by Chirath De Alwis
The invention of the Unmanned Aerial Vehicle (UAV), also known as the drone, has the potential to address some crucial issues in society. Commercial aerial surveillance, oil/gas/mineral exploration, and disaster relief are some of them [1]. Considering the increasingly popular use of drones, it is evident that there is potential for them to be used in crimes. This demands forensics investigation.
When it comes to analysis of drone artifacts, GPS data plays a huge role. It is vital to answer to questions like where was this drone flying? From where this drone was sent? This article describes evidence acquisition from drones and extraction of GPS information from drone artifacts.
Drone Structure
To operate a drone requires the aircraft, a mobile device, battery, camera, radio controller, and/or Wi-Fi range extender (some models do connect using Wi-Fi). The structure of a drone can be vary based on the vendor, design and purpose. But most commonly, drones consist of a main board, GPS module, gimbal image stabilization, and sensors.
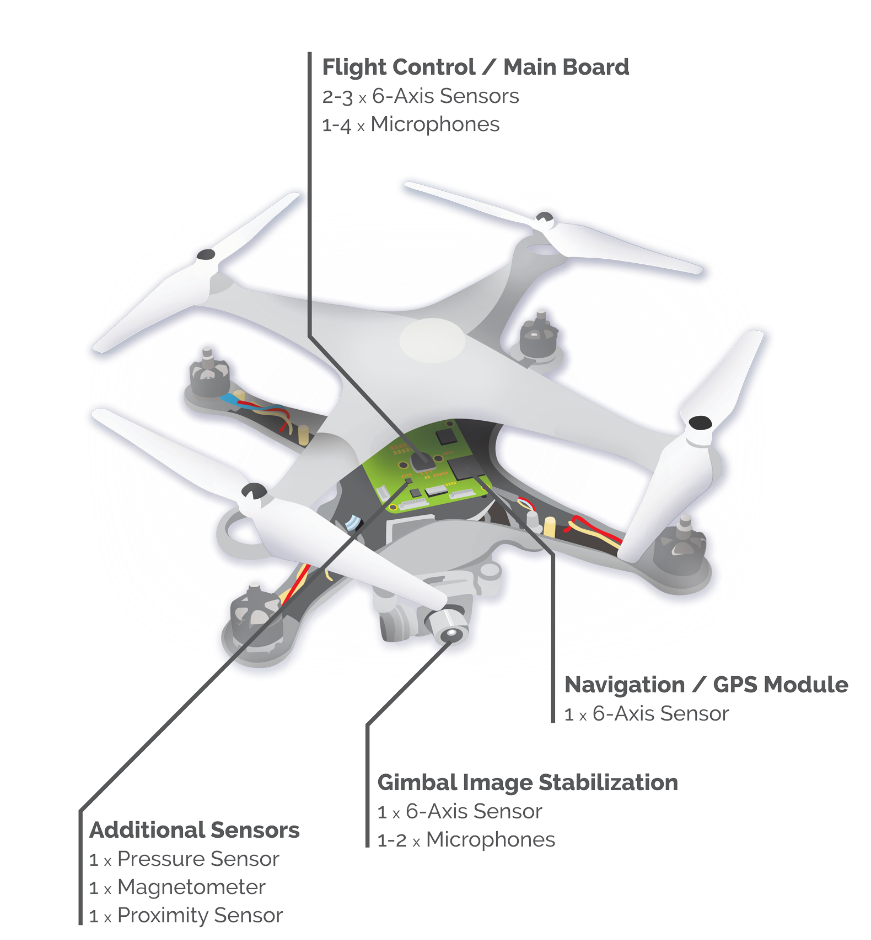

Evidence in Drones
A drone’s primary evidence is stored in the mobile device connected to both the drone and its remote controller. To control the drone requires a controlling application inside the mobile device connected to the controller system. DJI Phantom 4 Pro drones use the app “DJI GO 4,” available in both Android and iOS. This application primarily stores data inside its application folder and provides the capability to the user to upload the files into DJI cloud.
Once these local files are synchronized to the cloud, users can delete them from the local storage. It is important to know that users have an account to login to. To get the previous flight details, users have to login into their respective account using DJI GO 4 applications. The same drone can be used or controlled by different users by connecting each of their mobile devices to the controller, but flight information from these captures will not available in the original user account.
The DJI Phantom 4 Pro contains a 4GB SD card as its primary storage medium. In some drone models, this storage medium is glued into the board. This chip also contains some interesting files when it comes to analysis. Since this DJI Phantom 4 Pro drone does not connect to its controller via Wi-Fi, we cannot perform wireless connection to this drone.

Evidence Acquisition
Data Acquisition from Drone
Linux is the predominant OS for onboard UAV systems and it is possible to perform mobile forensic techniques to collect the data from the drone. It is possible to dump the file system directly from the drone using the “DD” Linux tool. Following is a command to perform this function: [3]
ssh 192.168.1.1 -l root “dd if=/dev/mtdblock3 ” | dd of=root.dd
Data Acquisition from SD Card
We can get the data directly from the SD card by connecting the SD card to the workstation, or we can access the SD card though the drone itself.
Data Acquisition from Mobile App
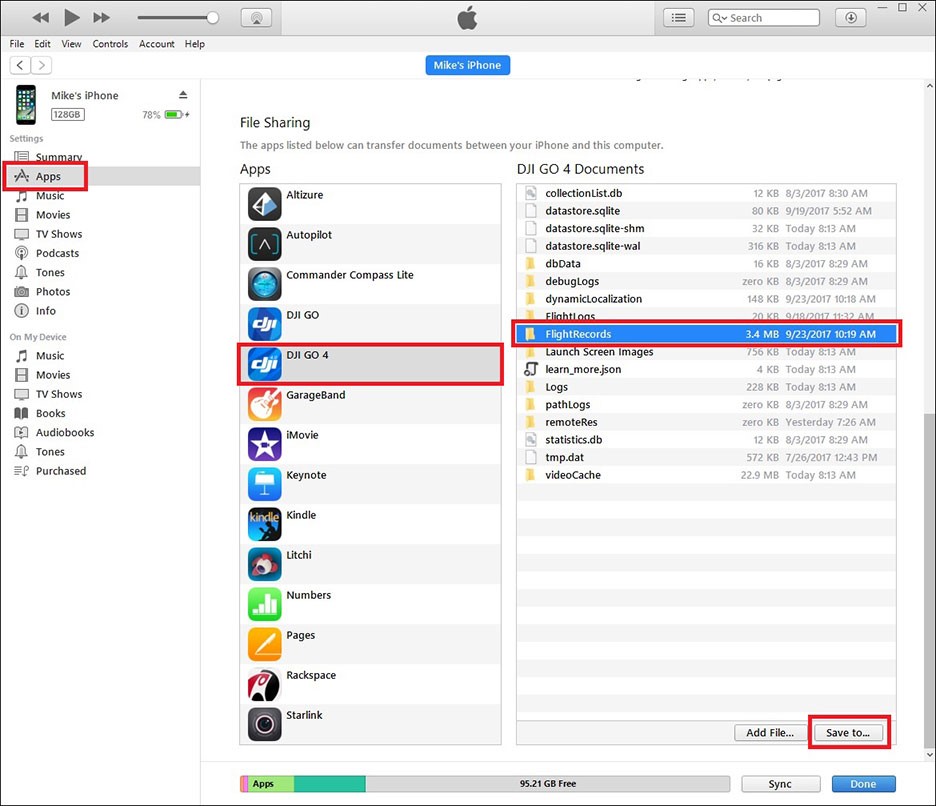
A considerable amount of data can be extracted from the DJI GO 4 mobile application. This data can be extracted using normal mobile forensic methods. If the device run iOS, then it is possible to extract data from iTunes. If the device is Android, it is possible to extract data from via the Android Debug Bridge (ADB).
Analysis of GPS Locations
Apart from recorded videos and pictures, the most interesting and important information that can have a forensic value is GPS information. When investigating GPS data from drones, there are three main places where GPS data is stored.
- Inside the application (flight details)
- Inside the drone
- Inside the captured files (videos and pictures)
From Flight Logs
Flight details are recorded inside the mobile application. In order to extract flight logs it is required to log into the account and synchronize data into the cloud. If the data is not stored in/synchronized to the cloud, then the data is stored inside the mobile device.
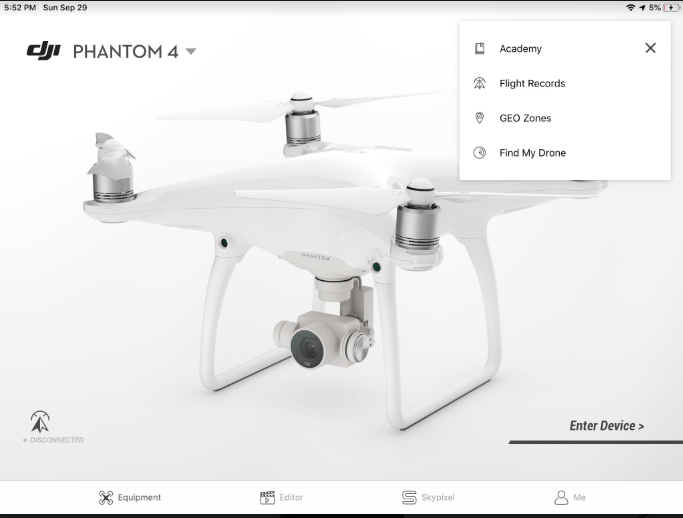
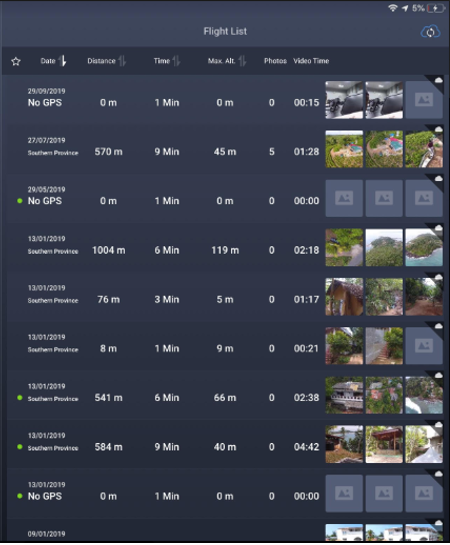
Following are the list of steps required to export flight logs from the DJI Phantom 4 Pro:
- Connect to the DJI GO 4 app.
2. Select the drone type.
3. Select Flight Records from the menu in the top right corner.
4. Now it is possible to see all the flight details. Select the flight you need to export.
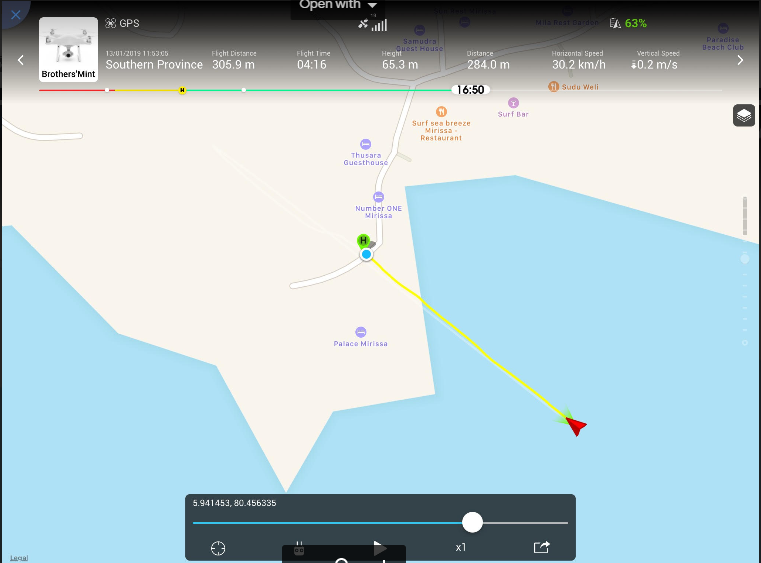
5. You can view the flight path here as well.
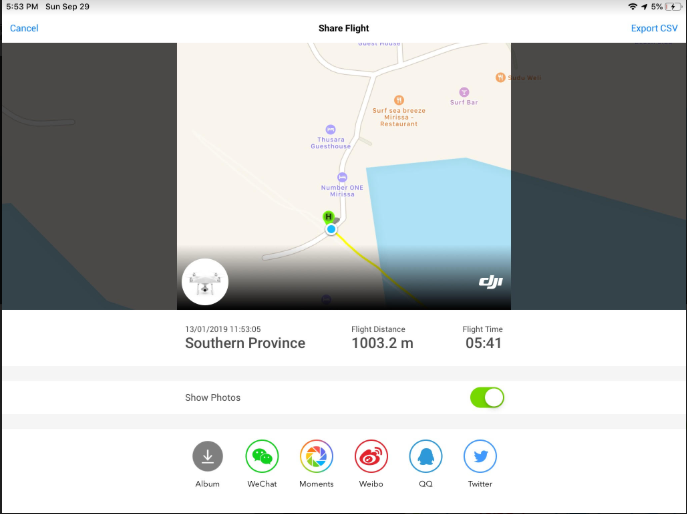
6. Click Export.
Once export is successful, these flight records are available inside the application folder and normal mobile forensics techniques can be used to extract these files. These flight records are stored in “.txt” file format and the naming convention will look like “DJIFlightRecord_2017-07-11_[15-25-14].txt”. Some flight records contain pictures, and these can be carved using header- and footer-based file carving techniques.
Drone activity since the drone started to fly is recorded inside the “2019-01-18_10-43-24_FLY812.DAT” file. This file can be opened and viewed using the “CsvView” tool. This tool converts .DAT file into .CSV format.
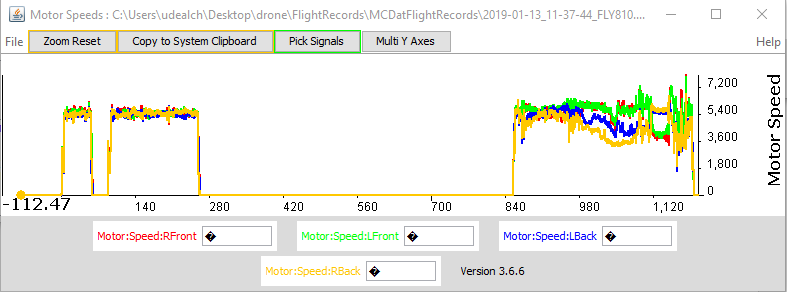
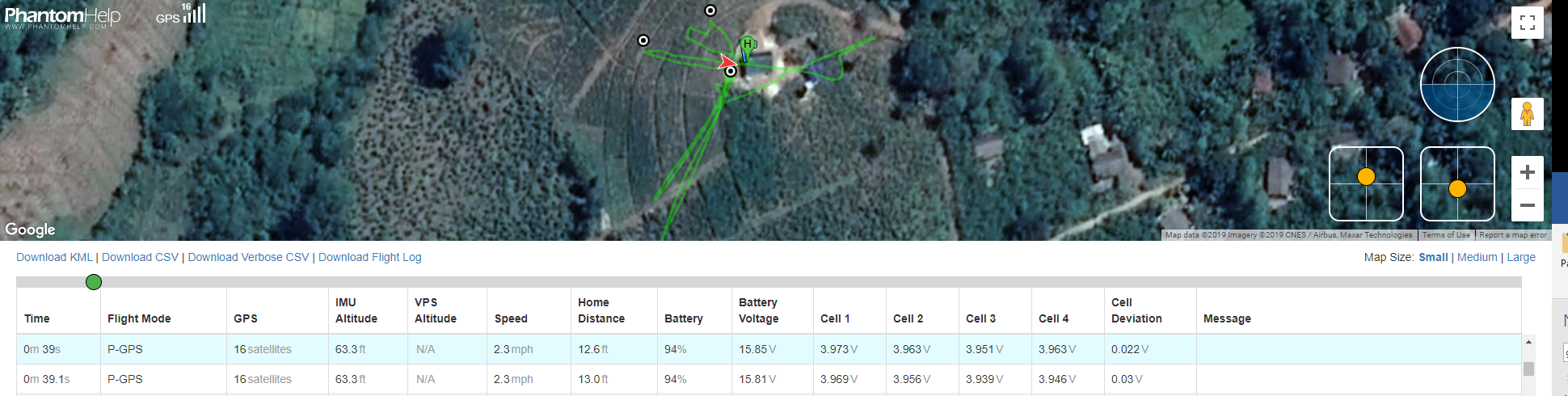
These flight records contain lot of information. Some interesting data includes aircraft name, date, maximum altitude, maximum speed, landing battery, takeoff battery, sensor information, images, controller average response time, etc. These details can be extracted using the “app.airdata.com” website [6]. Since this tool does have a paid version, using paid version avoids publishing flight data for public use.
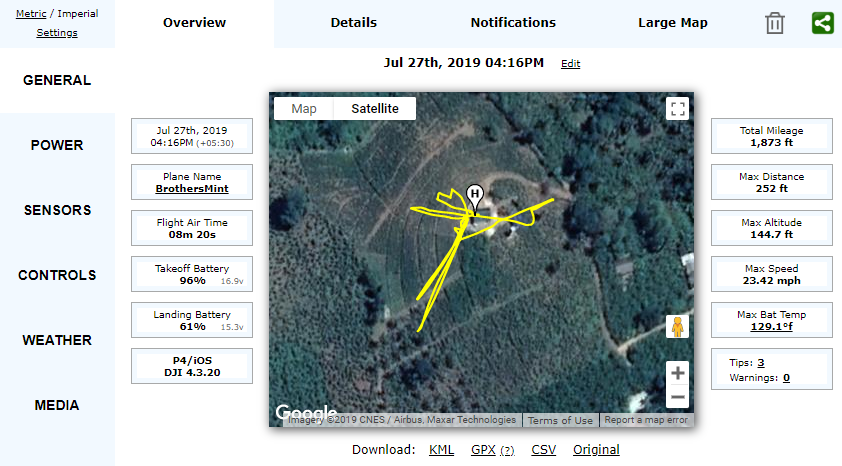
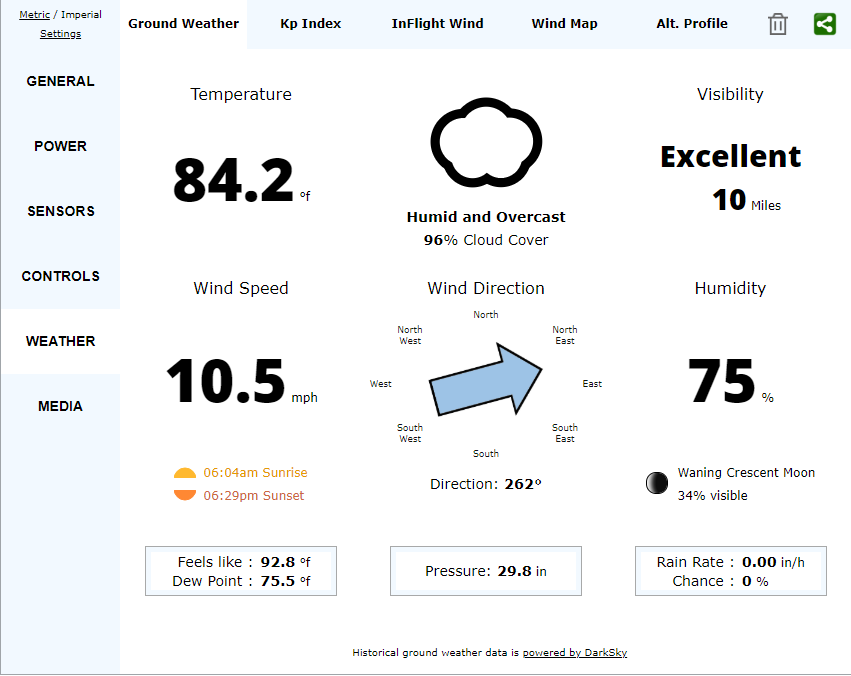
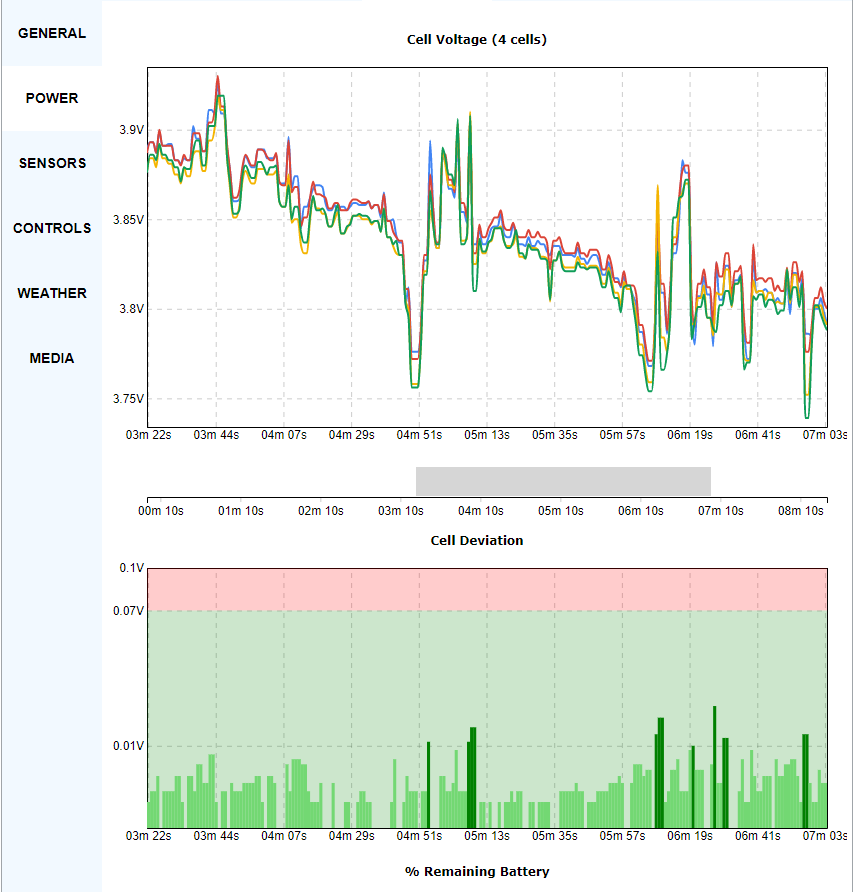
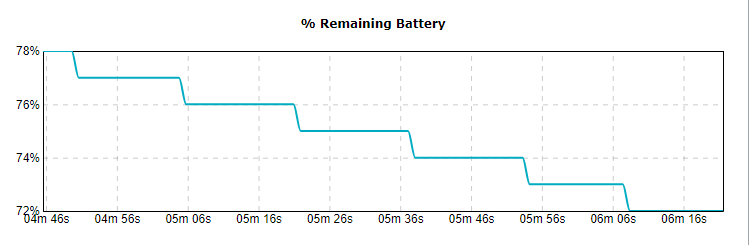
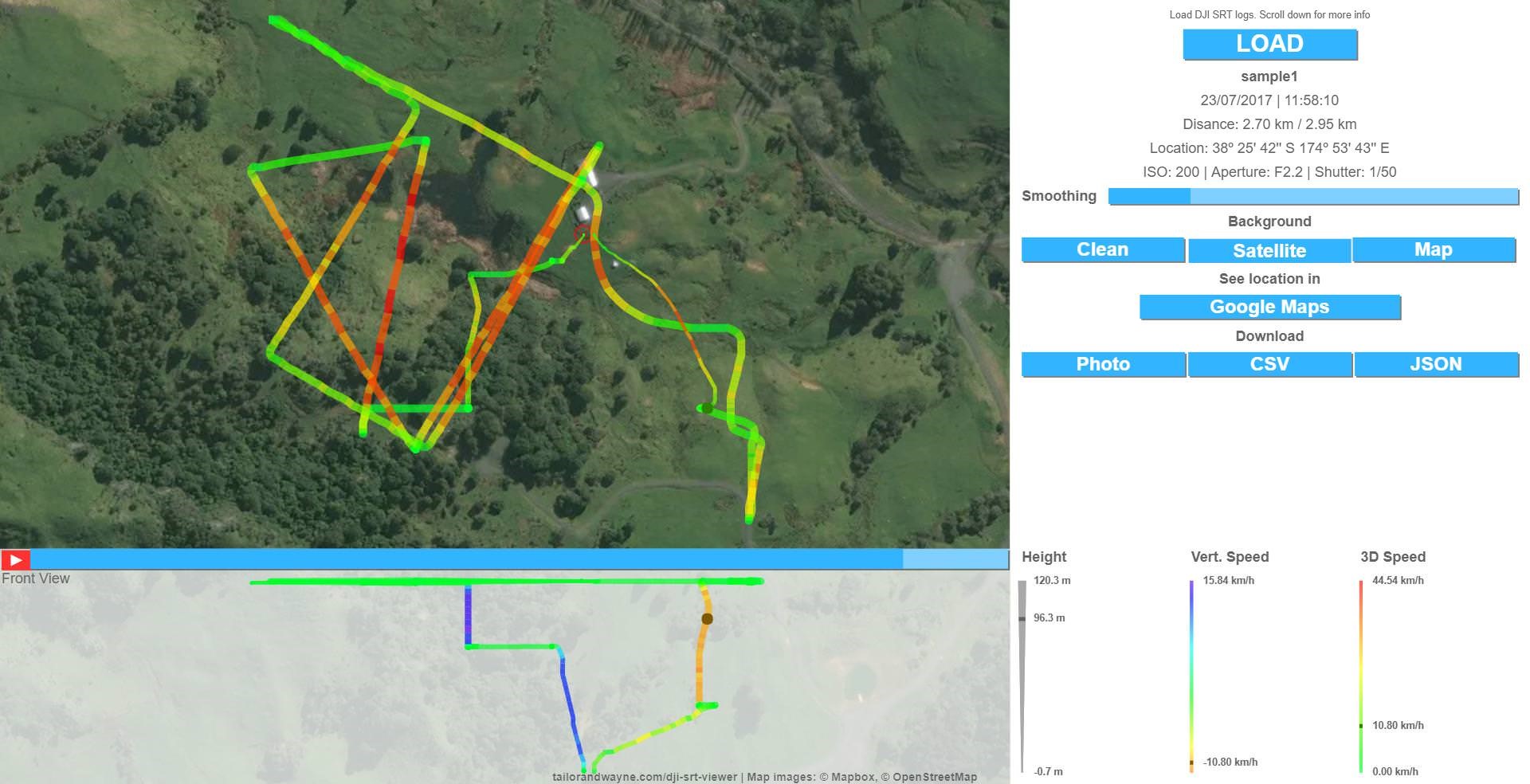
Apart from these details, it is also possible to visualize the flight path. Phantom Log Viewer [7] is another online viewer that can be used to visualize this information. Forensic use of this tool is not recommended, as it can make uploaded data publicly available. Therefore, it is recommended to use “CsvView” tool to visualize the data.
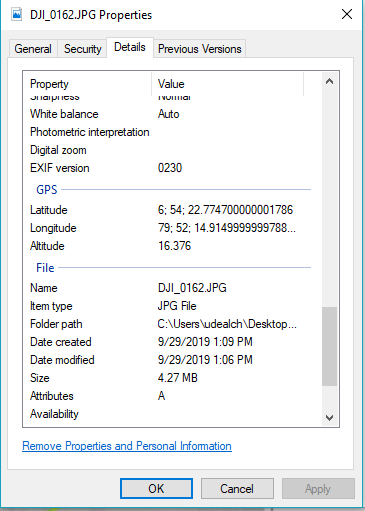
From Image Metadata
Image metadata contains some useful information for forensic investigations. It is possible to get the GPS information from image metadata. The data can be found from file properties or by uploading the file to “pic2map” [8]. For forensic use it is recommended to use file properties and input the coordinates directly to Google Maps.

From Drone Captures
By default, drone captures do not contain GPS information. It is required to enable GPS from the application settings. In order to enable this in the DJI GO 4 app, the user must enable “video capture” from the settings. The following picture depicts this step.
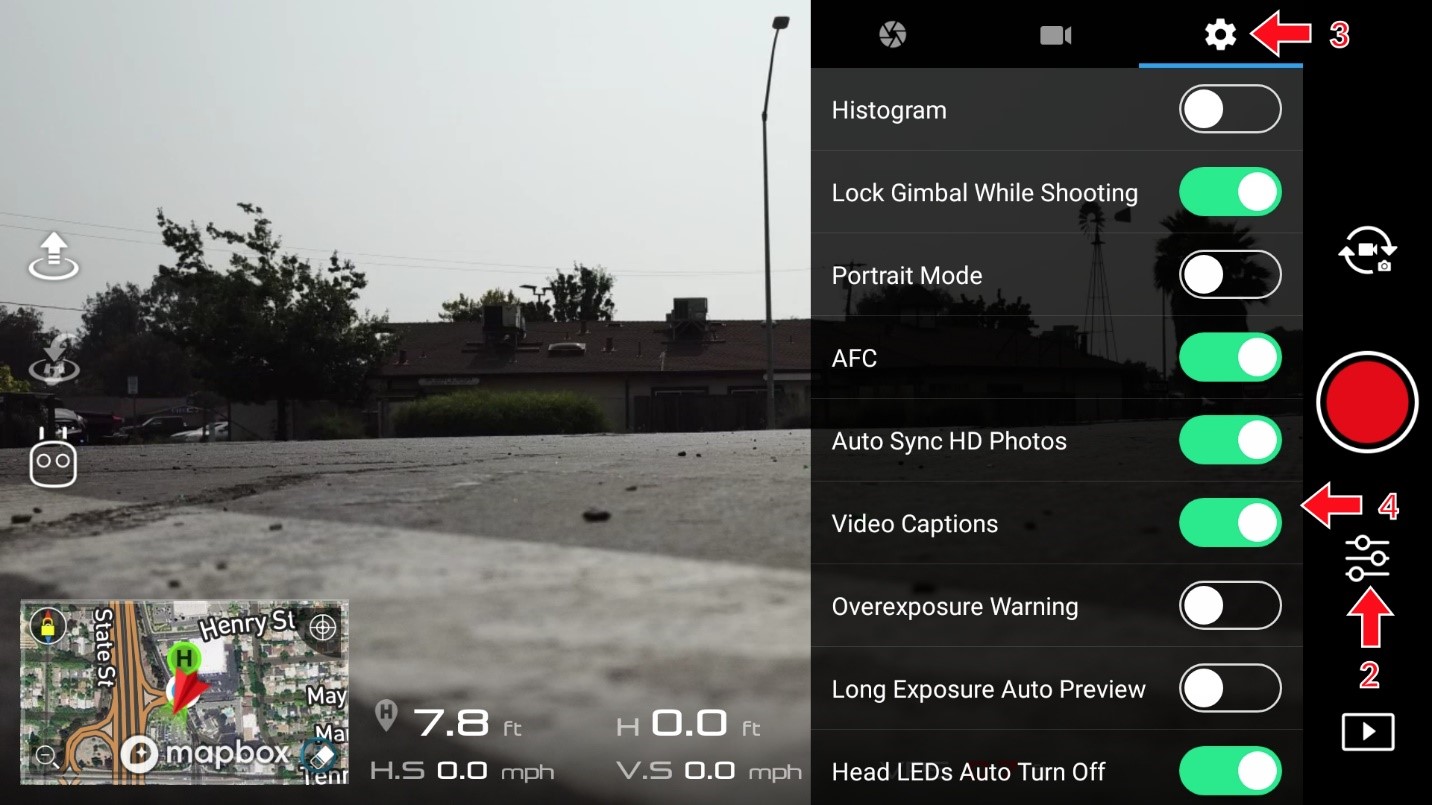
Once this video capture is enabled and starts recording, it creates two files: a main video file, and a new file with an .SRT file extension. This .SRT file contains the GPS locations and can be analyzed using https://tailorandwayne.com/dji-srt-viewer/. For forensic analysis, it is recommended to use the “CsvView” tool. Some drones, like the Phantom 2 Vision+, store the GEO information along with the video files in a new file with an .EXIF (Exchangeable Image Format) extension.
Reference
- https://www.dummies.com/consumer-electronics/drones/popular-uses-for-drones/
- https://dronelife.com/2016/09/06/top-5-drone-component-companies/
- https://www.sans.org/cyber-security-summit/archives/file/summit-archive-1492184184.pdf
- https://dfrws.org/sites/default/files/session-files/pres_drone_forensics_program.pdf
- https://commons.erau.edu/cgi/viewcontent.cgi?article=1513&context=jdfsl
- https://app.airdata.com/flight/last
- https://www.phantomhelp.com/LogViewer/Upload/
- https://www.pic2map.com/
About The Author
Chirath De Alwis is an information security professional with more than four years’ experience in Information Security domain. He holds BEng (Hons), PGdip and eight professional certifications in cyber security and is also reading for his MSc specializing in Cyber Security. Currently, Chirath is involved in vulnerability management, Threat Intelligence, incident handling and digital forensics activities in Sri Lankan cyberspace. You can contact him on chirathdealwis@gmail.com.

















This is a nice piece of work. Well done. Thank you for contributing to the community’s knowledge!