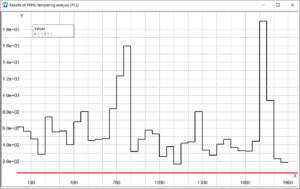
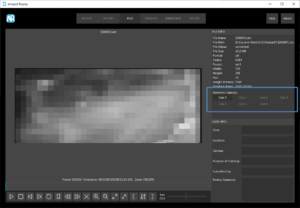
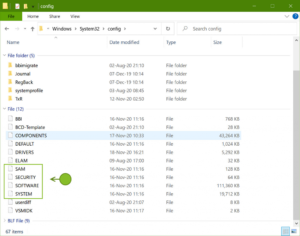
A Springboard To Digital Forensics Research In 2021
The end of 2020 could not come fast enough for most of us, and yet, as the year wound down, some things — such as the digital forensics research recapped in this article — were worth slowing down for. This