FF: Tell us about your background and how you came to be in your current role at Swiss FTS.
Before discussing my journey and project related to the investigation of iOS Unified Logs, I would like to express my gratitude to Forensic Focus for this interview.
My journey in Digital Forensics began nearly a decade ago with a Bachelor’s degree in Criminal Sciences from the University of Lausanne in Switzerland. This Bachelor’s program focused broadly on crime scene investigation and the evidence they may contain from their collection to their interpretation.
Following these three years of Bachelor, I pursued a Master’s degree in Digital Forensics, also at the University of Lausanne. Subsequently, I applied for a position at Swiss FTS as an eDiscovery consultant where I have been working for over three and a half years now.
FF: What does your job involve? What does a typical day look like?
As an eDiscovery Senior Consultant at Swiss FTS, I work closely with legal professionals to provide technical and tactical support throughout the EDRM process, covering data acquisition, review, and production. My responsibilities include coordinating data collection from different devices using forensic tools and assisting in the review process by helping identify relevant data and producing specific documents as required. Throughout this process, one of the key responsibilities is to ensure the integrity and confidentiality of the investigated data, notably by keeping the chain of custody up to date.
Over the years, I have specialized in handling phone data, both in terms of acquisition and review in specialized eDiscovery platforms. Managing smartphone data presents diverse challenges, particularly when dealing with chat data (like WhatsApp, Telegram or Teams) on platforms such as Relativity.
Looking at the bigger picture, my role goes beyond just digital forensics. It covers the entire eDiscovery process, including collaboration with legal teams, managing data workflows, and ensuring the presented information follows legal requirements.
FF: You’ve written extensively about iOS Unified Logs. How can these logs be a useful source of information during digital investigations?
My exploration of iOS Unified Logs began in 2020 during my Master’s thesis. Over the years, I observed a significant lack of documentation on these logs, despite their potential importance in digital investigations. Recognizing their crucial role, I decided to publish my findings in blog articles. The positive feedback and numerous questions I received affirmed the necessity of sharing this knowledge.
iOS Unified Logs serve as a valuable source of information in digital investigations due to their granularity and detailed content. When addressing questions such as “How was this action executed?” or “At what moment did the phone switch between WiFi and 5G connections?” these logs provide a level of detail that is particularly interesting to analyze. They offer insights into the sequence and specifics of events on an iOS device, contributing to a thorough understanding of the investigated activities. The depth and precision provided by these logs significantly enhance the efficacy of digital investigations.
The first example I like to mention is that their investigation allows us to highlight the method used to unlock them and to know the time between two unlocks (or two locks):
| Process | Event |
| SpringBoard: | Processed authentication request (success=YES): <SBFAuthenticationRequest: 0x2802e5c80; type: 1; hasPasscode: YES> |
| Apsd: | Screen did unlock (Was locked for 1.245383 seconds) |
If you’d like to find out more about investigating these logs, please take a look at the various articles on my blog: https://www.ios-unifiedlogs.com/blog
FF: Can you explain the process you follow to extract and analyze logs from iOS devices? What tools and techniques are essential in your workflow?
Investigating iOS Unified Logs involves a specific process, and documenting it precisely is, in my opinion, necessary, as is the case for any forensic investigation. The first step in investigating Unified Logs is to obtain a logarchive file, which is crucial and can be done in the following two ways:
- Obtaining a Full File System Extraction: This involves a comprehensive extraction of the investigated phone’s file system. Subsequently, the logarchive can be manually reconstructed (https://eclecticlight.co/2020/02/07/making-your-own-logarchive-from-a-backup/)
- Direct Extraction: Using a Mac computer and the command “sudo log collect –device-name ‘device-name’”, the logarchive can be extracted directly from the iPhone. To achieve this, it is necessary to connect the phone to your forensic Mac Laptop and unlock it.
Once you have your logarchive file, you have no choice but to use a Mac computer to analyze its content. You can either open it in the Console or try parsing the file using the Mac Terminal. Indeed, there are specific commands on a Mac to investigate these log files, and they can be particularly effective… if you know what you’re looking for!
Indeed, the number of logs recorded by iPhones is substantial, and delving into them without knowing what you’re looking for is, in my opinion, simply impossible and poses a risk of error. Having had the opportunity to conduct extensive research in this field, I wanted to share my knowledge in the investigation of Unified Logs through my blog articles. Over my experience and research, I’ve built my own small tool running on Mac to automate the extraction and parsing of iOS Unified Logs.:
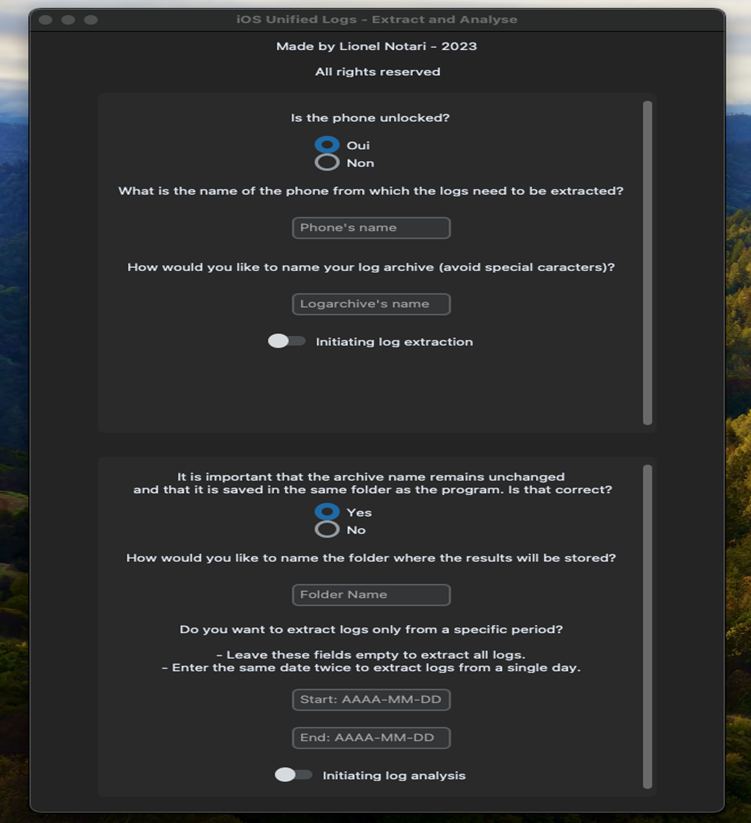
This allows me to quickly access the logs that I consider relevant (especially those presented in my articles) and investigate them, saving a considerable amount of time. It’s not perfect, but it serves its purpose, and some European and American law enforcement agencies already use it in their digital investigations. My goal is to refine it throughout this year and to make it accessible from my website.
FF: How do privacy and security features in iOS impact the process of log extraction and analysis? How do you navigate these challenges?
If you have ever ventured into the investigation of unified logs, you have likely noticed that some of them mention the value <private>, thereby concealing data that Apple deems confidential, which could be immensely valuable to us as digital investigators.
When I commenced investigating these logs on iOS 13 in 2020, this particular mention appeared far less frequently than in 2024. Consequently, over the years and across iOS versions, it has been necessary to identify alternative logs, and it is certain that this will continue to evolve. One of the challenges is, therefore, to stay up-to-date regarding these changes and consistently conduct tests.
In terms of security, possessing the iPhone’s unlocking code is sufficient to extract the logs. If you subsequently use a forensic extraction tool, it will be necessary to have a Full File System extraction to access the logs. If this type of extraction is not feasible, I strongly recommend utilizing a Mac, enabling you to leverage the commands directly integrated into these computers for extracting logs from an iPhone.
FF: Could you share a memorable case where iOS logs played a crucial role in solving a digital forensic investigation?
Initially, I view logs as particularly interesting in the context of road traffic accidents. Indeed, these traces can easily highlight whether a message was typed on the phone’s screen, for example, as multiple logs record each “tap.” However, these may not necessarily be the most memorable cases…
In other investigations, they have proven useful in shedding light on the presence of a suspect at the crime scene because the individual was connected to the WiFi network (in conjunction with other traces). WiFi logs can be very interesting in such cases as they help determine which WiFi networks are nearby the phone, for instance. If someone claims to be at a certain location but their phone suggests otherwise, it may be a sign that further investigation is needed. While their investigation is crucial in cases of road accidents to determine if the driver was using their phone or not, they can also provide information in other instances, especially regarding the ‘location’ of the device. In this regard, we can, for example, discuss the following logs:
| Process | Event |
| Itunestored: | ISNetworkObserver: Set network type “WiFi” |
| SpringBoard: | [SBWiFiManager] signal strength bars changed to 2 |
These are two logs that I particularly like because they illustrate my point very well when I say that they provide a very interesting level of detail. Indeed, through their investigation, it is possible to determine precisely when the network transitioned to a WiFi connection and what the signal strength was, for example.
FF: Are there any upcoming topics or projects related to iOS logs and digital forensics that you plan to explore in your blog?
The investigation of these logs and their publication currently takes up a significant amount of my time. I wish to focus on this at the moment to avoid spreading myself too thin. I still have quite a few ideas for logs that I need to investigate, particularly those related to Bluetooth, Camera and Photos applications, as well as those that record the orientation of the phone in space (Portrait, Landscape, etc.). The article about WiFi logs is almost ready to be published as I write these lines. However, I am also open to suggestions. If someone wishes for me to particularly study a specific application or activity, I will gladly do so.
In a second step, I would like to publish a comprehensive dossier (which would evolve as new ‘discoveries’ are made) of all these logs of interest. This would allow a digital investigator to find a relevant log in their investigation without having to go through all the articles on my website. This could undoubtedly save them a considerable amount of time. I also aim to establish a community space, like a forum, on my website so that an investigator who finds a potentially interesting log, but one I have never discussed, can share it. Each person could then conduct tests on that log to precisely determine the scenarios in which it is recorded, for example.
Exploring Unified Logs from other Apple devices also intrigues me greatly! The day I feel I have thoroughly covered iPhone. I will likely move on to investigating Unified Logs on watchOS. I believe combining the investigation of these logs with those from iPhones could be truly interesting. Moreover, I must admit that I am looking forward to Apple releasing an Apple Car, although the investment to investigate its logs may be substantial.
But one of my main short-term objectives is to refine my iOS unified log extraction and analysis tool and make it available to a wider audience on my website.
FF: What do you enjoy doing in your spare time?
As you may have noticed, the investigation of unified logs is a passion of mine. Currently, it takes up a significant amount of my evenings and weekends as I conduct the necessary research and write articles.
Outside of this, I am an avid enthusiast of sports of all kinds and photography.















