VFC was first launched to the forensic community in 2007. It makes it easy to create a virtual machine (VM) replica of a target system, enabling an investigator to recreate and interact with the “digital crime scene”.
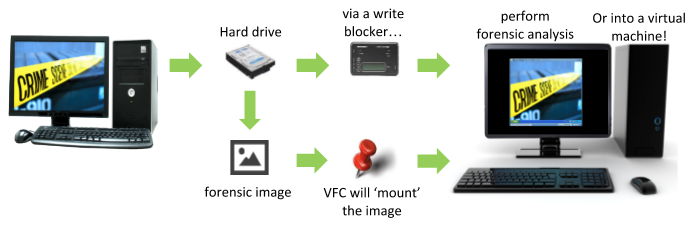
Using accepted forensic practices, VFC interrogates the target drive to gather relevant system information, so that it can very quickly build the VMware framework to create a forensically sound replica of the target system (the exhibit) as a Virtual Machine (VM). This process is automated by the VFC software to avoid BSOD and driver errors, saving the user hours of manual diagnosis and repair.
VFC allows virtualisation of Windows, Linux, Solaris & other OS platforms.
The VFC VM enables the user to navigate around the suspect’s desktop as if they had literally turned on their machine. This can be completed by working from forensic images, using the inbuilt mounting tool VFC Mount™, or can work directly from a write-blocked hard-drive. Due to its simplicity VFC allows forensic and non-forensic practitioners to triage computers in a forensic manner.
VFC automatically fixes known errors associated with virtualisation, and speeds up the process of manually virtualising devices. This allows exhibits to be quickly triaged, allowing investigators to look at more cases in shorter time-frames, reducing backlogs.
Investigations Using VFC
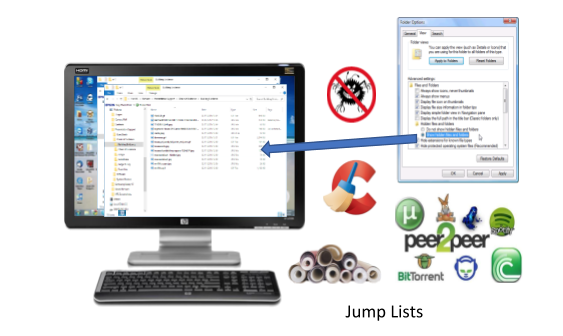
The VFC VM can be used to quickly identify obvious “accessible” files and folders. Recent file history can be accessed, internet history can be viewed in its native format, P2P/torrent downloads and shares can viewed in the native tools, and “Hidden Files” can be accessed.
A real-life example of VFC being used in this manner included in detail in the Testimonials (see link below) is from Oklahoma City PD:
“Never before has Oklahoma County been able to successfully prosecute a “No Body” case based only on circumstantial evidence – and it was VFC that drove it home to the jury.”
“VFC is a must-have tool for all forensic investigators and offers a different angle of investigation to the standard analysis software.”
VFC will also recover/bypass user locks hindering virtual machines. The software has the ability to reset online-authenticated “LiveID” Windows user passwords, or permanently reset passwords on local Windows accounts. These inbuilt features remove the need for other tools.
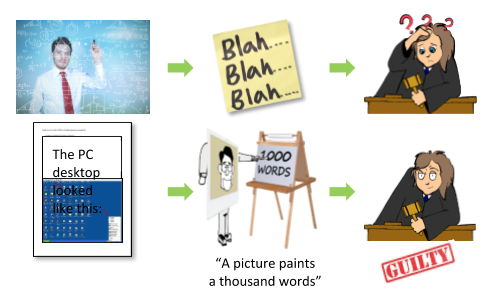
VFC can also be used to help an investigator get their bearings in relation to incriminating data. It enables an investigator to visually show a suspect’s desktop, in a format that any audience will understand. This can either be performed live at court, using a portable standalone clone VM, or captured as stills for reporting. This can have a huge benefit in cases that a non-technical person such as a judge, a member of the jury or a solicitor can understand and recognize the data (see testimonials).
VFC can be used to access bespoke data in their native applications using software already installed on the host system, whether this be P2P/torrent downloads, Sage databases or QuickBooks accounting records, among others (see link to Case Studies at the end of this article).
The VFC-generated VM means that all installed programs that were working at the time of last use are still in license and accessible to investigators (even those with time-bound licenses).
VFC has enabled investigators to access encrypted phones or USB devices where the decryption password is auto-saved on the suspect’s computer/laptop that the device had been connected to. This procedure will also enable the device to be forensically imaged by an investigator.
VFC has been used on investigations to run scripts or install software on the system with no fear of breaking it; you can always “rewind” it back to the initial state. This has proved invaluable for cyber inquiries where investigators have been able to run trojans or viruses, or investigate exploits.
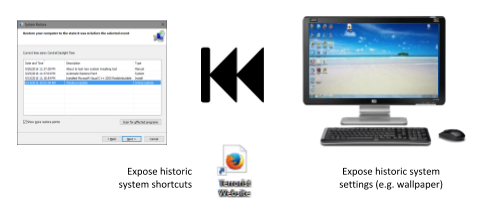
A final feature for investigators to consider is the Restore Point Forensics / Patch VM, which allows you to rewind a machine to an earlier state to see Shortcuts that had been saved on the desktop in an earlier version of the machine – such as links to websites of ill-repute or terrorism activity which have since been removed. It can also help you to ‘fix’ a broken VM by automatically applying the collective knowledge of VFC.
This VFC walkthrough is not exhaustive, but covers what we believe are methods and identifies uses of a virtual machine in a digital enquiry that we hope investigators may not have previously considered or explored and may now benefit from going forward. VFC has become an integral and must-have tool in the digital forensic investigator’s armoury of tools when investigating and fighting digital crimes.
MD5 Limited are organising webinars in January/February 2020 to demonstrate the benefits of VFC to all users, along with many other items not able to be covered in this article. Please register your interest by emailing info@md5.uk.com.
Case Studies: https://vfc.uk.com/resources/files/Case_Studies.pdf
Case Testimonials: https://vfc.uk.com/resources/files/Case_Testimonials.pdf