by W.Chirath De Alwis
Digital forensics is a technique in the identification of computer based crimes. But digital forensics faces a few major challenges when it comes to conducting investigations.
According to Fahdi, Clarke & Furnell (2013), th challenges of digital forensics can be categorized into three parts.
- Technical challenges – e.g. differing media formats, encryption, steganography, anti-forensics, live acquisition and analysis.
- Legal challenges – e.g. jurisdictional issues, privacy issues and a lack of standardized international legislation.
- Resource challenges – e.g. volume of data, time taken to acquire and analyze forensic media.
Technical Challenges
With the vast development of the computer technologies within the last decade, usage of technology has been defined as both good and bad. While some people use technology to invent things to benefit mankind, criminals also use technology to achieve their own targets. One of the main problems is that as soon as a technology is developed to identify and investigate criminals, there is another technique that helps the criminals to hide themselves. This is a massive challenge forensics officers face today.
Unlike many other sources of physical evidence, digital evidence is easy to modify, remove or hide, possibly without leaving tracks that might identify the criminal. So anti-forensics has become a major challenge for digital forensics.
According to Rekhis & Boudriga (2010), anti-forensic techniques can be classified into categories as listed below.
- Encryption
- Steganography
- Covert Channel
- Data hiding in storage space
- Residual Data Wiping
- Tail Obfuscation
- Attacking the tools
- Attacking the investigators
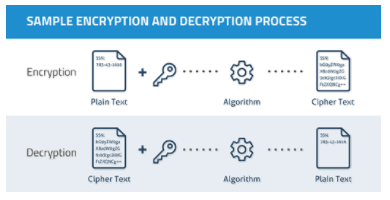
Encryption
According to TechTerms (2014), encryption is process of scrambling information that can only be decoded and read by someone who has the correct decoding key. Encryption is used to hide or make the evidence unreadable on the compromised system.
Balogh & Pondelic (2011) stated that:
In 2007, an incident happened when the US Customs found child pornography on Canadian citizen and legal US resident Sebastian Boucher’s laptop. The laptop was seized as vidence and he was charged with transporting the pornography across borders. The problem appeared when examiners tried to open the incriminating drive Z and found out that it was a Pretty Good Privacy encrypted container. Although a forensic duplicate of hard drive was created after shutdown of the notebook, the examiner could not open the encrypted container.
Attackers use many different encryption methods and in order to make the data usable, investigators have to decrypt the encrypted data. It is time consuming and sometimes the encrypted data cannot be decrypted.
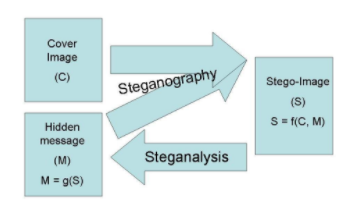
Steganography
“Steganography is an encryption technique that can be used along with cryptography as an extra-secure method in which to protect data.” (Janssen, 2014). Steganography is a technique that is used to hide any information inside a file carrier without modifying its outward appearance. Attackers use this steganography to hide their hidden data (payloads) inside the compromised system. When investigating computer crimes, the investigator has to identify these hidden data in order to reveal the information for further reference.
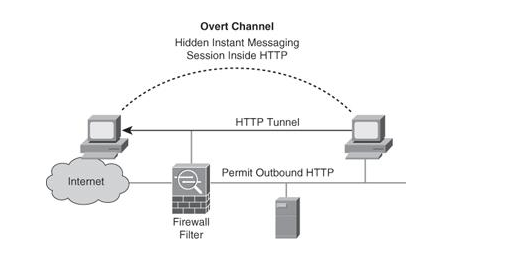
Covert Channel
“Covert channel in communication protocols allows attackers to hide data over the network and possibly bypass intrusion detection techniques. Typically, a network protocol is chosen and its header is modified to leak messages between attackers, exploiting the fact that few fields of the header are modified during transmission.” (Rekhis & Boudriga, 2010).
Attackers use these covert channels in order to maintain a hidden connection between the attacker and the compromised system. It is less identifiable.
Data hiding in storage space
Attackers hide some data inside storage areas and make them invisible to the usual system commands and programs. It makes the investigation more complex and more time consuming and sometimes data can be corrupted too. Rootkit is one of the most popular techniques used to hide data in storage space.
According to Microsoft (2014), malware designers use rootkits to hide malware inside victims’ PCs. It is very hard to identify rootkits and most computer users do not know how to remove these rootkits. As mentioned by Kassner (2008), user mode rootkits are capable of hiding “processes, files, system drivers, network ports, and even system services”.
Residual Data wiping
When the attacker uses a computer for his goal, a few hidden processes (e.g. temporary files, history of commands) are running without the knowledge of the attacker. But an intelligent attacker can avoid this risk by wiping out the tracks that were made by his process and making the system work as if it has not been used for such a purpose. Lee’s 2013 article indicates that 20-year-old Jake Davis “was convicted of computer hacking for his role in the notorious group LulzSec”. Furthermore, Lee (2013) says that he was “forbidden from creating encrypted files, securely wiping any data or deleting his internet history”.
Tail Obfuscation – attacking the tools
According to Rekhis & Boudriga, (2010), the most common technique is the obfuscation of the source of the attack. Here, the attacker uses some false information in order to mislead the investigator (e.g. false email headers, changing file extensions). Therefore sometimes the investigator might miss some data that has forensic value.
Resource Challenges
Depending on the scenario, the volume of data involved in the case might be large. In that case the investigator has to go through all the collected data in order to gather evidence. It may take more time for the investigation. Since time is a limiting factor, it becomes another major challenge in the field of digital forensics.
In volatile memory forensics, since the data stored in the volatile memory is ephemeral, user activities are overwritten in the volatile memory. Therefore investigators can analyze only recent information that is stored on the volatile memory. This reduces the forensic value of the data for the investigation.
When collecting data from the source, an investigator must make sure that none of the data is modified or missed during the investigation, and the data must be well secured.
Data sources which are damaged cannot be easily used in investigations. So it is a major issue when an investigator finds a valuable source that is not usable.
Legal Challenges
Privacy is also important to any organization or victim. In many cases it may be required that the computer forensics expert share the data or compromise privacy to get to the truth. A private company or an individual user might generate lots of private information in their day to day usage. So asking an investigator to examine their data might risk their privacy being revealed.
Casey (2011) stated that:
In 2000, during an investigation into the notorious online Wonderland Club, Grant argued that all evidence found in his home should be suppressed because investigators had failed to prove that he was the person associated with the illegal online activities in question. However, the prosecution presented enough corroborating evidence to prove their case.
It becomes a challenge when the investigator ‘accidently’ figures out or stumbles across some facts related to the crime, but is not allowed to use these against the attacker due to privacy issues. This affects the whole investigation process and limits the investigator to a point.
As stated by Bui, Enyeart & Luong (2003), ethical considerations should be examined because of the wealth of information that is collected from forensic investigations. In order to ensure integrity of the data, these should be collected and stored carefully and legally. As mentioned by Bui, Enyeart & Luong (2003) it is important to be aware of the privacy of suspects and victims. Furthermore Bui, Enyeart & Luong (2003) stated that investigators need to have good knowledge of several laws and “statutes that govern electronic evidence collection including the fourth amendment of the constitution.”
References
- Fahdi, M.L. Clarke, N.L. Furnell, S.M. (2013). Challenges to Digital Forensics: A Survey of Researchers & Practitioners Attitudes and Opinions. [Online]. P 1. Available from: http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=6641058 [Accessed 06/22/2017].
- Rekhis, S. Boudriga, N. (2010). Formal Digital Investigation of Anti-forensic Attacks. [Online]. P 34. Available from: http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=5491959 [Accessed 06/22/2017].
- TechTerms. 2014. Encryption. [ONLINE] Available at: http://www.techterms.com/definition/encryption. [Accessed 06/22/2017].
- Balogh, S. Mydlo, M. (2013). New Possibilities for Memory Acquisition by Enabling DMA Using Network Card
- Janssen, C. 2014. Steganography. [ONLINE] Available at: http://www.techopedia.com/definition/4131/steganography. [Accessed 06/22/2017].
- Microsoft Corporation. 2014. Rootkits. [ONLINE] Available at: http://www.microsoft.com/security/portal/mmpc/threat/rootkits.aspx. [Accessed 06/22/2017].
- Kassner, M. 2008. 10+ things you should know about rootkits. [ONLINE] Available at: http://www.techrepublic.com/blog/10-things/10-plus-things-you-should-know-about-rootkits/. [Accessed 06/22/2017].
- Lee, D. (2013). Jake Davis: Freed hacker faces strict tech rules. BBC news. [Online]. 24th June. Available from: http://www.bbc.com/news/technology-23029464 [Accessed 06/22/2017].
- Casey, E. (2011). Digital Evidence and Computer Crime. 3rd ed. USA: Elsevier.
- Bui, S. Enyeart, M. Luong, J. (2003). Issues in Computer Forensics. [Online]. P 7. Available from: http://www.cse.scu.edu/~jholliday/COEN150sp03/projects/Forensic%20Investigation.pdf [Accessed 06/22/2017].
About the Author
Chirath De Alwis is an information security professional with more than three years’ experience in Information Security domain. He holds C|EH, C|HFI and Qualys Certified Security Specialist certifications. Currently, Chirath is involved in vulnerability management, incident handling and digital forensics activities in Sri Lankan cyberspace. You can contact him on chirathdealwis@gmail.com.