DRONE is AIR’s built-in automated compromise assessment technology which dramatically reduces the time required to identify IOCs in a DFIR investigation and begin containment and remediation. DRONE flies above your live systems and data acquisitions to deliver an unparalleled decision support system.
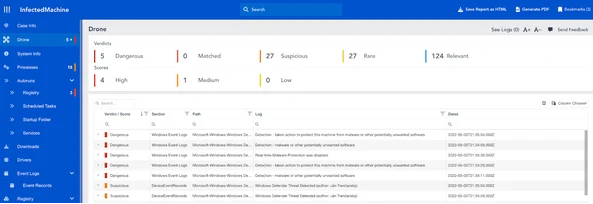
DRONE will guide analysts, helping them ‘pin-point’ anomalies in the shortest possible time by labeling what is Dangerous, Matched, Suspicious, Rare and Relevant.
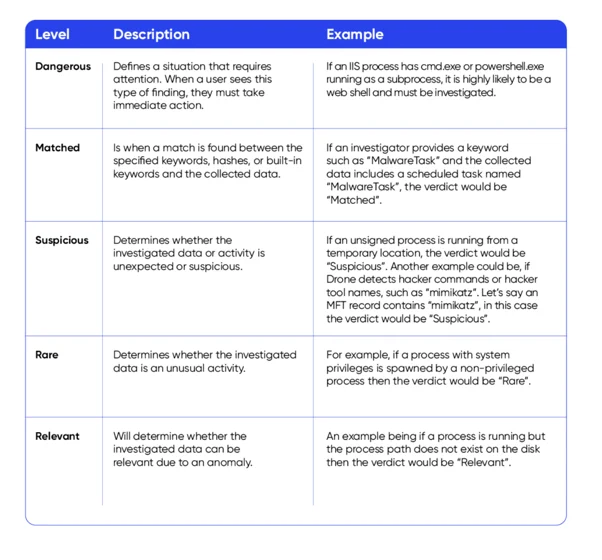
Where DRONE cannot come to a specific verdict it uses ‘evidence scoring’ to prioritize all findings using High, Medium or Low classification…
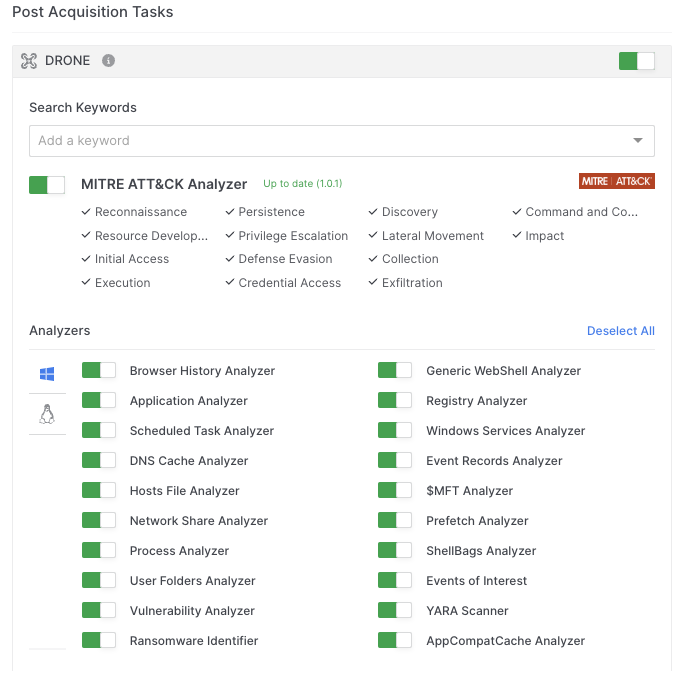
Analysts can easily enable or disable DRONE, or any of the individual analyzers in AIR, by toggling the associated switches on or off, either when setting up automated acquisition profiles or before manually launching an AIR task.
Disabling DRONE will still give you an AIR acquisition report for your collection, but with no compromise assessment, verdicts or scores.
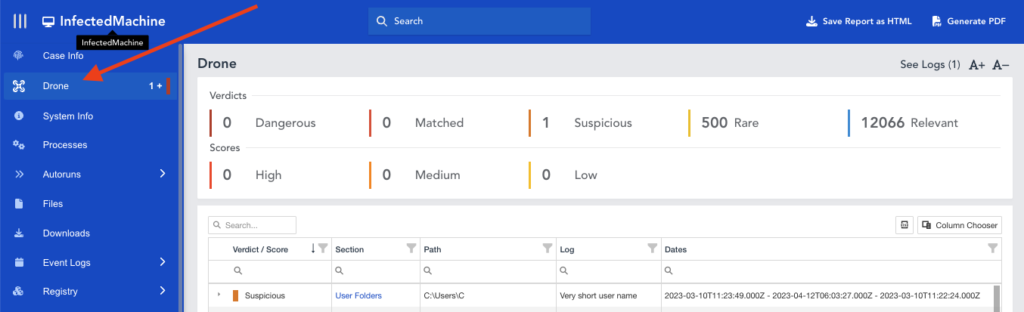
In this example case report, we can see that DRONE was run as part of the acquisition profile as it features in the left menu as indicated.
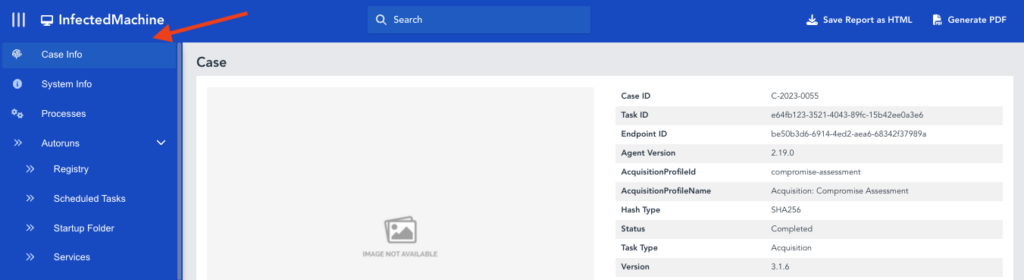
But, in this second case report we can see that DRONE has not been run, so the case report will simply present the parsed acquisition data without offering any assessment or guidance as to where to direct the investigation.
DRONE, Your Fully Automated Decision Support System
Each evidence item is processed by DRONE’s 20 proprietary analyzers (see table below) which check for specific characteristics of the evidence data.
Each analyzer has multiple stages through which the evidence item must pass to identify if the item is ‘correct’ or not.
DRONE will then score and report on any item which displays attributes that the analyzer believes may be worthy of further investigation, along with detailing the reasons for highlighting issues with that particular item.
DRONE is not simply detecting malware, in fact malware detection is only a small part of the process and a by-product of its MITRE ATT&CK scanning. The DRONE analyzers deliver much more and provide guidance to the investigator as to where to prioritize their efforts to help speed up the entire investigation.
Without DRONE, analysts will, as they have done for many years, work their own manual ‘pipelines’ and processes using a variety of often very slow legacy forensic tools.
For example; they’ll have to select and investigate individual processes, consider entropy, sort it to look for possible encryption, sweep over commands, filter for ‘unsigned’, sort by username, creation time etc etc… then do it all again for the next item.
It’s an extremely manual, laborious and time consuming process.
DRONE automatically does all of this and more for the analyst, and this whole process can be further automated by leveraging Webhooks (integrations) and access to the AIR API.
So, the very first thing the analyst may see after a breach is a DRONE report pointing them immediately to the areas of concern. Below we’ll look at a scenario where DRONE is being utilized.
Within AIR, an alert has triggered an acquisition which DRONE has automatically processed and then generated a report for, that has highlighted actionable items worthy of further investigation.
The Process Analyzer discovers an unsigned process running, DRONE reports a finding with a “Relevant” verdict to bring it to the attention of investigators.
Let’s take a look at what the DRONE levels indicate to the analyst and give some examples:
The pipeline is ordered by the verdict level descending, so this means higher-scoring verdict rules are checked first and as soon as there is a hit the pipeline does not need to be checked any further.
Next let’s take a look at how DRONE scores items:
Some rules, by themselves, may not be worth reporting, but when brought together with others, could assist in solving a case.
For example, in the Scheduled Task Analyzer, DRONE checks the command lines of scheduled tasks. If one line is “cmd.exe /c start C:\temp\m.bat”, it would be captured by two scoring rules:
- The item has a scripting extension – the ‘.bat’
- The item’s location is unusual.
The result of this is that the item is reported with a score of 65, which means that it scores “Medium” for the DRONE report.
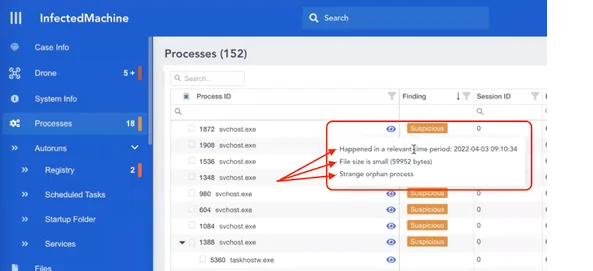
Here DRONE has identified 3 reasons to mark this Process as Suspicious:
- It was very recently created.
- File size is small – often the case with malware.
- svchost.exe was not started by the expected parent. (services.exe).
The score may determine the verdict but not vice-versa.
Once a verdict is achieved the artifact does not progress to the later stages of the pipeline.
The pipeline is ordered with the verdict level descending, so this means higher-scoring verdict rules are checked first.
Another example of how the score of an item can result in a verdict can be seen with date relevance:
This function is used to check if the item’s date and time stamps display activity at a time relevant to the incident under investigation:
SuperRelevant is between now and 1 week
HighlyRelevant is between now and 3 weeks
Relevant – between now and 3 months
In all other cases the function return is Irrelevant
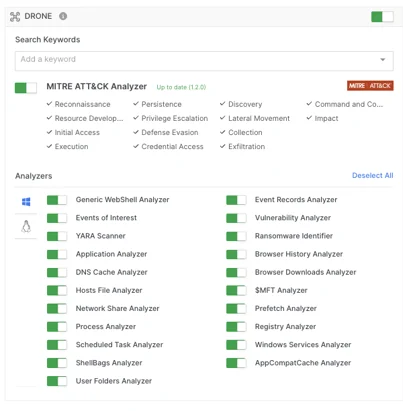
Within AIR, when you toggle off the ‘DRONE’ option, this will reveal individual switches for all of the analyzers, so you can select them on an individual basis as required for your investigation.
This analyzer pipeline process is implemented by proprietary algorithms, so they’re not publically available.
Let’s look at another example: Imagine AIR’s collection engine, has collected all of the artifacts requested in an acquisition profile, and passed them to DRONE for post acquisition analysis.
As we now know, DRONE has a number of analyzers, and each of them executes rules for the specific type of artifact collected. For example, the “Process Analyzer” executes the rules related to processes only.
Let’s say AIR has collected 5 processes and we’ve 3 rules in the processes analyzer, in reality DRONE actually has many more rules in the pipeline for the analysis of processes. The 3 rules will be executed against each of the 5 collected processes, so basically this pipeline has 3 stages through which the process artifact must pass.
This means, a process artifact visits only 1 pipeline. Most of the analyzers work in this way right now, but this is not a constant behavior and can be changed according to needs.
Let’s take a look at some more information about the DRONE analyzers:
Browsing History as an example, here we check the URLs for; Cross-Site Scripting, XSS strings, Macro Enabled Extensions and Blacklisted domains.
- So, any document files downloaded with macros will result in a finding
- Any strange domain extensions identified will also equal a finding
- Application categories such as Bitcoin wallets will also be shown as a finding.
The Ransomware Identifier analyzer is based on YARA rules and runs on the endpoint not the collected Case File data. We only search using these YARA rules in specific paths;
- Running process paths and sub directories
- Prefetch paths and subdirectories
- User folders and subdirectories
- Recycle bin folders
The Events of Interest analyzer takes a look at certain events of note – a good example being where there has been a lot of RDP connection requests in the night, this will equal a finding.
The DRONE Generic Webshell Analyzer will also detect 95%+ of Webshell compromises.
Let’s take a look at a more detailed list of the DRONE analyzers:
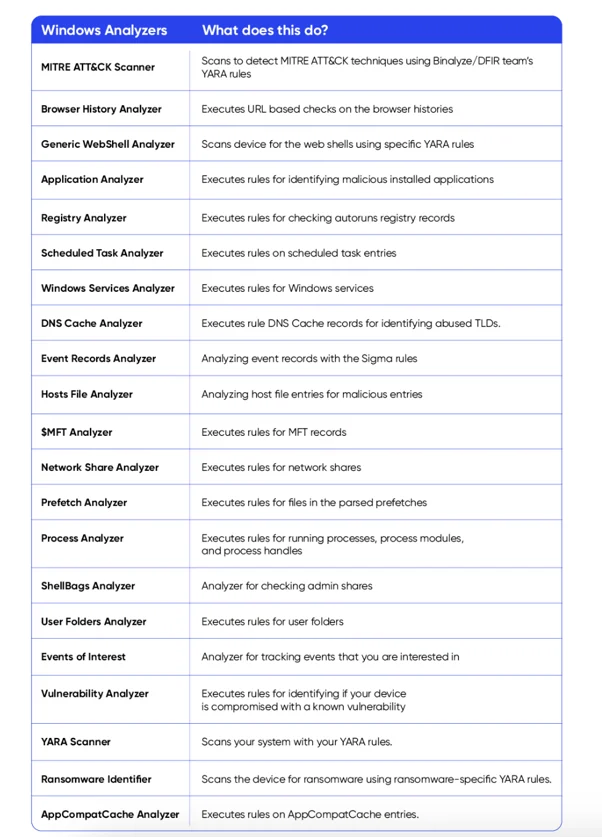
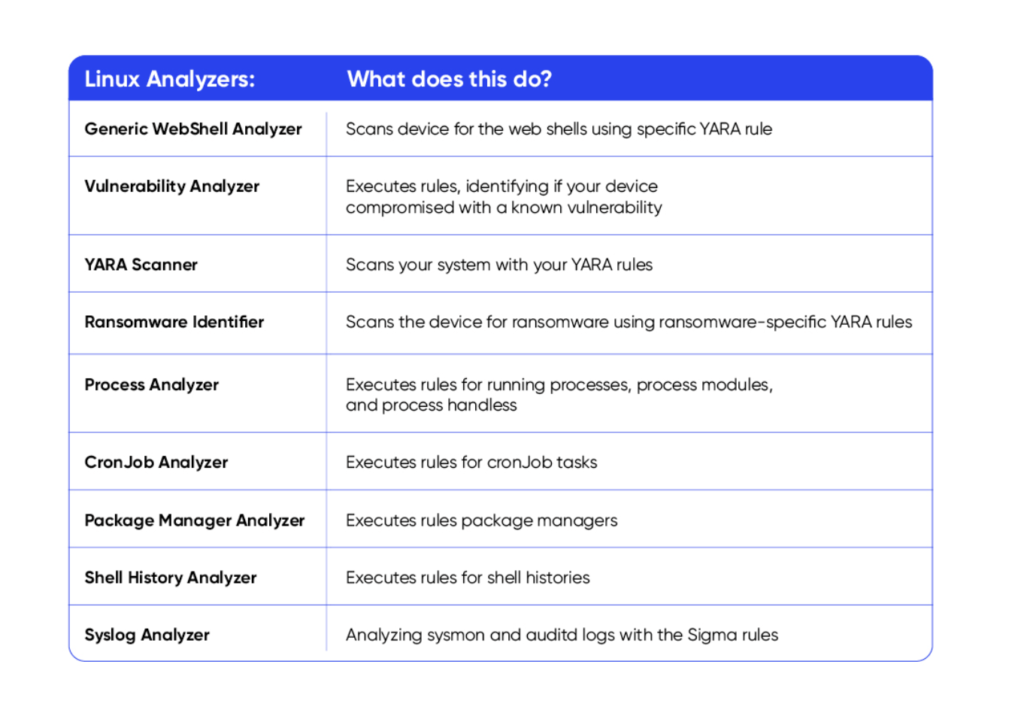
The MITRE ATT&CK Framework is globally recognised as a leading knowledge base with a standardized language of adversary tactics and techniques based on real-world observations.
The MITRE ATT&CK scanner implementation in DRONE is an extremely powerful analyzer which delivers huge benefits through over a thousand YARA rules constructed for detecting potential Indicators of Compromise, IoC’s, and TTPs, Tactics, Techniques and Procedures. The subsequent findings can be used to piece together critical information as part of any DFIR investigation.
Thanks to the exhaustive R&D work carried out by our world-class DFIR Lab team, the DRONE MITRE ATT&CK scanner combines high levels of detection rates for malicious indicators with extremely low false positive hit rates.
Looking at the DFIR process as a whole, with the MITRE ATT&CK scanner in place we’re now delivering a platform that supplies analysts with the most comprehensive solution for DFIR investigations. This information gives key pointers and direct signposting as to where and how breaches may have occurred.
As with all parts of AIR, we’ll continue to enhance this capability – adding further rules to shorten overall investigation times and reduce the potential for data loss and reputational damage.
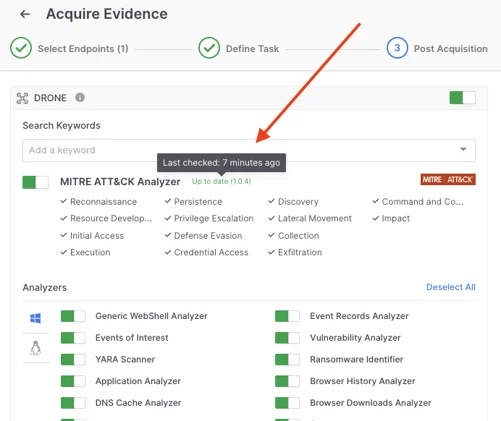
AIR now automatically checks every 30 minutes for any new MITRE ATT&CK rules that the Binalyze Threat Hunting Team have written. If you don’t have the latest version, the new rules will be pushed to your AIR platform automatically, potentially saving yet more valuable time, and avoiding any delay to you having access to the latest rule sets.
With our comprehensive analyzers, customers will see the attack stages, the footprints of any attackers, and which of the Tactics in MITRE ATT&CK were used.
By using this option, users have a greater understanding of what the attackers intentions were and what they’ve done in their systems. We then have three verdict levels representing how serious any discovered threat is.
So let’s take a final look at how the MITRE ATT&CK scanner results are reported as one of three possible DRONE verdicts:
First up, a ‘Dangerous’ DRONE verdict will indicate specific malware families or TTPs that are only ever used by malware.
A good example here would be any Yara rule that reported returns for Mimikatz, this would be marked as Dangerous.
A ‘Suspicious’ DRONE verdict aims to highlight indicators that are ‘more than likely’ to be used for malicious rather than legitimate purposes.
An example here would be a Yara rule under MITRE scanner that detects any executable with the ‘Onion’ domain address associated with it – On the Tor network, this is sometimes used by ransomware operators.
‘Relevant‘ is the lowest verdict level used by AIR’s implementation of MITRE ATT&CK . This level is intended to show indicators where we can’t say for sure they’re malicious without further analysis.
A good example would be either a password protected archive, or a macro enabled document. These file types are typically used for legitimate purposes but in recent times have gained popularity amongst bad actors for exploitation and therefore may warrant further investigation.
Deploy DRONE in Your DFIR
Binalyze AIR is the disruptive force in the DFIR space right now. This is because we combine lightning fast forensics with automation, supporting a wide range of integrations with which SOC analysts can today, easily and quickly remediate incidents.
All of this is further enhanced with DRONE’s powerful capabilities, enabled with just one click. Along with new enhancements like our Consolidated Reports, this single, easy-to-read DFIR intelligence report, displays all of the Verdicts and Scores from multiple endpoints in one pane of glass.
So, if you’re ready to see how AIR and DRONE’s automated compromise assessment can make a difference in your organization, help maintain a more resilient cyber security posture, and save you time – why not sign up for a free 14 day trial?
















