Apple T2 security chip.
Read the full article to see the cases in which Passware Kit facilitates the extraction of data from locked devices.
Summary
The table below summarizes the decryption and password recovery options for different types of Keychain.
A comprehensive forensic investigation involves the analysis of multiple devices and artifacts. Starting from the least-secure devices (e.g., memory images, iTunes backups, and Macs without T2/M1 chip), Passware Kit extracts and decrypts a Keychain that can then be used to access data from other devices.
Learn more about Passware Kit Forensic capabilities and the best practices on the Passware Knowledge Base.