Integrate Automated Evidence Analysis and Mapping to Your Investigations
Understanding an attacker’s behavior and their tactics, techniques and procedures (TTPs) is vitally important to any investigation – it provides critical context that allows for more efficient and effective investigations. This context informs what response actions are appropriate, and improves short, and long-term, response outcomes.
But the threat landscape is growing increasingly complex, and it can be difficult to keep on top of every IoC, malware family, and adversary tricks, particularly given the scope of activities that can be involved in any one investigation. Luckily, frameworks like the MITRE ATT&CK framework are available to aid analysts and investigators.
What Exactly Is MITRE ATT&CK?
MITRE ATT&CK is a globally-accessible knowledge base of adversary tactics and techniques, curated from real-world observations.
It acts as a knowledge base that can be used as the foundation for the development of specific threat models and methodologies. These threat models and methodologies are relevant across the private sector, government organizations and are a cornerstone of the cybersecurity product and service communities.
MITRE ATT&CK was conceived to help combat the continuously advancing threats that arise daily by mapping IoCs and uniting communities to forge improved cybersecurity strategies.
Integrating Valuable Insights Into Investigations
The MITRE ATT&CK framework therefore offers key information and helps provide signposts for incident responders, hunters and analysts to leverage as they work through an investigation. It’s also really important in helping them better understand how a cybersecurity incident may have occurred.
In addition to providing this important context, the mapping of observed indicators of compromise (IoCs) and tactics, techniques, and procedures (TTPs) to specific ATT&CK tactics and techniques, helps to speed up the detection and analysis phase, by providing:
- Common Language: MITRE ATT&CK provides a common taxonomy and language for cyber security practitioners to describe adversary tactics, techniques, and procedures (TTPs). This common language can be invaluable during incident response to quickly and accurately convey information about the attack amongst other analysts or colleagues.
- Attack Characterization: Analysts can use MITRE ATT&CK to help characterize and categorize the nature of the attack. By matching observed behaviors to the framework, analysts can identify the TTPs being used by the adversary.
- Guidance on Response: The framework can guide analysts in identifying which actions to take to counteract observed TTPs. This might involve specific mitigation measures to prevent further breaches or adjustments to defenses to disrupt ongoing attacks.
- Prioritization: MITRE ATT&CK can help analysts prioritize their actions based on the tactics and techniques observed. Some actions may be more critical to address immediately, while others can be handled later. This can be a big help to teams where there are resource challenges or teams are geographically dispersed and might need to collaborate.
- Threat Intelligence: MITRE ATT&CK can be used to enrich threat intelligence by comparing current incident data with known patterns of adversary behavior. This can help in attributing the attack to specific threat actors or campaigns, if they’re known to use certain TTPs.
What Is the AIR MITRE ATT&CK Analyzer Feature?
AIR includes a suite of incident response capabilities including automated evidence analyzers based on research from our in-house researchers and threat hunters – known as the Binalyze DFIR Lab – and incorporates the very latest versions of MITRE ATT&CK.
With their fingers on the pulse of the cybersecurity ecosystem, the DFIR Lab ensures that AIR’s built-in automated evidence analyzers always include the latest IOCs to provide detailed insights into the tactics and techniques used by attackers.This is all about giving you visibility into suspicious activity on your networks and assets. Being able to automate this process means that you can save time on what’s “known”, are able to confidently cut through the noise of evidence, and move more quickly through investigations.
The DFIR Lab, here at Binalyze, is always working towards an ambitious roadmap of new features and enhanced capabilities, all designed to make your investigations easier from the moment they start.
Below, we’ll explore how AIR’s MITRE ATT&CK analyzers and mapping can help you protect your organization from cyber threats.
Like all the other analyzers built into AIR, the MITRE ATT&CK Analyzer enables responders and analysts, like you, to make decisions faster and piece together critical information as part of an investigation.
Thanks to the exhaustive R&D work carried out by our world-class DFIR Lab team, the MITRE ATT&CK Analyzer combines a high level of detection rate for malicious indicators with an extremely low false positive rate.
The integration of MITRE ATT&CK Analyzer delivers benefits of additional YARA rules for detecting potential Indicators of Compromise (IoC) or TTPs (Tactics, Techniques and Procedures).
As of November 2023, we’re supporting more than 25,000 IoCs, with additional rules being added constantly by the DFIR Lab team. Keep track of our additions by following our team on X (Twitter) and Linkedin.
Finding details;
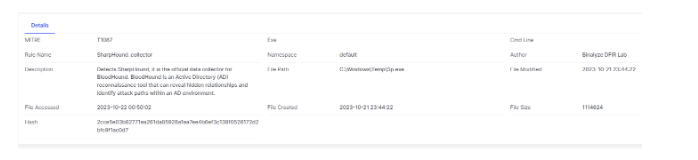
Detailed information for each verdict
Comprehensive analyzers help you see the attack stages, the footprints of any attackers, and which of the tactics in MITRE ATT&CK were used.
By using this option, you’ll have a greater understanding of what the attackers intentions were and what they’ve done in your systems. Categorizing IOCs and malware identified by our automated evidence analyzers against certain MITRE tactics and categories using MITRE ATT&CK mapping makes it even quicker and easier to understand the intent of certain IOCs and start the process towards appropriate remediation.
Findings from the automated analyzers can then be viewed as part of comprehensive, intuitive and efficient investigation experience in the new AIR Investigation Hub.
Read more about how our automated analyzers are used within the Investigation Hub to move through a malware investigation in our recent blog.
The Investigation Hub consolidates case relevant evidence, artifacts and insights into a single pane of glass. By having everything in one place, it removes the unnecessary and inefficient back and forth of hunting for relevant information, streamlining your investigation and remediation efforts.
To help focus and progress the investigation, analyzers provide three verdict levels to you, representing how serious any discovered threat is.
Threat levels:
- Dangerous – a dangerous verdict will indicate specific malware families or TTPs that are only ever used by malware.
- Suspicious – a suspicious verdict aims to highlight indicators that are more than likely to be used for malicious rather than legitimate purposes.
- Relevant – relevant is our lowest verdict level. This level is intended to show indicators that we can’t say are 100% malicious until they’ve been more thoroughly analyzed. A good example would be either a password protected archive or macro enabled office document. These file types are typically used for legitimate purposes but have gained popularity amongst bad actors for exploitation
What Problem Does This Solve for AIR Customers?
During your analysis, the analyzers will quickly and clearly show you any easily compromised assets amongst your total estate of hundreds or thousands of machines.
You’ll never again have to spend your time hunting for a needle in a haystack. Finding from AIR’s MITRE ATT&CK Analyzer, working in conjunction with Investigation Hub, free-up time to focus on other key parts of your DFIR investigation process – driving faster remediation and incident response case closures.
Watch our new on-demand webinar to learn more about how AIR’s Investigation Hub provides the context needed to prioritize next steps in your investigation.















