by Jasmin Cosic, Miroslav Baca & Peter Grd
Abstract
Today there is no criminal investigation that does not contain a digital dimension. A large number of criminal offenses, whether official investigations conducted by judicial bodies or corporate investigations, contain digital evidence, which in most investigations is key to the identification of perpetrators. Since the cyber space is undefined – it has no owner, place, time dimension, it does not belong to anyone – very often such evidence must be exchanged between the various subjects involved in the investigation. However, in addition to the exchange of digital evidence, it is also necessary to exchange the so-called “5ws&1h data” or metadata that are key to chain of custody identification. This is necessary because of the large number of factors that can influence the evidence and undermine the integrity of digital evidence, after which the evidence will not be accepted by the court. The need for the standardization of metadata exchange procedures and processes that ensure the chain of custody has been imposed as a necessity and through the realization of DEMF, as a possible solution.
Introduction
Every digital investigation nowadays involves digital evidence collected from different sources, in different ways, by various institutions and people employed in these institutions. Investigations can be criminal, official, can be internal and corporate within the organization (firms), but what is common to all is digital evidence. Given that the cyber space is undefined, often the site of execution is the Internet in one country, the affected is located in another country and the perpetrator is geographically on the other end of the world. This requires a special, multi-functional approach, as well as the procedures to be followed in this process. The particular problem here is the absence of procedures in many countries which exchange digital evidence, for example the SE European countries.
This paper will outline the usage of Digital Evidence Management Framework (DEMF), the framework outlined in previous researches [1] [2] [3] [4] that allows guidance and proving of 5ws&1h, or chain of custody at any time in any phase of digital forensic investigation. At every moment it is known who handled digital evidence, what the evidence was, and when, where and why it was handled. The need to set standards will also be emphasized, for example, the standardization of metadata exchange along with digital evidence, which DEMF provides. In the event that institutions or agencies from one country have a need to exchange digital evidence with another institution or agency in another country, along with digital evidence a .demf file will be provided that will contain all the metadata of the complete digital life cycle that will ultimately determine and prove that the digital evidence has not changed or that its integrity has not been violated in any phase of the digital forensic investigation.
Likewise, what DEMF allows and where its strength lies on the other hand, is not only in the ability to exchange metadata 5ws&1h that provides evidence of digital evidence integrity, but also the ability to exchange data in the so-called “container”.
Related Work
There are many papers on standardization and interoperability of digital evidence.
One of the ways in which scientists tried to solve the problem of preserving the chain of custody was through creating different formats for storing digital evidence. One of the efforts of authors who are actively involved in the problem of standardizing the format of digital evidence storage as a prerequisite for the exchange of digital evidence, forensic tools and so on was also an attempt by members of the DFRWS working group. The recommended framework was built using the RDF (Resource Description Framework) as the most common and most affordable data presentation format and ontology for describing the vocabulary relevant to this data. The methods used by authors in their paper are ontological approaches (ontologies), modeling, the Unified Modeling Language (UML), XML (eXtensible Modeling Language) and RDF (Resources Description Framework) [5]. It is emphasized that the ontology of the Philip Turner Digital Evidence Bag was applied, and there are not many papers where ontology has been applied in the field of digital forensics and computer crime. The paper did not solve the problem of the digital evidence chain of custody, and the ontology was used only to define the vocabulary used in defining this format.
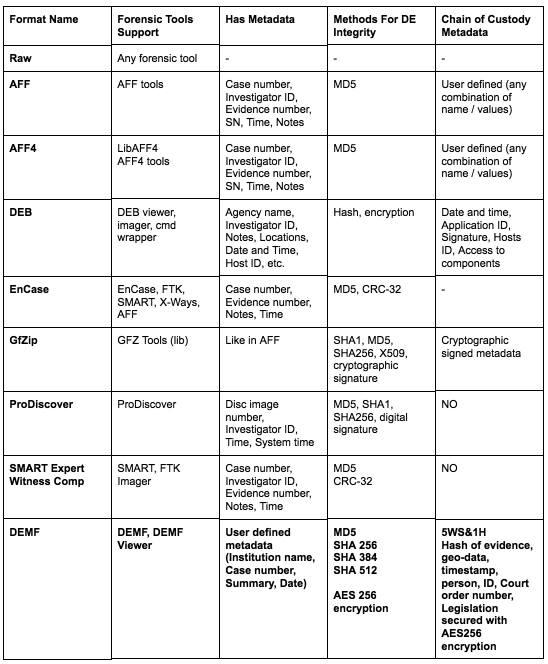
Digital Evidence Bag (DEB) [6] [7] represents a universal container for storing digital evidence collected from any source. It ensures that not only data (potential digital evidence) can be stored but also the source of evidence and maintain continuity during the investigation process. In other words, DEB is part of the software that can store data from any forensic tool that is running. The DEB consists of the tag file, the index file and the contents file. The metadata file contains the metadata of the digital evidence (the name of the organization, the name and surname of the person who collected the evidence, date and time of collection, ID number, hash function calculation). The index file contains information about the corresponding content file (path to the data carrier, file name, time stamp). The content file is the actual digital evidence (image, video, text file, and so on). There is no detailed elaboration of this concept, and according to some authors [5] DEB can be any archive (tar, zip, etc.) that contains these files. The most common and publicly available formats for digital evidence storage are AFF, Raw, DEB, Expert Witness, Gfzip, ProDiscovery, EnCase, and SMART Expert Witness [8]. Some of these tools have built-in digital evidence integrity mechanisms through the combination of MD5 and CRC while only the SMART default format has cryptographic signature support.
Compared to other formats, DEMF has user-defined metadata, strong summary functions (MD5, SHA256/384/512), AES256 encryption support, as well as all metadata required to demonstrate the chain of evidence integrity. It also enables the original evidence (first copy) storage in the container itself.
Table 1 shows the most popular formats for storing digital evidence with the features important for chain of evidence and the protection of digital evidence integrity. It is evident that no format contains metadata that would answer the question 5ws&1h and the way to maintain a digital chain of evidence.
In comparison, for the first time, DEMF, as a possible solution that offers complete control of 5ws&1h, is presented.
TABLE I
MATRIX OF AVAILABLE FORMATS
Casey and others [9] developed CASE and DFAX standard to present an open community-developed specification language called Cyber-investigation Analysis Standard Expression (CASE). To further promote a common structure, CASE aligns with and extends the Unified Cyber Ontology (UCO) construct, which provides a format for representing information in all cyber domains. This ontology abstracts objects and concepts that are not CASE-specific, so that they can be used across other cyber disciplines that may extend UCO. His work is a rational evolution of the Digital Forensic Analysis eXpression (DFAX) for representing digital forensic information and provenance. CASE is more flexible than DFAX and can be utilized in any context, including criminal, corporate and intelligence. [9][10]
For the Digital Forensic Community, a unique framework is needed – to ensure that the chain of digital evidence can be treated the same way around the world. Nowadays, common practice is (especially in the case of terrorist attacks) that some criminal activities are agreed on in one state on one side of the world and are committed in another country on the other side of the world, and the means of execution (a digital device) is at a third end of the world. The question they ask is where is digital evidence, when it was being handled, did the evidence remain unchanged during this process? How can the metadata be shared along with the digital evidence itself to the interested parties involved in the investigations?
Proposed Framework
DEMF is an almost 10-year-old idea, proposed in conceptual model of Cosic and Baca in their early work [11][12].
The DEMF not only allows recording and managing the chain of evidence at all stages of the digital forensic investigation, but also ensures the integrity of the digital evidence itself. It also enables packing of all 5ws&1h data together with digital evidence and then secure protection with the help of powerful AES256 encryption. The model can be applied and used in digital investigations when we want to prove that the proof was not altered and that it is known at any time who came into contact with digital evidence, when, where, where, why and how throughout the life cycle.
Later, DEMF was realized as an application created in Java, and a case study with specific data was made – a test scenario. The power of DEMF is not just a chain of custody and assurance of metadata integrity, but also the possibility of preserving the whole case (digital evidence and their metadata), but also the chain of evidence metadata in one container. The so-called container or
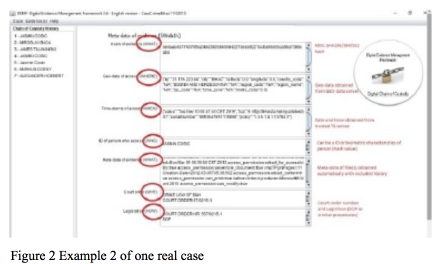
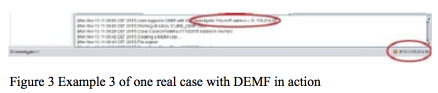
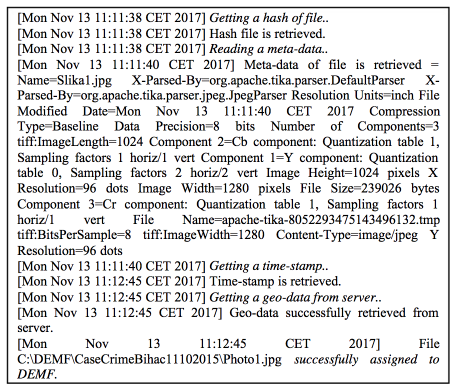
.demf file is additionally secured with AES256 encryption, allowing full protection. This practically means that the exchange of evidence between the participants in the digital forensic investigation process would also exchange digital evidence themselves, their metadata, as well as the metadata needed to prove the chain of custody. On the other hand, DEMF’s strength lies in the fact that this tool has integrated fully functional forensic tool features, because the tool reads data from digital evidence with the help of built-in libraries. The example of using DEMF can be seen in Figures 1, 2 and 3.
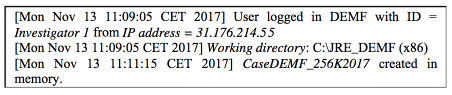
The .log file that represents DEMF in action of collecting meta data can be seen below:
Conclusion
The exchange of digital evidence between different institutions is necessary for a number of reasons. Given the undefined cyber space, a number of agencies/institutions are often involved in digital forensic investigations. The interoperability of digital evidence is necessary but it is also necessary to exchange metadata and chain of evidence. Today, dealing with chain of evidence in the world is often handled manually, while there are systems and solutions that offer electronic recording. The DEMF framework, in addition to conducting a chain of evidence, ensures the integrity and inviolability of digital evidence, as well as the proving of 5ws&1h which is the strict procedure on which the courts insist (Daubert principle). Every moment, we must know who has accessed what, and where, when, why and how digital evidence has been accessed. Given that a large number of participants are involved in this process – investigators, court attorneys, court experts, prosecutors, judges, police officers, bystanders and similar – there will be a large amount of data, and in every single step of the chain all data must be collected.
DEMF as the proposed framework, but also a finished solution, offers complete control of digital evidence management. In addition to metadata exchange, it also offers control of the digital evidence itself and proves its inviolability and integrity, which is most important in the forensic investigation.
Acknowledgement
Research and development of DEMF in the first phase was supported by the Centre for biometrics, forensics and privacy, Faculty of Organization and Informatics, University of Zagreb.