If you are like many digital investigators, you’ve heard about the Autopsy™ digital forensics tool and associate it with a course that used Linux to analyze a device. Or, maybe you associate it with a book that made references to the Linux/OS X tool, but it wasn’t applicable to you at the time because you were using Windows. This article is about how Autopsy 3 is different. In fact it is a complete rewrite from version 2 and is now applicable to everyone. It will change the way you think about digital forensics tools.
Runs on Windows and Easy to Use
Let’s start off with the fundamentals: Autopsy 3 runs on Windows with an easy to use, double-click installer. No dependency hells that you may typically associate with open source tools. No esoteric download paths or source code repositories to navigate through. Just download the latest from http://sleuthkit.org/autopsy and run the installer.
Note: We’re also working on the Linux and OS X packages, but Windows has been the primary focus. Stay tuned for when these are available.
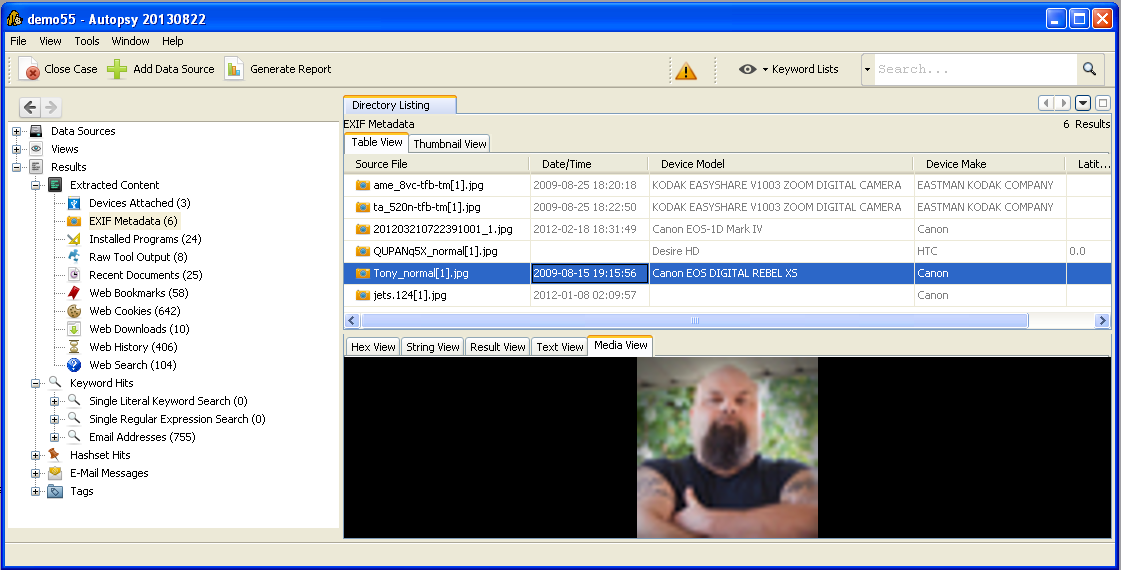
Autopsy 3 has been developed with an overarching goal of providing an intuitive layout and workflow. For instance, all analysis results are found in a single tree on the left-hand side rather than strewn about in several areas.
Autopsy has wizards to guide you through each step of the process and has many interface features to make your investigations faster.
For example:
-
When you find a file from a keyword search or hashset hit, you can right click on it to view its parent directory to see what else is near that file.
-
Back and Forward history buttons to allow you to backtrack when you realize that your investigation went down the wrong path.
-
The “views” node in the main evidence tree contains many common file type, size and date based filters to quickly and easily view files that meet these criteria.
Familiar Features and Fast Results
Now that we’ve covered that Autopsy 3 is more applicable than you may remember, let’s cover how it can help you. It has the standard set of features that you need from a digital forensics tool and most of the features you’ll find in commercial offerings:
-
File system analysis and recovery using The Sleuth Kit™, which has support for NTFS, FAT, Ext2/3/4, Yaffs2, UFS, HFS+, ISO9660
-
Indexed Keyword Search using Apache SOLR (More…)
-
Hash database support for EnCase, NSRL, and HashKeeper hashsets.
-
Registry analysis using RegRipper
-
Web browser analysis for Firefox, Chrome, Safari, and IE including automated discovery of bookmarks, history, and web searches
-
Thumbnail views and video playback
-
MBOX Email analysis
-
Visual Timeline analysis (More…)
-
Tagging and Reporting in HTML and Excel
-
Coming Soon: 64-bit support and Scalpel integration for carving
Autopsy is also built to give you fast results. As soon as you add an image to a case, the analysis begins and continues in the background. As soon as a hash hit is found, you’ll know about it. You won’t need to wait until the entire drive is done. Autopsy prioritizes how it analyzes the files to focus on user content first.
Extensible and Evolves With Your Needs
Autopsy 3 was designed to be a platform for 3rd-party modules. Development began after the first Open Source Digital Forensics Conference in 2010 when discussions highlighted the need for a platform that would allow a user to perform an end-to-end investigation using open source tools. People were tired of needing to use several stand-alone tools with different input requirements and report formats to perform an investigation. Autopsy 3 was developed to be that platform.
Autopsy 3 has several frameworks in its design to allow other developers to write plug-in modules. Here are some examples:
-
Ingest modules run on the disk images and logical files to extract evidence and artifacts from them. Many of the features previously listed, such as keyword search and hashset analysis, are implemented as ingest modules.
-
Content viewer modules display a file to the user in different ways, such as Hex, Video playback, or static analysis of an executable.
-
Report modules create a final report for the investigation
We know Autopsy 3 can’t solve everyone’s problems straight out of the box and we want developers to write modules instead of stand-alone tools. Writing modules is easier than stand-alone tools because the Autopsy platform takes care of all the boilerplate forensics development, like knowing about disk images versus logical files, UIs, and reporting.
If you are a developer, we have full module writing documentation and sample modules . To motivate you a bit more, Basis Technology is organizing an Autopsy module writing competition. Developers have until Oct 21, 2013 to write a module and the attendees of the 4th Annual Open Source Digital Forensics Conference will get to vote who gets the cash prize.
Free
You can download the Autopsy installer and get up and running on your Windows machine from http://www.sleuthkit.org/autopsy/ or you can visit the source code repository at https://github.com/sleuthkit/autopsy and see the inner workings, repackage, and improve the software.
Note: We are also planning on a developer focused article, so stay tuned for that.
If you run into any problems or have questions, submit them to the sleuthkit-users email list. If you have any feature ideas, then submit them to the github issue tracker.















This seems to be a great advancement for users. I installed it easily and ingested an E01 test image.
The interface is logical and well displayed, My one issue was that I did not get any MD5 values in the Directory Listing table. I did not see any tool/command to extract them (post-ingestion) and populate the table. What am I missing?
When you add the disk image, you are given a list of ingest modules to run. One of them is Hash Lookup. It does both calculation of MD5s and looks them up in databases that you have configured. Even if you didn’t add a hash database, it will still calculate the hashes if you have the module enabled. The module will hash files in the background and add them to the table as they are calculated.
In the next release, the hash is included in the HTML report for tagged files.
Good Work team. Have been a fan of autopsy tool after i started using SIFT workstation for Analyzing certain incidents. The windows version will save my time from switching physical machine to VM for running certain jobs using autopsy. I tried parsing a E01 image file where the partition table entry is Fdisked or deleted. The entire chunk is displayed as unallocated space. is there a way to point out the partition table entry for this tool? so that it can run the desired jobs?
Not at this point. The priority has been on the general use case scenarios. The Sleuth Kit infrastructure is currently there to allow the user to specify an offset and to from there, but we haven’t added the pseudo-carving feature to scan for file system signatures if none are found in the beginning and try to open them. I just made a feature request for this (https://github.com/sleuthkit/autopsy/issues/289).
very simple to use and with a lot features such as index search,but the current version does not support multiple selection to export deleted files
3.0.7 will (or if you are brave, you can pull the latest and greatest code from the github repository and build it). 3.0.7 will be out end of this week or early next week.