Authors
Alan, Kelvin, Anthony and Zetta (VXRL)
Disclaimer
This framework was first introduced in DFRWS EU 2014 (the first DFRWS conference in Europe) at Amsterdam held in May and later presented at Hacks in Taiwan 2014 (HITCON) which is a high-tech security conference in Taiwan held in August.
Abstract
Digital forensics investigators are facing new challenges every day because there are a large variety of high-tech cybercrimes reported. For instance APT, Hacking, Ransomware and DDOS etc… During investigation, investigators are often too concentrated on the evidence itself, like reversing the malware for the detailed behaviors or analyzing packets for credential leakage, but seldom or having difficulties to draw out the whole picture of the incident by correlating the seized / acquired evidences for the intelligence purpose. All relevant data from seized media should be utilized and analyzed, later transformed to intelligence so as to build a profile of the potential suspect with the corresponding attributes.
Based on the principle of Zachman Framework, we propose and design an Investigation and Intelligence Framework, which is an automated mechanism to identify the potential suspect at the early stage for the ease of the further investigation, correlating evidence to oversee the entire picture of the cybercrime. Our framework has adopted four of the intersections, i.e. When, Where, Who and How. 4W of the incident should be the concerned factors no matter what type of cybercrimes happened. To fulfill this 4W concept, related artifacts including timeline, location, identity and attack path would be effectively recognized at the earlier phase, and investigators can tackle the cybercrimes more successfully. Analyzing the evidences with intelligence for example VirusTotal, PassiveTotal, PhishTank and MalProfile[2], the artifacts can be transformed into new pieces of intelligence and build the possible story of the incident / crime for further investigation.
Introduction
Cybercrimes are advancing every day, investigators are facing more and more challenges, but they are often too focused technically, hence miss out to draw whole picture of the incident by correlating the seized / acquired evidences for the intelligence purpose.
The idea of Investigation and Intelligence Framework (IIF) is to help to correlate evidence and intelligence to help investigation more effectively. Therefore, all network related evidences including Memory, Registry, Web-applications (e.g. Browser or Social Network) and Network traffic (e.g. Network Packet) should be investigated.
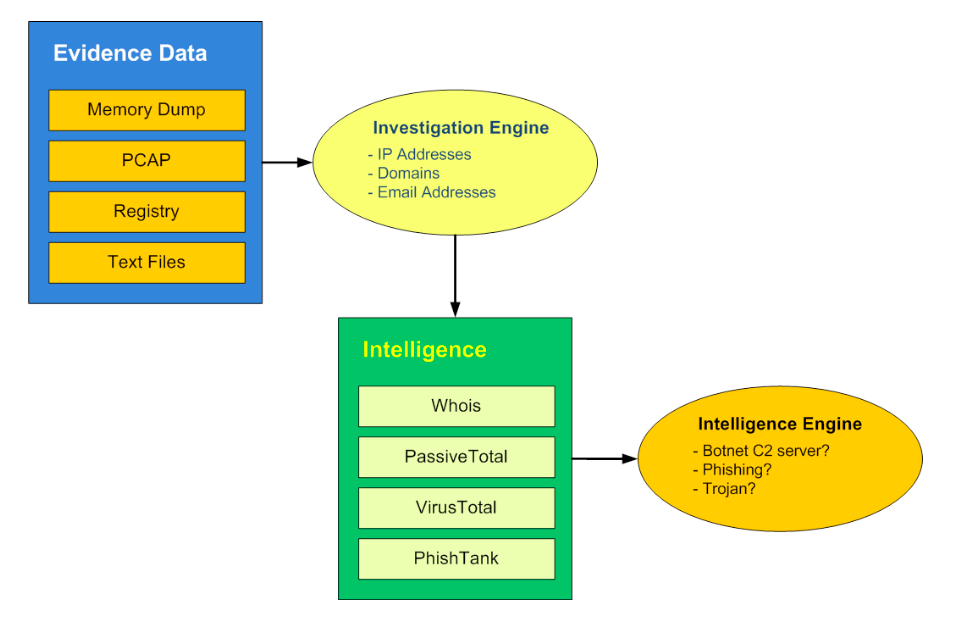
Below is the basic flow of the IIFramework Tool. Evidence data is imported to the engine, it will extract the IP Addresses, Domains and Email Addresses (later phone number, social network ID) automatically. It then ranks which evidence data deserves more attention for further investigation. Maltego with customized transformer is used to correlate the important evidence to give a bigger picture of the incident.
Figure 1. The flow of IIFramework Tool
A tool is now developed to correlate the evidence. Together with intelligence sources, the tool will apply probability model and algorithms to correlate evidence. It will then return the confidence level, risk scores and possible attack path/ incident type for the collected evidence and suggest which worth further investigation. This will provide a big picture of the cybercrime story and build a potential profile of the suspect so as to help investigation more effectively.
Proposed Model for Investigation
An Investigation and Intelligence Framework is an automated mechanism to identify the potential suspect at the early stage for the ease of the further investigation, correlating evidence to oversee the entire picture of the cybercrime. To fulfill the 4W concept, related artifacts including timeline, location, identity and attack path would be effectively recognized at the earlier phase, and investigators can tackle the cybercrimes more successfully.
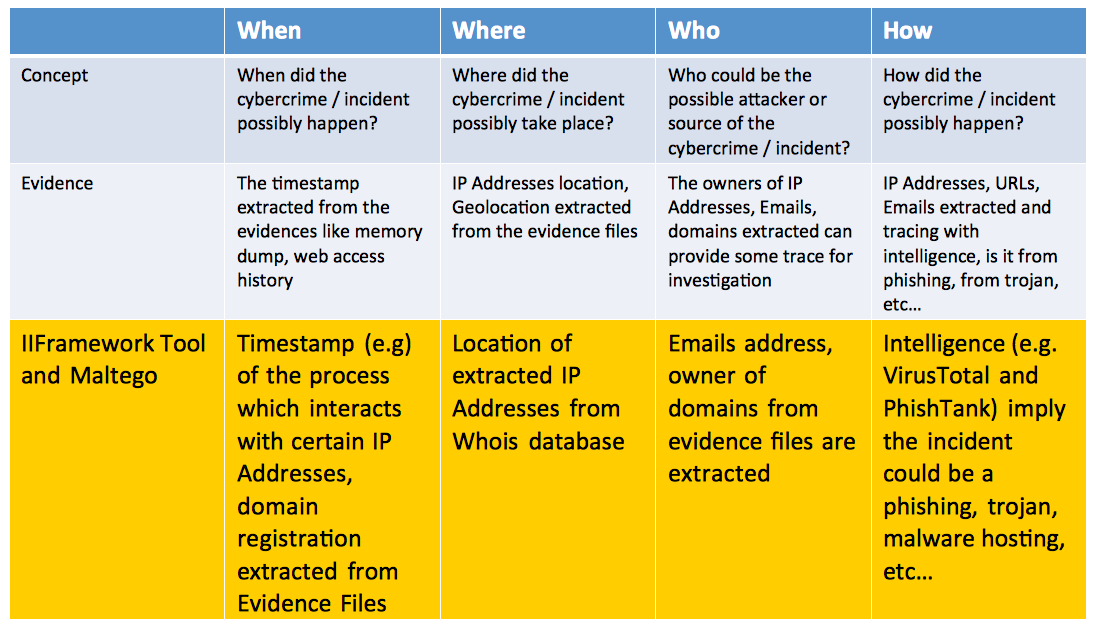
The table summarizes the relationship of 4W concepts and evidence, and how IIFramework Tool and Maltego can help the situation.
Figure 2. Table summarized the 4W concept
Phase 1 – Preparation and Identification
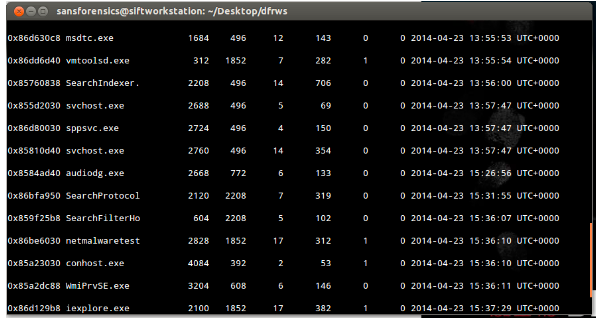
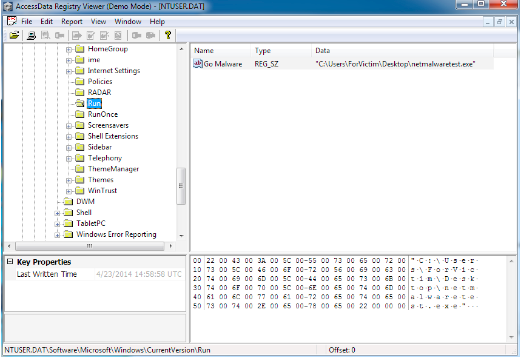
This phase takes place before the investigation. It is aimed to understand the case nature and identify what type of evidence data should be collected. An appropriate strategy would then be applied for further analysis. The following figures are shown the example of the evidence data we could obtain during the incident.
Figure 3. Memory Dump showed the suspicious process on the victim machine.
Figure 4. Registry entry showed the suspicious program (*.exe).
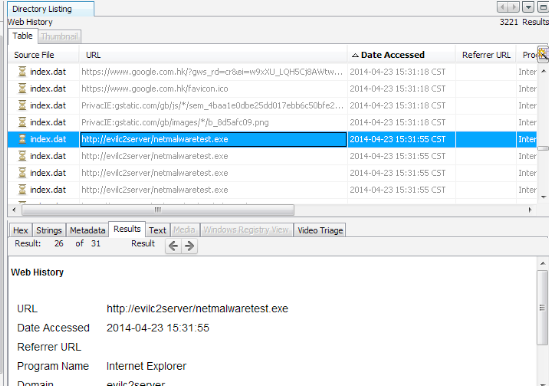
Figure 5. The download list of the browser recorded the download activities.
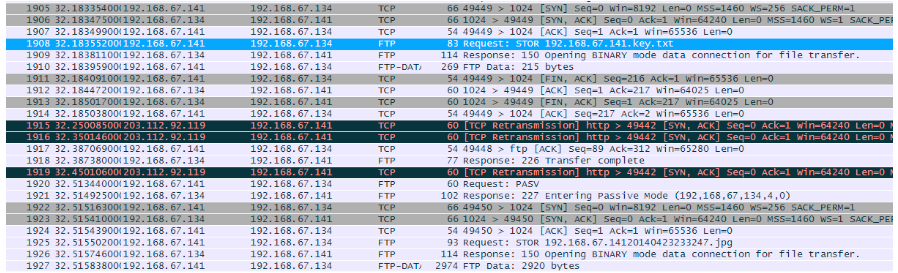
Figure 6. Network Traffic showed the suspicious network activities after infection.
Phase 2 – Strategy and Priority
The procedure to collect the evidence depends on the:
1. the value of the evidence
2. the volatility of evidence
3. the source of evidence
Phase 3 – Examination and Analysis
This phase is to correlate the relationships between the recovered valuable information and evidence together to draw a picture of the incident.
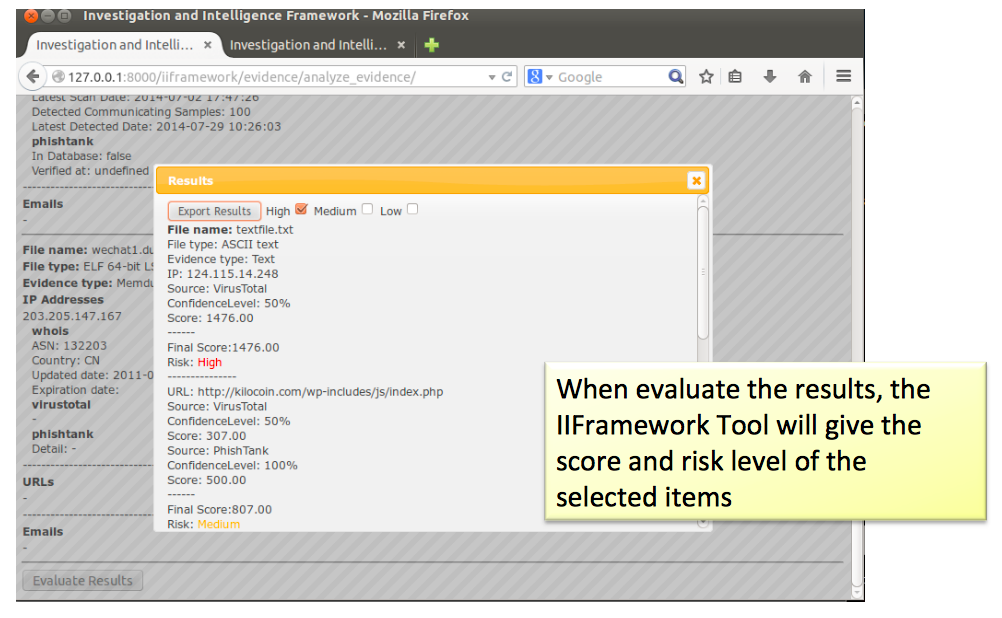
At the current stage of research and development, open source intelligence of VirusTotal, PassiveTotal and PhishTank are used to analyze the artifacts extracted.
Extracted artifacts (e.g. domains and IP Addresses) are submitted to VirusTotal and PassiveTotal through the API, then they will return whether such domains / IP Addresses have been detected as suspicious or malicious records before.
Extracted URLs are submitted to PhishTank through API, it will return whether the URLs are marked as phishing websites before. Together with the ranking formula in the tool, each extracted artifacts will be scored and ranked as High, Medium or Low so as to suggest which of them deserves further investigation.
Figure 7. Investigation and Intelligence Framework
The tool will be launched at open-source base soon and the demonstration video could be viewed at
http://alanh0research.blogspot.hk/2014/11/investigation-and-intelligence.html
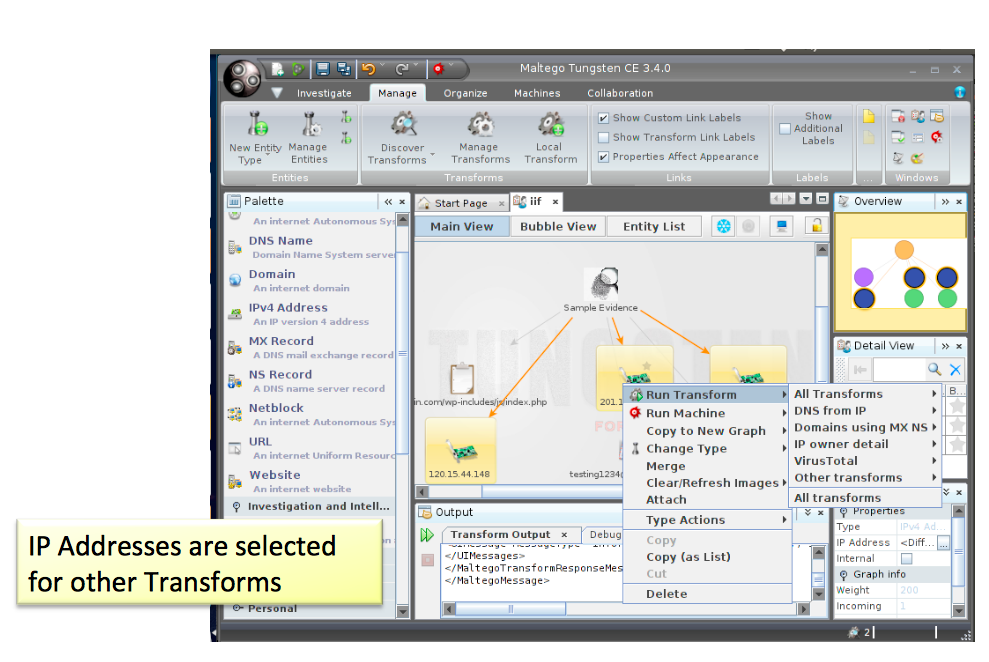
Figure 8. Intelligence transformed by Maltego
Based on the above information, IIF could perform an initial analysis as a result of the extraction of timeline, location, identity and attack path and transform it as an intelligence data. The result can be extracted as JSON format and import to Maltego (with custom Transform) for further analysis.
Phase 4 – Reporting and Documentation
After the examination and analysis phase, the results must be documented. This should include any conclusive finding from the examination and analysis phases. The report should include the following:
1. Background of the incident
2. Chain of custody of evidence
3. Detailed forensic methodologies – the extraction of evidence
4. Conclusive result – the whole picture of the incident
The forensics methodology must be systematic and scientific that accepted by court.
Conclusion
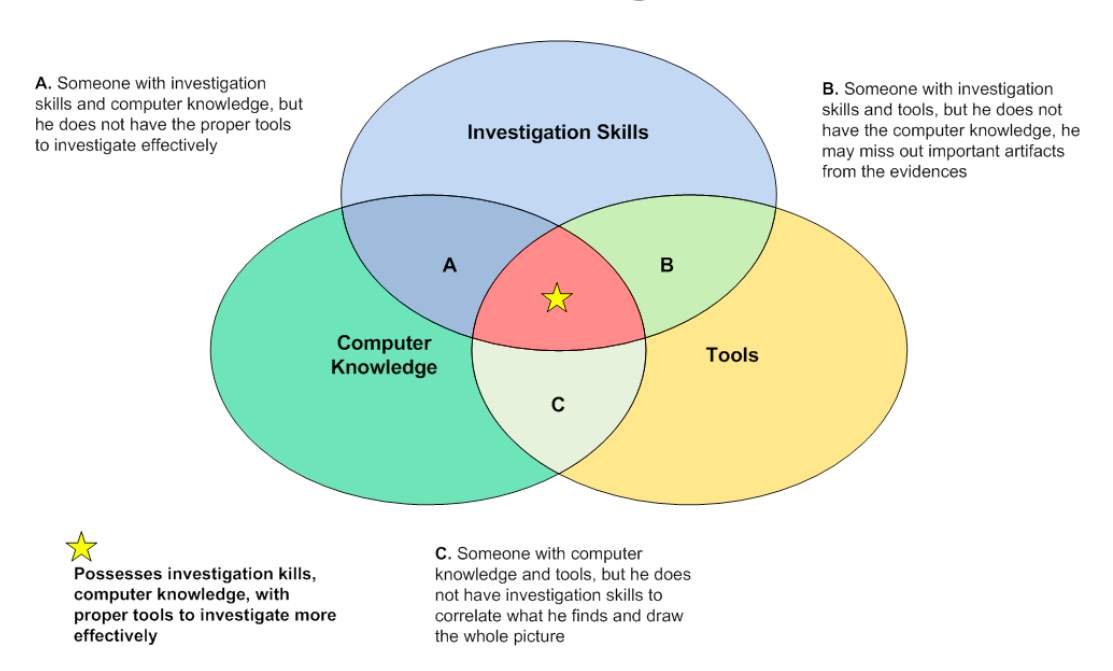
This is a quick paper to introduce the concept of Investigation and Intelligence Framework (IIF). The research is still on-going. IIF helps the investigator to understand the whole incident by covering all the information retrieved from the relevant locations. Hopeful the framework tool could fulfil the criteria as a ‘Perfect’ forensics investigator.
Figure 9. ‘Perfect’ forensics investigator
Valkyrie-X Security Research Group (VXRL) is a group of passionate security researchers in Hong Kong.















An interesting article! Understanding the context and purpose of the forensic work is important, and applying the Zachman framework seems like it could be an effective method of ensuring quality and purpose in the analysis.
Excellent article, thank you for sharing. The perfect forensic examiner needs one more skill to be perfect: the ability to effectively communicate their findings to a non-technical audience.