Julie: Hi, everyone. Thanks for joining today’s webinar: Windows 10 Activity Timeline: An Investigator’s Gold Mine. My name is Julie O’Shea and I’m the manager of global marketing here at BlackBag.
Before we start today, there are a few things we’d like to review. We’re recording this webinar, so we’ll share an on demand version when the webinar’s complete. And if you have any questions, please submit them in the questions window, and we will answer them throughout and in our Q&A at the end of the webinar.
I’m excited to introduce our speaker today. Dr. Vico Marziale. Dr. Vico is a senior digital forensics researcher here at BlackBag, where he is responsible for R&D supporting all of our software offerings. He holds a PhD in digital forensics, and over the years has done forensics and general cybersecurity work, written open source tools, and delivered presentations at trainings and numerous venues across the US and internationally.
Thanks for joining us today, Vico, and if you’re ready, I will hand the reins over to you to get started.
Vico: Thanks, Julie, welcome everyone to a deep dive into the Windows 10 activity timeline, which you can tell I’ve changed the name of the presentation. So what are we talking about? Basically, you’ll see documentation all over the place about the activity cache, the Windows timeline activity feed, Windows activity feed, Windows activity feed cache timeline. They all refer to the same thing. It’s a used for actual users to record what they’ve been doing and make it easy for them to see what they’ve been doing recently, and to pick back up those activities.

So editing documents or URLs, and this stuff is not just on a single machine necessarily. You can pick up activities across your laptop or tablet, phone, even across operating systems, as we’ll see. The basic basics are, you can get somewhere between three and 30 days of history of what a user’s been up to depending on settings, which we’ll get into. And the basics of what we get is really, it resolves around applications that were run and what files and URLs the application was touching. And when the user was actually actively engaged with the app, plus a bunch more things, as we’ll see.
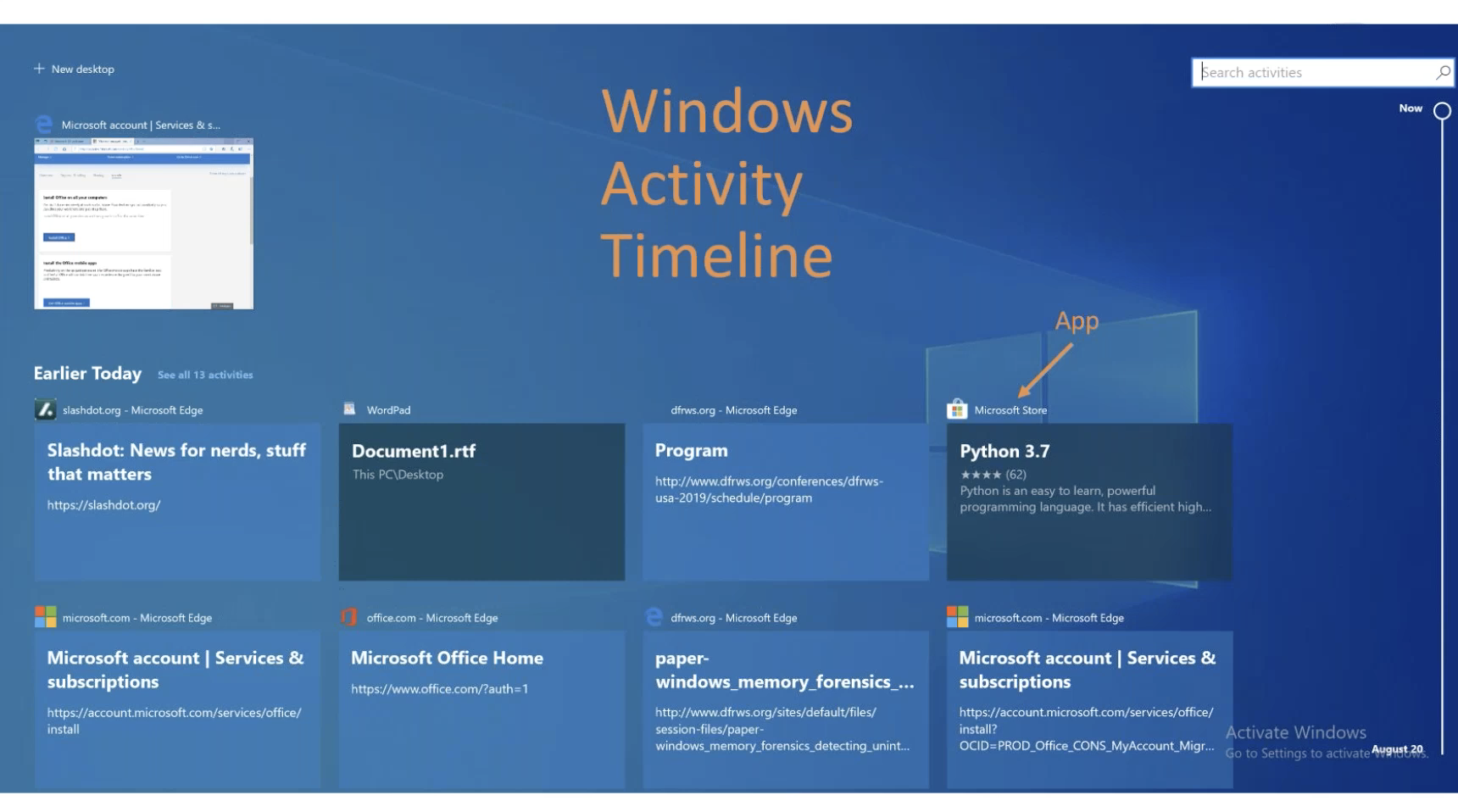
So, start from the very beginning. If you click the button in Windows 10 after 1803, or 1803 or later, you’ll get this bunch of boxes show up in the UI, which are current and past activities that this particular user has been up to. We’re going to look at these pretty closely.
So first and foremost, these things are called tiles. So anytime in the rest of the talk, when I refer to a tile, any one of these boxes is referred to a tile. If we look at where the tiles are and what they mean, you can have tiles for our current activities. These are windows that are currently open on the machine that they user is actively using. You can also have previous activities, like from earlier today, or from farther back. And these go all the way back to August 20th. And this screenshot is from around September 20th. So there’s about 30 days of history here.
So what kind of history are we talking about? Well, it’s applications and what they were doing. So first off, we see that this tile has WordPad up top, the application that was being used, and inside of the tile is document1.rtf, which is a file that was opened by Word Pad earlier today on whatever day that was, you can also see things like URLs. And this other time we have Microsoft Edge opened up to a URL of a conference that it was looking at for papers. And in addition to things like URLs and files, you can also have other things that are application specific. So here we see the Microsoft store app, with me looking at downloading Python 3.7, to download onto a machine. So all kinds of fun stuff here.
There’s also a search bar. You can search across all of these tiles to find activities that relate to something that you’re specifically interested in. And if you play with it enough, you’ll see that there are things that will appear when you search that may not appear by default. So this was the first of many hints that this pretty interesting facility is storing way more information somewhere in the OS than we’re actually actively seeing in this interface.
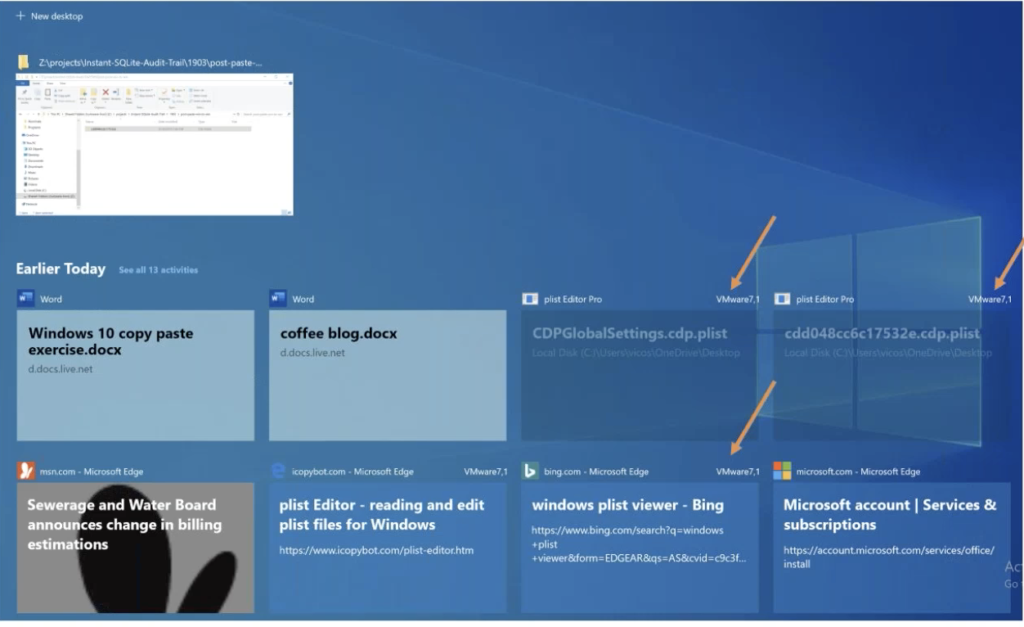
This is just a little teaser for a little later, when we’ve looked at the applications and the files that they access. And this looks just like those previous screenshots, but there’s another little piece of text over here that says VMware 71. We’re going to talk about what this is later, but just kind of put it under your hat for a second.
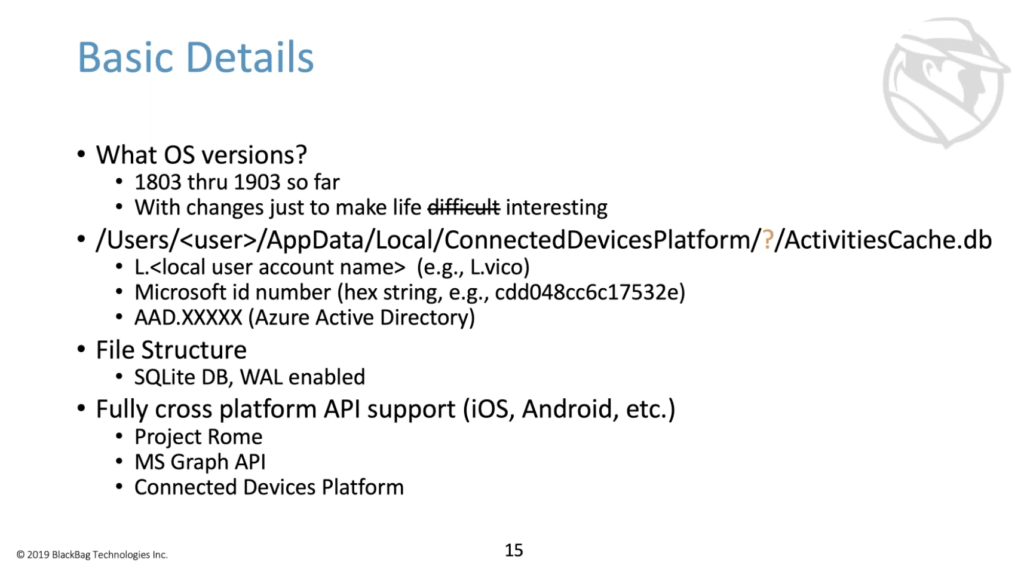
So basic details that are a little bit less basic. This appeared in Windows version 1809. It’s still in 1903. I haven’t gotten to look yet at the 1908, or whatever’s coming out at the end of this year. There were changes in how it functions, and a little bit of how it’s stored, just to make life particularly interesting over time. There were a few files, but the ones that we care about most are under Users and then username’s home directory, app data, local connected devices platform.
You’ll see a lot of nomenclature around connected devices platform, because that’s one of the underlying technologies that makes all this thing happen. And then the question mark here in this path is because, depending on the type of account that the user is logged in with, that folder name can have a different format. So if the user is logged in with a standard local account, like if I logged in with my own local account, then that folder would be named L.Vico. The user, if he’s a logged in with a Microsoft account, we’ll get this hex string, that’s a Microsoft ID. And if the user is logged in with an Azure active directory account, then the folder will look like AAD. and then some numbers and stuff.
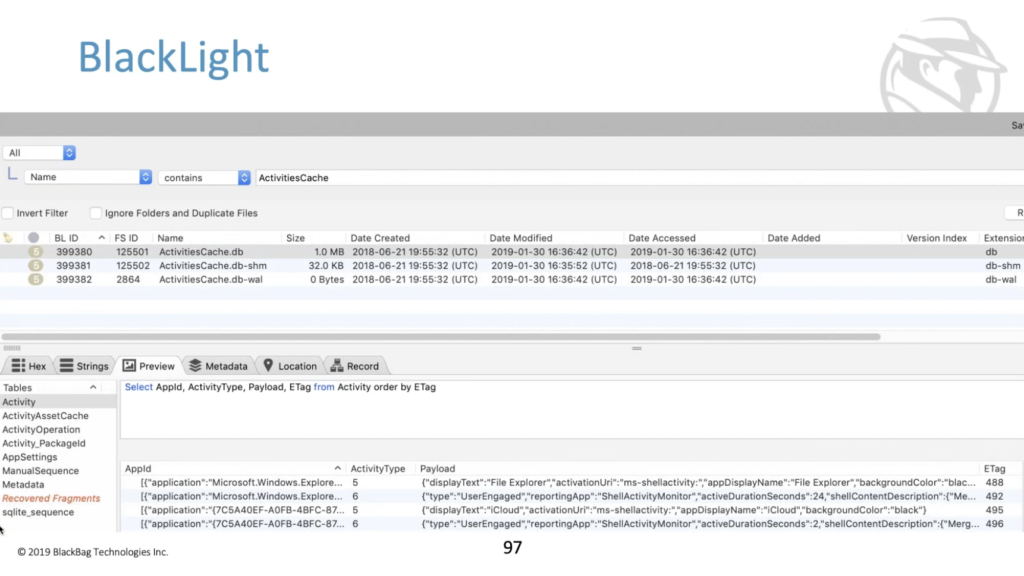
But one way or the other inside of this folder, the main thing that we care about are twofold. There’s some configuration files, and there’s also a database, the activities cache.db, that’s where all of the good stuff is. It’s important to note here that it is wall enabled, and that the wall was actually configured to be pretty big. So if you’re analyzing these databases and you export them, make sure that you export the right ahead block too, and that the tool that you’re using is reading the right head block as well ahead.
This thing, as we’ll get into over time, is fully cross-platform. So we’ll see that there are bits and pieces of this amount of stuff that you can see from iOS or Android, and from multiple versions of Windows 10.
The Microsoft ID part, if you want to be able to resolve that back to the username that was logged in, you can look in the NTuser.dot that relates to this particular user and look at this particular key and this user extended properties key, and you’ll see that the CID pointed to on the right, the CDD048 is the same as the one that we saw on the previous slide, and that’s me logging in with my very wittily named vico.scenario test account.
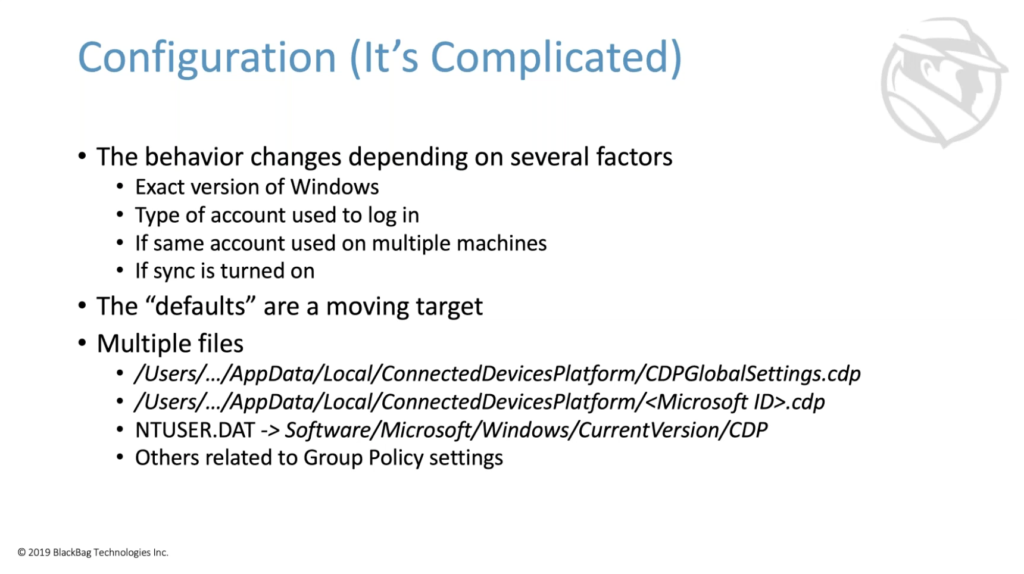
So we get to spend a few minutes on configuration, even though it’s not the most interesting in the world sometimes, but it’s important to understand how this piece works to get the most value out of it for your investigations. So the behavior of what kinds of activities are stored, and how they’re stored, and where they’re stored, changes based on the specific Windows version that’s being used. So 1803, 1809, 1903, whatever; the type of account that user logged in with, like we said, it could be a local user account or Microsoft account. If the same account is used on multiple machines, this can change what’s stored and where, and if the sinking part of the system is turned on. This configuration is even more complicated because the defaults over time are a moving target. The defaults that were turned on and off when you install the operating system have changed across multiple different versions of Windows.
The configuration themselves you can play with in the UI — and we’re going to look at all of these things — but there are a handful of files that actually hold the configuration. So there’s two of these CDP files stored in the same connected devices, platform folder near the activity cache. There’s also stuff stored in the NTuser for that particular user. And then there’s other things related to the group policy settings that we won’t touch at all. But multiple ways to configure it, multiple ways to look at the configuration, and all of them have an effect on what’s stored and what you can find and what you can expect to find.
So in order to determine what the baseline is for right now, I decided to set up a new Windows, 10 1903, that was the stuff released in the spring of this year, VM, a default install and see what the defaults were in order to kind of peg, at least for the moment, what you should be expecting with these machines.
So, first off, if you just start the installation, it will immediately ask you if you want to set up for a personal use or for an organization. If you set up for personal use, it basically tries to force you to set up a Microsoft account to log into. At least when I did it, it made it difficult to impossible to attempt to log in at the beginning with a standard user account. It just kind of prompts you to set up a Microsoft account. And as we’ll see, this has some significant ramifications, good for forensicators, bad for privacy, that we’ll see coming up.
The next thing it does is force you to make a PIN: note that there’s no skip button around here anyway, or making a pin one way or the other. And then it asks you if you want to do more with devices across activity history. So this is part of what turns the activity history on. And it’s important to note that while there was a yes and a no button here, yes is selected by default. So it’s probably safe to assume that most users are just going to hit the yes button and continue on.
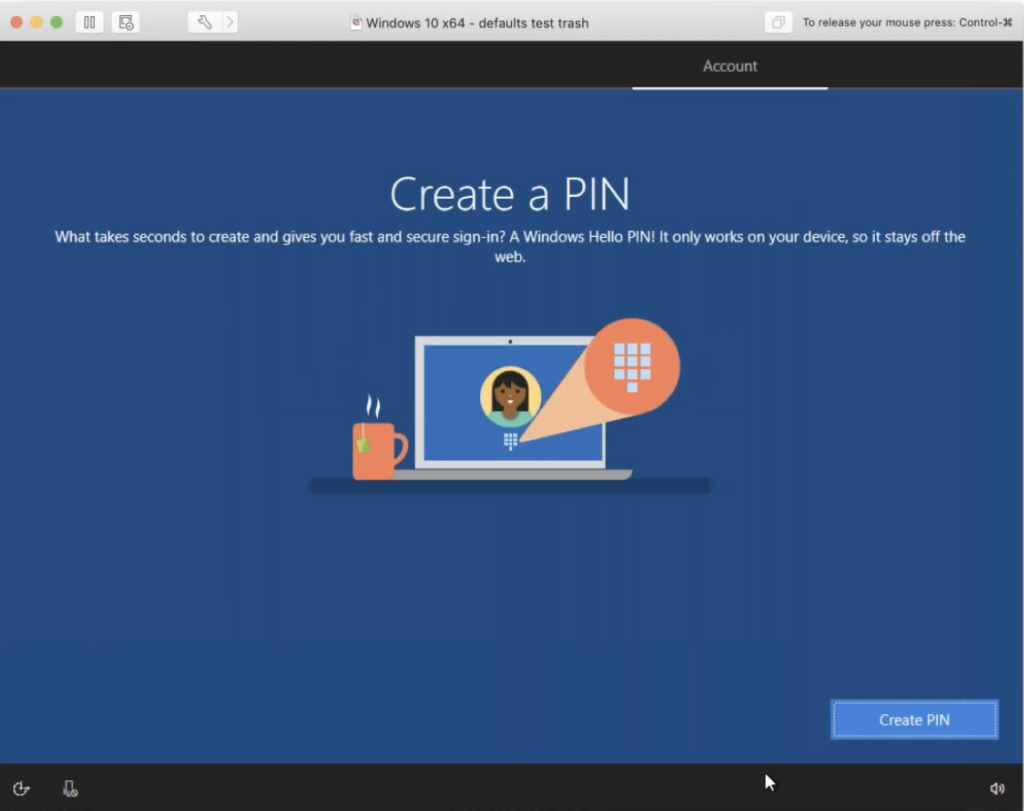
Also, ‘Back up your files with One Drive’ is selected as on by default, you can turn it off. If you look all the way at the lower left over there, to save files to this PC, but again, most users are just going to hit the next button. And as we’ll see later, it’s important to keep in mind that for syncing activities across devices and having things backed by One Drive makes it a lot simpler to see what’s going on.
This I just left in kind of as a little nugget of 10 other different things. And these privacy settings, these are all of these things are turned on by default. So just more interesting things to have a look at if you want to run through this installation thing at some point. There’s all kinds of fun, other things that I don’t think that most of the investigators have poked around at yet, but that’s just for your edification.
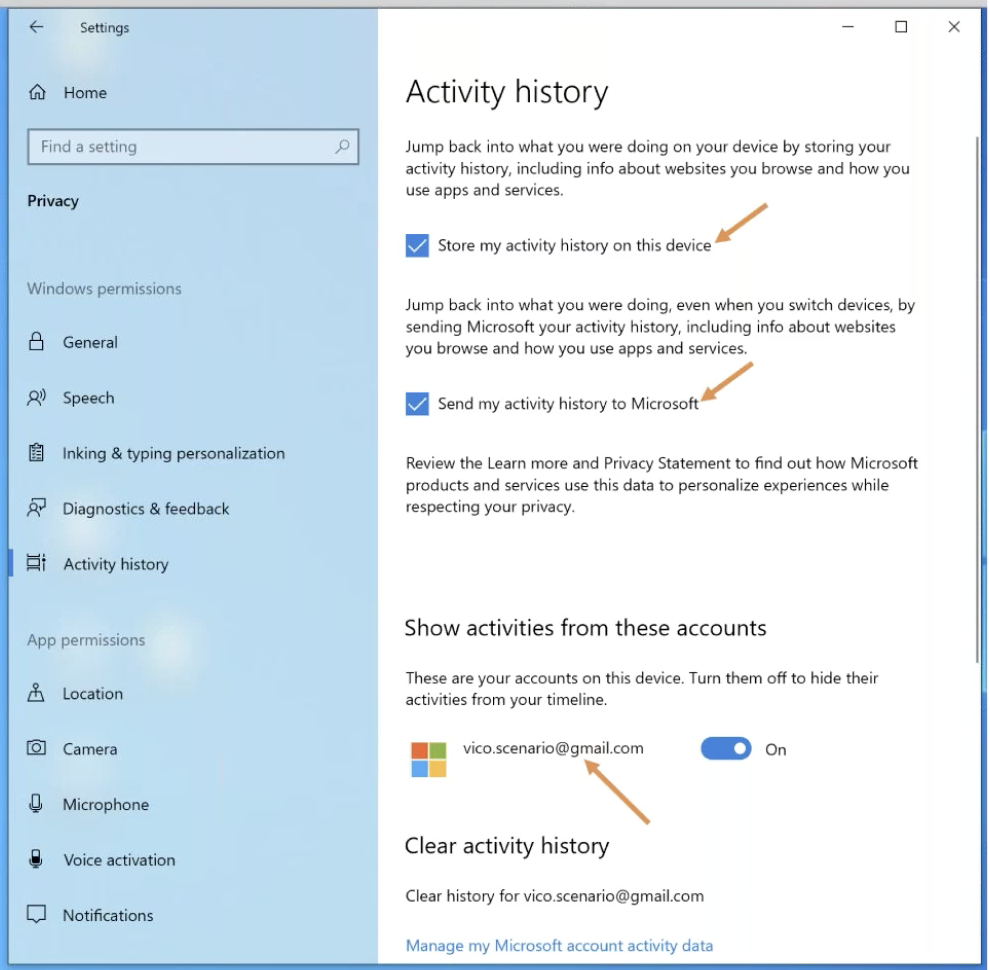
If we look at these things in the UI and you open up the Windows settings and go to privacy, we’ll see activity history on the left. And if you select activity history, you get this dialogue. So there are three things that are important here, and they’re all on by default: store activity history on this device, send my activity history to Microsoft, and show activities from this accounts. You can actually log in with multiple accounts and see activity from multiple accounts within a machine. You can turn off ‘send my activity to Microsoft’, which will stop syncing. And then you can turn off the ‘store my activity history’, which you would think would turn the activity history off. It doesn’t, it just reduces the number of days. Things are stored from something on the order of 30 to something on the order of three.
Also, while we’re digging around in the configuration settings, there’s another setting for clipboard data. There’s also recently been introduced a cloud syncde clipboard feature in Windows. And while you might think that this is completely unrelated to the activity cache, we’ll see that these things actually are related. And we’re going to take a look at some fun ramifications of that too.
So these settings files, if you look in the user’s home directory, the connected devices platform folder into this globalsettings.CDP. The default on the left here is that activity feed, cloud sync, publish user activity, user upload, upload user activity are all zeros. They’re all on by default. If you go into the UI and uncheck ‘send my activity history to Microsoft’, the upload user activity thing changes to a 1, which turns off syncing of activities across machines.
If you uncheck ‘store my activity on this device’, then publish user activity changes to a 1 which reduces the amount of time that activity history is stored on the device, but doesn’t actually really turn it off. In the lower left, if you turn on clipboard history, then there are no changes to the configuration files. But if you turn on… the clipboard history has a ‘sync across devices’ on the right over here. And we’ll note that then this one in this other file, your Microsoft ID.cdp being one of those two configuration files, and the connected devices platform folder, there were two changes. There are number of activity types, the activity types that are turned on for this machine changes. We’re going to talk about activity types later, but just kind of note for the moment that activity type 10 is now a new activity type that’s been added to the list of types that are configured for this machine.
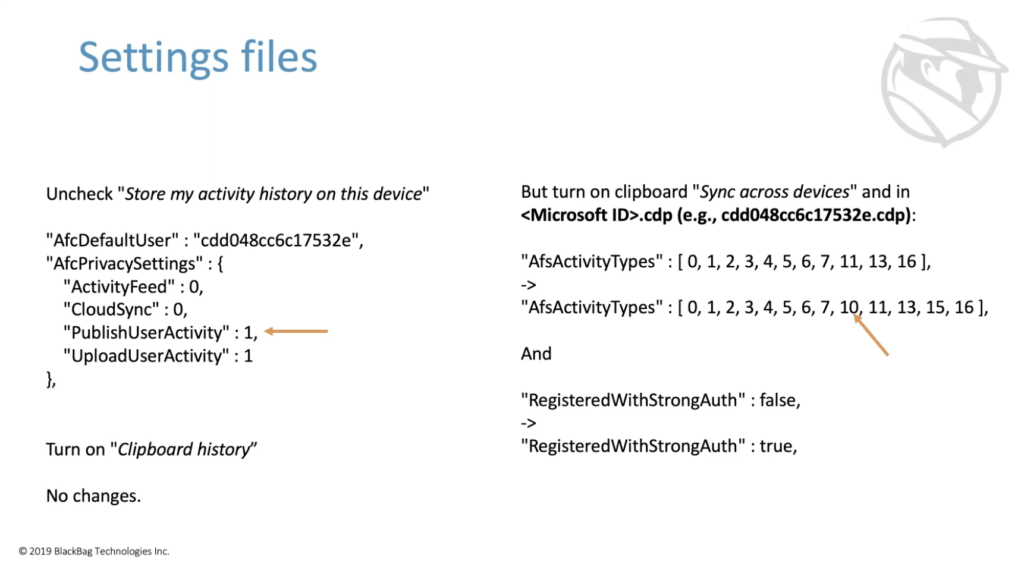
And on the bottom, we have another configuration option that changes, but I’m not entirely sure what that does yet. So we’re just going to ignore it for now. Okay. Are there any questions so far on the config stuff? I know this isn’t entirely clear yet because we haven’t gotten to the meat of it, but I just want to clear room for questions every now and again, because there’s a lot of material to cover.
Julie: Yes. Thanks Vico. So if they clear the history. is the database still there?
Vico: We’re going to talk about this at the end. So you can hit the ‘clear history’ and you can hit the ‘clear history across all the devices’. And in theory, they work. Although I haven’t tested them, I do know that if you take the maybe slightly a simpler route of just deleting the database, then it gets basically immediately recreated. And then obviously if you delete the database, it’s probably going to leave a database sitting there and unallocated space where there are now events that will be sitting there that aren’t deleted after 30 days.
Julie: Got it. Thanks for clarifying. So then our next question is when collect history is turned off, what is the smaller amount of time that is collected?
Vico: About three days, about three days. Now, again, these things change over time. So it’s important to verify, as the last time I’ve verified, it was about three days.
Julie: Got it. And if you upgrade a Windows system, is it enabled?
Vico: That is a thing that I have not touched. We’re going to see that this is a pretty broad topic, and I haven’t been able to delve incredibly deeply into each of these topics, only because there’s too much low hanging fruit to digest before we even get into the deep dives into that kind of stuff.
Julie: Got it. That makes sense. And we have one more question. What are the default history storage times?
Vico: By default the activity history is going to stay for 30 days, as long as all of the… if you hit all the next buttons, just like I did in 1903 in Windows 10, 1903, you get 30 days of history.
Juie: Awesome. That’s very helpful. I’m sure there will be more throughout.
Vico: Yes. All right. Let’s get to some actual forensics things. There’s the activity cached IDB file, which — again, while enabled, don’t forget that — which has a handful of tables here. The ones labeled one through four are the ones that we’re actually going to talk about and care about. So the main needs of the database here is the activity table, which has a whole bunch of fields. Some of which are pretty well understood. Some of which, we’re not sure entirely what they do, many of which I’ve failed to see populate at all. So in addition to the name not being super helpful, I’m trying out different activities. I haven’t even been able to make them populate with anything.
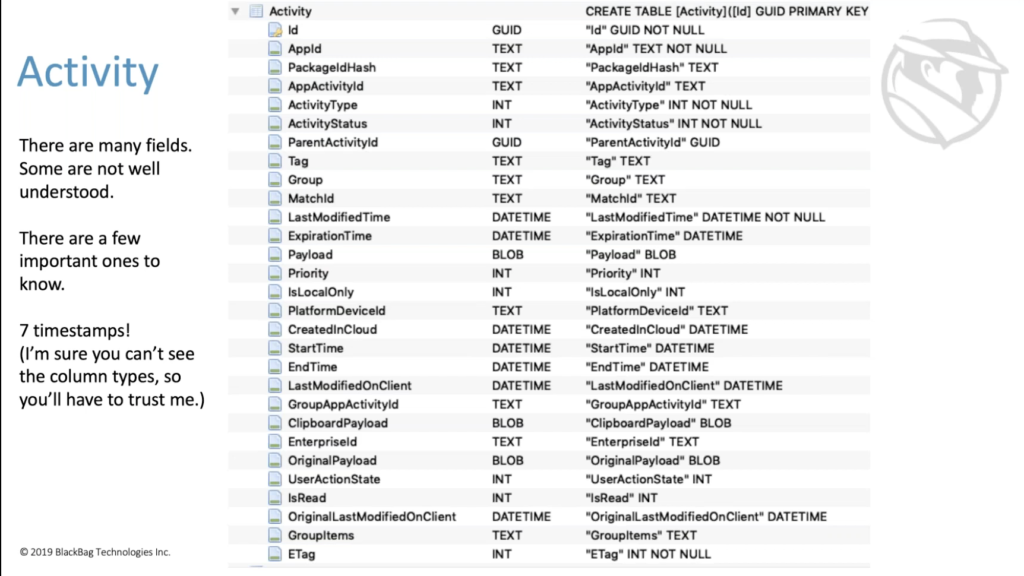
It is important to know here that there are a lot of timestamps for timestamp junkies like me. There are seven-ish timestamps in here, and there might even be new timestamps in newer versions of databases that tell you things like when an activity started, when an activity was changed, when an activity expires or when it expired, all kinds of fun timestamps in here.
So we’re going to go through some of these fields. After we look at some of the tables to find the important stuff from a forensics point of view, the next table is activity, operation activity, operation. It looks 85% the same as activity, but it serves a slightly different purpose. It’s used specifically for the process of syncing activities across machines. So depending on — and we’ll see why in a little bit — when you examine the database, you may often see activity operation be empty, and activity be populated. If you see activity operation empty, many times don’t assume that it’s always going to be empty. It definitely can be populated.
Activity package ID. So one of the slightly difficult things to understand about the activity timeline is that I told you that it talks about when applications did things; most of the other process executions, the artifacts that we look at, point to a specific executable that was run potentially at a time and potentially other things that it did.
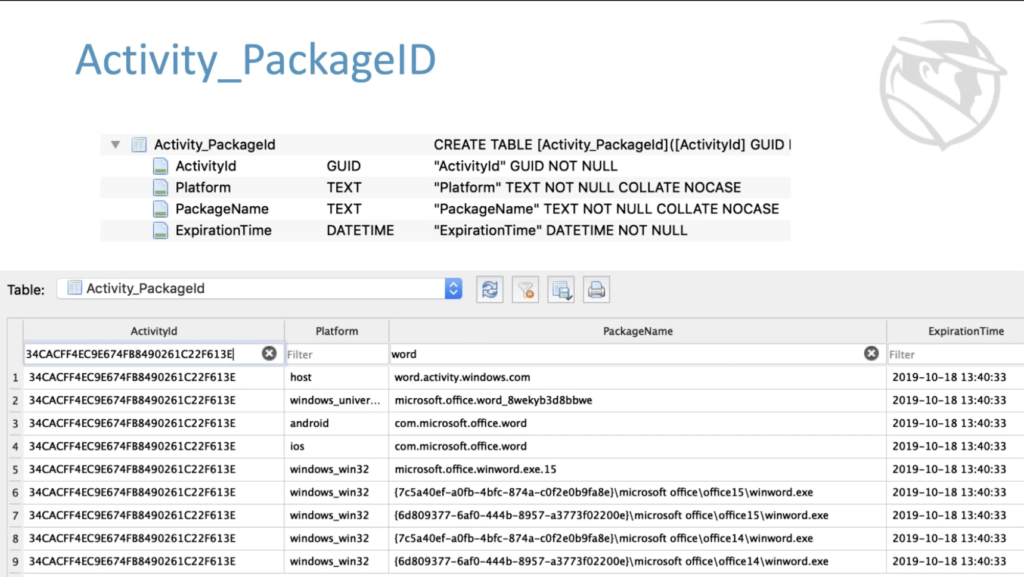
This activity timeline really talks in terms of packages. So the activity package ID table holds a list of packages for an activity. Most of them for one particular activity. And we’re going to talk more about what an activity is, a unique ID is generated. So if we look at the activity package ID table, and we look at this one, all of the entries for this one particular activity ID this activity was created by, it can be picked up by one of these particular platforms and this particular package name. So this could have been created by an Android device using Microsoft Office Word, or a number of versions of Winward for one 32. And so it’ll become a little more clear over time, but this is a pretty much a cache of all of the packages.
Let’s look at the big picture for a moment, before we lose track. So user opens an app, a new unique activity ID is generated. It’s a good, so global unique, then entries are created for an activity package ID for the package that created this activity. So not really a specific executable, but a kind of a set of executables that are responsible for this particular activity. Then the activity itself is created in the activity operation table. Then it’s synced to the cloud, then it’s added to the activity table, and then it’s deleted from the activity operation table. This is why oftentimes you’ll see that the activity operation table is empty, but you can definitely catch things at a time when upgrades were… when uploads were occurring, or if the machine didn’t recently have a network connectivity for some reason. Activity operation can definitely have lots of interesting stuff in there.
Okay. ID is the main thing that links these three tables that we care about together, and activity has an ID field activity operation as an ID field, and activity package ID has an activity ID field that are all the same thing. So activity package ID belongs to activities, and activity operations is kind of the way that works. It is unique for an activity. And you’ll see that when we sync across machines, this ID goes with it. And so it remains a unique identifier for an activity. The app ID — be very prepared for word soup here — everything around here has app ID, app activity, ID, app package, activity, ID… you have to stare at it for a little while, until it starts to make sense. If we look at the activity table and narrow it down to an entry, the app ID is the app that generated the activity.

And if you look down on the right, it’s not one specific executable, it looks like the stuff that we saw in the activity package ID table. It’s a package of activities that… a package of applications that are responsible for this particular activity. So in addition to the fact that this app ID is parts of an activity in the table, there’s also a listing of this platform stuff in the activity package ID table, linked to this table by the activity ID, slightly different than before. This is an ID that’s related directly to the application that created the activity. So this is specific to the type of application and the application that created things. So what we see in here is things like URLs. In fact, almost all of these are URLs, but you can also see files that were touched, and other types of entities, that were touched by an application.
So this is an easy and interesting place to find URLs and paths that are related to a particular activity that occurred as you’re digging around in these databases, you’re going to see this particular, like all over the place. As far as I know, no one knows what it means. Most of the tools that parse the Windows activity timeline just completely ignore this value or or delete it. If anybody out there happens to know what it is, I would love for you to tell me.
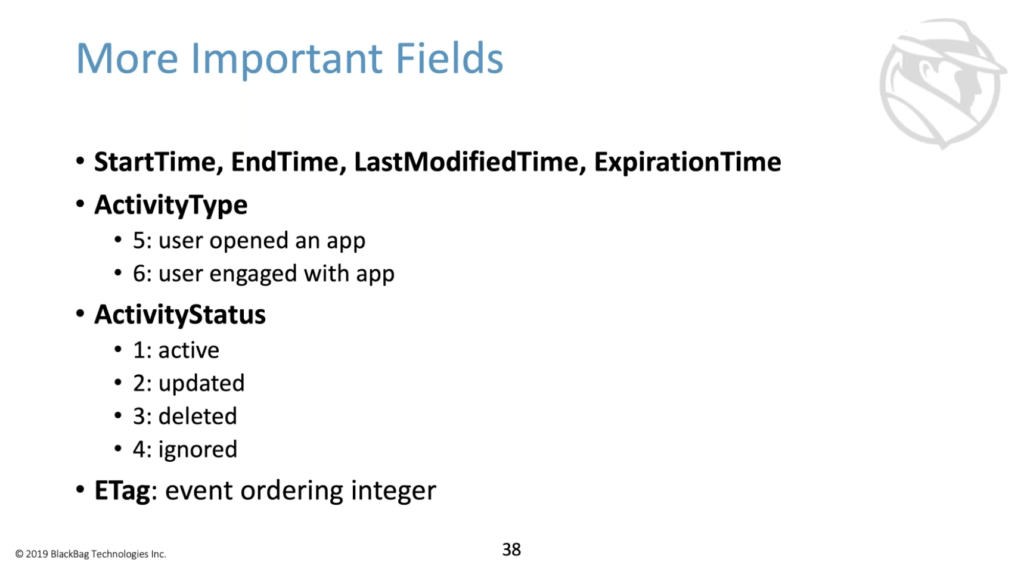
More important fields: so start time, end time, last modified time, expiration time, are very much what they sound like. The start time and end time for an activity class time was modified. One of the expired activity types we’ve mentioned a few times, but now you get to see two of them concretely, activity type five and six.
So when a user opens an app, there will be a new activity created following the process that we saw with an activity type five. And then when a user is actively engaged with the app again, then we’ll see some user activity type six activities created. There’s also an activity status just to let you know that activities can be updated. That can be deleted by users. That can be ignored. These things can change over time, which is why sometimes you can see activities that started far longer than 30 days ago. If they’d been updated, then every time they’re updated, the exploration time gets pushed back to another 30 days.
The tag is also interesting. Each of the activity tables and activity operation tables both contain an E tag. Any time there’s a change to the database, something is deleted or or inserted or changed, a new tag integer is created. And that tag is a part of that particular row that was changed or inserted or whatever. So it’s a way of ordering events on the database. That’s slightly different than ordering, seeing things say by the start time of an activity, the payload field.
This is where most of the fun stuff that we’re going to see is, and we’re going to look at many of them coming up soon for different types of activities. Its purpose is to define — is at least some of the time to define — how the tile looks in the UI. So you’ll see things like, the app display name is ‘notepad’ and the background color, referring to the tile, and the description and the display text. But note that these things talk about things that we care about: the app display name is obviously the application, and the display text here is a file that was touched. The description is the exact path to the file that was touched. We’ll also see engagement times and a ton more fun stuff.
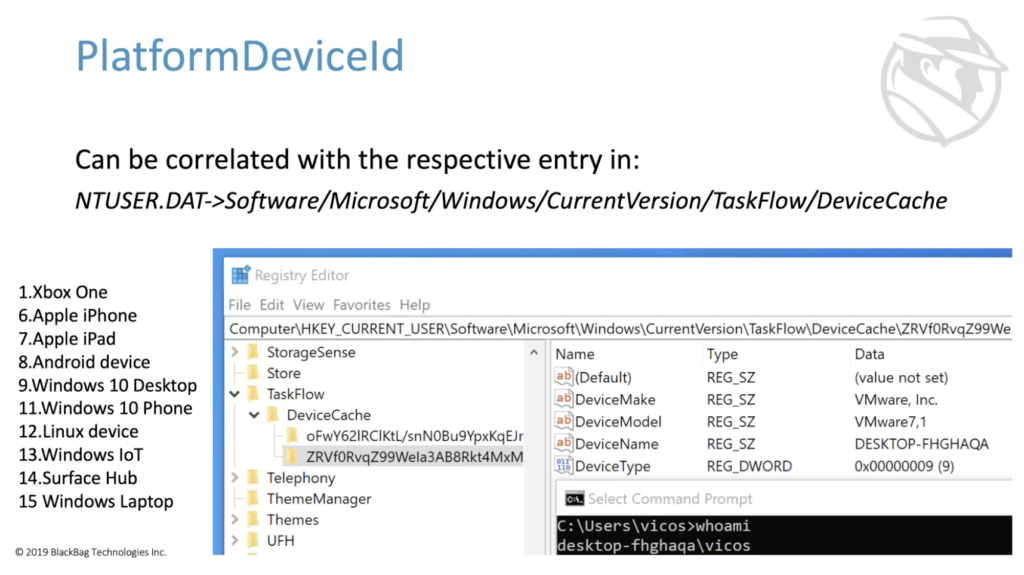
Platform, device ID, didn’t figure this one out until just recently. It doesn’t look entirely too useful. It’s like some base-64 encoded junk, but the key is if you look in NTuser for the activity timeline at this key, there’s a few things going on here. First off, we see it at task flow device cache, there’s a couple of entries here. This particular entry, this ZR, whatever, entry has a device make and model, and importantly, a device name. And if we look at the host name for this particular machine, and we’ll note that FHGH, whatever, is the host name for this machine. And so when we see the platform device ID of ZRV, whatever, we know that that’s activities that were created… generated on this particular machine. We’ll see a better example of this later.
Also note the device type, which might be helpful, this maps to [incdecipherable]/ And so Microsoft documentation and all of my samples, basically the device type is nine, because most of what I use is Windows VMs. And they all just show up as a Windows 10 desktop, but these are other options for things you might see.
Package hash ID, I’m only going to talk about for a brief moment, because we don’t really know what it is yet. It’s an unknown, it’s a base 64 encoded 256 bit hash that we know changes when you use different versions of an executable, seems to say stable when you run the same executable over again. I’ve seen some documentation that says it’s a Microsoft QuickXorHash. I’ve tried to QuickXorHash some executables. And I have not have not found anything particularly interesting, but I figured I’d point out that I don’t know what it is, just in case someone else does, or for a research project.
Last table that we’ll talk about real quickly is the metadata table, which holds a bunch of things that we may find interesting. But from a point of view of things that we may or may not find in a particular database, it holds the activity types that this particular database can hold. So we note here that this particular database can hold activity type five and six. That was the five is opening an app, and six is actively engaging with an app, plus a bunch of other things that we haven’t talked about yet.
Any more questions for the moment? Let’s take a quick, quick break.
Julie: Yes. We’ve had a lot of good questions come in. So first one: are app IDs the same across machines. So Microsoft Word, always the same ID, for instance?
The app ID usually has a GUID and a path with a folder name. So the GUIDs are probably not known folder ideas. So it’s a more difficult question to answer than you might think. The app ID is a set of packages that can open a thing. And so it depends on what the thing was that was created. That might not have been too helpful.
Julie: Well, we can always do a follow up question too. Is Windows grouping types of actions by app activity ID? And if so, do we know how many types of activity there are?
Vico: The, the app activity? No, we do not know how many types of there are. Yeah, I’m not entirely sure. So the mechanism by which an activity is picked up across machines, or even picked up later — and given that we have a platform ID, which, you know, again refers to a whole bunch of particular specific executables and, and packages on different different types of platforms — the machine… this is all backed by the project Rome and the Microsoft graph API and the connected devices platform. And it’s well beyond my understanding at this particular point in time, it’s a beast. This topic is… this activity timeline thing, it is absolutely positively, it’s a ginormous thing to attempt to understand, and we’re not going to get anywhere near it in less than an hour.
Julie: Got it. Okay. And last question for now, do you get further history by parsing shadow copies?
Vico: Yes. Shadow copies, backups, and deleted entries just in case there are any, yeah. Yes.
Julie: Great. Thank you.
Vico: Right. So I’ve told you I’ve gone on and on and on about configuration and on desk stuff, but you know, where’s the beef, what can we actually see here?
So this thing, the activity timeline can record all kinds of different types of actions that a user has been engaged in. So what you might want to look for can depend on what you care about in a particular case. If we just take torrent usage, for example, and we open up the database and filter the app IDs on the word ‘torrent’, because we know that that exists in a name of some application somewhere, what you’re looking at here is one row broken up into two that we can see. And if we look at this first row, we’ll see that it has an ‘E’ tag and an application that’s uTorrent run from the E drive.
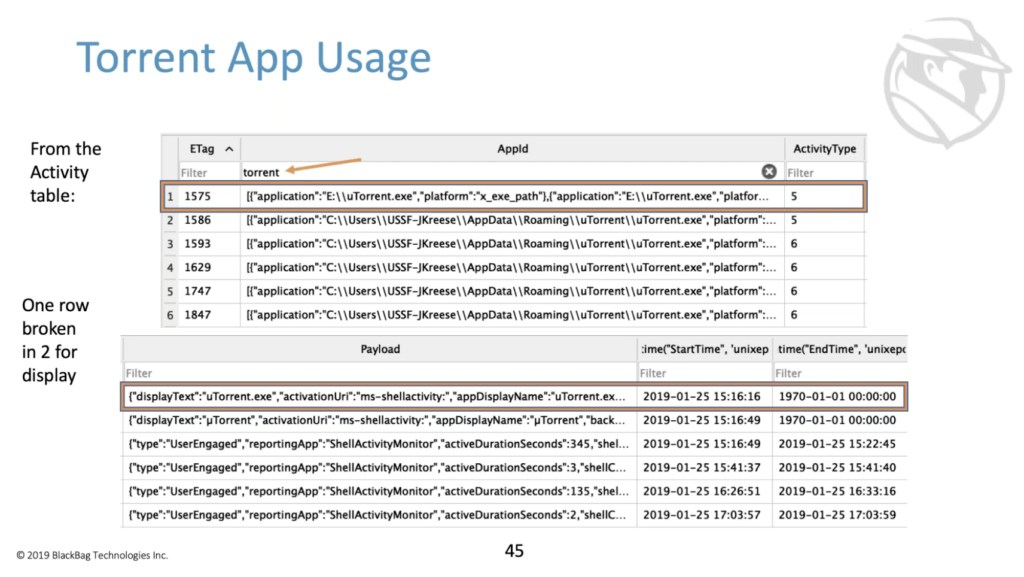
And it’s an activity type five. So that means a user has opened the app on the E drive. It was opened at this particular time, one 25, 15, 16, 16. So all important things to note. If we look at the very next entry, but we see it looks similar, but a little bit different. We see them opening new torrents, but now from the C drive. So it’s likely that the top entry is an installer from a removable drive. And now we’re looking at the actual app being run. It’s also an activity type five. So it’s the app being opened up at this particular time, which is about 30 seconds before the installer ran. So this all kind of makes a little bit of sense.
This next one is an activity type six. So this is a user engagement type of activity. So what’s different here… what’s the same and different here is that we see that the app ID stays basically the same, the payload here changes to the type is user engaged. And we have this active duration seconds here, which is super fun. This tells you that the user was actively engaged with the app for 345 seconds, starting and ending at these two times. So very granular idea of when the user was doing what they were doing.
If we look at the next three lines here, they are also the same. They’re also activity type six that have other durations of activity when the user was engaged with start times and end times. The activity type six that we couldn’t see before, because of the view, also holds a time zone. So not a super fine way to pinpoint where a user was, but still some interesting information on where the user was at a particular time.

If we move on from torrent stuff, and maybe for whatever reason, notepad activity is something that we care about, you could do something similar where you go to the app ID and filter on ‘notepad’ and look at what appears in payloads or other fields. Here, we can see that the payload field shows that the app named Notepad was opening this particular file with this particular path, and even a separate way to describe the path with a content URI. So, with a start time and end times and expiration times, lots of good information, and this is an activity type five. So the user was opening a thing. Follow it up by an activity type six, and then fives and sixes and fives and sixes: you’ll see that pattern an awful lot.
This file shelving here is another one of the fun mysteries. It’s a base 64 encoded variable size blob that went on base 64 encoded, it looks like this. We don’t know what this is. Some structure in there. I spent a lot of time staring at a hex editor, but I have yet to make sense of it. So we’ll move on.
If we look at more notepad things, this is another activity type five of notepad opening a file. This time to file happens to be on an external drive. So just keep in mind that this particular artifact doesn’t differentiate between internal drives or external drives or network drives. You can find all types of activity that occurred on the machine or on attached devices.
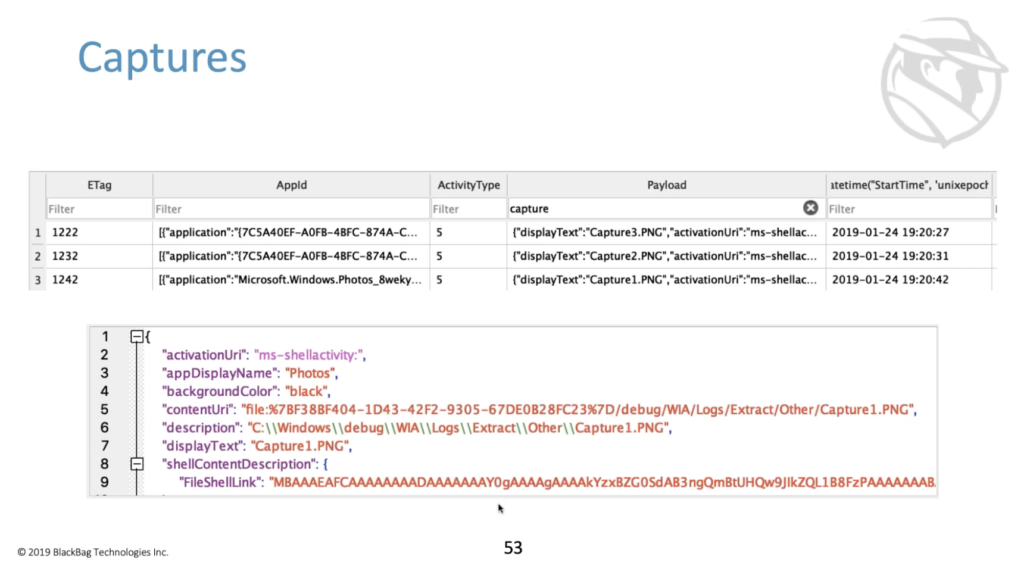
What if you were interested in users taking screenshots to exfiltrate data? On Microsoft, you can use snipping tool to do this, it’s built in by default. And if you do the same thing that we’ve been doing, where you filter the app ID by snipping tool, and you look at the payload, you’ll know down here that neither the app ID, nor the payload, tell you anything interesting about if there were files created, or files accessed, or files opened or whatever, by snipping tool. This database holds a lot of kind of redundant data… redundant information. So there’s almost always a different way to look to see if we can figure out what we’re trying to figure out.
This particular snipping tool by default names, the output files, the capture, and a number of .PNG. So if we switched from looking at an app ID for the application that we cared about, and we switched looking at payloads that might have the word ‘capture’ in them, we see that there are three entries here and they all look kind of similar, but it shows that the Windows Photos app was used to open this capture1.png. So it’s important to understand that you might have to involve multiple of these database fields in order to get at the data that you want. There’s always different ways to look at the stuff.
Just more random… not random. More payloads that I’ve seen in poking around. It’s probably important to note here that you never know what will show up in a payload blob. So if it’s a particularly important machine to your investigation, you can search and filter and all to your heart’s content. But at some point you may just have to sit there and go look through all of them because you don’t know what can possibly appear in there. So this is me accessing my scenario Gmail account: happens to the note that I have 11 messages in my inbox at this particular time. Again, this will be timestamped in the activity. Search terms: this is me looking for an online base 64 decoder. I don’t even remember why, but using Bing, and search terms that I used inside of Bing. Using One Drive, this shows that I was using the app named Word to access a One Drive file called test.docx. So specifically timed information, again, multiple timestamps for what I was up to at a particular moment, Windows Live docs, very similar type of thing. This payload shows that Word was used to access this particular document.
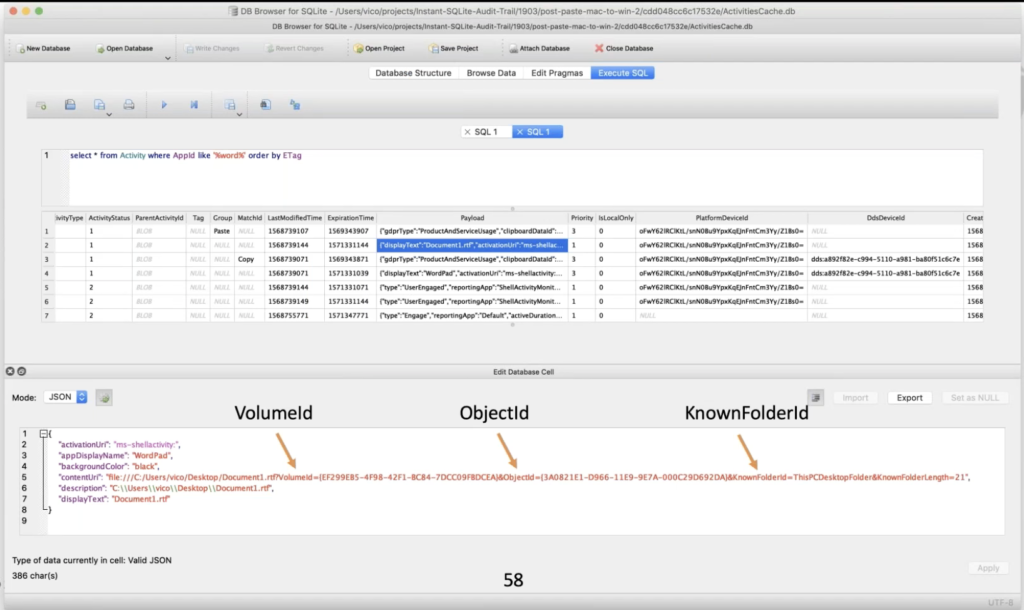
Every now and again, when you’re digging around, you’ll find stuff that you don’t know existed like this. I was looking for a WordPad activity and I’m looking at payloads. And this particular payload shows WordPad opens a file held document. One’s on RTF at this path, but the content [indecipherable] actually holds a volume ID and object ID and a known folder writing. There’s always fun new stuff in here to look at. I don’t know exactly when these things are generated, but tons of interesting information in here that you wouldn’t necessarily expect from reading a paragraph about what’s in the activity timeline.
So we can kind of beat payloads to death again, across any different type of app or class of apps. Somebody had mentioned in a recent talk I gave, had I looked at if password managers like store anything in here, or other types of apps, I just haven’t looked yet. There’s an infinite number of apps and they could all be fun things.
Don’t forget that these things all have all of these timestamps for you to play with. And as someone asked also, don’t forget that while we get 30 days of history, there’s volume shadow copies, and backups, and, you know, potentially far more history there than 30 days.
No matter how many times I tried to write the word sync or synced or syncing, it always just looks dumb. So this was just here for me to laugh at. So we have said over and over and over again that this timeline functionality can be synced across machines. We’ve also said that the configuration is a little bit complicated. So if the user has a Microsoft account, and if the user logs into multiple machines with that same Microsoft account, and these machines are set up to sync activities, then a timeline on any of the machines — a timeline of activities that includes activities that occur on that machine plus activities that occurred on other machines — can all appear at the same time in the same database. It’s often leveraged as One Drive for files, which is again from a forensic standpoint, we’re thankful that Microsoft now tries to get you to use One Drive by default during installation
Windows. So we saw very early in the presentation, these VMware seven.one things. If we look at what was going on here, Plist editor pro, and being, looking for a Plist viewer, these are all activities that occurred and they’re in the UI for the activity timeline, but these all occurred on a different machine than this machine that’s displaying these results. We’re going to look at this in some detail, because I think it’s super interesting.
So this is a database off of a machine where I’m telling you that the Plist based activity did not actually occur. And if we go into the database and we look for app activity IDs that look something like Plist, we see that there’s a whole bunch of things here. The first thing that we see is an activity type five, where the payload shows us that Bing was used to search Windows Plist viewer. So we know what a user was up to. This next slide just shows that the app activity ID corroborates that the Windows… it’s just another place to look for the same information; if payload wasn’t super helpful then maybe app activity ID could be helpful.
The next thing we see as an activity type six, the user was engaged with that particular activity for 16 seconds. So a search for windows Plist viewer, looked at it for 16 seconds. Same data also shows in the app activity ID. Then the next thing we see is an activity type five of a different webpage being opened up, Edge opening up the Plist editor page, same thing, activity ID corroborates, then an activity type six. So is it 27 seconds? The user was engaged with this particular activity. That was me. The website looked a little… I couldn’t tell if it was a good thing to download and install or not. So I hemmed and hawed for about 27 seconds before I clicked it.
Then the next thing we see down here is that another activity type five, and that Plist Editor Pro was used to open one of these configuration files. So the CDP resourc is that Plist. Note that for those that are paying too close of attention, this configuration file is not a plist. That was having a bad day and try to open it with a plist opener that didn’t work. So don’t try to do that. It’s a JSON blob. So you can just open it up in any random text editor, if you want.
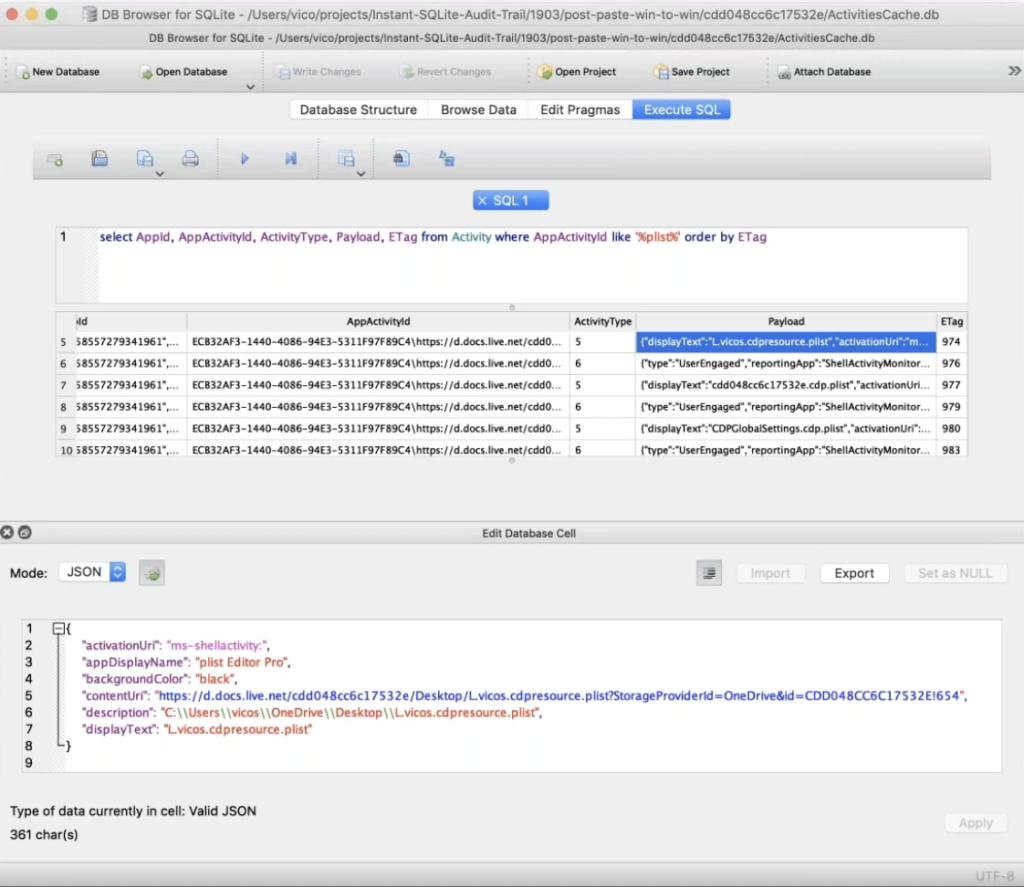
This also shows me opening up just another file with the same plist editor, another activity type five, and another one. So I told you these things didn’t occur on the machine that we were looking at, but let’s take a little closer look.
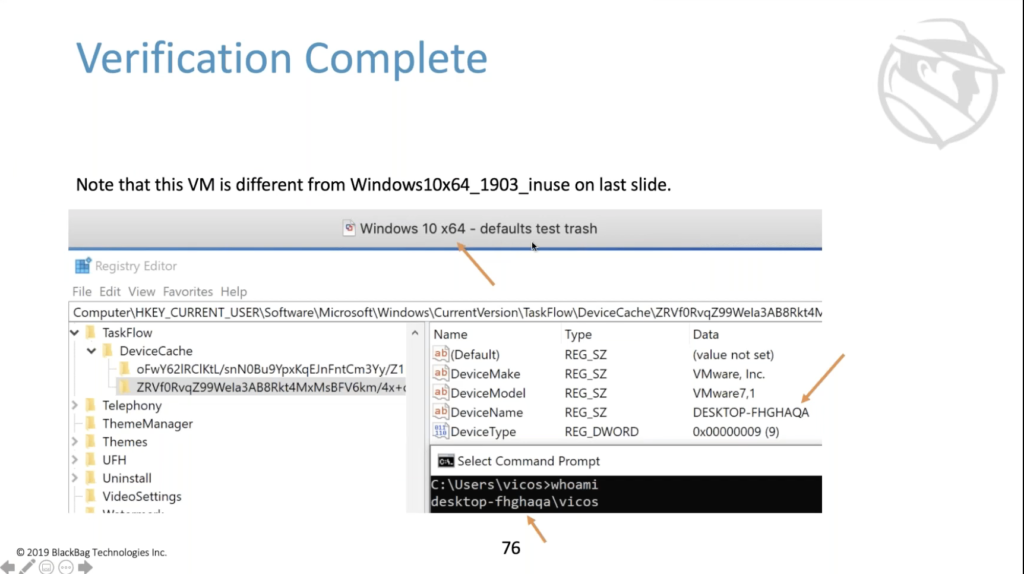
So if we look at the platform device ID here for these. So we’re running the same query as we did before. We’re looking for app activity ID, or it looks like Plist. But this time we’ve included the platform device ID in the output.
So Windows 1903 in use as my Windows 10, 1903 testing machine, that’s where the database came from. And if you look at the registry entries that we saw earlier in the presentation, you’ll note that this Windows 1903 in use VM, the actual machine name is this RF seven and RF seven is the device cash OFW, whatever right? OFW. And if we look at ZRV, which again, all of these were ZRVs, right? We can see that this was a different machine. It has a different machine name. So that’s super fun. We don’t have a way of learning a whole lot more about the machine given this type of stuff. But if we happen to have other machines around, we can certainly go look. And so if we look at this different machine, the other one was Windows 64 1903 in use. If we look at this other… this is the trash VM that I actually used to test defaults from installing 1903. We’ll note that the Z RV thing is in fact, again, the same machine name, and the machine name for this VM is the one that matches. So now we have verified that in the activity cache.db file for one machine, you can see activities that occurred on another Windows machine.
That was super cool from my point of view, I really liked that. So I went thinking one step further, and it turns out that Office 365 tools are available for all kinds of platforms. And One Drive is available for all kinds of platforms. So if you log into office 365 with the same Microsoft ID and across some of these platforms and go installing stuff, especially Office, then activities can be synced a little bit like they’re synced across Windows machines, although not exactly.
So I started up a Mojave VM with this particular configuration, just in case that matters. And I went and did some actions on the Mojave VM. I went in, just went to the store and downloaded Office stuff using my Office 365, my vico.scenario Microsoft ID, and went and opened some files that were on One Drive.
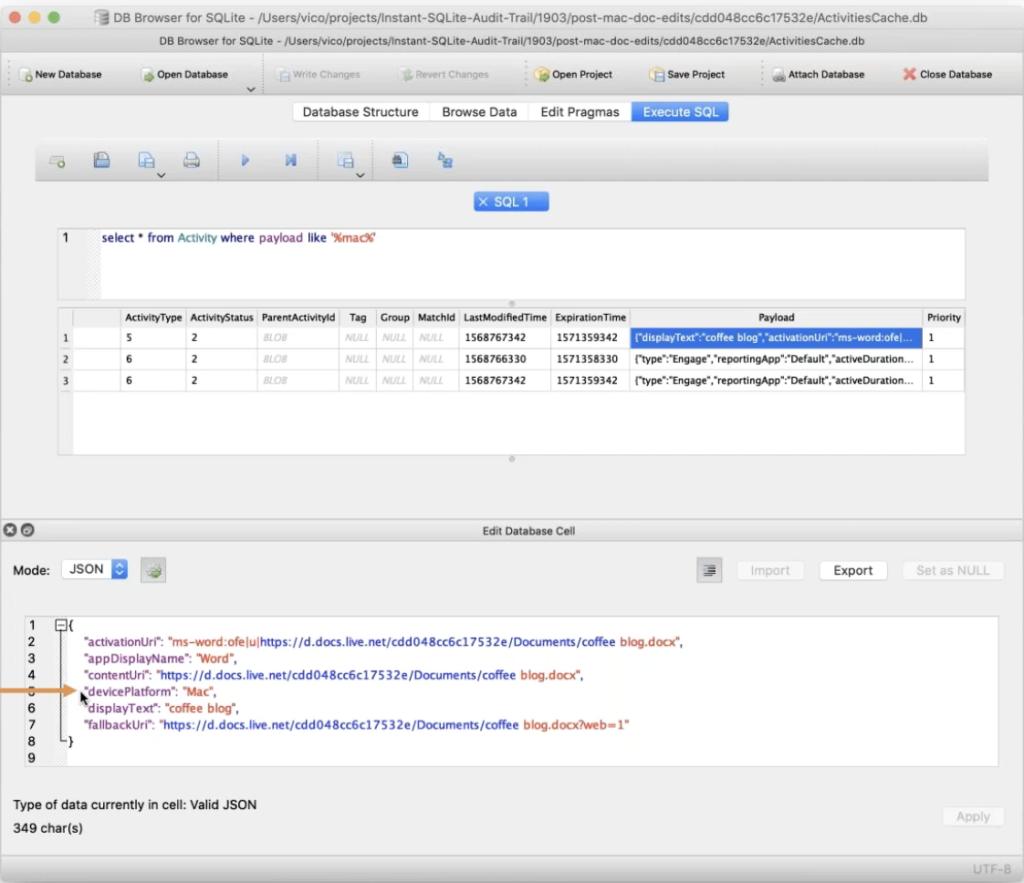
So now we’re back on a Windows machine, looking at the activity cache database. And if we look at the database and we look at the select star from activity where the payload looks like Mac, cause I was just curious what would show up, telling me that it might’ve come from a different machine. We’ll note that this payload looks a lot like the payloads we’ve seen before, with a display name and a content URI and display text, but what’s different here is the device platform is Mac. This can tell you that the machine that actually performed this activity was a Mac machine. And it turns out that this was in fact, the document that I was editing on this Mac VM.
In addition to activity type five, you’ll see activity type six. The good part about the activity type six is that it’s there and shows a start time for the activity type six; the bad part is that it doesn’t tell you the duration, and it doesn’t tell you the time zone, and even the type changed just from ‘engaged’ to ‘engage’. So there’s some good stuff and some bad stuff there, but super cool that you can even see this activity that occurs on a Mac on a Windows machine. I don’t think that’s something that a lot of a lot of suspects know, I certainly didn’t as of not too long ago.
This is just showing more app activity IDs, and showing the same files, accessed again by Mac. Always, if you look at a payload and you don’t see what you want, look at the app activity ID. Platform, device ID, if you want to try to figure out like the machine name of the Mac or something like that. And my testing so far has always been known. So you might not know what Mac machine this came from, but you know that it was a Mac machine.
And I started thinking, how does this work on Android? So I happened to have a Pixel three, it’s my own personal phone that runs Android 10. And I did the same thing. I logged into it. I don’t remember if I logged into the website or went to the store, the play store, but one way or the other, I downloaded the Office 365 stuff and logged in and it installed One Drive and Word and all of the rest of the Office things. And a little bit like on Mac, you’ll see the same thing. You’ll see that if you look for in the activity table where the payload, instead of looking for things that looked like Mac, look for things that look like Android, you will again see activity type five and six, where here’s an activity type five that shows an app display name, word, being used to open the thing with this to play displace X. And this file path that the device platform now says Android. So even if you’re editing stuff on your phone, you’re going to leave a residue on a Windows machine if you’ve logged in with the same ID.
Same thing here with the activity type six, the engagement thing, you don’t get an actual amount of time the user was engaged, but you get a start time when they were engaged, and you also don’t get a timestamp at all.
And just to beat this horse to death, if you’re going to look at the payload, look at the app activity ID. Cause one or the other may at any given time have more information. Same stuff here. Questions, at this point?
Julie: Yes, we’ve had a few more come in. So do apps like ccleaner delete artifacts,
Vico: Ccleaner does delete artifacts. I don’t know if ccleaner does anything with this Windows timeline and I’d kind of doubt it. Well, I don’t have any reason to doubt it. I haven’t seen that. It does, but I have not tested it.
Julie: Okay, got that. How about is time zone information stored with the artifacts?
Vico: Time zone information is stored in the database, in the activity type six entries and stays there for as long as the entry stays there. The entry will expire after 30 days, and so at that point, it’s gone.
Julie: Thanks for clarifying. Okay. We have a few more that are coming in. Is the web activity only recorded if you use Microsoft Edge, or does it record for any other browser?
Vico: I’ve seen it record stuff for Chrome, and I’ve also seen where I’ve used Chrome and it didn’t record it. And it might’ve been across different versions of Chrome, or different versions of Windows. Like I said, the stuff requires a lot of verification, and I wish I had more solid answers, but I don’t think they exist. I think the behavior changes over time.
Julie: Got it. Is the time duration captured app-specific, or can it differentiate between browser tab views? So for example, cnn.com was viewed for 10 seconds, and then BBC.com was viewed for 30 seconds within a single browser window, or will it just show browser duration of 30 seconds?
Vico: I’m pretty sure that when you open a new tab or even go to a new webpage, a new activity has started. And so the new activity, you’ll have new activity type five and new activity type six. Like we saw in the previous example where I was using Bing to search for a plist editor, and then there a new activity started when I opened one of the links to actually download a plist editor. It created a new activity, so you’ll get a new activity type five, and then new activity type sixes for engagement with that new tab.
Julie: Got it. Okay.
Vico: However you want to say that this is an API that, that any app writer, any third party app writer, can subscribe to and write his tool against. So for other types of browsers, it may be the case that Microsoft wanted Edge to do that for every tab and maybe the Chrome devs don’t want it to do that for every tab. They will definitely have some measure of control over that.
Julie: Right. Okay. In the activity table, can you filter by device ID?
Vico: Absolutely. Yeah.
Julie: Great. And last question for now, or we actually have another one coming in too, so will it sync across iPad and iPhones as well?
Vico: I don’t have an iPad, an iPad or an iPhone, but you know, I’m reasonably confident that as long as when you install, download and install, the Microsoft Office 365 stuff, and you log in with the same ID that the stuff’s going to get synced. I can do more testing, but I don’t actually possess either one of those devices.
Julie: Okay. So are the timestamps device generated or are they on the server side?
Vico: That is a very good question. I’d have to think about for a second.
Julie: No problem. We can always do a follow-up or if we want to do a blog after we will let everyone know any questions that Vico needs to search a little bit more on.
VicoL Yeah. Like I said, there’s a, there’s a lot of work to do here. It’s a really fun artifact that I keep finding new things in it. I thought, you know, I thought I’d get bored with it at some point, but there’s just constantly new stuff.
Julie: Well, that keeps it exciting. So those are all the questions we had for now.
Vico: Okay, cool. So I said earlier, we looked at clipboard configuration stuff just for instance. And I told you that even though the clipboard is kind of a separate subsystem, that there’s some interrelation here with the activity timeline. So let’s take a gander at that.
So first off the bad part. The clipboard history and sync across devices and everything is not… none of it’s turned on by default and the user isn’t prompted to turn it on during the installation process. So unless a user, at least as of 1903, knows that it’s there and it goes and turns it on, then we’re not going to have a whole lot of luck with this, but I’m super curious to see if the next release of Windows… it seems like over time, more and more stuff is turned on by default. Super, super curious if the next release of Windows is going to have this stuff turned on by default.
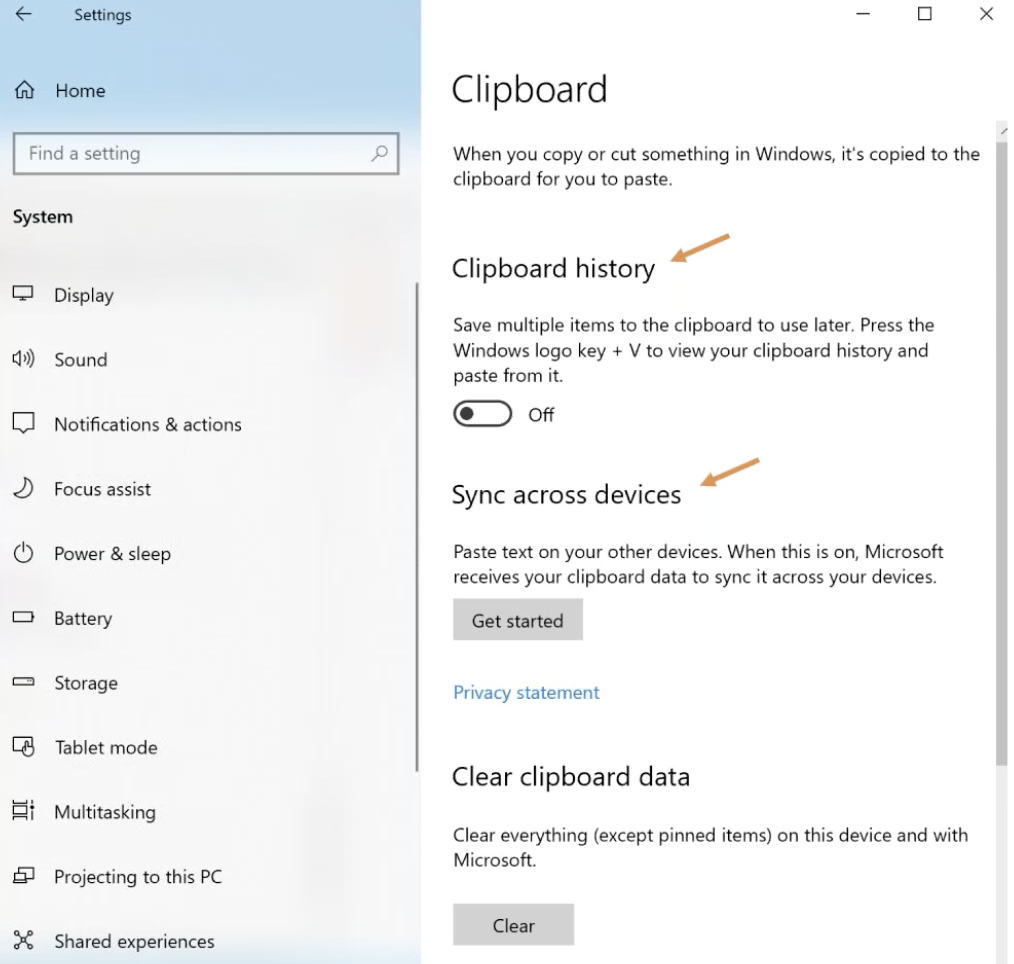
But anyway, this is the configuration: clipboard history on and off, and sync across devices. You turn on clipboard history and sync across devices. Then as we said, way, way, way at the beginning that no one remembers, we saw a new activity type ten. It’s the copy paste activity. So five is app open, six is user engaged, ten: copy paste. So sometimes you’ll see a payload field for these activities populated, sometimes not, but you’ll almost always see a clipboard payload field populated. So if you see a content of a clipboard field populated, and it looks like this, this is the base 64 encoded text that was copied and pasted. So in my my test I did, I have selected this text and copied it and this stuff sits around in the database. I don’t know for sure if this… I’ve seen documentation online that says this stuff only sits around for 12 hours instead of 30 days. And that may be the case. I just haven’t been verified for myself, but be aware that it might not stick around for quite as long as other types of activity.
So this I thought was really interesting, and I’ve tested it back and forth a few times. You don’t always know exactly what app was copied into or pasted from, it’s a little hard to decipher, but the fact that a copy paste occurred, and a timestamp for it, and the text that was copied or pasted, is definitely there.
And brand new in newer Windows timeline and databases is this activity type 16. Still working through this one, there are two things. This is another copy paste type of artifact. So when a new activity type, that’s another type that also has to do with copy and paste. This particular artifact doesn’t store any any texts that was copied or pasted, and also mentions GDPR in the payload. So maybe, they’re not in newer versions going to have copy paste texts sitting around, but it does match up activities for copy and paste with times. So different times, a copy and paste that are matched up by this clipboard data ID.
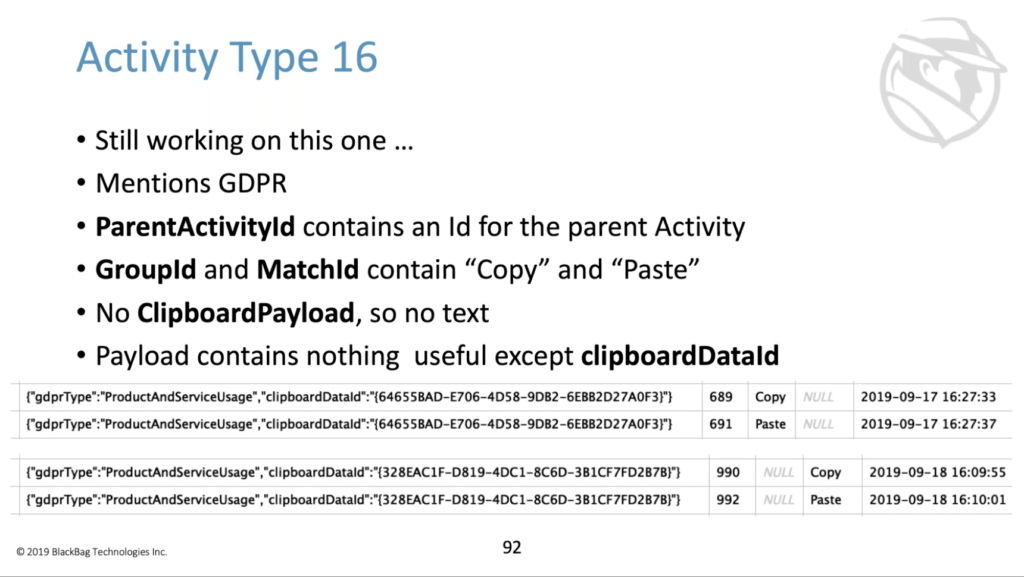
So a copy occurred, a paste occurred at these particular times, and you will have the platform device ID there too, to find out what machine. And this doesn’t tell you anything about an app right here, but there’s another field that we’re not looking at. That’s the parent activity ID. And if you go look at the parent activity ID, which again is an activity ID that points to another activity, to the parent of this one. You could potentially see what app was doing the copying and pasting. So it was more fun here and again, more testing to do, but you need to know that it’s there because the timestamps of copy paste data is something that we don’t see in a tremendous number of other artifacts.
Copy paste stuff. I’ve only tried really with Windows. I tried to cross for Mac things and it didn’t seem to work for me. I tried it on Android things and it didn’t work for me. But then I noticed in the Windows configuration under the clipboard history, there’s this little thing, it says, ‘get an app to sync clipboard or items to your phone’. And if you click the right buttons, it will send an app to your Android device to sync clipboard data. I did not run this or test it, but it exists. And almost certainly does exactly what it says it does. So copy paste data potentially across from Windows devices and Android and back. Super cool stuff.

Anti forensic stuff, which again, I haven’t tested a whole lot, but it’s always good to note some of the issues. If you delete the database itself, it just pop pops back up. There are configuration options to turn off the activity timeline, but it seems to continue to generate timelines, just for shorter durations. There’s also thing that there’s also a button to delete this and delete it across synced devices, which probably does what it says it does, but maybe does it poorly. I haven’t checked to see if there are deleted records still stored in the database after that. It’s a cross machine sync thing, means that if you have a machine that’s turned off at some point and sitting in a closet somewhere and hasn’t touched the network in a while, then clearly even if you hit ‘clear activity across all synced devices’, then this guy’s not going to get the message to clear any of the activities. So all kinds of fun ways to find things.
Plus we noted that a lot of the synced activity stuff occurs using One Drive. And so One Drive has direct ways to go get access to documents without having to have machines. And even after you’ve turned off syncing and then all that other kind of fun stuff. There’s also… so we said that the activity operations table is part of the process that syncs activities up to the cloud, or syncs them up to Microsoft somewhere. This uses the graph API, project Rome, and connected devices platform. And I’ve done no looking at all to see how much of this data is stored on Microsoft servers.
So let’s say the anti forensics that the suspect did wasn’t deleting all the things, but he threw the laptop in the river. It certainly may be the case that there’s a way to query the activity timeline stuff directly from Microsoft, using either one of these APIs, or some service available to law enforcement, or again, lots of lots and lots of questions. There’s probably a whole… it’s probably a whole presentation to do just based on any forensics in this particular entry artifact.
Fun mysteries. I always like fun mysteries. They keep me in engaged with an artifact. File show link, we don’t know what it is; the package hash ID, package ID hash — I’d love to know what that’s a hash of specifically — all the fun things that you find when you’re looking through payloads, like the word pad volume ID, object ID, known folder ID.
We looked at four activity types: five, six, 10, and 16. And while I’ve seen some of the other ones, I haven’t seen them in great enough number to really understand what it is that they’re doing or what they’re for, but these things do get recorded. They don’t get recorded often, given the specific types of activity I engage in. That doesn’t mean that they’re uncommon for other users, right. I do the things the way I do them. Other people do them different ways.
Just so you know, you can do all these things in BlackLight by default right now, because we have an awesome SQLite viewer that will let you go do queries against this SQLite data because it’s a SQLite database. Also coming this fall is some much more interesting support for the Windows timeline stuff. I think it’s a really powerful artifact. And so we’re going to make sure that it’s in the tool in a way that’s super cozy and comfortable and powerful to use.
Wrapping up: kind of a summary. So new from Windows 10, 1803, it’s definitely in 1903. I don’t see it going anywhere in the next release, although I haven’t looked. Tracks files and URLs, and actual engagement times and timestamps, and timestamps just all over the place. There could be an interesting study of just how to use all those timestamps to better reconstruct user activity, clipboard activity, sync across devices. That’s not just Windows devices: it can be synced across Mac devices and Android stuff to even clipboard data sync across your phone. That kind of blew my mind. Potentially only say for 30 days by default, but all your shadow copies and backups, if you don’t have one of these every 30 days or so for your machines, you’ve got other problems than the fact that you only have 30 days of a timeline history.
And again, it’s a moving target. So every time there’s a new release, they add and remove columns and database tables and the behavior of the stuff that’s already in there changes. It’s going to provide tons of fun for a long time to come.
Jules? Julie?
Julie: We’ve got a few more questions come in. So before we wrap up, I will ask these and if you have any other questions, you can always email Vico after the webinar. So the first few we have: is type 10 for text only, or is it also for files and images?
Vico: I’ve only seen text in there. But you know that there was a field in there that said the content was type: text or something, which implies that there could be other types. I don’t know.
Julie: Okay. Makes sense. Can you manage at the business level, whether activity is collected across systems?
Vico: You get asked this question every time I talk about this. So I should certainly have an answer by now. There are policy… Windows policy settings that apply to the timeline thing, but I don’t know. That’s not my area of expertise at all. I don’t know.
Julie: Got it. Okay. If you unsync with another device, does it auto-delete and clear everything from all the devices or just that one specific device you originally un-sync it?
Vico: Going to take more testing to know. Like I said, broad topic with lots of depth, that’s why that we just don’t have time to cover.
Julie: Great. Well, I know we are at the top of the hour, so thank you, Vico. And thanks for walking us through the activity timeline. We hope this was helpful for everyone, and you enjoyed learning more about this new forensics artifact. If you did submit a question, and we didn’t get to it, someone will reach out and follow up with you. And as a reminder, this will be sent out on demand. So stay tuned if you missed any of the beginning.
And of course, if you’re interested in learning more about any of our products or services, please email sales@blackbagtech.com, or specific to the activity timeline you can reach out to Vico. And if you would like follow us on social, on Twitter, Facebook, YouTube, and LinkedIn, and subscribe to our blog. But thank you all for joining today. That will wrap everything up and we hope you have a great rest of your day. Thanks, Vico.
Vico: Thanks, everybody.