Good evening. My name is Evangelos Dragonas and today we’ll talk about the Forensic Analysis of Xiaomi IoT Ecosystem. Before I begin, let me introduce myself. I live in Greece where I work as a digital forensics examiner. Currently I am finishing my PhD in the area of IoT forensics at the University of Piraeus, here in Athens. In my free time, I conduct DFIR research which I typically sell at my research blog, namely, atropos4n6.com.
I’m feeling honored to announce that the research article I wrote with two colleagues of mine, Alexandros Vasilaras and Dimitrios Katsoulis, is now one of the three finalists for the world of the DFIR Article of the Year category at this year’s Forensic 4:cast Awards. If you haven’t done it already, please cast your votes at the link you see in my slide. And with that, let us begin by talking about Xiaomi.
Xiaomi one of the world’s biggest manufacturers when it comes to smartphones and IoT solutions. It is safe to state that some Xiaomi devices are becoming more and more likely to appear in our smart home investigations. Xiaomi is also really popular in Europe and is coming to the US, as well.
And now let’s see some Xiaomi IoT statistics. As you can see, Xiaomi closed the fourth quarter of 2020 with more than 324 million connected IoT devices. This number is really big and it’s continued to grow up to this day, but what devices does this number include exactly?
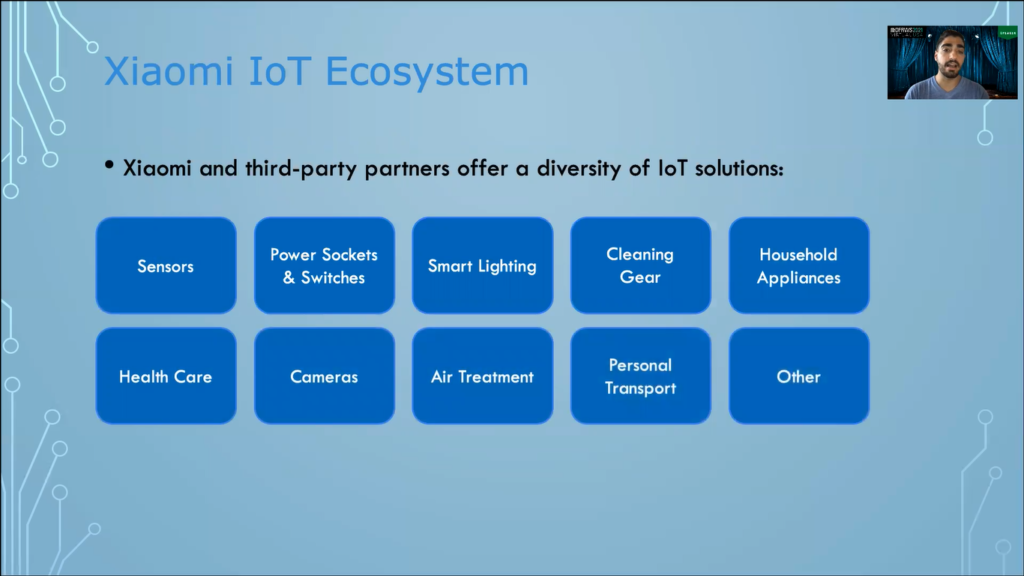
Well, Xiaomi and third-party manufacturers with which Xiaomi has partnered; like Mijia, Aqara, Yeelight and more; together they all offer a diversity of IoT solutions, which include; sensors, smart lighting, household appliances and more. Out of all of these categories, I chose a representative subset of IoT products for my research, which I will present during the following section, where I will discuss the equipment I use and my setup.
So, for my research, I use all of these devices. Due to the limited time I have, I will present you artifacts obtained for the forensic analysis of the devices in the red box, which, along with the Mi Home Security Camera, together they comprise Xiaomi’s IoT security bundle.
So, the Mi Door and Window Motion Sensor and the Wireless Switch, they communicate with the control hub or the central unit of our smart home security system via ZigBee protocol. For my research, I also used Xiaomi’s RedMi Note 6 Pro smartphone with Android 9, which was rooted.
In order to control these IoT devices, I used Xiaomi’s corresponding Android application: the Mi Home application. I tested several versions of this application, with the latest being the one you see in my slide, which happens to be the latest version available for download from the Play Store.
Of course, both the Mi Home application and the control hub, they are used to put input data to Xiaomi Cloud services, and more specifically, to my Mi account.
This is my home. All of the devices were assigned to my home and transformed it into a smart home. I use a smartphone application to control these devices which I used for a period of two months, approximately. From time to time, I changed some settings in order to perform a more complete forensic analysis.

And now let’s talk about the evidence extraction. Before extracting the evidence we need first to identify all the potential sources of evidence.
In my research, the first potential source of evidence that comes to mind is of course the smartphone application. Then we have the Xiaomi Cloud services.
Following the IoT devices themselves, not all of the devices, but some IoT devices store data locally and can be found useful in smart home investigations.
Next we have the local API. Actually, this only applies to the Xiaomi Mi Smart Speaker. And last but not least, we have the network traffic, which can be found really useful, especially if we conduct cyber crime investigations.
Again, due to the limited time I have, I will only talk about the forensic artifacts obtained from the forensic analysis of the smartphone application.
So, in order to extract the evidence from the application, I used the following procedure:, I turned airplane mode on on my smartphone, I didn’t clear the Hi Home application cache after I used the application, and I used ADB commands to retrieve the data from the smartphone application.
And now for the forensic analysis. Before presenting you the artifacts obtained for my forensic analysis, I would like to give you an overview of the Mi Home application.
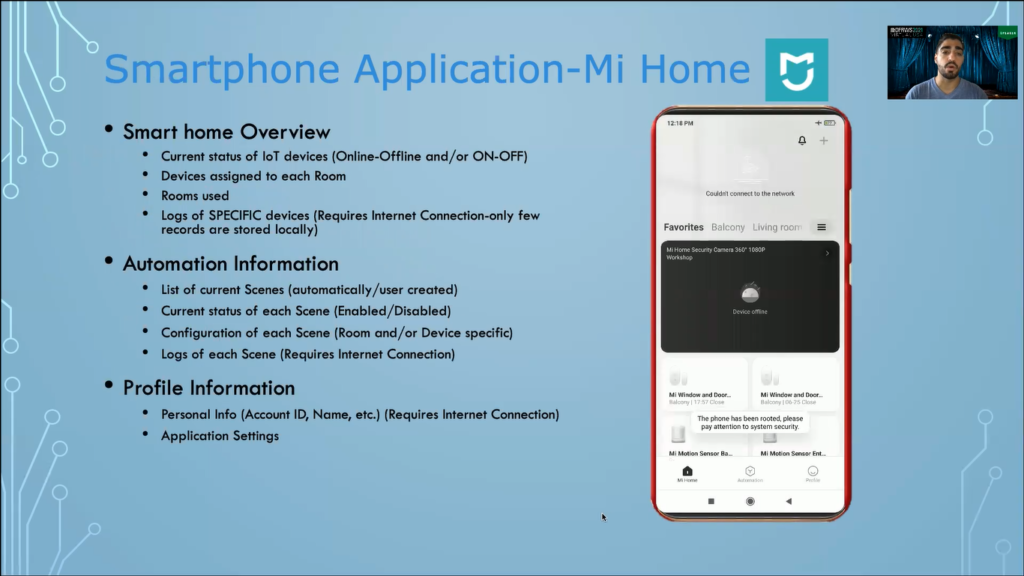
So, if we enter the Mi Home application we’ll get a smart home overview. We will get the current status of IoT devices on my smart home, which devices are online or offline, which of them are turned on or off. We can also see which devices are assigned to each room and therefore which rooms are used in my smart home. Lastly, we can retrieve logs of specific devices. As this information will require an internet connection, only a few of these records are stored locally.
Next, we can find information about the automation system of my smart home. So, we can see a list of all the current Scenes, which of them are enabled or disabled, and if we tap on a Scene, we will see its configurations, which rooms does it include, and which devices are involved in it.
Again, we can retrieve logs of each Scene, which means when this Scene was triggered, but this would require an internet connection, and as you can see here, we’re in airplane mode and none of this information is available. Lastly, we can see the profile information of the user of the smart home. This information again needs an internet connection in order to be retrieved from the Cloud services, so it is unavailable when in airplane mode.
And now, let’s see the full list of artifacts obtained from my forensic analysis. So, for the account, under the database directory, there is this [inaudible] database which under the shared user table we will find the email of the user, the nickname, the phone number, the shared timestamp, and the unique user ID.
So, the shared timestamp, what does this mean? We can choose to share the control of our smart home with other Mi accounts. So, if the user has opted to share the control of his smart home with other Mi accounts, here we have when he chose to do so. So, identifying that is useful and can be found under the shared prefs.
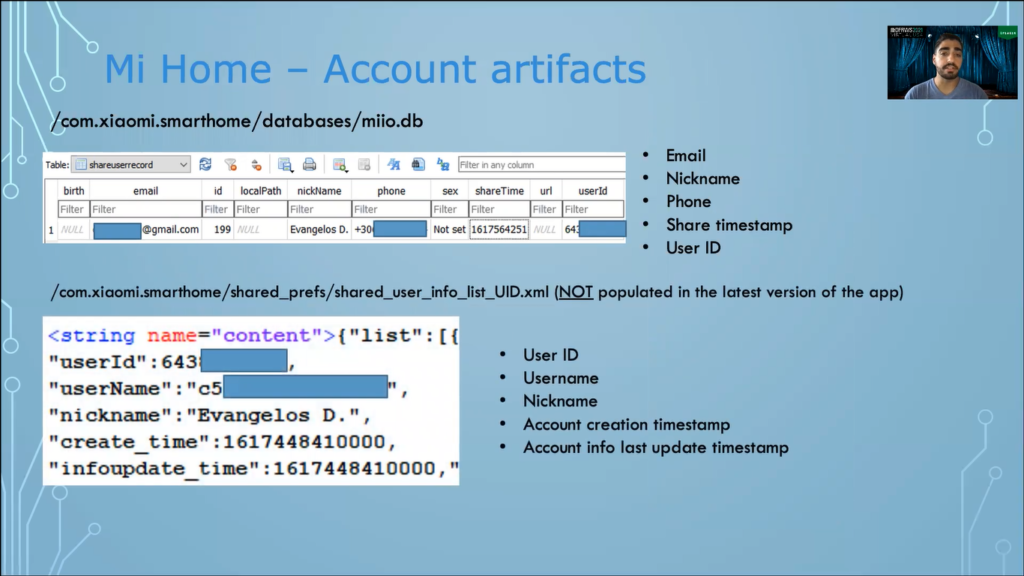
So, this XML did not hold this information in the latest version of the application, but I found that it was populated with this information in earlier versions of the application. So here the most important artifact that can be retrieved is the account creation timestamp, so we can learn when the account was first created. And this is how the personal information looks from within the application.
Next, let’s see what we can find out about the smart home. So, under the shared prefs directory, there is this XML file. And within it, we can find the unique ID of our smart home; its geolocation, if the user granted location permissions, well, in my case, I didn’t; and next we can find the smart home name and we can retrieve some information about the rooms of our smarthome.
So, the room names, the rooms’ unique IDs, when was its room created, which devices are assigned to it, and if a particular room is shared with other Mi accounts. So, not only can we share our whole smart home, but we can choose to share individually a room of our smart home. So, this is how the home name looks from within the app.
And now for the automation system of our smart home, what we retrieved is this. So, under shared prefs there is an XML file, which begins with MD5, has value of the user ID, and then followed by the scene_list_cache, which includes some important artifacts about the automation system.
So, we can retrieve information about current Scenes, the Scene number, the Cene ID, the unique user ID, who created the Scene, the Scene name, and when was the Scene created, and we can also find out the configuration of each Scene. One point of consideration here, no Scene’s logs are stored within this file, as this information would require internet connection and it is unavailable when we are offline.
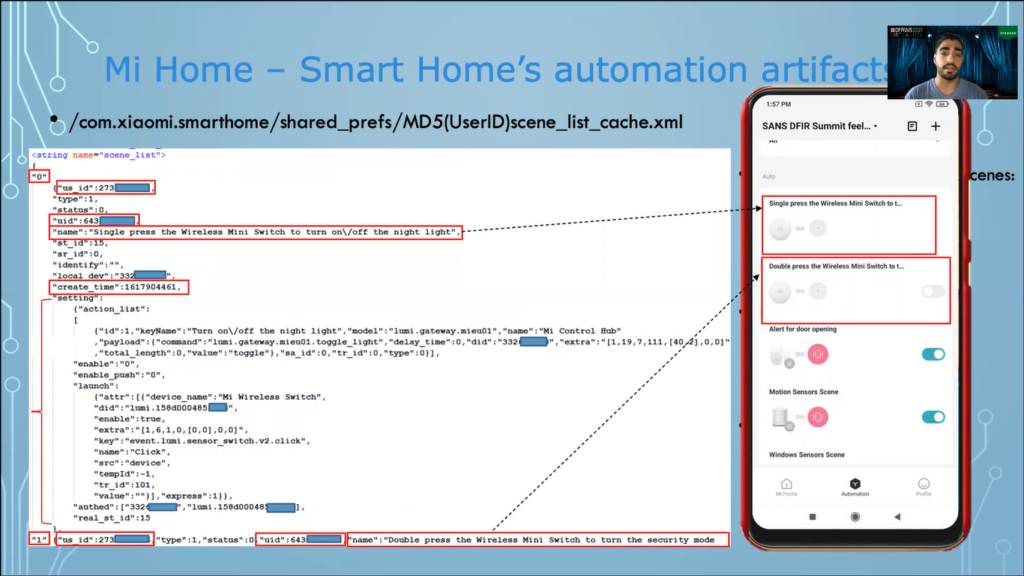
These are the Scene names, how they’re the depictions from within the app. And if we tap on a particular Scene, we can see its configuration, its [inaudible] and its action list.
Next, when it comes to IoT devices, under this directory, we will find one or more folders. Each folder represents a specific IoT device type. If we open this folder, for example, within we will find two sub-folders. If we open the numerical sub-folder, within we will find files that reveal which device type this folder refers to.
So, in this case, if we open the model_list.json, we will find out that this folder represents these motion sensor devices. Whereas if we open the data sub-folder, within we will find one or more folders.
What does this mean? This means that we have one or more devices of this device type in our smart home. So, in this case, I have two motion sensors in my smart home. If I open the first folder, within we will find a data sub-folder and within it, a config.XML file. This file is the device log file, and it will store any offline records of the device.
So, the Mi Motion, Door and Window Sensors and the Wireless Switch, for all of these devices, the config.XML files are fixed in size at about 3KB, and they will only store then 20 latest events recorded by each device.
So, for the Motion Sensor, as you can see, this is a config.XML, and we have the occurrence timestamp. This is actually when the event was recorded by the device. They Event type, here we have motion detections and when was this event stored within the conflg.XML.
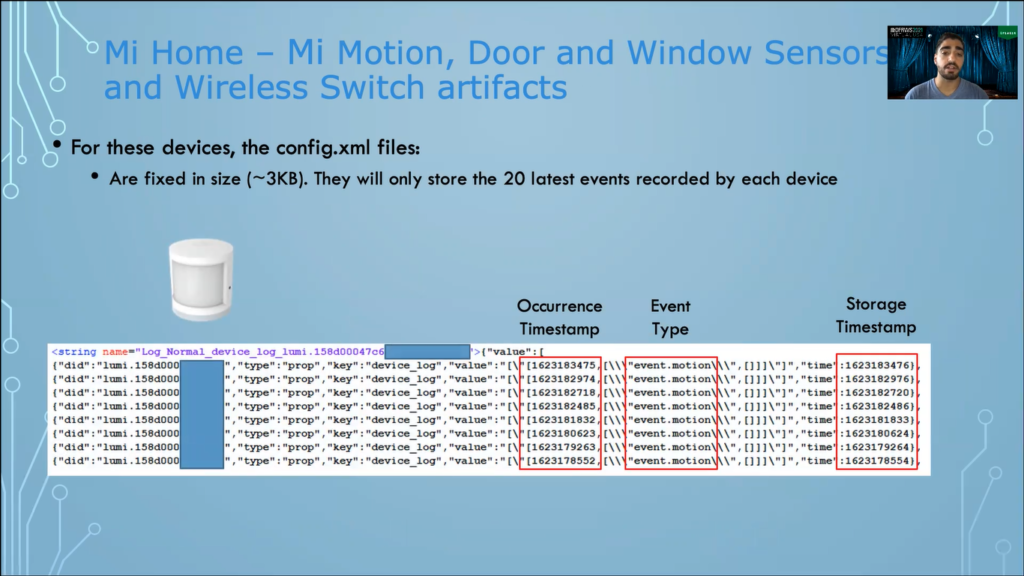
To the same extent, then Mi Door and Window Sensors hold the same data. The only difference here is the event type. And the same holds true about the Wireless Switch. Once again, the only thing that changes is the event time. And this is how the events look from within the app.
Moving on. So, the Control Hub, our central unit of our security system. The config.XML file stores specific information about this device; including the guard status, is the security enabled or disabled; the guard settings, which are the light conditions and the sound that the user has chosen; and which devices are currently paired with the control hub; and we can also retrieve the alert log.
So, this is a config.XML. As you can see, the guard status is off, we can also see the latest cache log that the device has recorded. And if we tap on the alert log, we will find the rest of the records there.
Okay, and those are the artifacts of our forensic analysis. Now, some findings and points of consideration. So, as you can see, Xiaomi IoT Ecosystem is an under-researched field of IoT forensics, which can be really valuable in current or future smart home investigations.
This forensic analysis of the Mi Home application can provide information about the smart home’s structure, the smart home’s automation system, and the smart home’s devices’ logs and/or settings. And of course we can retrieve the owner’s personal information, which is really important for our investigations.
And some points of consideration if you are conducting Xiaomi smart home investigations. So, config.XML file’s content depends on the device type. What does this mean? This means that for some devices, it may not exist. For some devices, it may only store settings or other information about the device. For some devices, it may store logs of the device.

So, most logs, as I previously mentioned, will reside in the Cloud. This means that if you pull some data from the Cloud using the application, typically this data will remain available until you exit the application. So, consider taking pictures of the smartphone screen, as some of this data will not be available if the internet connection is lost.
If any Bluetooth devices are present in the smart home you’re investigating, please make sure to connect to them, pull their data and take pictures of that, especially if you’re only investigating the smartphone application.
And now, to conclude, I will give you some references. So, the first two references, I found them really useful when it comes to Xiaomi IoT forensics. And then there is my Github account, where you will find Python parsers for the majority of the config.XMLs that you will find if you conduct Xiaomi IoD forensics.
I would like to express my special gratitude to my supervising professor, Mr. Costas Lambrinoudakis from the University of Piraeus for his support and guidance throughout this research. Without him, I would probably not be here today with you. And with that, that is all from me. I would like to thank you all for watching, and I wish you a great DFRWS conference. Goodbye.















