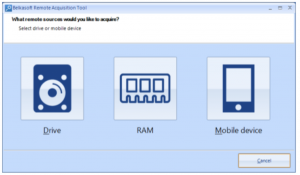
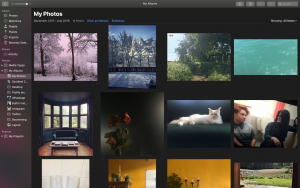
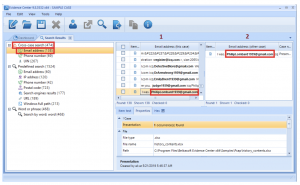
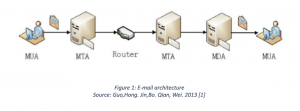
Forensic Focus Legal Update December 2019 – Part II: Search And Seizure
by Christa Miller
In cooperation with the National White Collar Crime Center (NW3C) and SEARCH, The National Consortium for Justice Information and Statistics, Forensic Focus offers a quarterly roundup of the latest legal developments around digital forensic evidence.
Comprising major… Read more