Justin Tolman: Welcome to this week’s episode of FTK Feature Focus. This week we have another special episode with a special guest: Dan Sumpter, who’s the principal instructor at Exterro over North America. Dan, how are you doing?
Dan: Hey, thanks for having me.
Justin: Hey, always good to have you here. And what we’ve got Dan on to talk about today is Project VIC. If you’re in the law enforcement industry, you’ve probably had to deal with cases dealing around child pornography or child exploitation, child trafficking, all those types of different things that break down and go into those different areas. Of course, we have different names for a lot of the same thing.
Fortunately and unfortunately, right, Dan, in my law enforcement career, while I worked cases that dealt with that I never dealt with Project VIC. For whatever reason, the organizations that I worked for, Dan, we just didn’t interface with it, but I know you did. And so here we are. And so, Dan, tell us a little bit about Project VIC.
Dan: So in order to even look at Project VIC, to find out about it, a lot of people don’t even know it exists, the first thing you’ve got to do is law enforcement. I mean, it’s hands off if you’re not in law enforcement. So even to get involved in that, you have to be a sworn officer in some aspect.
But Project VIC, it’s a collaboration of a bunch of people’s work, you know, law enforcement’s work. And it’s a collection of hash values of known child exploitation, videos, and pictures, and it’s housed so to speak at the National Center for Missing & Exploited Children. So that’s where all of these hash values are at or disseminated from. And remember; it’s just the hash values, not necessarily the pictures or videos.
So I wanted to get into that, I got into forensics, I knew that that was going to be a part of it. I needed to take that next step to be able to have access to the software and the hash sets and everything. So I got involved with the Internet Crimes Against Children organization here in Cleveland, Ohio.
And once I got hooked up with Dave Frattare, who’s the guy in charge over there who still is, nice guy, he got me involved with the training classes, he got me access to IcacCops, which is a website strictly for this. You’re heavily vetted, you’re heavily trained in being able to access this stuff. Once you get access to it though it’s a plethora of information and tools.
And I really can’t get into exactly what it is as far as that goes. But just to know that we are able to identify pictures and videos based off of a file signature or hash from the file signature and the file itself is amazing, you know? So Project VIC is just another tool for us to identify these exploitation videos and pictures, and identify that on a suspect machine or suspect media from being identified in the past by law enforcement.
Justin: Yeah. I think that’s super important because the saying’s often, you know, like, every time these images are shared, the victim is kind of ‘revictimized’, right? That’s kind of the idea here. And Project VIC is another tool to help stop that victimization by rapidly identifying victims that, yes, this is this and ties it, that this is confirmed contraband and hopefully stopping the spread of it, slowing the spread of it, right, through the Internet.
Dan: Well, I’ll tell you it probably spread more than we think, because there are new releases of hash sets all the time, it’s updated on a constant basis. So that’s officers that are uploading more known videos and pictures that have been shared that weren’t there a week prior that it’s just growing in size all the time.
Justin: So we had a podcast a little bit ago where we talked with someone who deals with trauma, with investigators as well as victims, and using hash sets like this can help speed up investigations, I think helping reduce the amount of time an investigator spends wading through garbage. Did you find that in your experience as well?
Dan: Yeah, but it’s like during your investigation and then at the end, if you happen to come across new hash values that aren’t in the system, then it’s on you to identify what’s the content, write a synopsis of that content and then upload it later.
But during the investigation, yeah, I could run an image against our known file filter that I used and it would tell me, “Hey, this one’s no good, this one’s no good.” You know, it’ll just start alerting me on the suspected files. And, you know, maybe I don’t have to look at all 1000 of them on this guy’s hard drive and I just need to pop out 10 known files that are already confirmed by the system to keep me from having to watch an entire video over and over again, you know? So yeah, it definitely helps with my mental wellbeing.
Justin: Yeah, we can’t let it go any further down, can we, Dan? Well, yeah, those types of texts are super helpful. And we have been working to implement tools to obviously incorporate that help into things like FTK. And so this is FTK Feature Focus. And so what we want to do is take a look at how FTK kind of allows the investigator interface with that.
Now, as you mentioned earlier, we can’t show things dealing with the ICAC Project VIC NCMEC side, that’s highly controlled, but what we want to show is what FTK does that helps the investigator to categorize and create their data set to either give back to Project VIC or to get it organized, so.
Dan: Yeah. So with FTK, what’s nice is these hash sets come to us in a JSON file? So definitely more than a glorified text document, so to speak, right? That document does nothing more than organize data for us. It doesn’t do any sort of programming or anything. So it just holds those values for us.
And then we will input those into FTK using our known file filter tool. So it’s way easy. We teach it in our 101 class, we teach it in our 201 class, so it’s used a lot. And yeah, depending on the size of that JSON file, it might take a minute or two, but then we’ll import that as a known file filter. And then we can apply that, we can run that filter before we make our case, pre-processing, or you can do it later on and run it against specific files that you have in your file list or check mark or filtered out so you can see them. So it’s pretty robust when you get those hashes thrown into FTK.
Jason: Oh, perfect. And one thing I will say is you talked about all the services provided to law enforcement are locked down. I should say the same thing with FTK, you do have to have a law enforcement tag on your license to access the Project VIC features.
And so if you are law enforcement and you’re like, “Hey, I don’t have this.” contact your sales rep. They can get that flag added to your license so that you of course have access to those features. We want to make sure that law enforcement has access to that.
So, Dan, do you think you could at least show us how to bookmark in the features associated with that Project VIC bookmarking here in FTK?
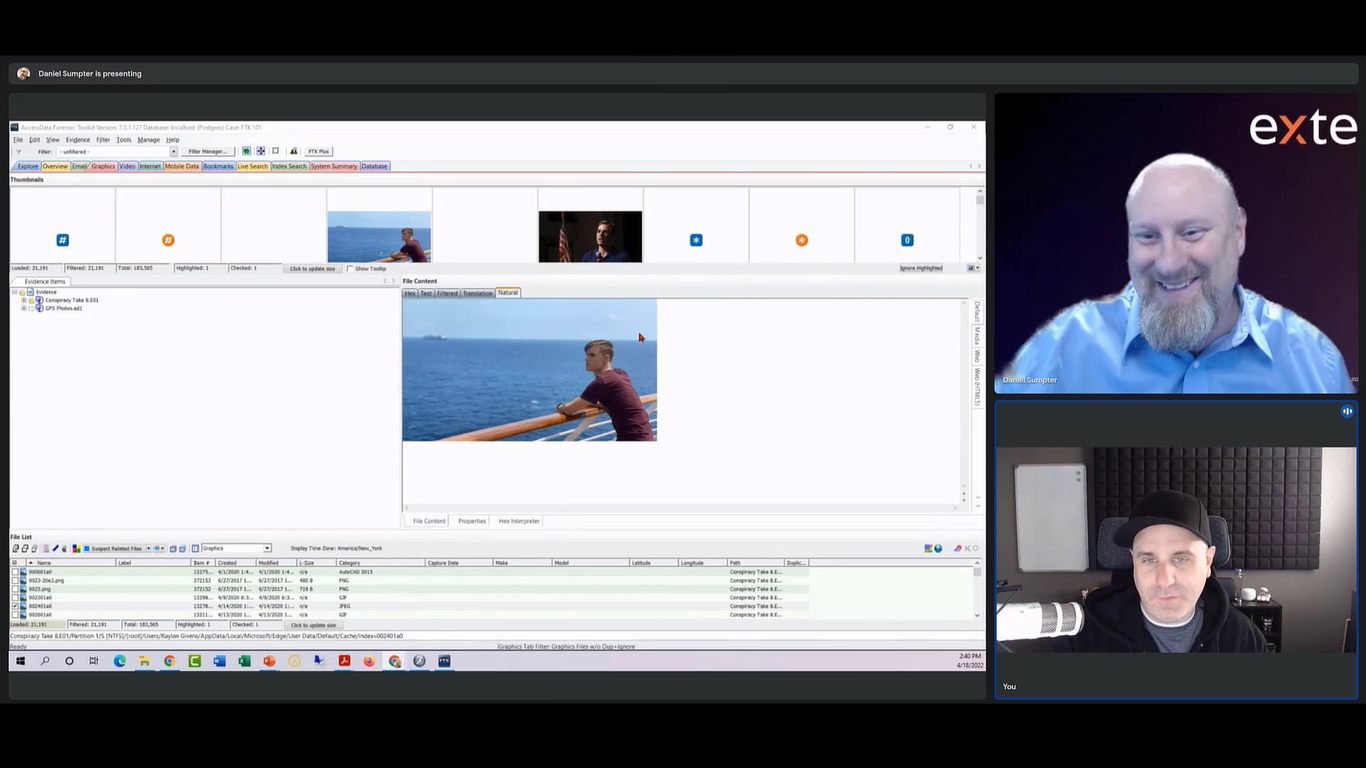
Dan: Yeah. Let me share my screen here and I can knock that out. So as you see here, I have FTK up. I did most of my investigations when it came to child exploitation, videos and pictures, either from the videos tab or the graphics tab. So I’m in the graphics tab now. And I just have some random picture up and we can just pretend that this is a child exploitation photo, right?
Justin: I’d be concerned if it wasn’t a random photo.
Dan: Yeah, we might get in trouble if it was otherwise. So it’s really easy. You know, a lot of our users already know how to make bookmarks. A lot of times in some of the training, when there’s not law enforcement in the training, we kind of skip over the Project VIC stuff, and we have a little button here next to our little multicolored labeling button. We have this little, it says “VIC” really small, if you can’t see it, that’s what it says.
So you can hit that once you have a file checkmark highlighted, selected, or you could just right click, as well. And then we have create a Project VIC bookmark here. So there’s a couple ways of doing it. And if you’re familiar with FTK, there are a couple ways of doing everything in FTK, which is kind of nice. So there’s no wrong way of doing it.
So this is specifically for Project VIC’s content. So for instance, let’s say that picture is what we wanted to bookmark as a child exploitation video or a picture. As you can see at the top, you have your bookmark name, we can fill that out, I could write whatever the file name I want, or ‘something child video’, ‘child picture’, whatever I wanted to put in there that’s relevant to that file.
The Project VIC case number is next. That that usually comes from your IcacCops account. So let’s say for instance, I see something that’s in there and I want to take over or start an investigation, then a case number will be assigned to it.
So I’ll use that case number in here and add it to that. Just another way to file all of these files that we’re actually going to be looking at.
But one of the biggest things here, we have a dropdown for categorization. So in Project VIC, those assets are categorized themselves. And so you have animation, you have child abuse, child exploitation. Then we have comparison images, non-pertinent, or maybe something’s just uncategorized that you saw on there, and you think that it’s probably child exploitation, not too sure, or there’s just not a category for it. You know, if there’s not a category for it, then I’ll usually make a separate bookmark and then I’ll put everything inside that bookmark. So you’ll have a sub bookmark, so to speak.
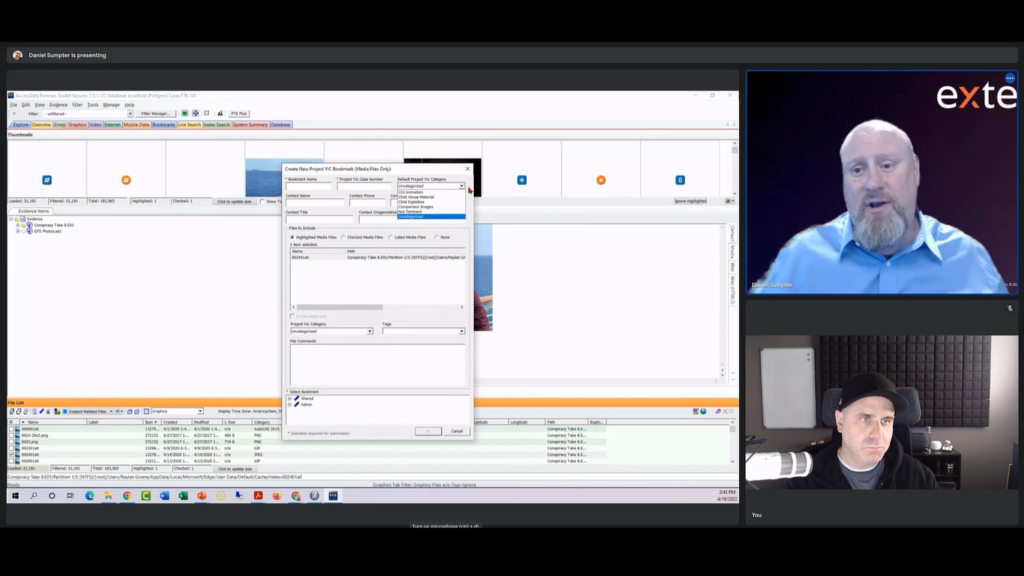
So maybe if I had, you don’t see anything, it doesn’t say actually videos, like comparison images, maybe comparison videos or something like that. You know, I would want to add that. But if this was exploitation, you could mark it as such, and then you could put your information in here.
You know, my name would be Dan Sumpter, my contact phone number, my work email, title, and the department that I work for, right? And then once I make sure I have my target items selected, then you have another shot here to change that category if you didn’t already at the top. And then you could add some tags, too.
So here you can add, well, is this going to include an infant because in the federal system and in some state courts, the younger the child, the worse the offense is. Or is it just violent and not including those or is it the S&M bondage type of stuff? So you have additional tags, as well.
And then you always have room for a comment if you want to put some more information in there, that’s up to you. And then once you pick your bookmark then you’ll be able to save and hit OK, and it’ll show up in the bookmarks tab.
Justin: And just to clarify, the categories and the tags, those are populated by the organization, Project VIC NCMEC. That’s not something that the user here in FTK creates, right?
Dan: No. That’s automatically populated from their hash sets.
Justin: And then the other thing too, is this is not a single file at a time required, right? You could do all checked files, all listed, that sort of thing as well.
Dan: Yeah. And then the one thing that most law enforcement guys don’t do or forget to do, it’s a lot of work doing a case like this in the first place. But yeah, I could select this whole list. I have 21,000 showing, I can checkmark them all and throw them all in that one bookmark if they were all related to that type of investigation.
But the one thing guys don’t do at the end, they make the report, they copy all their evidence, they send all their reports and evidence to the courts and put it away for holding. The last step in all these cases is uploading your assets back to Project VIC so that they can add those if they’re not already in their system.
So for instance, let’s say I identified a bunch of pictures or videos that maybe some guy created on his own. Those are probably not known, right? Well, I can hash them myself using FTK. And then I can put all of those files that I know that aren’t in the Project VIC hashes and list them here on this file list.
And then we could export this file list and upload those hashes to NCMEC so that they can be used for the next guy, or maybe I’ll do another case down the road and it’ll hit on it again. So that’s the last step that a lot of investigators, I don’t don’t know if they forget, but sometimes it’s just overlooked.
Justin: Yeah. You’re onto the next case, as soon as you’ve done that one. It’s just like, “I’ve got to go to the next one and I’ll upload it.” Yeah, yeah, yeah. But then tomorrow is code for never, you know? And then the cool thing about it is that with your contact information, like you were saying, you found this stuff that was created by this person. If they had any questions as to the case or needed background information, that would allow an investigator down the road to call you up or email you or whatever.
Dan: Yeah. I mean, if you and I both had access to the same accounts, like IcacCops, we can look up that case and look at everything that you did in that case. And I can say, “Oh yeah, this video was already marked” or, “This suspect was involved in this case.” So there’s a lot of interconnectivity, so to speak, with investigators with these resources.
Justin: I think that’s important. I think networking and communication between investigators on the good side has been a topic both in law-enforcement-style forensics, as well as corporate and agency forensics lately. And incident response is trying to get the people on the good side that are protecting to communicate more because the bad actors definitely don’t hesitate to communicate with each other and network and build these undergrounds.
Dan: Yeah. You’ll see, if you start doing a lot of these cases, you’re going to start seeing the same images, the same collection of videos from one guy to another, cause they’re just sharing it between each other, and they’re using those peer-to-peer networks.
And so, unfortunately a lot of those collections, so to speak, are recognizable just by the name of the folder, and I’ll be like, “Oh, not this one again.” You know? So when you start getting into the job, you’ll know exactly what you’re expecting to see when you open up a folder due to the naming.
Justin: Cool. So that’s Project VIC, right? In a nutshell.
Dan: Yeah, exactly. Yeah, I mean, obviously there’s a lot more to it, but if any of the investigators out there want to get involved in this, a lot of people are like, “No I’m never going to do that kind of work.” Right?
But if you think about it, like you said, in our opening, these victims get revictimized over and over again. And if it’s a baby, a toddler, a little kid that can’t talk for themselves, then if you can get comfort in knowing that you’re their voice, then it makes it worth it at the end of the day when you find the bad stuff.
And I’m going to tell you, most of those guys don’t want to go to trial when a forensic expert finds evidence. They’re pretty quick to, “Oh yeah. I’ll just take 15 years and go to prison,” or for longer than that. So that might not be what everybody wants to see as far as the end result, they might want to see something worse or something longer.
But when you could get some kind of justice for those victims, and just to add a little tidbit to that is that there are — part of NCMEC what they do is, the re-offending like you were talking about and re-victimization — there are victims out there that are older than you and I, and their child exploitation videos are still being shared, but there have been funds set up or like a suspect that has been fined in court millions of dollars or whatever.
And any time that revictimization happens, that victim gets compensated. And I know a lot of those victims donate that money back to the National Center. So that’s something a lot of people don’t know that no, they’re not actually putting the money in their pockets and going shopping. They’re giving it to this organization to help the next victim.
Justin: That’s great. And I think that’s a great coverage of Project VIC and the good that it does. And I think our training department is doing their part, as well. I think we’ve offered some free training for law enforcement or are offering coming up here and at your new on location stuff, as well.
Dan: Yeah. So we’re offering right now for the next like three weeks. I think we’ve got a couple weeks every month where we’re offering FTK Imager for law enforcement professionals. I’ll be teaching that as well as one of our new instructors, Kate.
And then on the UK side, I know Daz and John are going to be teaching that in London at the London office. So yeah, we have a new facility in Covent Garden in London, and then here in the US in Frisco, just outside of Dallas. So keep your eyes open for law enforcement-only classes there, too. We’re going to try to get something organized very soon for that.
Justin: Perfect. The thing I like about Imager and the fact that people may think, “Oh, it’s just Imager.” but the cool thing about Imager is it can create hash sets that are compatible with submitting to NCMEC.
So it’s a free tool out there in imaging, get the training that you need so that you can at least at minimum create the hash set of a drive, a jump drive, a couple of images, a folder, and again, get that information to the people that can archive that and help us do more about it, so.,
Dan: Yeah, for sure, for sure. I think it’s a good tool. Everybody knows about it, you know? And everybody likes the price. So I like it too, you know? When we were new at this, I had several copies of it sitting in a thumb drive somewhere. So yeah, definitely. But it’s a powerful tool, it can do what we need it to do, and taking that extra step to get those hash sets is pretty important for closure of the case, for sure.
Justin: Cool. Well, Dan, thanks again for jumping on an episode of FTK Feature Focus. Hopefully we’ll see you again.
Dan: Thank You.
Justin: Have a good one.