Hey everyone, Trey Amick from Magnet Forensics, and today I want to highlight Magnet OUTRIDER version 3.0. If you may have noticed I’m not triaging a Windows box today, that’s right, version 3.0 of OUTRIDER is a purpose-built triage tool for Macs. Let’s face it, when it comes to investigating Macs, it’s really never been easy, but with OUTRIDER we’ve made it much, much easier.
Now to start, all I’ve done is insert my OUTRIDER dongle into the Mac. I want to investigate and launch the app. As you can see, we’ve given OUTRIDER a complete UX overhaul to make it even easier to use than before. Like before, I’ll go ahead and give this scan a case number. Now let’s go ahead and take a look at “Scan templates”. What’s great about OUTRIDER .0 is the ability to have pre-configured templates set up. So when you’re in the field, you can just select the one you need and you’re off to the races.
Let’s go ahead and configure a new one. So I’ll hit the “Plus” button, we’ll go ahead and go into the edit, and here you can see we have our options as far as locating files, we can do keywords list, we can do Regex keywords, just like we could with previous versions of OUTRIDER, I’m going to add a couple of keywords here. So, for this investigation, I’m interested if they have Lightroom, as well, as I’m curious about Photoshop on this Mac.
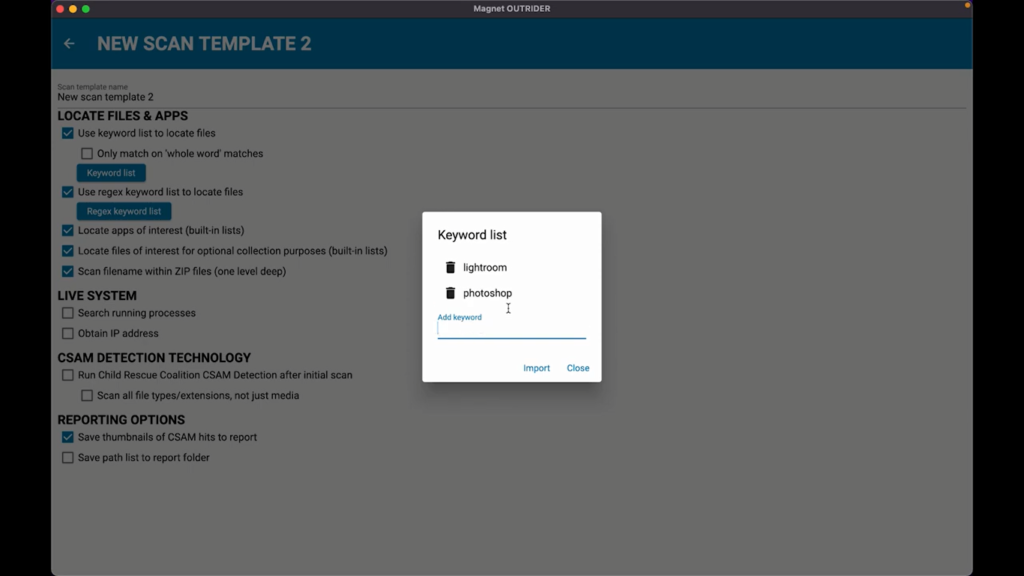
Simply hit “Close”, we’re all going to have locate the apps of interest with the built-in list. We’re going to locate files of interest with potential collection opportunities there, as well, and then we’ll scan file names within the zip files that we find. I’m also going to go ahead and turn on “Search running processes”, as well as “Obtain the IP”, and I’m also going to run the CSAM detection technology that we have through Child Rescue Coalition, o I’ll have that selected.
Now, once we have all this information out, I’m going to go ahead and just name this template “Field Triage 2”, and we’ll just hit “Back”. Now from here, as you can see, I can just simply select my new scan template, and then on the right-hand side we can decide what we want to actually run this scan against. And I’m going to go ahead and run it on the internal drive of this Mac. And this Mac is one of the new N1-based Macs.
So, I’m going to go ahead and run it. Now we’ll hit “Start scan”. As you can see on the bottom, we had the scan processes, we’re running the scan across the drive and we’re checking some of the artifacts, as well. Everything’s finished up now within 16 seconds and we can now just start navigating to look at what we found; some anti-forensics files here, we have some cloud files that could be of interest, looks like OneDrive and Dropbox are present, we have the ability to collect files, so it looks like we found some wallet files for Bitcoin, definitely worth our interest if we want to collect those.
And moving on down, once again, the core client for Bitcoin, Dark Web files, we have encryption that we’ve found, we’ve found some VMs as well, and then getting down to the keyword hits, here you can see the built-in keywords that we have with OUTRIDER, as well as the keyword hits for the words that I added. So here we can see what we found many Photoshop hits, as well as some Lightroom in here, as well. And just keep in mind, we did this keyword scan within 16 seconds.
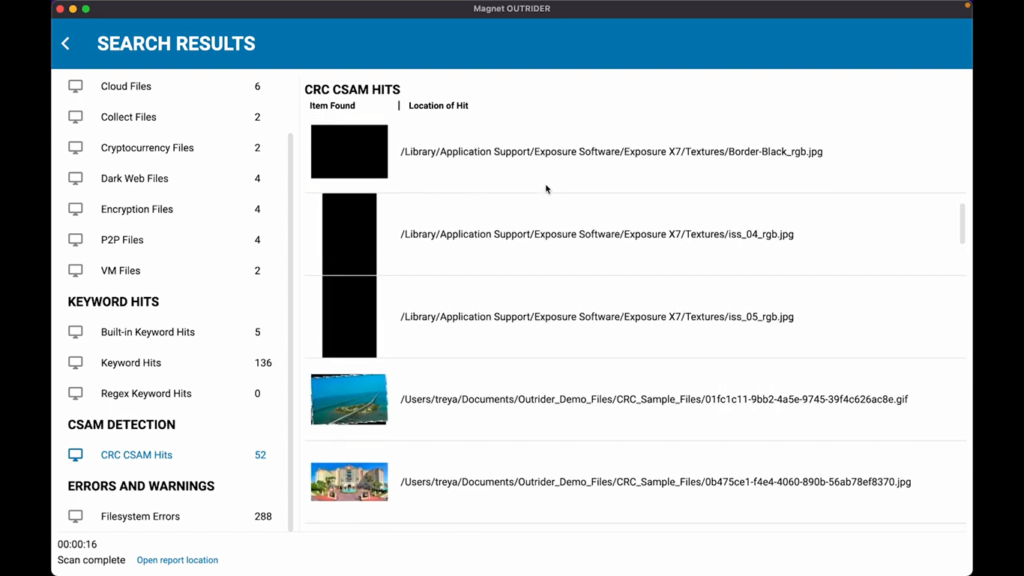
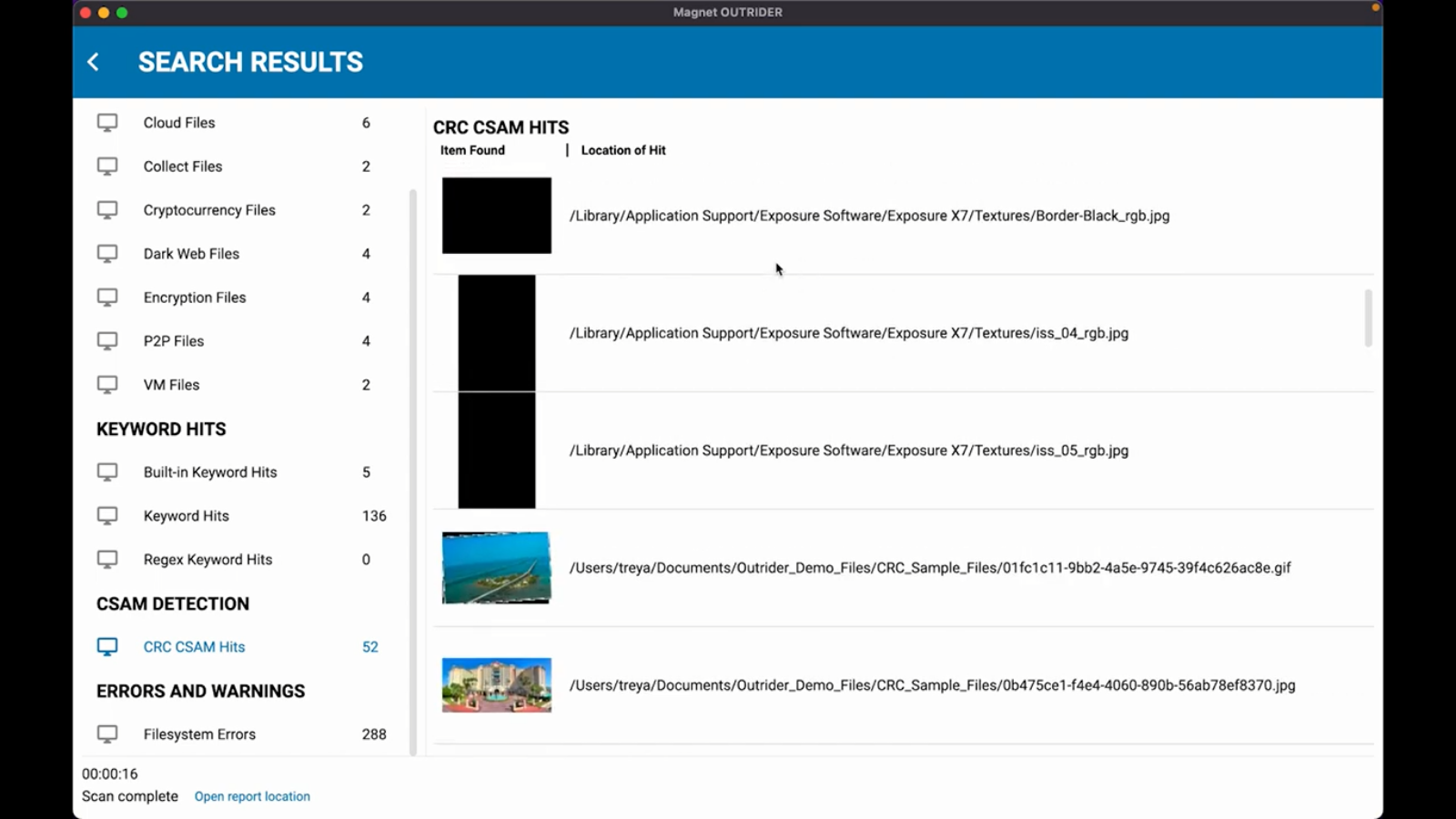
Next, the CSAM detection. And as you can see, we have 52 potential hits here. Now, one thing to take note as you’re looking at this, actually Lightroom and a lot of the photo editing software actually will get hits from within the CRC detection. That’s normal. So here you can see Exposure X7 with some of their textures, and then down here we have some of the Lightroom contents with some of their plugins. We also have these two images and we’ve actually designed just for demo purposes, these two images to be highlighted with the CSAM hits. So that’s why you’re seeing these two images.
And then lastly, we have errors and warnings. So, these are going to be file system errors. And obviously with Macs now, you’re going to have a very protected ecosystem on that Mac in terms of some of the files that are read-only, and that’s going to be some of those errors on things that we can’t scan when we are running OUTRIDER. So, something just to be aware of, you’re always going to get these hits just because, you know, in essence, you’re not going to have full access to the entire drive. You’re going to have access to the data side of the drive that has the user’s information, which is really the important part for this investigation.
But here you can see, we have all of our information and it’s 16 seconds. I can hit “Open report location”, we can go ahead and open up the HTML report, and here you can see, we have a quick rundown of everything that we found from this quick scan. Thanks for tuning in. I hope you’re as excited as I am about the new OUTRIDER version 3.0 for Mac, and we’ll see you next time. Thanks.