by Andrey Fedorov
The purpose of this article is to find additional information about the capabilities, specifics, and USPs of the ADR512 Android Data Recovery program. A full description of this software can be found here.
Developers from 512 BYTE, who created the software, invited specialists from digital forensics lab Gross to test it.
Let’s take a look at the practical tests.
The essence of the experiment step by step was as follows.
Two devices were taken: Lenovo A319 (OS version 4.4.2) and Xiaomi Redmi Note 3 Pro (OS version 6.0.1).
The Lenovo A319’s phone memory was reset to factory settings (all data, including the user’s, were deleted).
For the Lenovo A319, root rights were obtained to have full access to the memory (Hynix eMMC H4G2a) of the device.
An image of the Lenovo’s drive was created. The size of the image was 4GB.
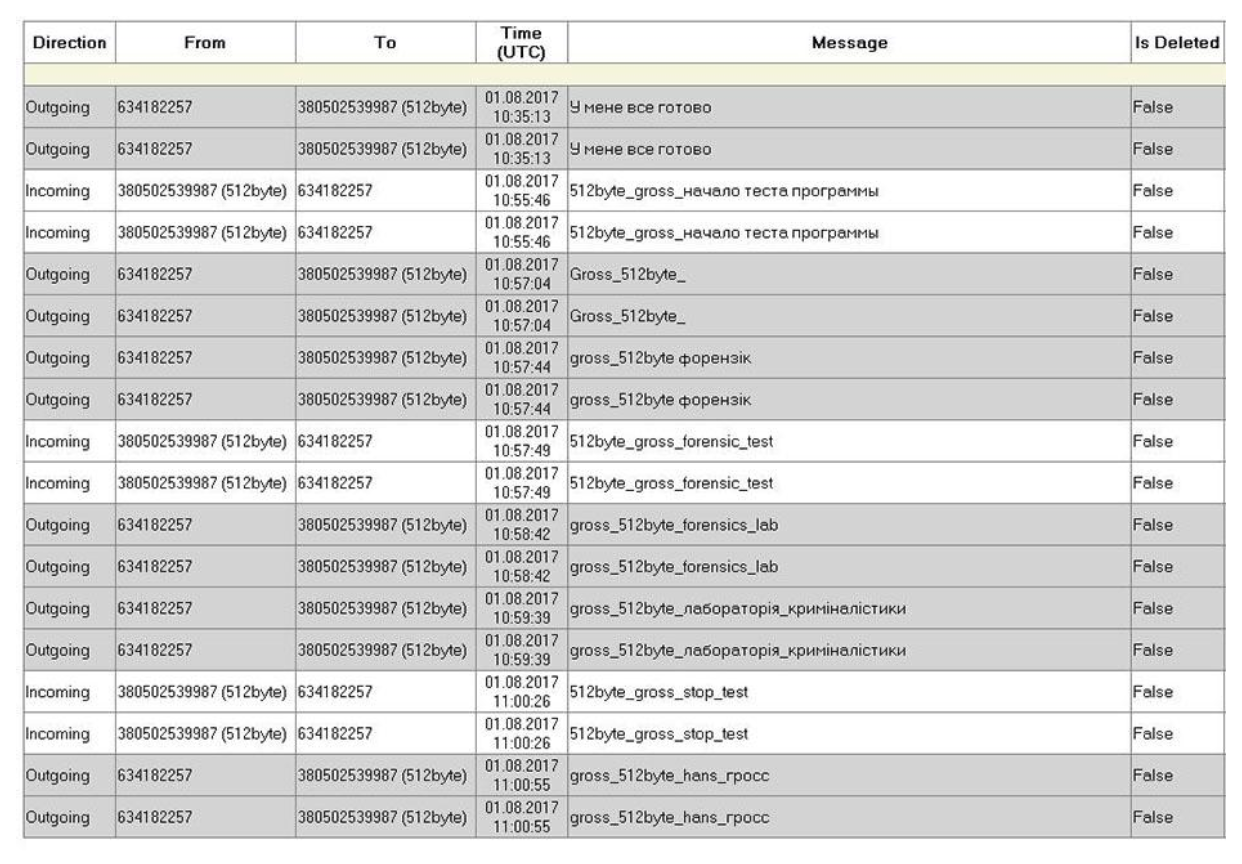
The image was then investigated using Belkasoft Evidence Center Ultimate 2017, which is designed for data retrieval and analysis. The section “Messages” was missing in the report.
For testing, the instant messaging application imo was selected. This was installed via the Google Play Service. We chose this program because it has had over 100 million downloads. We purposefully did not choose the most used applications like “Viber”and “WhatsApp”.
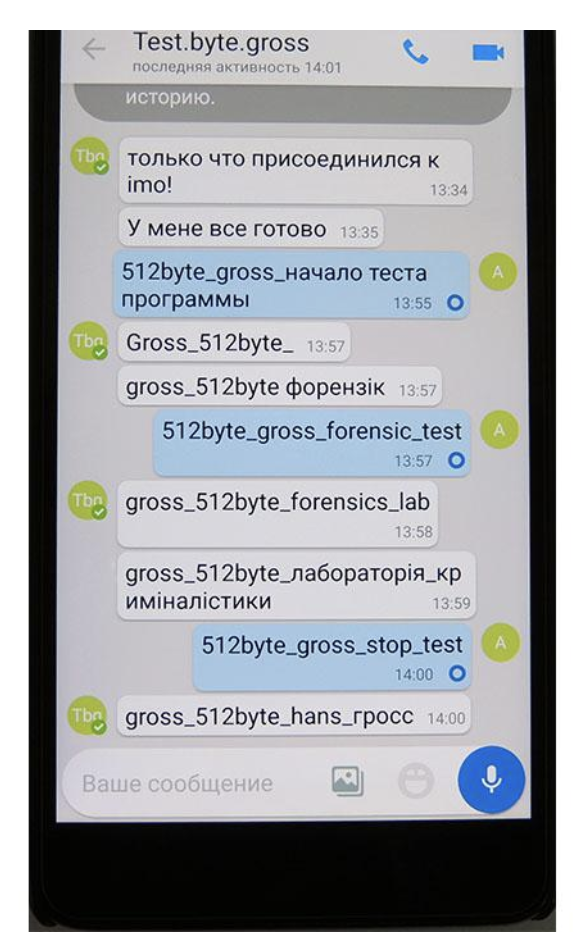
Between these two devices instant messages were exchanged in “imo” (text: “512byte_gross”, “gross_512byte”). There is a screenshot below with the contents of the text messages, taken from the Xiaomi Redmi Note 3 Pro.
After using the “imo” application, the Lenovo A319 was re-imaged.
The image of the drive from was then investigated by using Belkasoft Evidence Center Ultimate. The “Messages” section now appears.
 After that, the “imo” application was removed from the Lenovo A319 phone in the standard way.
After that, the “imo” application was removed from the Lenovo A319 phone in the standard way.
After removing the application, the image of the Lenovo A319 drive was made again.
This image was then studied with Belkasoft Evidence Center Ultimate and X-Ways Forensics 19.2. Belkasoft Evidence Center Ultimate did not detect the deleted messages (there was no “Messages” section). The search was carried out among available and deleted data: the structure of the file system of the logical section was investigated. We applied the carving method (signature analysis, carved), and searched by keywords (since the message content was known). The research time was about one hour twenty minutes. The probable reason for the lack of a positive result can be explained is that this software explores the SQLite database file (db) directly. In addition, this software can search this type of file as a result of signature analysis (carving). As a result, it can be assumed that in the event of damage to the SQLite data structures (damage or lack of signature), the evidence in the file will not be detected.
Using the X-Ways Forensics 19.2 software, entries in the free sectors of the section (image) were identified. At the same time, as in the previous case, the search was carried out among available and deleted data: the structure of the file system of the logical section was investigated; a carving method was applied; and we searched for keywords. The research took about one hour forty minutes (including research of file system structures, signature analysis, and searching for inputs). The positive result was achieved thanks to the known content of the messages.
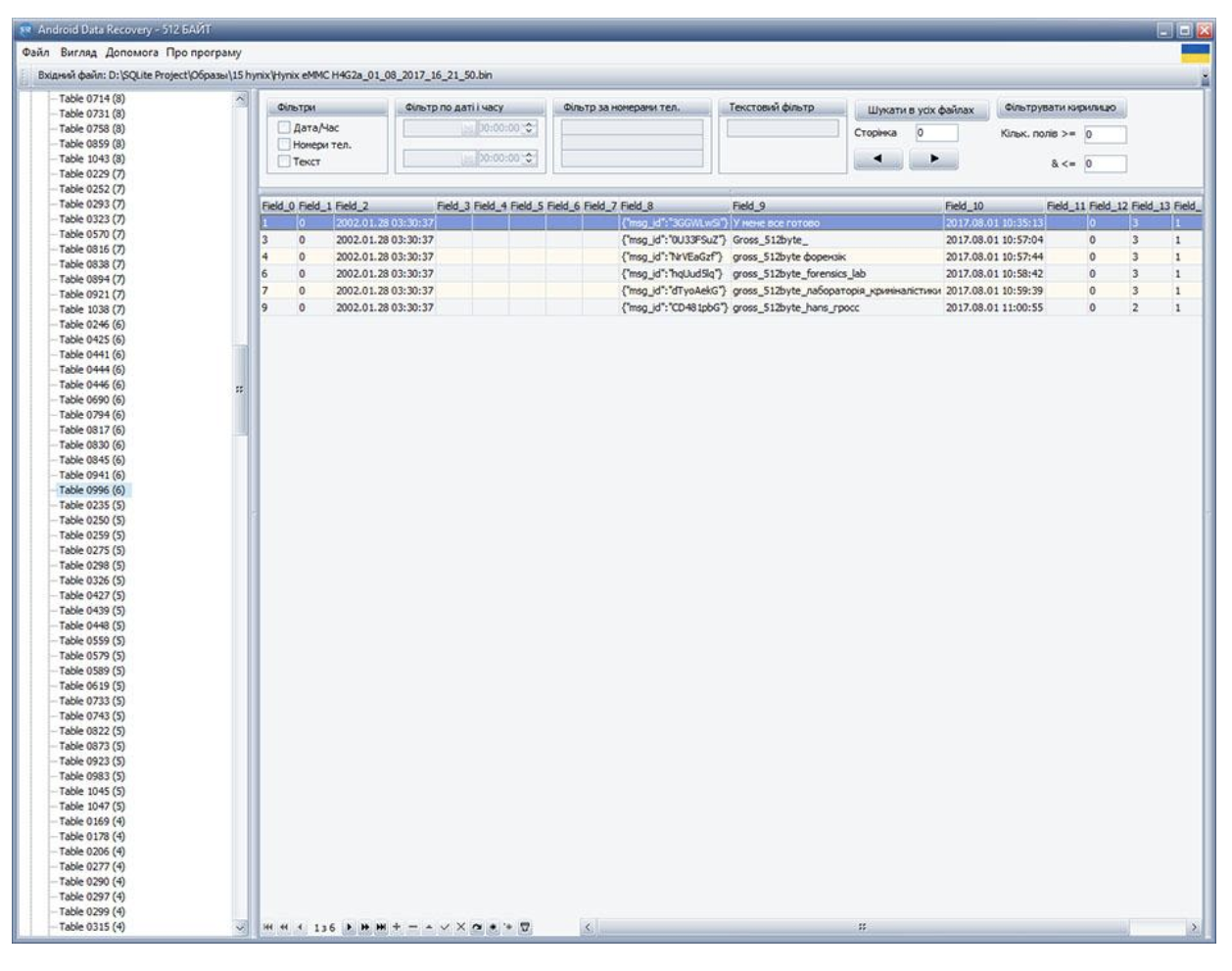
Next, the image was analysed using ADR512. The research time with the selected settings was less than two minutes. Using this software we detected the deleted messages from our test in the “imo” application.
Conclusion
This test demonstrated that ADR512 has the advantage of looking for deleted messages in front of applications that work directly with database files. The positive result is achieved due to the fact that the program ADR512 implements the search for all SQLite records, without reference to the database file.
If you know the message content, you can find it in any Hex editor. However, certain questions remain: interpretation of the fields, date and time, and most importantly, the time spent analysing the data.
In the case where the search context is unknown or the number of messages is too large, a fundamentally different approach is required. ADR512 finds the messages regardless of the content and number of records.
About The Author
Andrey Fedorov is co-owner of 512 BYTE company, specialists in data recovery, software development for data recovery and forensic analysis. He has more than 15 years of experience in this field.
















Living in the year 2018 it is a bit strange to compare an actual version of your product with a product of the first half of the year 2017. It is at least incorrect if unintentional and spoils the comparison completely if intentional.
The latest actual version of BEC 2017 was used at the time of testing but BEC 2018 was advertised as one that should be presented soon.
There’s a question. You state that it’s weird to compare BEC 2017 of the first half of 2017. So do you think that version of software didn’t work correctly? Yuri, don’t get it as comparison to offend you. We use many softwares and yours is one of them. There are many cases where BEC yield the best result than other softwares. Also there are cases where other softwares worked better. Each software has own advantages and disadvantages, nothing’s insulting here and you are gonna get it. Moreover, Andrey Fedorov noted that we don’t have any intention to offend other softwares that were used during softwares.
The article was not fully posted. In the full version:
P. S. This article in no way adversely affects the software “Belkasoft Evidence Center Ultimate” and “x-Ways Forensics 19.2”. A single case is considered.
There was no deliberate overtones.
I would advise to repeat the experiment with the actual versions of the software. It is easy to compare one product of year 2018 with a product from 1970, but not fair.
It seems like my previous respond hasn’t satisfied you. If you want to continue discuss, then okay.
First of all, let’s introduce each other to our readers. I’m Andrey Fedorov, the developer of ADR512 software, you are Yuri Gubanov, the developer of Belkasoft.
1. According to your previous feedback “Living in the year 2018 it is a bit strange to compare an actual version of your product with a product of the first half of the year 2017” do you admit that the software of 2017 hadn’t found all lost data?
2. The citation from your 2nd feedback “I would advise to repeat the experiment with the actual versions of the software.” Is it too complicated case for you?
Don’t you have any interest , as a developer, to test your own software?
If “yes”, so it’s weird
if “no”, so it’d be enough to leave the feedback the case is repeated.
Your software of 2018 solved the case.
3. Does your first feedback say that your software doesn’t have automatic updates?
If “yes” so that means all of your users have an actual version of software. As a result, you intentionally confuse the readers.
If ‘no’ so there are users with unactual versions. Then your feedback is also weird. Users work with the tool you presented to them.
4. The citation of the second feedback is “a product from 1970”. Do you think we compared your software from 1970?
5. https://articles.forensicfocus.com/2018/03/14/forensic-analysis-of-damaged-sqlite-databases/
Why haven’t you left the feedback to this citation “As we have quite a big forensic toolkit, we decided to start from trying to open the database with the most popular tools, including Belkasoft Evidence Center, BlackBag BlackLight, Cellebrite UFED Physical Analyser, DB Browser for SQLite, Magnet AXIOM and Oxygen Forensic Detective. Unfortunately, none of the tools could open the database.”?
Is there any case where your actual software doesn’t work?
We connected with authors and send them ADR512 software to test case
6. In this article we intentionally explained how we got the result step by step. We specified that we don’t want to ruin the reputation of Belkasoft. The purpose of this article was to determine the actual points of research for mobile devices.